You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
{{ message }}
This repository was archived by the owner on Jul 22, 2024. It is now read-only.
description: "Repository for Python scripts using MDATP public API"
8
8
---
9
9
10
-
# MDATP Python automation
10
+
# MDATP Python API samples
11
11
12
-
In this blog, we will use Python (!) to automate a response to a high severity alert, by isolating the machine involved.
12
+
Welcome to the repository for Python scripts using MDATP public API!
13
+
This repository is a starting point for all MDATP users to share content and sample code in different languages that utilizes MDATP API to enhance and automate your security.
13
14
14
-
In a [previous blog](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Automate-Windows-Defender-ATP-response-action-Machine-isolation/m-p/362701#M8), we provided a PowerShell script with the same functionality. Due to several requests we want to demonstrate the same with Python as well.
15
15
16
-
* Step 1: Add the required permission to your application
16
+
Here are a few examples we published:
17
17
18
-
* Step 2: Download the script and insert your credentials
18
+
1.[MDATP "Hello World" - Pull alerts from MDATP using API](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/WDATP-API-Hello-World-or-using-a-simple-PowerShell-script-to/ba-p/326813)
19
19
20
-
* Step 3: Run the script and bask in automation glory
20
+
2.[Get Indicators of Attack (IoC) from MISP to MDATP](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Microsoft-Defender-ATP-and-Malware-Information-Sharing-Platform/m-p/576648#M100) ([Code](https://github.com/microsoft/MicrosoftDefenderATP-API-PowerShell/blob/master/Samples/Get-MISP-Hash.ps1))
21
21
22
-
## Step 1 - Add the required permission to the application:
If you’ve already created an app, you can skip and move to the “add isolation permissions” section below. If you haven’t, first you need to create one using the instructions described in the first part of the [Hello world](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/WDATP-API-Hello-World-or-using-a-simple-PowerShell-script-to/ba-p/326813) blog, and then move on to "add isolation permissions".
24
+
4.[Ticketing system integration – Alert update API](https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Ticketing-system-integration-Alert-update-API/ba-p/352191)
25
25
26
-
Please save your **Application key, Application ID and Tenant ID** while you create your app, you will use them soon (instructions on where to find this are in the blog linked above).
26
+
## Share your work
27
+
We welcome you to share and contribute, check out the guide in the [CONTRIBUTING.md file](https://github.com/microsoft/MicrosoftDefenderATP-API-PowerShell/blob/master/CONTRIBUTING.md).
27
28
28
-
### Add isolation permissions:
29
+
## Additional MDATP repositories
30
+
We have more repositories for different use cases, we invite you to explore and contribute.
29
31
30
-
* Open [Azure portal](https://ms.portal.azure.com/#home)
31
-
* Navigate to Azure Active Directory > App registrations
32
-
* Under All Apps, find and select the application, for example ContosoSIEMConnector
33
-
* Click on View API Permissions > then Add a permission
34
-
* Select the checkbox for Isolate machine application permission (make sure you have the “read alerts” permission as well).
Done! You have successfully added the required permissions to the application.
42
-
43
-
## Step 2: copy the script and insert your credentials
44
-
Copy the content of the isolation.py file from this repository to your own python (.py) file.
45
-
46
-
Remember when I asked you to save your **Application key, Application ID and Tenant ID** from the azure portal? We will now *embed them into the script*.
47
-
48
-
Paste the values as strings (between a pair of quotation marks) here (line 9):
| Comment | String | Comment to associate with the action. **Required.**|
69
-
| IsolationType | String | Type of the isolation. Allowed values are: 'Full' or 'Selective'. **Required.**|
70
-
71
-
You can read more about our API in [this link](https://docs.microsoft.com/en-gb/windows/security/threat-protection/microsoft-defender-atp/exposed-apis-list).
72
-
73
-
## Bonus step: Isolate a single machine using MachineID
74
-
75
-
This script can also isolate a single machine, you simply need to provide the the ID of this machine. You can find the MachineID in the URL of the machine page in the security center:
76
-
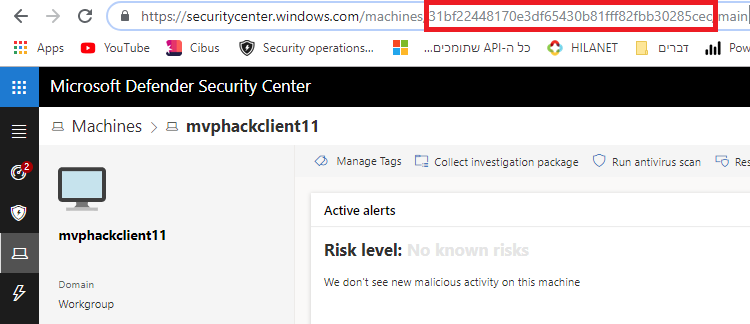
77
-
Now, simply run the script, same as before, but pass the MachineID as the first argument as follows:
78
-
```
79
-
Python isolation.py 31bf22448170e3df65430b81fff82fbb30285cec “Comment regarding the isolation” Full
80
-
```
81
-
82
-
The rest of the arguments are the same as above.
83
-
84
-
**You can use this functionality to build more (exciting) automations!**
85
-
86
-
87
-
As always, we would love to get your thoughts and feedback.
88
-
89
-
Thanks,
90
-
91
-
@Itai Zur, program manager, Windows Defender ATP
92
-
93
-
@Dan Michelson, program manager, Windows Defender ATP
94
-
95
-
@Haim Goldshtein, security software engineer, Windows Defender ATP
32
+
*[PowerShell scripts using MDATP public API](https://github.com/microsoft/MicrosoftDefenderATP-API-PowerShell)
*[PowerBI reports using MDATP data](https://github.com/microsoft/MicrosoftDefenderATP-PowerBI)
96
35
36
+
## API documentation
37
+
For more info on our available APIs - go to our [API documentation](https://docs.microsoft.com/en-gb/windows/security/threat-protection/microsoft-defender-atp/exposed-apis-list)
0 commit comments