diff --git a/cloudsplaining/output/dist/js/chunk-56fa57a3.js b/cloudsplaining/output/dist/js/chunk-56fa57a3.js
new file mode 100644
index 00000000..538610ff
--- /dev/null
+++ b/cloudsplaining/output/dist/js/chunk-56fa57a3.js
@@ -0,0 +1,2 @@
+(window["webpackJsonp"]=window["webpackJsonp"]||[]).push([["chunk-56fa57a3"],{"97a1":function(e,t,a){"use strict";a.r(t);var i=function(){var e=this,t=e.$createElement,a=e._self._c||t;return a("b-tab",["default"===e.appendices_content?a("div",[a("Glossary")],1):a("div",{domProps:{innerHTML:e._s(e.appendices_content)}})])},s=[],o=function(){var e=this,t=e.$createElement,a=e._self._c||t;return a("div",{staticStyle:{"text-align":"justify"}},[a("h3",{attrs:{id:"overview"}},[e._v("Glossary")]),a("p",[a("span",{domProps:{innerHTML:e._s(e.glossary)}})]),a("br"),a("br")])},n=[],r=a("fa5b"),c=a.n(r),l=a("d4cd")({html:!0,linkify:!0,typographer:!0});const d=l.render(c.a);var h={name:"Glossary",computed:{glossary(){return d}}},p=h,m=a("2877"),u=Object(m["a"])(p,o,n,!1,null,"1c16e608",null),f=u.exports,g={components:{Glossary:f},data(){return{appendices_content:appendices_content}}},y=g,A=Object(m["a"])(y,i,s,!1,null,null,null);t["default"]=A.exports},fa5b:function(e,t){var a='Impact
The impact the risk would have on an organization if such a vulnerability were successfully exploited is rated according to criteria listed below. Note that these ratings are based on NIST 800-30 impact definitions.
- Critical: The issue causes multiple severe or catastrophic effects on operations, assets or other organizations.
- High: Causes produces severe degradation in mission capability to the point that the organization is not able to perform primary functions or results in damage to organizational assets.
- Medium: Trigger degradation in mission capability to an extent the application is able to perform its primary functions, but their effectiveness is reduced and there may be damage to the organization's assets.
- Low: Results in limited degradation in mission capability; the organization is able to perform its primary functions, but their effectiveness is noticeably reduced and may result in minor damage to the organization's assets.
Privilege Escalation
These policies allow a combination of IAM actions that allow a principal with these permissions to escalate their privileges - for example, by creating an access key for another IAM user, or modifying their own permissions. This research was pioneered by Spencer Gietzen at Rhino Security Labs. Remediation Guidance can be found here.
Resource Exposure
Resource Exposure actions allow modification of Permissions to resource-based policies or otherwise can expose AWS resources to the public via similar actions that can lead to resource exposure - for example, the ability to modify AWS Resource Access Manager.
Infrastructure Modification
Infrastructure Modification describes IAM actions with "modify" capabilities, and can therefore lead to Resource Hijacking, unauthorized creation of Infrastructure, Backdoor creation, and/or modification of existing resources which can result in downtime.
Data Exfiltration
Policies with Data Exfiltration potential allow certain read-only IAM actions without resource constraints, such as s3:GetObject, ssm:GetParameter*, or secretsmanager:GetSecretValue. Unrestricted s3:GetObject permissions has a long history of customer data leaks. ssm:GetParameter* and secretsmanager:GetSecretValue are both used to access secrets. rds:CopyDBSnapshot and rds:CreateDBSnapshot can be used to exfiltrate RDS database contents.
Service Wildcard
"Service Wildcard" is an unofficial way of referring to IAM policy statements that grant access to ALL actions under a service - like s3:*. Prioritizing the remediation of policies with this characteristic can help to efficiently reduce the total count of high risk issues in the Cloudsplaining report.
Credentials Exposure
Credentials Exposure actions return credentials as part of the API response , such as ecr:GetAuthorizationToken, iam:UpdateAccessKey, and others. The full list is below.
Roles Assumable by Compute Services
IAM Roles can be assumed by AWS Compute Services (such as EC2, ECS, EKS, or Lambda) can present greater risk than user-defined roles, especially if the AWS Compute service is on an instance that is directly or indirectly exposed to the internet. Flagging these roles is particularly useful to penetration testers (or attackers) under certain scenarios. For example, if an attacker obtains privileges to execute ssm:SendCommand and there are privileged EC2 instances with the SSM agent installed, they can effectively have the privileges of those EC2 instances. Remote Code Execution via AWS Systems Manager Agent was already a known escalation/exploitation path, but Cloudsplaining can make the process of identifying theses cases easier.
Trust Policy
A JSON policy document in which you define the principals that you trust to assume the role. A role trust policy is a required resource-based policy that is attached to a role in IAM. The principals that you can specify in the trust policy include users, roles, accounts, and services.
This definition was taken from the AWS Documentation here.
Principal
An entity in AWS that can perform actions and access resources. A principal can be an AWS account root user, an IAM user, or a role.
Role
An IAM identity that you can create in your account that has specific permissions. An IAM role has some similarities to an IAM user. Roles and users are both AWS identities with permissions policies that determine what the identity can and cannot do in AWS. However, instead of being uniquely associated with one person, a role is intended to be assumable by anyone who needs it. Also, a role does not have standard long-term credentials such as a password or access keys associated with it. Instead, when you assume a role, it provides you with temporary security credentials for your role session.
We are particularly interested in roles used for compute services - i.e., Compute Service Roles.
This definition was taken from the AWS Documentation here.
Managed Policy
There are two types of Managed Policies: AWS-managed policies and Customer-managed policies. They are described below.
Criteria for selecting Managed Policies versus Inline policies can be found in the AWS documentation here.
Customer-managed policy
AWS documentation on Customer-managed policies can be found here.
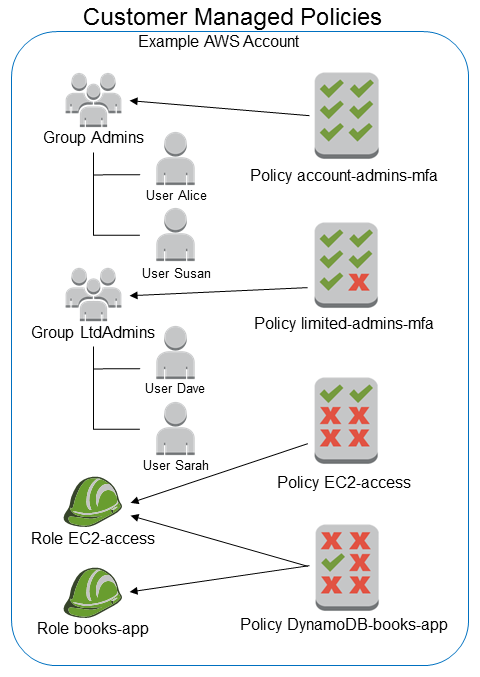
The following diagram illustrates customer managed policies. Each policy is an entity in IAM with its own Amazon Resource Name (ARN) that includes the policy name. Notice that the same policy can be attached to multiple principal entities—for example, the same DynamoDB-books-app policy is attached to two different IAM roles.
AWS-managed policy
An AWS managed policy is a standalone policy that is created and administered by AWS. Standalone policy means that the policy has its own Amazon Resource Name (ARN) that includes the policy name. For example, arn:aws:iam::aws:policy/IAMReadOnlyAccess is an AWS managed policy.
AWS documentation on AWS-managed policies can be found here.
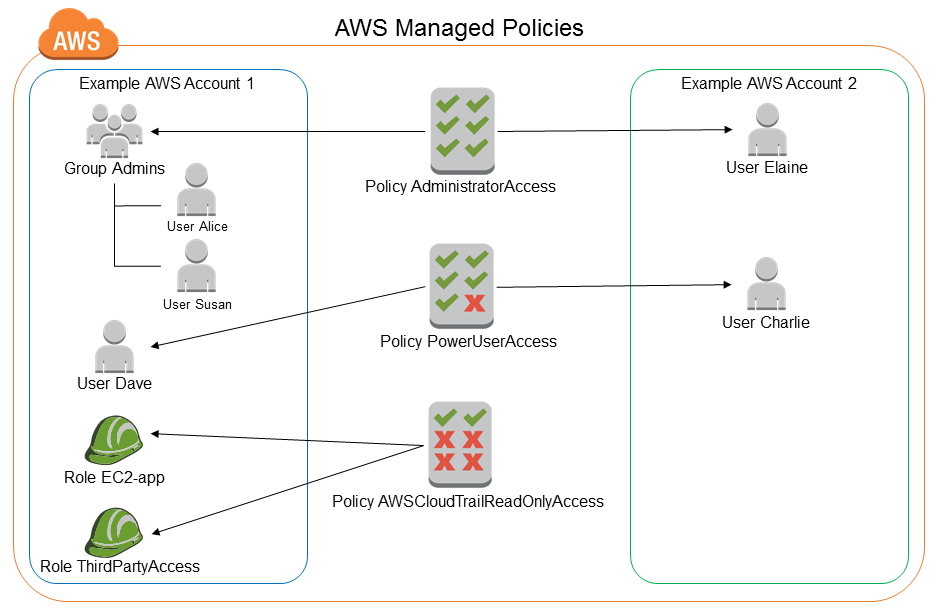
The following diagram (taken from the AWS documentation) illustrates AWS managed policies. The diagram shows three AWS managed policies: AdministratorAccess, PowerUserAccess, and AWSCloudTrailReadOnlyAccess. Notice that a single AWS managed policy can be attached to principal entities in different AWS accounts, and to different principal entities in a single AWS account.
Inline Policy
An inline policy is a policy that's embedded in an IAM identity (a user, group, or role). That is, the policy is an inherent part of the identity. You can create a policy and embed it in a identity, either when you create the identity or later.
AWS documentation on inline policies can be found here.
The following diagram illustrates inline policies. Each policy is an inherent part of the user, group, or role. Notice that two roles include the same policy (the DynamoDB-books-app policy), but they are not sharing a single policy; each role has its own copy of the policy.
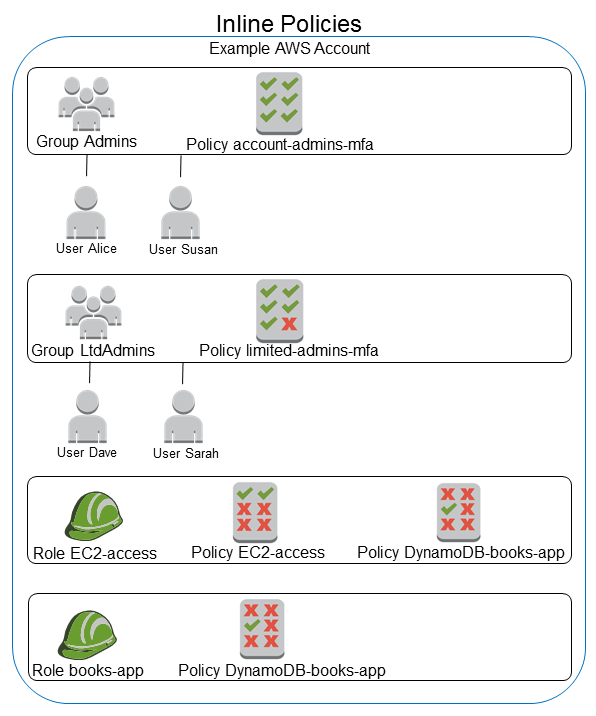
Inline policies are useful if you want to maintain a strict one-to-one relationship between a policy and the identity that it's applied to. For example, you want to be sure that the permissions in a policy are not inadvertently assigned to an identity other than the one they're intended for. When you use an inline policy, the permissions in the policy cannot be inadvertently attached to the wrong identity. In addition, when you use the AWS Management Console to delete that identity, the policies embedded in the identity are deleted as well. That's because they are part of the principal entity.
';e.exports=a}}]);
+//# sourceMappingURL=chunk-56fa57a3.js.map
\ No newline at end of file
diff --git a/cloudsplaining/output/dist/js/chunk-5e001255.js b/cloudsplaining/output/dist/js/chunk-5e001255.js
new file mode 100644
index 00000000..fdd91104
--- /dev/null
+++ b/cloudsplaining/output/dist/js/chunk-5e001255.js
@@ -0,0 +1,2 @@
+(window["webpackJsonp"]=window["webpackJsonp"]||[]).push([["chunk-5e001255"],{"0c96":function(e,i){var t=' After you've rewritten your IAM policy, we suggest two options for validating that it will pass Cloudsplaining and alleviate any remaining concerns:
- Run Cloudsplaining's
scan-policy-file command, which scans a single JSON policy file instead of the entire AWS Account's Authorization details. - Leveraging Parliament by Duo-Labs, courtesy of Scott Piper
You can validate that your remediated policy passes Cloudsplaining by running the following command:
cloudsplaining scan-policy-file --input-file policy.json --exclusions-file exclusions.yml
When there are no more results, it passes!
Using Parliament to Lint your Policies
parliament is an AWS IAM linting library. It reviews policies looking for problems such as:
- malformed JSON
- missing required elements
- incorrect service prefix and action names
- incorrect resources or conditions for the actions provided
- type mismatches
- bad policy patterns
This library duplicates (and adds to!) much of the functionality in the web console page when reviewing IAM policies in the browser.
You can use Parliament to scan your IAM policy by visiting the Web Page! https://parliament.summitroute.com/
';e.exports=t},"303b":function(e,i,t){"use strict";t.r(i);var o=function(){var e=this,i=e.$createElement,t=e._self._c||i;return t("b-tab",["default"===e.guidance_content?t("div",[t("Guidance")],1):t("div",{domProps:{innerHTML:e._s(e.guidance_content)}})])},s=[],n=function(){var e=this,i=e.$createElement,t=e._self._c||i;return t("div",{staticStyle:{"text-align":"justify"}},[t("h3",{attrs:{id:"triage-guidance"}},[e._v("Triaging")]),t("p",[t("span",{domProps:{innerHTML:e._s(e.triageGuidance)}})]),t("br"),t("br"),t("h3",{attrs:{id:"remediation-guidance"}},[e._v("Remediation")]),t("p",[t("span",{domProps:{innerHTML:e._s(e.remediationGuidance)}})]),t("br"),t("br"),t("h3",{attrs:{id:"validation-guidance"}},[e._v("Validation")]),t("p",[t("span",{domProps:{innerHTML:e._s(e.validationText)}})]),t("br"),t("br")])},a=[],r=t("dd2f"),l=t.n(r),c=t("5a07"),u=t.n(c),d=t("a91e"),p=t.n(d),h=t("0c96"),g=t.n(h),m=t("d4cd")({html:!0,linkify:!0,typographer:!0});const f=m.render(l.a),y=m.render(u.a),w=m.render(p.a),v=m.render(g.a);var b={name:"Guidance",computed:{overview(){return f},triageGuidance(){return y},remediationGuidance(){return w},validationText(){return v}}},A=b,x=t("2877"),k=Object(x["a"])(A,n,a,!1,null,"54f1a057",null),S=k.exports,M={components:{Guidance:S},data(){return{guidance_content:guidance_content}}},I=M,P=Object(x["a"])(I,o,s,!1,null,null,null);i["default"]=P.exports},"5a07":function(e,i){var t='Understanding Context
It's essential to understand the context behind the findings that the report generates. Understanding the context behind the findings aids the assessor in triaging the results accurately.
This report generates findings on Policies that do not leverage resource constraints and identifies some attributes to help prioritize which ones to address - such as Privilege Escalation, Resource Exposure, and Data Exfiltration. These results help you to identify your IAM threat landscape and reduce blast radius. In the event of credential compromise, you can prevent an attacker from exploiting the risks mentioned above, in addition to preventing mass deletion, destruction, or modification of existing infrastructure.
However, this tool does not attempt to understand the context behind everything in your AWS account. It's possible to understand the context behind some of these things programmatically - whether the policy is applied to an instance profile, whether the policy is attached, whether inline IAM policies are in use, and whether or not AWS Managed Policies are in use. Only you know the context behind the design of your AWS infrastructure and the IAM strategy.
For example, an AWS Lambda policy used as a simple service checking the configuration of AWS infrastructure might be a good use case for resource constraints. Conversely, perhaps you applied the AdministratorAccess AWS-managed policy to an Instance Profile so that an EC2 instance can run Terraform to provision AWS resources via Infrastructure as Code. In the second example, the role is extremely permissive by design - and a tool can't automatically understand that context.
As such, the tool aims to:
- Map out your risk landscape of IAM identity-based policies, enumerating the potential risks for a full IAM threat model
- Identify where you can reduce the blast radius in the case of credentials compromise
- Help you prioritize which ones to remediate
- Provide a straightforward workflow to remediate
- Provide a sufficient exclusions mechanism to programmatically define where deviations from resource constraints are by design
Assessment Recap
To recap: you've followed these steps to generate this report:
- Downloaded the Account Authorization details JSON file
cloudsplaining download --profile default --output default-account-details.json
- Generated your custom exclusions file
cloudsplaining create-exclusions-file --output-file exclusions.yml
- Generated the report
cloudsplaining scan --input-file default-account-details.json --exclusions-file exclusions.yml - This generates (1) The single-file HTML report and the raw JSON data file
Triaging workflow
An assessor can follow this general workflow:
- Open a ticket in your organization's project management tool of choice (for example, JIRA or Salesforce) in the AWS account owner's project
- Attach the HTML report, JSON Data file, and CSV worksheet
- Ask the service/account owner team to fill out the Triage worksheet
When you ask the service/account owner team to fill out the Triage CSV worksheet, you can use some text like the following:
As part of our security assessment, our team ran Cloudsplaining on your AWS account. Cloudsplaining maps out the IAM risk landscape in a report, identifies where resource ARN constraints are not in use, and identifies other risks in IAM policies like Privilege Escalation, Data Exfiltration, and Resource Exposure/Permissions management. Remediating these issues, where applicable, will help to limit the blast radius in the case of compromised AWS credentials. We request that you review the HTML report and fill out the "Justification" field in the Triage worksheet. Based on the corresponding details in the HTML report, provide either (1) A justification on why the result is a False Positive, or (2) Identify that it is a legitimate finding.
Triaging considerations
When triaging your results, consider some of the factors listed below as you identify False Positives vs. legitimate findings. There are some scenarios where "Resource": "*" access is by design and is therefore a false positive. This section covers some of the common scenarios.
Infrastructure Creation roles:
IAM roles that create infrastructure via Infrastructure as Code Technologies (for example, Terraform or CloudFormation) require high permission levels to provision AWS infrastructure. These will usually be false positives. When you see these instances, make sure that these roles are adequately protected. For instance, make sure that roles within the AWS account are not able to assume this role or affect its configuration in any way. Additionally, consider restricting the trust policy so that a set of explicitly stated IAM principals are the only ones who can assume that role. Take special care to audit instances of sts:AssumeRole within this AWS account.
System roles vs. User Roles: System roles - IAM Roles applied to compute services, such as EC2 Instance Profiles, ECS Task Execution roles, or Lambda Task Execution roles - should almost always leverage resource ARN constraints for actions that perform "Write" actions. Exceptions to this could include Infrastructure provisioning or other edge cases.
Conversely, user roles will almost always be used against * resources for the sake of convenience, innovation, and avoiding overly restrictive limitations. In the user role scenario, consider:
- Design context: is it appropriate? (For instance, maybe all your user roles don't need
iam:*) - Environment: If this is a Dev environment, frequently-used user roles probably allow more permissions for innovation purposes. However, in later environments - especially production - commonly used user roles should be read-only - or the more permissive ones should be for break-glass scenarios only.
- Regardless of the context: there should always be security guardrails in place, like Service Control Policies through AWS Organizations or IAM Permissions Boundaries to prevent against egregious mistakes.
Organization-specific results
For example, perhaps you allow kms:Decrypt for * resources (by design) in your organization for one reason or another. Cloudsplaining flags this as a result. However, there are mitigating controls in place. Firstly, you leverage strict resource-based KMS key policies to lock down all KMS keys, explicitly stating individual IAM principals that are allowed to use them. Secondly, you provision all KMS keys with CloudFormation or Terraform, so you are confident that this pattern is consistent across all KMS keys in your AWS accounts. Therefore, kms:Decrypt to * resources is not a finding you are concerned about. In this case, you decide it is acceptable to exclude kms:Decrypt from your results.
Common False Positive Scenarios
Conditions Logic:
This tool does not evaluate IAM Conditions logic. If your policies use wildcard resources but restrict according to condition keys, then it's possible this is a false positive. However, you might want to double-check the accuracy of the conditions logic in those IAM policies. While IAM conditions can be extremely powerful, implementation is also prone to human error. We suggest leveraging Parliament by Duo Labs (courtesy of Scott Piper), to lint your policies for accuracy - especially when IAM conditions are in use.
logs:CreateLogGroup and logs:PutLogEvent:
Depending on how your organization approaches CloudWatch Logs Agent configuration, IAM, and CloudWatch Logs Group naming conventions, it is sometimes near-impossible to prevent cross-contamination of logs or Log Injection to the Log Streams from other instance IDs. Cross-Contamination of CloudWatch Logs is an issue of its own that is definitely beyond the scope of this document - but consider this as a potential limitation by AWS when trying to identify a remediation plan.
Building the Exclusions File
After you have identified the False Positives, add the False Positive criteria to your custom Cloudsplaining exclusions file. The False Positives generally fall into one of two categories:
- False positives that will occur across all of your AWS accounts, due to your organization-wide implementation strategy
- False positives specific to this AWS account
To make the exclusions file, create a YAML file that we will use to list out exclusions with the create-exclusions-file command.
cloudsplaining create-exclusions-file\n
This will generate a file titled exclusions.yml in your current directory.
The default exclusions file contains these contents:
# Policy names to exclude from evaluation\n# Suggestion: Add policies here that are known to be overly permissive by design, after you run the initial report.\npolicies:\n - "AWSServiceRoleFor*"\n - "*ServiceRolePolicy"\n - "*ServiceLinkedRolePolicy"\n - "AdministratorAccess" # Otherwise, this will take a long time\n - "service-role*"\n - "aws-service-role*"\n# Don't evaluate these roles, users, or groups as part of the evaluation\nroles:\n - "service-role*"\n - "aws-service-role*"\nusers:\n - ""\ngroups:\n - ""\n# Read-only actions to include in the results, such as s3:GetObject\n# By default, it includes Actions that could lead to Data Exfiltration\ninclude-actions:\n - "s3:GetObject"\n - "ssm:GetParameter"\n - "ssm:GetParameters"\n - "ssm:GetParametersByPath"\n - "secretsmanager:GetSecretValue"\n# Write actions to include from the results, such as kms:Decrypt\nexclude-actions:\n - ""\n
Add whatever values you want to the above depending on your organization's context.
Under policies, list the path of policy names that you want to exclude.
If you want to exclude a role titled MyRole, list MyRole or MyR* in the roles list.
You can follow the same approach for users and groups list.
Now, run the scan to generate a new Cloudsplaining report that considers your exclusions criteria. This way, you are working with a report version that consists of True Positives only.
cloudsplaining scan --input-file default.json --exclusions-file exclusions.yml\n
You can now proceed to the Remediation stage.
';e.exports=t},a91e:function(e,i){var t=' Depending on the existing workload of the engineering team addressing your concerns, the team might ask to address high priority items first rather than addressing all items, especially if the report is quite large. In this scenario, consider instructing the team to address High Priority Risks and the usage of AWS-Managed Policies first.
High priority risks:
These include Privilege Escalation, Data Exfiltration, and Potential Resource Exposure/Permissions management. This report highlights each finding that has these high priority risks.
Moving from AWS Managed Policies over to custom policies:
AWS managed policies always include access to * resources because AWS provides these same policies universally to all customer accounts. If this report flags any AWS-managed policies, it means that the account/service owner team will not only have to implement resource constraints - they will have to create a custom IAM policy to do so. To limit this work, it is best to migrate away from the root cause of the problem - using AWS managed policies.
You can then queue the work for remediating the other Customer-managed policies that do not have the High-Priority Risks attributes. Implementing resource ARN constraints for True Positives is still important, since overly permissive "Write" actions can cause modification or deletion of AWS resources by a bad actor with compromised credentials, resulting in downtime.
We suggest two options for remediating each finding:
- Leveraging Policy Sentry, courtesy of Kinnaird McQuade, which generates policies with resource ARN constraints at user-specified access levels automagically.
- Manually rewriting the policies
Leveraging Policy Sentry
For guidance on how to use Policy Sentry, please see the documentation here. This is highly suggested - within 10 minutes of learning the tool, creating a secure IAM policy becomes a matter of:
- Generating the YAML template with
policy_sentry create-template --output-file crud.yml --template-type crud - Literally copying/pasting resource ARNs into the template
- Running
policy_sentry write-policy --input-file crud.yml
Manually rewriting the IAM Policies
For guidance on how to write secure IAM Policies by hand, see the tutorial here. Just be aware - you'll spend a lot of time looking at the AWS Documentation on IAM Actions, Resources, and Condition Keys, which can become quite tedious and time-consuming.
';e.exports=t},dd2f:function(e,i){var t='This report contains the security assessment results from Cloudsplaining, which maps out the IAM risk landscape in a report, identifies where resource ARN constraints are not used, and identifies other risks in IAM policies like Privilege Escalation, Resource Exposure, Infrastructure Modification, and Data Exfiltration. Remediating these issues, where necessary, will help to limit the blast radius in the case of compromised AWS credentials.
';e.exports=t}}]);
+//# sourceMappingURL=chunk-5e001255.js.map
\ No newline at end of file
diff --git a/cloudsplaining/output/dist/js/index.js b/cloudsplaining/output/dist/js/index.js
index 294f4af9..9917f0b8 100644
--- a/cloudsplaining/output/dist/js/index.js
+++ b/cloudsplaining/output/dist/js/index.js
@@ -1,4 +1,4 @@
-(function(e){var t={};function a(o){if(t[o])return t[o].exports;var s=t[o]={i:o,l:!1,exports:{}};return e[o].call(s.exports,s,s.exports,a),s.l=!0,s.exports}a.m=e,a.c=t,a.d=function(e,t,o){a.o(e,t)||Object.defineProperty(e,t,{enumerable:!0,get:o})},a.r=function(e){"undefined"!==typeof Symbol&&Symbol.toStringTag&&Object.defineProperty(e,Symbol.toStringTag,{value:"Module"}),Object.defineProperty(e,"__esModule",{value:!0})},a.t=function(e,t){if(1&t&&(e=a(e)),8&t)return e;if(4&t&&"object"===typeof e&&e&&e.__esModule)return e;var o=Object.create(null);if(a.r(o),Object.defineProperty(o,"default",{enumerable:!0,value:e}),2&t&&"string"!=typeof e)for(var s in e)a.d(o,s,function(t){return e[t]}.bind(null,s));return o},a.n=function(e){var t=e&&e.__esModule?function(){return e["default"]}:function(){return e};return a.d(t,"a",t),t},a.o=function(e,t){return Object.prototype.hasOwnProperty.call(e,t)},a.p="",a(a.s=0)})({0:function(e,t,a){e.exports=a("5a00")},"0068":function(e,t,a){"use strict";function o(e){return Object.prototype.toString.call(e)}function s(e){return"[object String]"===o(e)}var i=Object.prototype.hasOwnProperty;function n(e,t){return i.call(e,t)}function r(e){var t=Array.prototype.slice.call(arguments,1);return t.forEach((function(t){if(t){if("object"!==typeof t)throw new TypeError(t+"must be object");Object.keys(t).forEach((function(a){e[a]=t[a]}))}})),e}function c(e,t,a){return[].concat(e.slice(0,t),a,e.slice(t+1))}function l(e){return!(e>=55296&&e<=57343)&&(!(e>=64976&&e<=65007)&&(65535!==(65535&e)&&65534!==(65535&e)&&(!(e>=0&&e<=8)&&(11!==e&&(!(e>=14&&e<=31)&&(!(e>=127&&e<=159)&&!(e>1114111)))))))}function h(e){if(e>65535){e-=65536;var t=55296+(e>>10),a=56320+(1023&e);return String.fromCharCode(t,a)}return String.fromCharCode(e)}var d=/\\([!"#$%&'()*+,\-.\/:;<=>?@[\\\]^_`{|}~])/g,m=/&([a-z#][a-z0-9]{1,31});/gi,p=new RegExp(d.source+"|"+m.source,"gi"),u=/^#((?:x[a-f0-9]{1,8}|[0-9]{1,8}))$/i,f=a("bd68");function g(e,t){var a;return n(f,t)?f[t]:35===t.charCodeAt(0)&&u.test(t)&&(a="x"===t[1].toLowerCase()?parseInt(t.slice(2),16):parseInt(t.slice(1),10),l(a))?h(a):e}function v(e){return e.indexOf("\\")<0?e:e.replace(d,"$1")}function A(e){return e.indexOf("\\")<0&&e.indexOf("&")<0?e:e.replace(p,(function(e,t,a){return t||g(e,a)}))}var P=/[&<>"]/,b=/[&<>"]/g,y={"&":"&","<":"<",">":">",'"':"""};function w(e){return y[e]}function I(e){return P.test(e)?e.replace(b,w):e}var z=/[.?*+^$[\]\\(){}|-]/g;function C(e){return e.replace(z,"\\$&")}function D(e){switch(e){case 9:case 32:return!0}return!1}function R(e){if(e>=8192&&e<=8202)return!0;switch(e){case 9:case 10:case 11:case 12:case 13:case 32:case 160:case 5760:case 8239:case 8287:case 12288:return!0}return!1}var S=a("7ca0");function _(e){return S.test(e)}function k(e){switch(e){case 33:case 34:case 35:case 36:case 37:case 38:case 39:case 40:case 41:case 42:case 43:case 44:case 45:case 46:case 47:case 58:case 59:case 60:case 61:case 62:case 63:case 64:case 91:case 92:case 93:case 94:case 95:case 96:case 123:case 124:case 125:case 126:return!0;default:return!1}}function M(e){return e=e.trim().replace(/\s+/g," "),"Ṿ"==="ẞ".toLowerCase()&&(e=e.replace(/ẞ/g,"ß")),e.toLowerCase().toUpperCase()}t.lib={},t.lib.mdurl=a("d8a6"),t.lib.ucmicro=a("d5d1"),t.assign=r,t.isString=s,t.has=n,t.unescapeMd=v,t.unescapeAll=A,t.isValidEntityCode=l,t.fromCodePoint=h,t.escapeHtml=I,t.arrayReplaceAt=c,t.isSpace=D,t.isWhiteSpace=R,t.isMdAsciiPunct=k,t.isPunctChar=_,t.escapeRE=C,t.normalizeReference=M},"04f8":function(e,t,a){"use strict";var o=a("1212"),s=a("d039"),i=a("cfe9"),n=i.String;e.exports=!!Object.getOwnPropertySymbols&&!s((function(){var e=Symbol("symbol detection");return!n(e)||!(Object(e)instanceof Symbol)||!Symbol.sham&&o&&o<41}))},"06cf":function(e,t,a){"use strict";var o=a("83ab"),s=a("c65b"),i=a("d1e7"),n=a("5c6c"),r=a("fc6a"),c=a("a04b"),l=a("1a2d"),h=a("0cfb"),d=Object.getOwnPropertyDescriptor;t.f=o?d:function(e,t){if(e=r(e),t=c(t),h)try{return d(e,t)}catch(a){}if(l(e,t))return n(!s(i.f,e,t),e[t])}},"0758":function(e,t,a){"use strict";var o=a("0068").isSpace;e.exports=function(e,t,a,s){var i,n,r,c,l=e.bMarks[t]+e.tShift[t],h=e.eMarks[t];if(e.sCount[t]-e.blkIndent>=4)return!1;if(i=e.src.charCodeAt(l),35!==i||l>=h)return!1;n=1,i=e.src.charCodeAt(++l);while(35===i&&l6||ll&&o(e.src.charCodeAt(r-1))&&(h=r),e.line=t+1,c=e.push("heading_open","h"+String(n),1),c.markup="########".slice(0,n),c.map=[t,e.line],c=e.push("inline","",0),c.content=e.src.slice(l,h).trim(),c.map=[t,e.line],c.children=[],c=e.push("heading_close","h"+String(n),-1),c.markup="########".slice(0,n)),!0)}},"07fa":function(e,t,a){"use strict";var o=a("50c4");e.exports=function(e){return o(e.length)}},"0861":function(e,t){var a='If your IAM policy does require access to those actions, you should provide an explanation. Example requirements include:
- User Role: This IAM Policy is used by an IAM Role that requires access to
* resources because human users assume this role. We have restricted the access levels appropriate to what the user needs. - Infrastructure Provisioning role: This IAM Policy is used by roles that deploy infrastructure using CloudFormation or Terraform and need administrative access by design.
- Conditions logic is in use: The Policy has access to
* resources, but the statement enforces least privilege via IAM condition statements.
While other edge cases and justifications exist, the above items are the most common justifications. For information on Common False Positive Scenarios, see the documentation here.
';e.exports=a},"08ae":function(e,t,a){"use strict";var o=a("0068"),s=a("565b"),i=a("7cc2"),n=a("a915"),r=a("7696"),c=a("4cb4"),l=a("fbcd"),h=a("d8a6"),d=a("9d88"),m={default:a("8a31"),zero:a("1caa"),commonmark:a("428d")},p=/^(vbscript|javascript|file|data):/,u=/^data:image\/(gif|png|jpeg|webp);/;function f(e){var t=e.trim().toLowerCase();return!p.test(t)||!!u.test(t)}var g=["http:","https:","mailto:"];function v(e){var t=h.parse(e,!0);if(t.hostname&&(!t.protocol||g.indexOf(t.protocol)>=0))try{t.hostname=d.toASCII(t.hostname)}catch(a){}return h.encode(h.format(t))}function A(e){var t=h.parse(e,!0);if(t.hostname&&(!t.protocol||g.indexOf(t.protocol)>=0))try{t.hostname=d.toUnicode(t.hostname)}catch(a){}return h.decode(h.format(t),h.decode.defaultChars+"%")}function P(e,t){if(!(this instanceof P))return new P(e,t);t||o.isString(e)||(t=e||{},e="default"),this.inline=new c,this.block=new r,this.core=new n,this.renderer=new i,this.linkify=new l,this.validateLink=f,this.normalizeLink=v,this.normalizeLinkText=A,this.utils=o,this.helpers=o.assign({},s),this.options={},this.configure(e),t&&this.set(t)}P.prototype.set=function(e){return o.assign(this.options,e),this},P.prototype.configure=function(e){var t,a=this;if(o.isString(e)&&(t=e,e=m[t],!e))throw new Error('Wrong `markdown-it` preset "'+t+'", check name');if(!e)throw new Error("Wrong `markdown-it` preset, can't be empty");return e.options&&a.set(e.options),e.components&&Object.keys(e.components).forEach((function(t){e.components[t].rules&&a[t].ruler.enableOnly(e.components[t].rules),e.components[t].rules2&&a[t].ruler2.enableOnly(e.components[t].rules2)})),this},P.prototype.enable=function(e,t){var a=[];Array.isArray(e)||(e=[e]),["core","block","inline"].forEach((function(t){a=a.concat(this[t].ruler.enable(e,!0))}),this),a=a.concat(this.inline.ruler2.enable(e,!0));var o=e.filter((function(e){return a.indexOf(e)<0}));if(o.length&&!t)throw new Error("MarkdownIt. Failed to enable unknown rule(s): "+o);return this},P.prototype.disable=function(e,t){var a=[];Array.isArray(e)||(e=[e]),["core","block","inline"].forEach((function(t){a=a.concat(this[t].ruler.disable(e,!0))}),this),a=a.concat(this.inline.ruler2.disable(e,!0));var o=e.filter((function(e){return a.indexOf(e)<0}));if(o.length&&!t)throw new Error("MarkdownIt. Failed to disable unknown rule(s): "+o);return this},P.prototype.use=function(e){var t=[this].concat(Array.prototype.slice.call(arguments,1));return e.apply(e,t),this},P.prototype.parse=function(e,t){if("string"!==typeof e)throw new Error("Input data should be a String");var a=new this.core.State(e,this,t);return this.core.process(a),a.tokens},P.prototype.render=function(e,t){return t=t||{},this.renderer.render(this.parse(e,t),this.options,t)},P.prototype.parseInline=function(e,t){var a=new this.core.State(e,this,t);return a.inlineMode=!0,this.core.process(a),a.tokens},P.prototype.renderInline=function(e,t){return t=t||{},this.renderer.render(this.parseInline(e,t),this.options,t)},e.exports=P},"096b":function(e,t,a){"use strict";function o(e,t,a){this.type=e,this.tag=t,this.attrs=null,this.map=null,this.nesting=a,this.level=0,this.children=null,this.content="",this.markup="",this.info="",this.meta=null,this.block=!1,this.hidden=!1}o.prototype.attrIndex=function(e){var t,a,o;if(!this.attrs)return-1;for(t=this.attrs,a=0,o=t.length;a=0&&(a=this.attrs[t][1]),a},o.prototype.attrJoin=function(e,t){var a=this.attrIndex(e);a<0?this.attrPush([e,t]):this.attrs[a][1]=this.attrs[a][1]+" "+t},e.exports=o},"097b":function(e,t,a){"use strict";var o=a("096b"),s=a("0068").isWhiteSpace,i=a("0068").isPunctChar,n=a("0068").isMdAsciiPunct;function r(e,t,a,o){this.src=e,this.env=a,this.md=t,this.tokens=o,this.tokens_meta=Array(o.length),this.pos=0,this.posMax=this.src.length,this.level=0,this.pending="",this.pendingLevel=0,this.cache={},this.delimiters=[],this._prev_delimiters=[],this.backticks={},this.backticksScanned=!1,this.linkLevel=0}r.prototype.pushPending=function(){var e=new o("text","",0);return e.content=this.pending,e.level=this.pendingLevel,this.tokens.push(e),this.pending="",e},r.prototype.push=function(e,t,a){this.pending&&this.pushPending();var s=new o(e,t,a),i=null;return a<0&&(this.level--,this.delimiters=this._prev_delimiters.pop()),s.level=this.level,a>0&&(this.level++,this._prev_delimiters.push(this.delimiters),this.delimiters=[],i={delimiters:this.delimiters}),this.pendingLevel=this.level,this.tokens.push(s),this.tokens_meta.push(i),s},r.prototype.scanDelims=function(e,t){var a,o,r,c,l,h,d,m,p,u=e,f=!0,g=!0,v=this.posMax,A=this.src.charCodeAt(e);a=e>0?this.src.charCodeAt(e-1):32;while(u0&&o[0]<4?1:+(o[0]+o[1])),!s&&n&&(o=n.match(/Edge\/(\d+)/),(!o||o[1]>=74)&&(o=n.match(/Chrome\/(\d+)/),o&&(s=+o[1]))),e.exports=s},1357:function(e,t){var a='This policy contains actions that could lead to Credentials Exposure. These actions return credentials as part of the API response, such as ecr:GetAuthorizationToken, iam:UpdateAccessKey, and others. The full list is maintained here.
';e.exports=a},"13d2":function(e,t,a){"use strict";var o=a("e330"),s=a("d039"),i=a("1626"),n=a("1a2d"),r=a("83ab"),c=a("5e77").CONFIGURABLE,l=a("8925"),h=a("69f3"),d=h.enforce,m=h.get,p=String,u=Object.defineProperty,f=o("".slice),g=o("".replace),v=o([].join),A=r&&!s((function(){return 8!==u((function(){}),"length",{value:8}).length})),P=String(String).split("String"),b=e.exports=function(e,t,a){"Symbol("===f(p(t),0,7)&&(t="["+g(p(t),/^Symbol\(([^)]*)\).*$/,"$1")+"]"),a&&a.getter&&(t="get "+t),a&&a.setter&&(t="set "+t),(!n(e,"name")||c&&e.name!==t)&&(r?u(e,"name",{value:t,configurable:!0}):e.name=t),A&&a&&n(a,"arity")&&e.length!==a.arity&&u(e,"length",{value:a.arity});try{a&&n(a,"constructor")&&a.constructor?r&&u(e,"prototype",{writable:!1}):e.prototype&&(e.prototype=void 0)}catch(s){}var o=d(e);return n(o,"source")||(o.source=v(P,"string"==typeof t?t:"")),e};Function.prototype.toString=b((function(){return i(this)&&m(this).source||l(this)}),"toString")},"13d5":function(e,t,a){"use strict";var o=a("23e7"),s=a("d58f").left,i=a("a640"),n=a("1212"),r=a("9adc"),c=!r&&n>79&&n<83,l=c||!i("reduce");o({target:"Array",proto:!0,forced:l},{reduce:function(e){var t=arguments.length;return s(this,e,t,t>1?arguments[1]:void 0)}})},"14d9":function(e,t,a){"use strict";var o=a("23e7"),s=a("7b0b"),i=a("07fa"),n=a("3a34"),r=a("3511"),c=a("d039"),l=c((function(){return 4294967297!==[].push.call({length:4294967296},1)})),h=function(){try{Object.defineProperty([],"length",{writable:!1}).push()}catch(e){return e instanceof TypeError}},d=l||!h();o({target:"Array",proto:!0,arity:1,forced:d},{push:function(e){var t=s(this),a=i(t),o=arguments.length;r(a+o);for(var c=0;c=4)return!1;for(m=e.parentType,e.parentType="paragraph";p3)){if(e.sCount[p]>=e.blkIndent&&(c=e.bMarks[p]+e.tShift[p],l=e.eMarks[p],c=l)))){h=61===d?1:2;break}if(!(e.sCount[p]<0)){for(s=!1,i=0,n=u.length;i\x00-\x20]*)$/;e.exports=function(e,t){var a,i,n,r,c,l,h=e.pos;if(60!==e.src.charCodeAt(h))return!1;for(c=e.pos,l=e.posMax;;){if(++h>=l)return!1;if(r=e.src.charCodeAt(h),60===r)return!1;if(62===r)break}return a=e.src.slice(c+1,h),s.test(a)?(i=e.md.normalizeLink(a),!!e.md.validateLink(i)&&(t||(n=e.push("link_open","a",1),n.attrs=[["href",i]],n.markup="autolink",n.info="auto",n=e.push("text","",0),n.content=e.md.normalizeLinkText(a),n=e.push("link_close","a",-1),n.markup="autolink",n.info="auto"),e.pos+=a.length+2,!0)):!!o.test(a)&&(i=e.md.normalizeLink("mailto:"+a),!!e.md.validateLink(i)&&(t||(n=e.push("link_open","a",1),n.attrs=[["href",i]],n.markup="autolink",n.info="auto",n=e.push("text","",0),n.content=e.md.normalizeLinkText(a),n=e.push("link_close","a",-1),n.markup="autolink",n.info="auto"),e.pos+=a.length+2,!0))}},"2a62":function(e,t,a){"use strict";var o=a("c65b"),s=a("825a"),i=a("dc4a");e.exports=function(e,t,a){var n,r;s(e);try{if(n=i(e,"return"),!n){if("throw"===t)throw a;return a}n=o(n,e)}catch(c){r=!0,n=c}if("throw"===t)throw a;if(r)throw n;return s(n),a}},"2ae9":function(e,t){var a='This policy allows "Infrastructure Modification" actions. Infrastructure Modification describes IAM actions with "modify" capabilities, and can therefore lead to Resource Hijacking, unauthorized creation of Infrastructure, Backdoor creation, and/or modification of existing resources which can result in downtime. For example, ec2:AuthorizeSecurityGroupIngress grants the permission to add one or more inbound rules to a security group; malicious usage of this IAM action could potentially lead to downtime or unintentional exposure of compute resources.
';e.exports=a},"2b0e":function(e,t,a){"use strict";a.r(t),function(e){
+(function(e){var t={};function a(o){if(t[o])return t[o].exports;var s=t[o]={i:o,l:!1,exports:{}};return e[o].call(s.exports,s,s.exports,a),s.l=!0,s.exports}a.m=e,a.c=t,a.d=function(e,t,o){a.o(e,t)||Object.defineProperty(e,t,{enumerable:!0,get:o})},a.r=function(e){"undefined"!==typeof Symbol&&Symbol.toStringTag&&Object.defineProperty(e,Symbol.toStringTag,{value:"Module"}),Object.defineProperty(e,"__esModule",{value:!0})},a.t=function(e,t){if(1&t&&(e=a(e)),8&t)return e;if(4&t&&"object"===typeof e&&e&&e.__esModule)return e;var o=Object.create(null);if(a.r(o),Object.defineProperty(o,"default",{enumerable:!0,value:e}),2&t&&"string"!=typeof e)for(var s in e)a.d(o,s,function(t){return e[t]}.bind(null,s));return o},a.n=function(e){var t=e&&e.__esModule?function(){return e["default"]}:function(){return e};return a.d(t,"a",t),t},a.o=function(e,t){return Object.prototype.hasOwnProperty.call(e,t)},a.p="",a(a.s=0)})({0:function(e,t,a){e.exports=a("5a00")},"0068":function(e,t,a){"use strict";function o(e){return Object.prototype.toString.call(e)}function s(e){return"[object String]"===o(e)}var i=Object.prototype.hasOwnProperty;function n(e,t){return i.call(e,t)}function r(e){var t=Array.prototype.slice.call(arguments,1);return t.forEach((function(t){if(t){if("object"!==typeof t)throw new TypeError(t+"must be object");Object.keys(t).forEach((function(a){e[a]=t[a]}))}})),e}function c(e,t,a){return[].concat(e.slice(0,t),a,e.slice(t+1))}function l(e){return!(e>=55296&&e<=57343)&&(!(e>=64976&&e<=65007)&&(65535!==(65535&e)&&65534!==(65535&e)&&(!(e>=0&&e<=8)&&(11!==e&&(!(e>=14&&e<=31)&&(!(e>=127&&e<=159)&&!(e>1114111)))))))}function h(e){if(e>65535){e-=65536;var t=55296+(e>>10),a=56320+(1023&e);return String.fromCharCode(t,a)}return String.fromCharCode(e)}var d=/\\([!"#$%&'()*+,\-.\/:;<=>?@[\\\]^_`{|}~])/g,m=/&([a-z#][a-z0-9]{1,31});/gi,p=new RegExp(d.source+"|"+m.source,"gi"),u=/^#((?:x[a-f0-9]{1,8}|[0-9]{1,8}))$/i,f=a("bd68");function g(e,t){var a;return n(f,t)?f[t]:35===t.charCodeAt(0)&&u.test(t)&&(a="x"===t[1].toLowerCase()?parseInt(t.slice(2),16):parseInt(t.slice(1),10),l(a))?h(a):e}function v(e){return e.indexOf("\\")<0?e:e.replace(d,"$1")}function A(e){return e.indexOf("\\")<0&&e.indexOf("&")<0?e:e.replace(p,(function(e,t,a){return t||g(e,a)}))}var P=/[&<>"]/,b=/[&<>"]/g,y={"&":"&","<":"<",">":">",'"':"""};function w(e){return y[e]}function I(e){return P.test(e)?e.replace(b,w):e}var z=/[.?*+^$[\]\\(){}|-]/g;function C(e){return e.replace(z,"\\$&")}function D(e){switch(e){case 9:case 32:return!0}return!1}function R(e){if(e>=8192&&e<=8202)return!0;switch(e){case 9:case 10:case 11:case 12:case 13:case 32:case 160:case 5760:case 8239:case 8287:case 12288:return!0}return!1}var S=a("7ca0");function _(e){return S.test(e)}function k(e){switch(e){case 33:case 34:case 35:case 36:case 37:case 38:case 39:case 40:case 41:case 42:case 43:case 44:case 45:case 46:case 47:case 58:case 59:case 60:case 61:case 62:case 63:case 64:case 91:case 92:case 93:case 94:case 95:case 96:case 123:case 124:case 125:case 126:return!0;default:return!1}}function M(e){return e=e.trim().replace(/\s+/g," "),"Ṿ"==="ẞ".toLowerCase()&&(e=e.replace(/ẞ/g,"ß")),e.toLowerCase().toUpperCase()}t.lib={},t.lib.mdurl=a("d8a6"),t.lib.ucmicro=a("d5d1"),t.assign=r,t.isString=s,t.has=n,t.unescapeMd=v,t.unescapeAll=A,t.isValidEntityCode=l,t.fromCodePoint=h,t.escapeHtml=I,t.arrayReplaceAt=c,t.isSpace=D,t.isWhiteSpace=R,t.isMdAsciiPunct=k,t.isPunctChar=_,t.escapeRE=C,t.normalizeReference=M},"04f8":function(e,t,a){"use strict";var o=a("1212"),s=a("d039"),i=a("cfe9"),n=i.String;e.exports=!!Object.getOwnPropertySymbols&&!s((function(){var e=Symbol("symbol detection");return!n(e)||!(Object(e)instanceof Symbol)||!Symbol.sham&&o&&o<41}))},"06cf":function(e,t,a){"use strict";var o=a("83ab"),s=a("c65b"),i=a("d1e7"),n=a("5c6c"),r=a("fc6a"),c=a("a04b"),l=a("1a2d"),h=a("0cfb"),d=Object.getOwnPropertyDescriptor;t.f=o?d:function(e,t){if(e=r(e),t=c(t),h)try{return d(e,t)}catch(a){}if(l(e,t))return n(!s(i.f,e,t),e[t])}},"0758":function(e,t,a){"use strict";var o=a("0068").isSpace;e.exports=function(e,t,a,s){var i,n,r,c,l=e.bMarks[t]+e.tShift[t],h=e.eMarks[t];if(e.sCount[t]-e.blkIndent>=4)return!1;if(i=e.src.charCodeAt(l),35!==i||l>=h)return!1;n=1,i=e.src.charCodeAt(++l);while(35===i&&l6||ll&&o(e.src.charCodeAt(r-1))&&(h=r),e.line=t+1,c=e.push("heading_open","h"+String(n),1),c.markup="########".slice(0,n),c.map=[t,e.line],c=e.push("inline","",0),c.content=e.src.slice(l,h).trim(),c.map=[t,e.line],c.children=[],c=e.push("heading_close","h"+String(n),-1),c.markup="########".slice(0,n)),!0)}},"07fa":function(e,t,a){"use strict";var o=a("50c4");e.exports=function(e){return o(e.length)}},"0861":function(e,t){var a='If your IAM policy does require access to those actions, you should provide an explanation. Example requirements include:
- User Role: This IAM Policy is used by an IAM Role that requires access to
* resources because human users assume this role. We have restricted the access levels appropriate to what the user needs. - Infrastructure Provisioning role: This IAM Policy is used by roles that deploy infrastructure using CloudFormation or Terraform and need administrative access by design.
- Conditions logic is in use: The Policy has access to
* resources, but the statement enforces least privilege via IAM condition statements.
While other edge cases and justifications exist, the above items are the most common justifications. For information on Common False Positive Scenarios, see the documentation here.
';e.exports=a},"08ae":function(e,t,a){"use strict";var o=a("0068"),s=a("565b"),i=a("7cc2"),n=a("a915"),r=a("7696"),c=a("4cb4"),l=a("fbcd"),h=a("d8a6"),d=a("9d88"),m={default:a("8a31"),zero:a("1caa"),commonmark:a("428d")},p=/^(vbscript|javascript|file|data):/,u=/^data:image\/(gif|png|jpeg|webp);/;function f(e){var t=e.trim().toLowerCase();return!p.test(t)||!!u.test(t)}var g=["http:","https:","mailto:"];function v(e){var t=h.parse(e,!0);if(t.hostname&&(!t.protocol||g.indexOf(t.protocol)>=0))try{t.hostname=d.toASCII(t.hostname)}catch(a){}return h.encode(h.format(t))}function A(e){var t=h.parse(e,!0);if(t.hostname&&(!t.protocol||g.indexOf(t.protocol)>=0))try{t.hostname=d.toUnicode(t.hostname)}catch(a){}return h.decode(h.format(t),h.decode.defaultChars+"%")}function P(e,t){if(!(this instanceof P))return new P(e,t);t||o.isString(e)||(t=e||{},e="default"),this.inline=new c,this.block=new r,this.core=new n,this.renderer=new i,this.linkify=new l,this.validateLink=f,this.normalizeLink=v,this.normalizeLinkText=A,this.utils=o,this.helpers=o.assign({},s),this.options={},this.configure(e),t&&this.set(t)}P.prototype.set=function(e){return o.assign(this.options,e),this},P.prototype.configure=function(e){var t,a=this;if(o.isString(e)&&(t=e,e=m[t],!e))throw new Error('Wrong `markdown-it` preset "'+t+'", check name');if(!e)throw new Error("Wrong `markdown-it` preset, can't be empty");return e.options&&a.set(e.options),e.components&&Object.keys(e.components).forEach((function(t){e.components[t].rules&&a[t].ruler.enableOnly(e.components[t].rules),e.components[t].rules2&&a[t].ruler2.enableOnly(e.components[t].rules2)})),this},P.prototype.enable=function(e,t){var a=[];Array.isArray(e)||(e=[e]),["core","block","inline"].forEach((function(t){a=a.concat(this[t].ruler.enable(e,!0))}),this),a=a.concat(this.inline.ruler2.enable(e,!0));var o=e.filter((function(e){return a.indexOf(e)<0}));if(o.length&&!t)throw new Error("MarkdownIt. Failed to enable unknown rule(s): "+o);return this},P.prototype.disable=function(e,t){var a=[];Array.isArray(e)||(e=[e]),["core","block","inline"].forEach((function(t){a=a.concat(this[t].ruler.disable(e,!0))}),this),a=a.concat(this.inline.ruler2.disable(e,!0));var o=e.filter((function(e){return a.indexOf(e)<0}));if(o.length&&!t)throw new Error("MarkdownIt. Failed to disable unknown rule(s): "+o);return this},P.prototype.use=function(e){var t=[this].concat(Array.prototype.slice.call(arguments,1));return e.apply(e,t),this},P.prototype.parse=function(e,t){if("string"!==typeof e)throw new Error("Input data should be a String");var a=new this.core.State(e,this,t);return this.core.process(a),a.tokens},P.prototype.render=function(e,t){return t=t||{},this.renderer.render(this.parse(e,t),this.options,t)},P.prototype.parseInline=function(e,t){var a=new this.core.State(e,this,t);return a.inlineMode=!0,this.core.process(a),a.tokens},P.prototype.renderInline=function(e,t){return t=t||{},this.renderer.render(this.parseInline(e,t),this.options,t)},e.exports=P},"096b":function(e,t,a){"use strict";function o(e,t,a){this.type=e,this.tag=t,this.attrs=null,this.map=null,this.nesting=a,this.level=0,this.children=null,this.content="",this.markup="",this.info="",this.meta=null,this.block=!1,this.hidden=!1}o.prototype.attrIndex=function(e){var t,a,o;if(!this.attrs)return-1;for(t=this.attrs,a=0,o=t.length;a=0&&(a=this.attrs[t][1]),a},o.prototype.attrJoin=function(e,t){var a=this.attrIndex(e);a<0?this.attrPush([e,t]):this.attrs[a][1]=this.attrs[a][1]+" "+t},e.exports=o},"097b":function(e,t,a){"use strict";var o=a("096b"),s=a("0068").isWhiteSpace,i=a("0068").isPunctChar,n=a("0068").isMdAsciiPunct;function r(e,t,a,o){this.src=e,this.env=a,this.md=t,this.tokens=o,this.tokens_meta=Array(o.length),this.pos=0,this.posMax=this.src.length,this.level=0,this.pending="",this.pendingLevel=0,this.cache={},this.delimiters=[],this._prev_delimiters=[],this.backticks={},this.backticksScanned=!1,this.linkLevel=0}r.prototype.pushPending=function(){var e=new o("text","",0);return e.content=this.pending,e.level=this.pendingLevel,this.tokens.push(e),this.pending="",e},r.prototype.push=function(e,t,a){this.pending&&this.pushPending();var s=new o(e,t,a),i=null;return a<0&&(this.level--,this.delimiters=this._prev_delimiters.pop()),s.level=this.level,a>0&&(this.level++,this._prev_delimiters.push(this.delimiters),this.delimiters=[],i={delimiters:this.delimiters}),this.pendingLevel=this.level,this.tokens.push(s),this.tokens_meta.push(i),s},r.prototype.scanDelims=function(e,t){var a,o,r,c,l,h,d,m,p,u=e,f=!0,g=!0,v=this.posMax,A=this.src.charCodeAt(e);a=e>0?this.src.charCodeAt(e-1):32;while(u0&&o[0]<4?1:+(o[0]+o[1])),!s&&n&&(o=n.match(/Edge\/(\d+)/),(!o||o[1]>=74)&&(o=n.match(/Chrome\/(\d+)/),o&&(s=+o[1]))),e.exports=s},1357:function(e,t){var a='This policy contains actions that could lead to Credentials Exposure. These actions return credentials as part of the API response, such as ecr:GetAuthorizationToken, iam:UpdateAccessKey, and others. The full list is maintained here.
';e.exports=a},"13d2":function(e,t,a){"use strict";var o=a("e330"),s=a("d039"),i=a("1626"),n=a("1a2d"),r=a("83ab"),c=a("5e77").CONFIGURABLE,l=a("8925"),h=a("69f3"),d=h.enforce,m=h.get,p=String,u=Object.defineProperty,f=o("".slice),g=o("".replace),v=o([].join),A=r&&!s((function(){return 8!==u((function(){}),"length",{value:8}).length})),P=String(String).split("String"),b=e.exports=function(e,t,a){"Symbol("===f(p(t),0,7)&&(t="["+g(p(t),/^Symbol\(([^)]*)\).*$/,"$1")+"]"),a&&a.getter&&(t="get "+t),a&&a.setter&&(t="set "+t),(!n(e,"name")||c&&e.name!==t)&&(r?u(e,"name",{value:t,configurable:!0}):e.name=t),A&&a&&n(a,"arity")&&e.length!==a.arity&&u(e,"length",{value:a.arity});try{a&&n(a,"constructor")&&a.constructor?r&&u(e,"prototype",{writable:!1}):e.prototype&&(e.prototype=void 0)}catch(s){}var o=d(e);return n(o,"source")||(o.source=v(P,"string"==typeof t?t:"")),e};Function.prototype.toString=b((function(){return i(this)&&m(this).source||l(this)}),"toString")},"13d5":function(e,t,a){"use strict";var o=a("23e7"),s=a("d58f").left,i=a("a640"),n=a("1212"),r=a("9adc"),c=!r&&n>79&&n<83,l=c||!i("reduce");o({target:"Array",proto:!0,forced:l},{reduce:function(e){var t=arguments.length;return s(this,e,t,t>1?arguments[1]:void 0)}})},"14d9":function(e,t,a){"use strict";var o=a("23e7"),s=a("7b0b"),i=a("07fa"),n=a("3a34"),r=a("3511"),c=a("d039"),l=c((function(){return 4294967297!==[].push.call({length:4294967296},1)})),h=function(){try{Object.defineProperty([],"length",{writable:!1}).push()}catch(e){return e instanceof TypeError}},d=l||!h();o({target:"Array",proto:!0,arity:1,forced:d},{push:function(e){var t=s(this),a=i(t),o=arguments.length;r(a+o);for(var c=0;c=4)return!1;for(m=e.parentType,e.parentType="paragraph";p3)){if(e.sCount[p]>=e.blkIndent&&(c=e.bMarks[p]+e.tShift[p],l=e.eMarks[p],c=l)))){h=61===d?1:2;break}if(!(e.sCount[p]<0)){for(s=!1,i=0,n=u.length;i\x00-\x20]*)$/;e.exports=function(e,t){var a,i,n,r,c,l,h=e.pos;if(60!==e.src.charCodeAt(h))return!1;for(c=e.pos,l=e.posMax;;){if(++h>=l)return!1;if(r=e.src.charCodeAt(h),60===r)return!1;if(62===r)break}return a=e.src.slice(c+1,h),s.test(a)?(i=e.md.normalizeLink(a),!!e.md.validateLink(i)&&(t||(n=e.push("link_open","a",1),n.attrs=[["href",i]],n.markup="autolink",n.info="auto",n=e.push("text","",0),n.content=e.md.normalizeLinkText(a),n=e.push("link_close","a",-1),n.markup="autolink",n.info="auto"),e.pos+=a.length+2,!0)):!!o.test(a)&&(i=e.md.normalizeLink("mailto:"+a),!!e.md.validateLink(i)&&(t||(n=e.push("link_open","a",1),n.attrs=[["href",i]],n.markup="autolink",n.info="auto",n=e.push("text","",0),n.content=e.md.normalizeLinkText(a),n=e.push("link_close","a",-1),n.markup="autolink",n.info="auto"),e.pos+=a.length+2,!0))}},"2a62":function(e,t,a){"use strict";var o=a("c65b"),s=a("825a"),i=a("dc4a");e.exports=function(e,t,a){var n,r;s(e);try{if(n=i(e,"return"),!n){if("throw"===t)throw a;return a}n=o(n,e)}catch(c){r=!0,n=c}if("throw"===t)throw a;if(r)throw n;return s(n),a}},"2ae9":function(e,t){var a='This policy allows "Infrastructure Modification" actions. Infrastructure Modification describes IAM actions with "modify" capabilities, and can therefore lead to Resource Hijacking, unauthorized creation of Infrastructure, Backdoor creation, and/or modification of existing resources which can result in downtime. For example, ec2:AuthorizeSecurityGroupIngress grants the permission to add one or more inbound rules to a security group; malicious usage of this IAM action could potentially lead to downtime or unintentional exposure of compute resources.
';e.exports=a},"2b0e":function(e,t,a){"use strict";a.r(t),function(e){
/*!
* Vue.js v2.6.14
* (c) 2014-2021 Evan You
@@ -14,7 +14,7 @@ var a=Object.freeze({});function o(e){return void 0===e||null===e}function s(e){
*
* https://github.com/linusborg/portal-vue
*
- */function o(e){return e&&"object"===typeof e&&"default"in e?e["default"]:e}Object.defineProperty(t,"__esModule",{value:!0});var s=o(a("2b0e"));function i(e){return i="function"===typeof Symbol&&"symbol"===typeof Symbol.iterator?function(e){return typeof e}:function(e){return e&&"function"===typeof Symbol&&e.constructor===Symbol&&e!==Symbol.prototype?"symbol":typeof e},i(e)}function n(e){return r(e)||c(e)||l()}function r(e){if(Array.isArray(e)){for(var t=0,a=new Array(e.length);t1&&void 0!==arguments[1]?arguments[1]:{};return e.reduce((function(e,a){var o=a.passengers[0],s="function"===typeof o?o(t):a.passengers;return e.concat(s)}),[])}function p(e,t){return e.map((function(e,t){return[t,e]})).sort((function(e,a){return t(e[1],a[1])||e[0]-a[0]})).map((function(e){return e[1]}))}function u(e,t){return t.reduce((function(t,a){return e.hasOwnProperty(a)&&(t[a]=e[a]),t}),{})}var f={},g={},v={},A=s.extend({data:function(){return{transports:f,targets:g,sources:v,trackInstances:h}},methods:{open:function(e){if(h){var t=e.to,a=e.from,o=e.passengers,i=e.order,n=void 0===i?1/0:i;if(t&&a&&o){var r={to:t,from:a,passengers:d(o),order:n},c=Object.keys(this.transports);-1===c.indexOf(t)&&s.set(this.transports,t,[]);var l=this.$_getTransportIndex(r),m=this.transports[t].slice(0);-1===l?m.push(r):m[l]=r,this.transports[t]=p(m,(function(e,t){return e.order-t.order}))}}},close:function(e){var t=arguments.length>1&&void 0!==arguments[1]&&arguments[1],a=e.to,o=e.from;if(a&&(o||!1!==t)&&this.transports[a])if(t)this.transports[a]=[];else{var s=this.$_getTransportIndex(e);if(s>=0){var i=this.transports[a].slice(0);i.splice(s,1),this.transports[a]=i}}},registerTarget:function(e,t,a){h&&(this.trackInstances&&!a&&this.targets[e]&&console.warn("[portal-vue]: Target ".concat(e," already exists")),this.$set(this.targets,e,Object.freeze([t])))},unregisterTarget:function(e){this.$delete(this.targets,e)},registerSource:function(e,t,a){h&&(this.trackInstances&&!a&&this.sources[e]&&console.warn("[portal-vue]: source ".concat(e," already exists")),this.$set(this.sources,e,Object.freeze([t])))},unregisterSource:function(e){this.$delete(this.sources,e)},hasTarget:function(e){return!(!this.targets[e]||!this.targets[e][0])},hasSource:function(e){return!(!this.sources[e]||!this.sources[e][0])},hasContentFor:function(e){return!!this.transports[e]&&!!this.transports[e].length},$_getTransportIndex:function(e){var t=e.to,a=e.from;for(var o in this.transports[t])if(this.transports[t][o].from===a)return+o;return-1}}}),P=new A(f),b=1,y=s.extend({name:"portal",props:{disabled:{type:Boolean},name:{type:String,default:function(){return String(b++)}},order:{type:Number,default:0},slim:{type:Boolean},slotProps:{type:Object,default:function(){return{}}},tag:{type:String,default:"DIV"},to:{type:String,default:function(){return String(Math.round(1e7*Math.random()))}}},created:function(){var e=this;this.$nextTick((function(){P.registerSource(e.name,e)}))},mounted:function(){this.disabled||this.sendUpdate()},updated:function(){this.disabled?this.clear():this.sendUpdate()},beforeDestroy:function(){P.unregisterSource(this.name),this.clear()},watch:{to:function(e,t){t&&t!==e&&this.clear(t),this.sendUpdate()}},methods:{clear:function(e){var t={from:this.name,to:e||this.to};P.close(t)},normalizeSlots:function(){return this.$scopedSlots.default?[this.$scopedSlots.default]:this.$slots.default},normalizeOwnChildren:function(e){return"function"===typeof e?e(this.slotProps):e},sendUpdate:function(){var e=this.normalizeSlots();if(e){var t={from:this.name,to:this.to,passengers:n(e),order:this.order};P.open(t)}else this.clear()}},render:function(e){var t=this.$slots.default||this.$scopedSlots.default||[],a=this.tag;return t&&this.disabled?t.length<=1&&this.slim?this.normalizeOwnChildren(t)[0]:e(a,[this.normalizeOwnChildren(t)]):this.slim?e():e(a,{class:{"v-portal":!0},style:{display:"none"},key:"v-portal-placeholder"})}}),w=s.extend({name:"portalTarget",props:{multiple:{type:Boolean,default:!1},name:{type:String,required:!0},slim:{type:Boolean,default:!1},slotProps:{type:Object,default:function(){return{}}},tag:{type:String,default:"div"},transition:{type:[String,Object,Function]}},data:function(){return{transports:P.transports,firstRender:!0}},created:function(){var e=this;this.$nextTick((function(){P.registerTarget(e.name,e)}))},watch:{ownTransports:function(){this.$emit("change",this.children().length>0)},name:function(e,t){P.unregisterTarget(t),P.registerTarget(e,this)}},mounted:function(){var e=this;this.transition&&this.$nextTick((function(){e.firstRender=!1}))},beforeDestroy:function(){P.unregisterTarget(this.name)},computed:{ownTransports:function(){var e=this.transports[this.name]||[];return this.multiple?e:0===e.length?[]:[e[e.length-1]]},passengers:function(){return m(this.ownTransports,this.slotProps)}},methods:{children:function(){return 0!==this.passengers.length?this.passengers:this.$scopedSlots.default?this.$scopedSlots.default(this.slotProps):this.$slots.default||[]},noWrapper:function(){var e=this.slim&&!this.transition;return e&&this.children().length>1&&console.warn("[portal-vue]: PortalTarget with `slim` option received more than one child element."),e}},render:function(e){var t=this.noWrapper(),a=this.children(),o=this.transition||this.tag;return t?a[0]:this.slim&&!o?e():e(o,{props:{tag:this.transition&&this.tag?this.tag:void 0},class:{"vue-portal-target":!0}},a)}}),I=0,z=["disabled","name","order","slim","slotProps","tag","to"],C=["multiple","transition"],D=s.extend({name:"MountingPortal",inheritAttrs:!1,props:{append:{type:[Boolean,String]},bail:{type:Boolean},mountTo:{type:String,required:!0},disabled:{type:Boolean},name:{type:String,default:function(){return"mounted_"+String(I++)}},order:{type:Number,default:0},slim:{type:Boolean},slotProps:{type:Object,default:function(){return{}}},tag:{type:String,default:"DIV"},to:{type:String,default:function(){return String(Math.round(1e7*Math.random()))}},multiple:{type:Boolean,default:!1},targetSlim:{type:Boolean},targetSlotProps:{type:Object,default:function(){return{}}},targetTag:{type:String,default:"div"},transition:{type:[String,Object,Function]}},created:function(){if("undefined"!==typeof document){var e=document.querySelector(this.mountTo);if(e){var t=this.$props;if(P.targets[t.name])t.bail?console.warn("[portal-vue]: Target ".concat(t.name," is already mounted.\n Aborting because 'bail: true' is set")):this.portalTarget=P.targets[t.name];else{var a=t.append;if(a){var o="string"===typeof a?a:"DIV",s=document.createElement(o);e.appendChild(s),e=s}var i=u(this.$props,C);i.slim=this.targetSlim,i.tag=this.targetTag,i.slotProps=this.targetSlotProps,i.name=this.to,this.portalTarget=new w({el:e,parent:this.$parent||this,propsData:i})}}else console.error("[portal-vue]: Mount Point '".concat(this.mountTo,"' not found in document"))}},beforeDestroy:function(){var e=this.portalTarget;if(this.append){var t=e.$el;t.parentNode.removeChild(t)}e.$destroy()},render:function(e){if(!this.portalTarget)return console.warn("[portal-vue] Target wasn't mounted"),e();if(!this.$scopedSlots.manual){var t=u(this.$props,z);return e(y,{props:t,attrs:this.$attrs,on:this.$listeners,scopedSlots:this.$scopedSlots},this.$slots.default)}var a=this.$scopedSlots.manual({to:this.to});return Array.isArray(a)&&(a=a[0]),a||e()}});function R(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};e.component(t.portalName||"Portal",y),e.component(t.portalTargetName||"PortalTarget",w),e.component(t.MountingPortalName||"MountingPortal",D)}var S={install:R};t.default=S,t.Portal=y,t.PortalTarget=w,t.MountingPortal=D,t.Wormhole=P},"32bf":function(e,t,a){"use strict";e.exports=function(e){var t,a,o=0,s=e.tokens,i=e.tokens.length;for(t=a=0;t0&&o++,"text"===s[t].type&&t+1s)throw o("Maximum allowed index exceeded");return e}},"384f":function(e,t,a){"use strict";var o=a("e330"),s=a("5388"),i=a("cb27"),n=i.Set,r=i.proto,c=o(r.forEach),l=o(r.keys),h=l(new n).next;e.exports=function(e,t,a){return a?s({iterator:l(e),next:h},t):c(e,t)}},"395e":function(e,t,a){"use strict";var o=a("dc19"),s=a("cb27").has,i=a("8e16"),n=a("7f65"),r=a("5388"),c=a("2a62");e.exports=function(e){var t=o(this),a=n(e);if(i(t)=0&&32===e.pending.charCodeAt(a))if(a>=1&&32===e.pending.charCodeAt(a-1)){i=a-1;while(i>=1&&32===e.pending.charCodeAt(i-1))i--;e.pending=e.pending.slice(0,i),e.push("hardbreak","br",0)}else e.pending=e.pending.slice(0,-1),e.push("softbreak","br",0);else e.push("softbreak","br",0);n++;while(n3)&&!(e.sCount[l]<0)){for(s=!1,i=0,n=h.length;ia.parts.length&&(o.parts.length=a.parts.length)}else{var n=[];for(s=0;s=n)return-1;if(a=e.src.charCodeAt(i++),a<48||a>57)return-1;for(;;){if(i>=n)return-1;if(a=e.src.charCodeAt(i++),!(a>=48&&a<=57)){if(41===a||46===a)break;return-1}if(i-s>=10)return-1}return i=4)return!1;if(e.listIndent>=0&&e.sCount[x]-e.listIndent>=4&&e.sCount[x]=e.blkIndent&&(B=!0),(S=i(e,x))>=0){if(p=!0,k=e.bMarks[x]+e.tShift[x],P=Number(e.src.slice(k,S-1)),B&&1!==P)return!1}else{if(!((S=s(e,x))>=0))return!1;p=!1}if(B&&e.skipSpaces(S)>=e.eMarks[x])return!1;if(o)return!0;A=e.src.charCodeAt(S-1),v=e.tokens.length,p?(V=e.push("ordered_list_open","ol",1),1!==P&&(V.attrs=[["start",P]])):V=e.push("bullet_list_open","ul",1),V.map=g=[x,0],V.markup=String.fromCharCode(A),_=!1,T=e.md.block.ruler.getRules("list"),I=e.parentType,e.parentType="list";while(x=b?1:y-m,d>4&&(d=1),h=m+d,V=e.push("list_item_open","li",1),V.markup=String.fromCharCode(A),V.map=u=[x,0],p&&(V.info=e.src.slice(k,S-1)),D=e.tight,C=e.tShift[x],z=e.sCount[x],w=e.listIndent,e.listIndent=e.blkIndent,e.blkIndent=h,e.tight=!0,e.tShift[x]=c-e.bMarks[x],e.sCount[x]=y,c>=b&&e.isEmpty(x+1)?e.line=Math.min(e.line+2,a):e.md.block.tokenize(e,x,a,!0),e.tight&&!_||(L=!1),_=e.line-x>1&&e.isEmpty(e.line-1),e.blkIndent=e.listIndent,e.listIndent=w,e.tShift[x]=C,e.sCount[x]=z,e.tight=D,V=e.push("list_item_close","li",-1),V.markup=String.fromCharCode(A),x=e.line,u[1]=x,x>=a)break;if(e.sCount[x]=4)break;for(M=!1,l=0,f=T.length;l=e.pos)throw new Error("inline rule didn't increment state.pos");break}}else e.pos=e.posMax;t||e.pos++,r[o]=e.pos}else e.pos=r[o]},n.prototype.tokenize=function(e){var t,a,o,s=this.ruler.getRules(""),i=s.length,n=e.posMax,r=e.md.options.maxNesting;while(e.pos=e.pos)throw new Error("inline rule didn't increment state.pos");break}if(t){if(e.pos>=n)break}else e.pending+=e.src[e.pos++]}e.pending&&e.pushPending()},n.prototype.parse=function(e,t,a,o){var s,i,n,r=new this.State(e,t,a,o);for(this.tokenize(r),i=this.ruler2.getRules(""),n=i.length,s=0;sh)if(l=r[h++],l!==l)return!0}else for(;c>h;h++)if((e||h in r)&&r[h]===a)return e||h||0;return!e&&-1}};e.exports={includes:n(!0),indexOf:n(!1)}},"4fc2":function(e,t){e.exports=/[ \xA0\u1680\u2000-\u200A\u2028\u2029\u202F\u205F\u3000]/},5095:function(e,t,a){var o=a("24fb");t=o(!1),t.push([e.i,"#main{font-family:Avenir,Helvetica,Arial,sans-serif;-webkit-font-smoothing:antialiased;-moz-osx-font-smoothing:grayscale;text-align:left;color:#2c3e50}.router-link-exact-active{font-weight:700}",""]),e.exports=t},"50c4":function(e,t,a){"use strict";var o=a("5926"),s=Math.min;e.exports=function(e){var t=o(e);return t>0?s(t,9007199254740991):0}},"52d9":function(e,t,a){"use strict";a("14d9");let o=a("fd5f"),s=a("f230"),i=a("54d2");function n(e,t,a){return"role"===a.toLowerCase()?e["roles"][t]:"group"===a.toLowerCase()?e["groups"][t]:"user"===a.toLowerCase()?e["users"][t]:void 0}function r(e,t){let a=[];if("role"===t.toLowerCase()){let t=Object.keys(e["roles"]);for(let o of t)a.push(e["roles"][o]["name"]);return a.sort()}if("group"===t.toLowerCase()){let t=Object.keys(e["groups"]);for(let o of t)a.push(e["groups"][o]["name"]);return a.sort(),a}if("user"===t.toLowerCase()){let t=Object.keys(e["users"]);for(let o of t)a.push(e["users"][o]["name"]);return a.sort(),a}}function c(e,t){let a;return"role"===t.toLowerCase()?(a=Object.keys(e["roles"]),a.sort()):"group"===t.toLowerCase()?(a=Object.keys(e["groups"]),a.sort(),a):"user"===t.toLowerCase()?(a=Object.keys(e["users"]),a.sort(),a):void 0}function l(e,t,a,o){let s,i;"role"===a.toLowerCase()?s="roles":"group"===a.toLowerCase()?s="groups":"user"===a.toLowerCase()&&(s="users"),"inline"===o.toLowerCase()?i="inline_policies":"Customer"===o?i="customer_managed_policies":"AWS"===o&&(i="aws_managed_policies");let n=e[s][t][i],r=Array.from(Object.keys(n));return r.sort(),r}function h(e,t,a,i){let n,r=[],c=l(e,t,a,i);if("inline"===i.toLowerCase())for(n in c)r.push(o.getInlinePolicy(e,c[n])["PolicyName"]);else if("AWS"===i)for(n in c)r.push(s.getManagedPolicyName(e,"AWS",c[n]));else if("Customer"===i)for(n in c)r.push(s.getManagedPolicyName(e,"Customer",c[n]));return r.sort(),r}function d(e,t,a,n){let r=l(e,t,a,"Inline"),c=l(e,t,a,"Customer"),h=l(e,t,a,"AWS"),d=[];if(r.length>0){let t;for(t of r){let a,s=o.getInlinePolicyFindings(e,t,n);for(a of s)a in d||d.push(a)}}if(c.length>0){let t;for(t of c){let a,o=s.getManagedPolicyFindings(e,"Customer",t,n);for(a of o)a in d||d.push(a)}}if(h.length>0){let t;for(t of h){let a,o=s.getManagedPolicyFindings(e,"AWS",t,n);for(a of o)a in d||d.push(a)}}return d.length>0?(d.sort(),d=i.removeDuplicatesFromArray(d),d):[]}t.getPrincipalMetadata=n,t.getPrincipalNames=r,t.getPrincipalIds=c,t.getPrincipalPolicies=l,t.getRiskAssociatedWithPrincipal=d,t.getPrincipalPolicyNames=h},5388:function(e,t,a){"use strict";var o=a("c65b");e.exports=function(e,t,a){var s,i,n=a?e:e.iterator,r=e.next;while(!(s=o(r,n)).done)if(i=t(s.value),void 0!==i)return i}},"54d2":function(e,t,a){"use strict";a("14d9");const o=e=>{let[t,a,o,s,i]=Array(5).fill(0);return Object.keys(e).forEach(n=>{e[n]["PrivilegeEscalation"]["findings"].length>0&&(t+=1),e[n]["DataExfiltration"]["findings"].length>0&&(a+=1),e[n]["ResourceExposure"]["findings"].length>0&&(o+=1),e[n]["InfrastructureModification"]["findings"].length>0&&(s+=1),e[n]["CredentialsExposure"]["findings"].length>0&&(i+=1)}),{PrivilegeEscalation:t,DataExfiltration:a,ResourceExposure:o,CredentialsExposure:i,InfrastructureModification:s}};function s(e){return e=e.replace(/([a-z])([A-Z])/g,"$1 $2"),e=e.replace(/([A-Z])([A-Z][a-z])/g,"$1 $2"),e}function i(e){const t=e=>e&&e.match(/[A-Z]{2,}(?=[A-Z][a-z]+[0-9]*|\b)|[A-Z]?[a-z]+[0-9]*|[A-Z]|[0-9]+/g).map(e=>e.toLowerCase()).join("_");return t(e)}function n(e){const t=e=>e&&e.match(/[A-Z]{2,}(?=[A-Z][a-z]+[0-9]*|\b)|[A-Z]?[a-z]+[0-9]*|[A-Z]|[0-9]+/g).map(e=>e.toLowerCase()).join("-");return t(e)}function r(e){const t=e=>e&&e.match(/[A-Z]{2,}(?=[A-Z][a-z]+[0-9]*|\b)|[A-Z]?[a-z]+[0-9]*|[A-Z]|[0-9]+/g).map(e=>e.charAt(0).toUpperCase()+e.slice(1)).join(" ");return t(e)}function c(e){let t=[];return e.forEach(e=>{t.includes(e)||t.push(e)}),t}function l(e,t="asc"){return function(a,o){if(!a.hasOwnProperty(e)||!o.hasOwnProperty(e))return 0;const s="string"===typeof a[e]?a[e].toUpperCase():a[e],i="string"===typeof o[e]?o[e].toUpperCase():o[e];let n=0;return s>i?n=1:s{const a=e.length<=h?String(e):String(e).slice(-h);return t?`${t}.${a.toLowerCase()}`:a.toLowerCase()};function m(e,t){let a={},o=e.links;for(let s=0;s`\\x00-\\x20]+",i="'[^']*'",n='"[^"]*"',r="(?:"+s+"|"+i+"|"+n+")",c="(?:\\s+"+o+"(?:\\s*=\\s*"+r+")?)",l="<[A-Za-z][A-Za-z0-9\\-]*"+c+"*\\s*\\/?>",h="<\\/[A-Za-z][A-Za-z0-9\\-]*\\s*>",d="\x3c!----\x3e|\x3c!--(?:-?[^>-])(?:-?[^-])*--\x3e",m="<[?][\\s\\S]*?[?]>",p="]*>",u="",f=new RegExp("^(?:"+l+"|"+h+"|"+d+"|"+m+"|"+p+"|"+u+")"),g=new RegExp("^(?:"+l+"|"+h+")");e.exports.HTML_TAG_RE=f,e.exports.HTML_OPEN_CLOSE_TAG_RE=g},5926:function(e,t,a){"use strict";var o=a("b42e");e.exports=function(e){var t=+e;return t!==t||0===t?0:o(t)}},"59ed":function(e,t,a){"use strict";var o=a("1626"),s=a("0d51"),i=TypeError;e.exports=function(e){if(o(e))return e;throw new i(s(e)+" is not a function")}},"5a00":function(e,t,a){"use strict";a.r(t);var o=a("2b0e"),s=function(){var e=this,t=e.$createElement,a=e._self._c||t;return a("div",{attrs:{id:"main"}},[a("b-navbar",{attrs:{toggleable:"md",variant:"faded"}},[a("b-navbar-brand",{attrs:{to:"/summary"}},[e._v(" Cloudsplaining ")]),a("b-navbar-toggle",{attrs:{target:"nav-collapse"}}),a("b-collapse",{attrs:{id:"nav-collapse","is-nav":""}},[a("b-navbar-nav",[a("b-nav-item",{attrs:{to:"/customer-policies"}},[e._v("Customer Policies")]),a("b-nav-item",{attrs:{to:"/inline-policies"}},[e._v("Inline Policies")]),a("b-nav-item",{attrs:{to:"/aws-policies"}},[e._v("AWS Policies")]),a("b-nav-item",{attrs:{to:"/iam-principals"}},[e._v("IAM Principals")]),a("b-nav-item",{attrs:{to:"/guidance"}},[e._v("Guidance")]),a("b-nav-item",{attrs:{to:"/appendices"}},[e._v("Appendices")])],1),a("b-navbar-nav",{staticClass:"ml-auto"},[a("b-nav-text",[a("strong",[e._v("Account ID:")]),e._v(" "+e._s(e.account_id)+" | "),a("strong",[e._v("Account Name:")]),e._v(" "+e._s(e.account_name))])],1)],1)],1),a("b-container",{staticClass:"mt-3 pb-3 report"},[a("b-tabs",{attrs:{"nav-class":"d-none"}},[a("router-view")],1)],1),a("b-container",[a("b-row",{staticClass:"mt-5"},[a("b-col",{staticClass:"text-center text-muted"},[e._v(" Report Generated: "+e._s(e.report_generated_time)+" ⋄ Cloudsplaining version: "),a("b-link",{attrs:{href:"https://github.com/salesforce/cloudsplaining"}},[e._v(e._s(e.cloudsplaining_version))])],1)],1)],1)],1)},i=[];const n=a("f230"),r=a("fd5f"),c=a("87dd"),l=a("5e81");function h(e){return n.getManagedPolicyNameMapping(iam_data,e)}function d(){return r.getInlinePolicyNameMapping(iam_data)}function m(e){return c.getTaskTableMapping(iam_data,e)}console.log("process.env.NODE_ENV: production"),!0===isLocalExample?(console.log("isLocalExample is set to: "+isLocalExample),console.log("process.env.NODE_ENV: production"),console.log("Note: a report generated with the Python template will not have isLocalExample set to True, because that uses a separate template.html file, which has isLocalExample set to False."),iam_data=l.sample_iam_data,console.log("IAM Data keys inside the development if statement: "+Object.keys(iam_data)),account_id="12345678912",account_name="example",report_generated_time="2020-09-01",cloudsplaining_version="0.2.2"):console.log("isLocalExample is set to: "+isLocalExample),console.log("IAM Data keys outside of the NODE_ENV if statements: "+Object.keys(iam_data));var p={name:"App",mounted:function(){setTimeout(()=>this.scrollFix(this.$route.hash),1)},data(){return{sharedState:iam_data,account_id:account_id,account_name:account_name,report_generated_time:report_generated_time,cloudsplaining_version:cloudsplaining_version}},computed:{iam_data(){return this.sharedState}},methods:{getManagedPolicyNameMapping:function(e){return h(e)},getInlinePolicyNameMapping:function(){return d()},getTaskTableMapping:function(e){return m(e)},scrollFix:function(e){location.hash=e}},provide(){return{iam_data:this.iam_data,getManagedPolicyNameMapping:this.getManagedPolicyNameMapping,getInlinePolicyNameMapping:this.getInlinePolicyNameMapping}}},u=p;a("e877");function f(e,t,a,o,s,i,n,r){var c,l="function"===typeof e?e.options:e;if(t&&(l.render=t,l.staticRenderFns=a,l._compiled=!0),o&&(l.functional=!0),i&&(l._scopeId="data-v-"+i),n?(c=function(e){e=e||this.$vnode&&this.$vnode.ssrContext||this.parent&&this.parent.$vnode&&this.parent.$vnode.ssrContext,e||"undefined"===typeof __VUE_SSR_CONTEXT__||(e=__VUE_SSR_CONTEXT__),s&&s.call(this,e),e&&e._registeredComponents&&e._registeredComponents.add(n)},l._ssrRegister=c):s&&(c=r?function(){s.call(this,(l.functional?this.parent:this).$root.$options.shadowRoot)}:s),c)if(l.functional){l._injectStyles=c;var h=l.render;l.render=function(e,t){return c.call(t),h(e,t)}}else{var d=l.beforeCreate;l.beforeCreate=d?[].concat(d,c):[c]}return{exports:e,options:l}}var g=f(u,s,i,!1,null,null,null),v=g.exports,A="undefined"!==typeof window,P="undefined"!==typeof document,b="undefined"!==typeof navigator,y="undefined"!==typeof Promise,w="undefined"!==typeof MutationObserver||"undefined"!==typeof WebKitMutationObserver||"undefined"!==typeof MozMutationObserver,I=A&&P&&b,z=A?window:{},C=P?document:{},D=b?navigator:{},R=(D.userAgent||"").toLowerCase(),S=R.indexOf("jsdom")>0,_=(/msie|trident/.test(R),function(){var e=!1;if(I)try{var t={get passive(){e=!0}};z.addEventListener("test",t,t),z.removeEventListener("test",t,t)}catch(a){e=!1}return e}()),k=I&&("ontouchstart"in C.documentElement||D.maxTouchPoints>0),M=I&&Boolean(z.PointerEvent||z.MSPointerEvent),T=I&&"IntersectionObserver"in z&&"IntersectionObserverEntry"in z&&"intersectionRatio"in z.IntersectionObserverEntry.prototype,V="BvConfig",x="$bvConfig",B=["xs","sm","md","lg","xl"],L=/\[(\d+)]/g,O=/^(BV?)/,E=/^\d+$/,U=/^\..+/,F=/^#/,H=/^#[A-Za-z]+[\w\-:.]*$/,j=/(<([^>]+)>)/gi,G=/\B([A-Z])/g,W=/([a-z])([A-Z])/g,N=/^[0-9]*\.?[0-9]+$/,$=/\+/g,q=/[-/\\^$*+?.()|[\]{}]/g,J=/[\s\uFEFF\xA0]+/g,K=/\s+/,Q=/\/\*$/,Y=/(\s|^)(\w)/g,X=/^\s+/,Z=/_/g,ee=/-(\w)/g,te=/^\d+-\d\d?-\d\d?(?:\s|T|$)/,ae=/-|\s|T/,oe=/^([0-1]?[0-9]|2[0-3]):[0-5]?[0-9](:[0-5]?[0-9])?$/,se=/^.*(#[^#]+)$/,ie=/%2C/g,ne=/[!'()*]/g,re=/^(\?|#|&)/,ce=/^\d+(\.\d*)?[/:]\d+(\.\d*)?$/,le=/[/:]/,he=/^col-/,de=/^BIcon/,me=/-u-.+/;function pe(e){return pe="function"==typeof Symbol&&"symbol"==typeof Symbol.iterator?function(e){return typeof e}:function(e){return e&&"function"==typeof Symbol&&e.constructor===Symbol&&e!==Symbol.prototype?"symbol":typeof e},pe(e)}function ue(e,t){if(!(e instanceof t))throw new TypeError("Cannot call a class as a function")}function fe(e,t){if("function"!==typeof t&&null!==t)throw new TypeError("Super expression must either be null or a function");Object.defineProperty(e,"prototype",{value:Object.create(t&&t.prototype,{constructor:{value:e,writable:!0,configurable:!0}}),writable:!1}),t&&Ie(e,t)}function ge(e){var t=ye();return function(){var a,o=ze(e);if(t){var s=ze(this).constructor;a=Reflect.construct(o,arguments,s)}else a=o.apply(this,arguments);return ve(this,a)}}function ve(e,t){if(t&&("object"===pe(t)||"function"===typeof t))return t;if(void 0!==t)throw new TypeError("Derived constructors may only return object or undefined");return Ae(e)}function Ae(e){if(void 0===e)throw new ReferenceError("this hasn't been initialised - super() hasn't been called");return e}function Pe(e){var t="function"===typeof Map?new Map:void 0;return Pe=function(e){if(null===e||!we(e))return e;if("function"!==typeof e)throw new TypeError("Super expression must either be null or a function");if("undefined"!==typeof t){if(t.has(e))return t.get(e);t.set(e,a)}function a(){return be(e,arguments,ze(this).constructor)}return a.prototype=Object.create(e.prototype,{constructor:{value:a,enumerable:!1,writable:!0,configurable:!0}}),Ie(a,e)},Pe(e)}function be(e,t,a){return be=ye()?Reflect.construct:function(e,t,a){var o=[null];o.push.apply(o,t);var s=Function.bind.apply(e,o),i=new s;return a&&Ie(i,a.prototype),i},be.apply(null,arguments)}function ye(){if("undefined"===typeof Reflect||!Reflect.construct)return!1;if(Reflect.construct.sham)return!1;if("function"===typeof Proxy)return!0;try{return Boolean.prototype.valueOf.call(Reflect.construct(Boolean,[],(function(){}))),!0}catch(e){return!1}}function we(e){return-1!==Function.toString.call(e).indexOf("[native code]")}function Ie(e,t){return Ie=Object.setPrototypeOf||function(e,t){return e.__proto__=t,e},Ie(e,t)}function ze(e){return ze=Object.setPrototypeOf?Object.getPrototypeOf:function(e){return e.__proto__||Object.getPrototypeOf(e)},ze(e)}var Ce=A?z.Element:function(e){fe(a,e);var t=ge(a);function a(){return ue(this,a),t.apply(this,arguments)}return a}(Pe(Object)),De=A?z.HTMLElement:function(e){fe(a,e);var t=ge(a);function a(){return ue(this,a),t.apply(this,arguments)}return a}(Ce),Re=A?z.SVGElement:function(e){fe(a,e);var t=ge(a);function a(){return ue(this,a),t.apply(this,arguments)}return a}(Ce),Se=A?z.File:function(e){fe(a,e);var t=ge(a);function a(){return ue(this,a),t.apply(this,arguments)}return a}(Pe(Object));function _e(e){return _e="function"==typeof Symbol&&"symbol"==typeof Symbol.iterator?function(e){return typeof e}:function(e){return e&&"function"==typeof Symbol&&e.constructor===Symbol&&e!==Symbol.prototype?"symbol":typeof e},_e(e)}var ke=function(e){return _e(e)},Me=function(e){return Object.prototype.toString.call(e).slice(8,-1)},Te=function(e){return void 0===e},Ve=function(e){return null===e},xe=function(e){return Te(e)||Ve(e)},Be=function(e){return"function"===ke(e)},Le=function(e){return"boolean"===ke(e)},Oe=function(e){return"string"===ke(e)},Ee=function(e){return"number"===ke(e)},Ue=function(e){return N.test(String(e))},Fe=function(e){return Array.isArray(e)},He=function(e){return null!==e&&"object"===_e(e)},je=function(e){return"[object Object]"===Object.prototype.toString.call(e)},Ge=function(e){return e instanceof Date},We=function(e){return e instanceof Event},Ne=function(e){return e instanceof Se},$e=function(e){return"RegExp"===Me(e)},qe=function(e){return!xe(e)&&Be(e.then)&&Be(e.catch)};function Je(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Ke(e){for(var t=1;te.length)&&(t=e.length);for(var a=0,o=new Array(t);a1&&void 0!==arguments[1]?arguments[1]:t;return Fe(t)?t.reduce((function(t,a){return[].concat(ut(t),[e(a,a)])}),[]):je(t)?at(t).reduce((function(a,o){return mt(mt({},a),{},pt({},o,e(t[o],t[o])))}),{}):a},yt=function(e){return e},wt=function(e,t){var a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:void 0;if(t=Fe(t)?t.join("."):t,!t||!He(e))return a;if(t in e)return e[t];t=String(t).replace(L,".$1");var o=t.split(".").filter(yt);return 0===o.length?a:o.every((function(t){return He(e)&&t in e&&!xe(e=e[t])}))?e:Ve(e)?null:a},It=function(e,t){var a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:null,o=wt(e,t);return xe(o)?a:o},zt=a("938d"),Ct=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:null;Object(zt["a"])()||console.warn("[BootstrapVue warn]: ".concat(t?"".concat(t," - "):"").concat(e))},Dt=function(e){return!I&&(Ct("".concat(e,": Can not be called during SSR.")),!0)},Rt=function(e){return!y&&(Ct("".concat(e,": Requires Promise support.")),!0)},St=function(e){return!w&&(Ct("".concat(e,": Requires MutationObserver support.")),!0)};function _t(e,t){if(!(e instanceof t))throw new TypeError("Cannot call a class as a function")}function kt(e,t){for(var a=0;a0&&void 0!==arguments[0]?arguments[0]:{};if(je(t)){var a=tt(t);a.forEach((function(a){var o=t[a];"breakpoints"===a?!Fe(o)||o.length<2||o.some((function(e){return!Oe(e)||0===e.length}))?Ct('"breakpoints" must be an array of at least 2 breakpoint names',V):e.$_config[a]=bt(o):je(o)&&(e.$_config[a]=tt(o).reduce((function(e,t){return Te(o[t])||(e[t]=bt(o[t])),e}),e.$_config[a]||{}))}))}}},{key:"resetConfig",value:function(){this.$_config={}}},{key:"getConfig",value:function(){return bt(this.$_config)}},{key:"getConfigValue",value:function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:void 0;return bt(wt(this.$_config,e,t))}}]),e}(),Vt=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:{},t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:o["default"];t.prototype[x]=o["default"].prototype[x]=t.prototype[x]||o["default"].prototype[x]||new Tt,t.prototype[x].setConfig(e)};function xt(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Bt(e){for(var t=1;t0&&void 0!==arguments[0]?arguments[0]:{},t=e.components,a=e.directives,o=e.plugins,s=function e(s){var i=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};e.installed||(e.installed=!0,Ot(s),Vt(i,s),Wt(s,t),$t(s,a),jt(s,o))};return s.installed=!1,s},Ut=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:{},t=e.components,a=e.directives,o=e.plugins,s=function e(s){e.installed||(e.installed=!0,Ot(s),Wt(s,t),$t(s,a),jt(s,o))};return s.installed=!1,s},Ft=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:{},t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};return Bt(Bt({},t),{},{install:Et(e)})},Ht=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:{},t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};return Bt(Bt({},t),{},{install:Ut(e)})},jt=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};for(var a in t)a&&t[a]&&e.use(t[a])},Gt=function(e,t,a){e&&t&&a&&e.component(t,a)},Wt=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};for(var a in t)Gt(e,a,t[a])},Nt=function(e,t,a){e&&t&&a&&e.directive(t.replace(/^VB/,"B"),a)},$t=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};for(var a in t)Nt(e,a,t[a])},qt="BAlert",Jt="BAspect",Kt="BAvatar",Qt="BAvatarGroup",Yt="BBadge",Xt="BBreadcrumb",Zt="BBreadcrumbItem",ea="BBreadcrumbLink",ta="BButton",aa="BButtonClose",oa="BButtonGroup",sa="BButtonToolbar",ia="BCalendar",na="BCard",ra="BCardBody",ca="BCardFooter",la="BCardGroup",ha="BCardHeader",da="BCardImg",ma="BCardImgLazy",pa="BCardSubTitle",ua="BCardText",fa="BCardTitle",ga="BCarousel",va="BCarouselSlide",Aa="BCol",Pa="BCollapse",ba="BContainer",ya="BDropdown",wa="BDropdownDivider",Ia="BDropdownForm",za="BDropdownGroup",Ca="BDropdownHeader",Da="BDropdownItem",Ra="BDropdownItemButton",Sa="BDropdownText",_a="BEmbed",ka="BForm",Ma="BFormCheckbox",Ta="BFormCheckboxGroup",Va="BFormDatalist",xa="BFormDatepicker",Ba="BFormFile",La="BFormGroup",Oa="BFormInput",Ea="BFormInvalidFeedback",Ua="BFormRadio",Fa="BFormRadioGroup",Ha="BFormRating",ja="BFormRow",Ga="BFormSelect",Wa="BFormSelectOption",Na="BFormSelectOptionGroup",$a="BFormSpinbutton",qa="BFormTag",Ja="BFormTags",Ka="BFormText",Qa="BFormTextarea",Ya="BFormTimepicker",Xa="BFormValidFeedback",Za="BIcon",eo="BIconstack",to="BIconBase",ao="BImg",oo="BImgLazy",so="BInputGroup",io="BInputGroupAddon",no="BInputGroupAppend",ro="BInputGroupPrepend",co="BInputGroupText",lo="BJumbotron",ho="BLink",mo="BListGroup",po="BListGroupItem",uo="BMedia",fo="BMediaAside",go="BMediaBody",vo="BModal",Ao="BMsgBox",Po="BNav",bo="BNavbar",yo="BNavbarBrand",wo="BNavbarNav",Io="BNavbarToggle",zo="BNavForm",Co="BNavItem",Do="BNavItemDropdown",Ro="BNavText",So="BOverlay",_o="BPagination",ko="BPaginationNav",Mo="BPopover",To="BProgress",Vo="BProgressBar",xo="BRow",Bo="BSidebar",Lo="BSkeleton",Oo="BSkeletonIcon",Eo="BSkeletonImg",Uo="BSkeletonTable",Fo="BSkeletonWrapper",Ho="BSpinner",jo="BTab",Go="BTable",Wo="BTableCell",No="BTableLite",$o="BTableSimple",qo="BTabs",Jo="BTbody",Ko="BTfoot",Qo="BTh",Yo="BThead",Xo="BTime",Zo="BToast",es="BToaster",ts="BTooltip",as="BTr",os="BVCollapse",ss="BVFormBtnLabelControl",is="BVFormRatingStar",ns="BVPopover",rs="BVPopoverTemplate",cs="BVPopper",ls="BVTabButton",hs="BVToastPop",ds="BVTooltip",ms="BVTooltipTemplate",ps="BVTransition",us="BVTransporter",fs="BVTransporterTarget",gs=function(){return(gs=Object.assign||function(e){for(var t,a=1,o=arguments.length;a=0||Object.prototype.propertyIsEnumerable.call(e,a)&&(s[a]=e[a])}return s}function Cs(e,t){if(null==e)return{};var a,o,s={},i=Object.keys(e);for(o=0;o=0||(s[a]=e[a]);return s}function Ds(e){return Ds="function"==typeof Symbol&&"symbol"==typeof Symbol.iterator?function(e){return typeof e}:function(e){return e&&"function"==typeof Symbol&&e.constructor===Symbol&&e!==Symbol.prototype?"symbol":typeof e},Ds(e)}var Rs="_uid",Ss=o["default"].version.startsWith("3"),_s=Ss?"ref_for":"refInFor",ks=["class","staticClass","style","attrs","props","domProps","on","nativeOn","directives","scopedSlots","slot","key","ref","refInFor"],Ms=o["default"].extend.bind(o["default"]);if(Ss){var Ts=o["default"].extend,Vs=["router-link","transition","transition-group"],xs=o["default"].vModelDynamic.created,Bs=o["default"].vModelDynamic.beforeUpdate;o["default"].vModelDynamic.created=function(e,t,a){xs.call(this,e,t,a),e._assign||(e._assign=function(){})},o["default"].vModelDynamic.beforeUpdate=function(e,t,a){Bs.call(this,e,t,a),e._assign||(e._assign=function(){})},Ms=function(e){if("object"===Ds(e)&&e.render&&!e.__alreadyPatched){var t=e.render;e.__alreadyPatched=!0,e.render=function(a){var o=function(e,t,o){var s=void 0===o?[]:[Array.isArray(o)?o.filter(Boolean):o],i="string"===typeof e&&!Vs.includes(e),n=t&&"object"===Ds(t)&&!Array.isArray(t);if(!n)return a.apply(void 0,[e,t].concat(s));var r=t.attrs,c=t.props,l=zs(t,["attrs","props"]),h=ws(ws({},l),{},{attrs:r,props:i?{}:c});return"router-link"!==e||h.slots||h.scopedSlots||(h.scopedSlots={$hasNormal:function(){}}),a.apply(void 0,[e,h].concat(s))};if(e.functional){var s,i,n=arguments[1],r=ws({},n);r.data={attrs:ws({},n.data.attrs||{}),props:ws({},n.data.props||{})},Object.keys(n.data||{}).forEach((function(e){ks.includes(e)?r.data[e]=n.data[e]:e in n.props?r.data.props[e]=n.data[e]:e.startsWith("on")||(r.data.attrs[e]=n.data[e])}));var c=["_ctx"],l=(null===(s=n.children)||void 0===s||null===(i=s.default)||void 0===i?void 0:i.call(s))||n.children;return l&&0===Object.keys(r.children).filter((function(e){return!c.includes(e)})).length?delete r.children:r.children=l,r.data.on=n.listeners,t.call(this,o,r)}return t.call(this,o)}}return Ts.call(this,e)}.bind(o["default"])}var Ls=o["default"].nextTick,Os="activate-tab",Es="blur",Us="cancel",Fs="change",Hs="changed",js="click",Gs="close",Ws="context",Ns="context-changed",$s="destroyed",qs="disable",Js="disabled",Ks="dismissed",Qs="dismiss-count-down",Ys="enable",Xs="enabled",Zs="filtered",ei="first",ti="focus",ai="focusin",oi="focusout",si="head-clicked",ii="hidden",ni="hide",ri="img-error",ci="input",li="last",hi="mouseenter",di="mouseleave",mi="next",pi="ok",ui="open",fi="page-click",gi="paused",vi="prev",Ai="refresh",Pi="refreshed",bi="remove",yi="row-clicked",wi="row-contextmenu",Ii="row-dblclicked",zi="row-hovered",Ci="row-middle-clicked",Di="row-selected",Ri="row-unhovered",Si="selected",_i="show",ki="shown",Mi="sliding-end",Ti="sliding-start",Vi="sort-changed",xi="tag-state",Bi="toggle",Li="unpaused",Oi="update",Ei=Ss?"vnodeBeforeUnmount":"hook:beforeDestroy",Ui=Ss?"vNodeUnmounted":"hook:destroyed",Fi="update:",Hi="bv",ji="::",Gi={passive:!0},Wi={passive:!0,capture:!1},Ni=void 0,$i=Array,qi=Boolean,Ji=Date,Ki=Function,Qi=Number,Yi=Object,Xi=RegExp,Zi=String,en=[$i,Ki],tn=[$i,Yi],an=[$i,Yi,Zi],on=[$i,Zi],sn=[qi,Qi],nn=[qi,Qi,Zi],rn=[qi,Zi],cn=[Ji,Zi],ln=[Ki,Zi],hn=[Qi,Zi],dn=[Qi,Yi,Zi],mn=[Yi,Ki],pn=[Yi,Zi],un="add-button-text",fn="append",gn="aside",vn="badge",An="bottom-row",Pn="button-content",bn="custom-foot",yn="decrement",wn="default",In="description",zn="dismiss",Cn="drop-placeholder",Dn="ellipsis-text",Rn="empty",Sn="emptyfiltered",_n="file-name",kn="first",Mn="first-text",Tn="footer",Vn="header",xn="header-close",Bn="icon-clear",Ln="icon-empty",On="icon-full",En="icon-half",Un="img",Fn="increment",Hn="invalid-feedback",jn="label",Gn="last-text",Wn="lead",Nn="loading",$n="modal-backdrop",qn="modal-cancel",Jn="modal-footer",Kn="modal-header",Qn="modal-header-close",Yn="modal-ok",Xn="modal-title",Zn="nav-next-decade",er="nav-next-month",tr="nav-next-year",ar="nav-prev-decade",or="nav-prev-month",sr="nav-prev-year",ir="nav-this-month",nr="next-text",rr="overlay",cr="page",lr="placeholder",hr="prepend",dr="prev-text",mr="row-details",pr="table-busy",ur="table-caption",fr="table-colgroup",gr="tabs-end",vr="tabs-start",Ar="text",Pr="thead-top",br="title",yr="toast-title",wr="top-row",Ir="valid-feedback",zr=function(){return Array.from.apply(Array,arguments)},Cr=function(e,t){return-1!==e.indexOf(t)},Dr=function(){for(var e=arguments.length,t=new Array(e),a=0;a1&&void 0!==arguments[1]?arguments[1]:{},a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:{};return e=Dr(e).filter(yt),e.some((function(e){return t[e]||a[e]}))},Mr=function(e){var t,a=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{},o=arguments.length>2&&void 0!==arguments[2]?arguments[2]:{},s=arguments.length>3&&void 0!==arguments[3]?arguments[3]:{};e=Dr(e).filter(yt);for(var i=0;i0&&void 0!==arguments[0]?arguments[0]:wn,t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:this.$scopedSlots,a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:this.$slots;return kr(e,t,a)},normalizeSlot:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:wn,t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{},a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:this.$scopedSlots,o=arguments.length>3&&void 0!==arguments[3]?arguments[3]:this.$slots,s=Mr(e,t,a,o);return s?Dr(s):s}}}),Vr=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:NaN,a=parseInt(e,10);return isNaN(a)?t:a},xr=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:NaN,a=parseFloat(e);return isNaN(a)?t:a},Br=function(e,t){return xr(e).toFixed(Vr(t,0))},Lr=function(e){return e.replace(G,"-$1").toLowerCase()},Or=function(e){return e=Lr(e).replace(ee,(function(e,t){return t?t.toUpperCase():""})),e.charAt(0).toUpperCase()+e.slice(1)},Er=function(e){return e.replace(Z," ").replace(W,(function(e,t,a){return t+" "+a})).replace(Y,(function(e,t,a){return t+a.toUpperCase()}))},Ur=function(e){return e=Oe(e)?e.trim():String(e),e.charAt(0).toLowerCase()+e.slice(1)},Fr=function(e){return e=Oe(e)?e.trim():String(e),e.charAt(0).toUpperCase()+e.slice(1)},Hr=function(e){return e.replace(q,"\\$&")},jr=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:2;return xe(e)?"":Fe(e)||je(e)&&e.toString===Object.prototype.toString?JSON.stringify(e,null,t):String(e)},Gr=function(e){return jr(e).replace(X,"")},Wr=function(e){return jr(e).trim()},Nr=function(e){return jr(e).toLowerCase()},$r=Ce.prototype,qr=["button","[href]:not(.disabled)","input","select","textarea","[tabindex]","[contenteditable]"].map((function(e){return"".concat(e,":not(:disabled):not([disabled])")})).join(", "),Jr=$r.matches||$r.msMatchesSelector||$r.webkitMatchesSelector,Kr=$r.closest||function(e){var t=this;do{if(cc(t,e))return t;t=t.parentElement||t.parentNode}while(!Ve(t)&&t.nodeType===Node.ELEMENT_NODE);return null},Qr=(z.requestAnimationFrame||z.webkitRequestAnimationFrame||z.mozRequestAnimationFrame||z.msRequestAnimationFrame||z.oRequestAnimationFrame||function(e){return setTimeout(e,16)}).bind(z),Yr=z.MutationObserver||z.WebKitMutationObserver||z.MozMutationObserver||null,Xr=function(e){return e&&e.parentNode&&e.parentNode.removeChild(e)},Zr=function(e){return!(!e||e.nodeType!==Node.ELEMENT_NODE)},ec=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:[],t=C.activeElement;return t&&!e.some((function(e){return e===t}))?t:null},tc=function(e,t){return jr(e).toLowerCase()===jr(t).toLowerCase()},ac=function(e){return Zr(e)&&e===ec()},oc=function(e){if(!Zr(e)||!e.parentNode||!hc(C.body,e))return!1;if("none"===yc(e,"display"))return!1;var t=wc(e);return!!(t&&t.height>0&&t.width>0)},sc=function(e){return!Zr(e)||e.disabled||Ac(e,"disabled")||uc(e,"disabled")},ic=function(e){return Zr(e)&&e.offsetHeight},nc=function(e,t){return zr((Zr(t)?t:C).querySelectorAll(e))},rc=function(e,t){return(Zr(t)?t:C).querySelector(e)||null},cc=function(e,t){return!!Zr(e)&&Jr.call(e,t)},lc=function(e,t){var a=arguments.length>2&&void 0!==arguments[2]&&arguments[2];if(!Zr(t))return null;var o=Kr.call(t,e);return a?o:o===t?null:o},hc=function(e,t){return!(!e||!Be(e.contains))&&e.contains(t)},dc=function(e){return C.getElementById(/^#/.test(e)?e.slice(1):e)||null},mc=function(e,t){t&&Zr(e)&&e.classList&&e.classList.add(t)},pc=function(e,t){t&&Zr(e)&&e.classList&&e.classList.remove(t)},uc=function(e,t){return!!(t&&Zr(e)&&e.classList)&&e.classList.contains(t)},fc=function(e,t,a){t&&Zr(e)&&e.setAttribute(t,a)},gc=function(e,t){t&&Zr(e)&&e.removeAttribute(t)},vc=function(e,t){return t&&Zr(e)?e.getAttribute(t):null},Ac=function(e,t){return t&&Zr(e)?e.hasAttribute(t):null},Pc=function(e,t,a){t&&Zr(e)&&(e.style[t]=a)},bc=function(e,t){t&&Zr(e)&&(e.style[t]="")},yc=function(e,t){return t&&Zr(e)&&e.style[t]||null},wc=function(e){return Zr(e)?e.getBoundingClientRect():null},Ic=function(e){var t=z.getComputedStyle;return t&&Zr(e)?t(e):{}},zc=function(){var e=z.getSelection;return e?z.getSelection():null},Cc=function(e){var t={top:0,left:0};if(!Zr(e)||0===e.getClientRects().length)return t;var a=wc(e);if(a){var o=e.ownerDocument.defaultView;t.top=a.top+o.pageYOffset,t.left=a.left+o.pageXOffset}return t},Dc=function(e){var t={top:0,left:0};if(!Zr(e))return t;var a={top:0,left:0},o=Ic(e);if("fixed"===o.position)t=wc(e)||t;else{t=Cc(e);var s=e.ownerDocument,i=e.offsetParent||s.documentElement;while(i&&(i===s.body||i===s.documentElement)&&"static"===Ic(i).position)i=i.parentNode;if(i&&i!==e&&i.nodeType===Node.ELEMENT_NODE){a=Cc(i);var n=Ic(i);a.top+=xr(n.borderTopWidth,0),a.left+=xr(n.borderLeftWidth,0)}}return{top:t.top-a.top-xr(o.marginTop,0),left:t.left-a.left-xr(o.marginLeft,0)}},Rc=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:document;return nc(qr,e).filter(oc).filter((function(e){return e.tabIndex>-1&&!e.disabled}))},Sc=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};try{e.focus(t)}catch(a){}return ac(e)},_c=function(e){try{e.blur()}catch(t){}return!ac(e)},kc=function(e){var t=Xe(null);return function(){for(var a=arguments.length,o=new Array(a),s=0;s1&&void 0!==arguments[1]?arguments[1]:void 0,a=Mc[x];return a?a.getConfigValue(e,t):bt(t)},Vc=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:null,a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:void 0;return t?Tc("".concat(e,".").concat(t),a):Tc(e,{})},xc=function(){return Tc("breakpoints",B)},Bc=kc((function(){return xc()})),Lc=function(){return bt(Bc())},Oc=kc((function(){var e=Lc();return e[0]="",e}));function Ec(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Uc(e){for(var t=1;t0&&void 0!==arguments[0]?arguments[0]:Ni,t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:void 0,a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:void 0,o=arguments.length>3&&void 0!==arguments[3]?arguments[3]:void 0,s=!0===a;return o=s?o:a,Uc(Uc(Uc({},e?{type:e}:{}),s?{required:s}:Te(t)?{}:{default:He(t)?function(){return t}:t}),Te(o)?{}:{validator:o})},Nc=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:yt;if(Fe(e))return e.map(t);var a={};for(var o in e)ot(e,o)&&(a[t(o)]=He(e[o])?it(e[o]):e[o]);return a},$c=function(e,t){var a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:yt;return(Fe(e)?e.slice():at(e)).reduce((function(e,o){return e[a(o)]=t[o],e}),{})},qc=function(e,t,a){return Uc(Uc({},bt(e)),{},{default:function(){var o=Vc(a,t,e.default);return Be(o)?o():o}})},Jc=function(e,t){return at(e).reduce((function(a,o){return Uc(Uc({},a),{},Fc({},o,qc(e[o],o,t)))}),{})},Kc=qc({},"","").default.name,Qc=function(e){return Be(e)&&e.name&&e.name!==Kc};function Yc(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var Xc=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{},a=t.type,o=void 0===a?Ni:a,s=t.defaultValue,i=void 0===s?void 0:s,n=t.validator,r=void 0===n?void 0:n,c=t.event,l=void 0===c?ci:c,h=Yc({},e,Wc(o,i,r)),d=Ms({model:{prop:e,event:l},props:h});return{mixin:d,props:h,prop:e,event:l}},Zc=function(e){return _?He(e)?e:{capture:!!e||!1}:!!(He(e)?e.capture:e)},el=function(e,t,a,o){e&&e.addEventListener&&e.addEventListener(t,a,Zc(o))},tl=function(e,t,a,o){e&&e.removeEventListener&&e.removeEventListener(t,a,Zc(o))},al=function(e){for(var t=e?el:tl,a=arguments.length,o=new Array(a>1?a-1:0),s=1;s1&&void 0!==arguments[1]?arguments[1]:{},a=t.preventDefault,o=void 0===a||a,s=t.propagation,i=void 0===s||s,n=t.immediatePropagation,r=void 0!==n&&n;o&&e.preventDefault(),i&&e.stopPropagation(),r&&e.stopImmediatePropagation()},sl=function(e){return Lr(e.replace(O,""))},il=function(e,t){return[Hi,sl(e),t].join(ji)},nl=function(e,t){return[Hi,t,sl(e)].join(ji)};function rl(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var cl=Jc({ariaLabel:Wc(Zi,"Close"),content:Wc(Zi,"×"),disabled:Wc(qi,!1),textVariant:Wc(Zi)},aa),ll=Ms({name:aa,functional:!0,props:cl,render:function(e,t){var a=t.props,o=t.data,s=t.slots,i=t.scopedSlots,n=s(),r=i||{},c={staticClass:"close",class:rl({},"text-".concat(a.textVariant),a.textVariant),attrs:{type:"button",disabled:a.disabled,"aria-label":a.ariaLabel?String(a.ariaLabel):null},on:{click:function(e){a.disabled&&We(e)&&ol(e)}}};return kr(wn,r,n)||(c.domProps={innerHTML:a.content}),e("button",bs(o,c),Mr(wn,{},r,n))}});function hl(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function dl(e){for(var t=1;t0?e:0)},Rl=function(e){return""===e||!0===e||!(Vr(e,0)<1)&&!!e},Sl=Jc(lt(Pl(Pl({},Il),{},{dismissLabel:Wc(Zi,"Close"),dismissible:Wc(qi,!1),fade:Wc(qi,!1),variant:Wc(Zi,"info")})),qt),_l=Ms({name:qt,mixins:[wl,Tr],props:Sl,data:function(){return{countDown:0,localShow:Rl(this[zl])}},watch:(pl={},bl(pl,zl,(function(e){this.countDown=Dl(e),this.localShow=Rl(e)})),bl(pl,"countDown",(function(e){var t=this;this.clearCountDownInterval();var a=this[zl];Ue(a)&&(this.$emit(Qs,e),a!==e&&this.$emit(Cl,e),e>0?(this.localShow=!0,this.$_countDownTimeout=setTimeout((function(){t.countDown--}),1e3)):this.$nextTick((function(){Qr((function(){t.localShow=!1}))})))})),bl(pl,"localShow",(function(e){var t=this[zl];e||!this.dismissible&&!Ue(t)||this.$emit(Ks),Ue(t)||t===e||this.$emit(Cl,e)})),pl),created:function(){this.$_filterTimer=null;var e=this[zl];this.countDown=Dl(e),this.localShow=Rl(e)},beforeDestroy:function(){this.clearCountDownInterval()},methods:{dismiss:function(){this.clearCountDownInterval(),this.countDown=0,this.localShow=!1},clearCountDownInterval:function(){clearTimeout(this.$_countDownTimeout),this.$_countDownTimeout=null}},render:function(e){var t=e();if(this.localShow){var a=this.dismissible,o=this.variant,s=e();a&&(s=e(ll,{attrs:{"aria-label":this.dismissLabel},on:{click:this.dismiss}},[this.normalizeSlot(zn)])),t=e("div",{staticClass:"alert",class:bl({"alert-dismissible":a},"alert-".concat(o),o),attrs:{role:"alert","aria-live":"polite","aria-atomic":!0},key:this[Rs]},[s,this.normalizeSlot()])}return e(vl,{props:{noFade:!this.fade}},[t])}}),kl=Ft({components:{BAlert:_l}}),Ml=Math.min,Tl=Math.max,Vl=Math.abs,xl=Math.ceil,Bl=Math.floor,Ll=Math.pow,Ol=Math.round;function El(e,t){return Gl(e)||jl(e,t)||Fl(e,t)||Ul()}function Ul(){throw new TypeError("Invalid attempt to destructure non-iterable instance.\nIn order to be iterable, non-array objects must have a [Symbol.iterator]() method.")}function Fl(e,t){if(e){if("string"===typeof e)return Hl(e,t);var a=Object.prototype.toString.call(e).slice(8,-1);return"Object"===a&&e.constructor&&(a=e.constructor.name),"Map"===a||"Set"===a?Array.from(e):"Arguments"===a||/^(?:Ui|I)nt(?:8|16|32)(?:Clamped)?Array$/.test(a)?Hl(e,t):void 0}}function Hl(e,t){(null==t||t>e.length)&&(t=e.length);for(var a=0,o=new Array(t);a0&&void 0!==arguments[0]?arguments[0]:{},t=e.target,a=e.rel;return"_blank"===t&&Ve(a)?"noopener":a||null},ih=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:{},t=e.href,a=e.to,o=arguments.length>1&&void 0!==arguments[1]?arguments[1]:Kl,s=arguments.length>2&&void 0!==arguments[2]?arguments[2]:"#",i=arguments.length>3&&void 0!==arguments[3]?arguments[3]:"/";if(t)return t;if(ah(o))return null;if(Oe(a))return a||i;if(je(a)&&(a.path||a.query||a.hash)){var n=jr(a.path),r=Zl(a.query),c=jr(a.hash);return c=c&&"#"!==c.charAt(0)?"#".concat(c):c,"".concat(n).concat(r).concat(c)||i}return s};function nh(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var rh={viewBox:"0 0 16 16",width:"1em",height:"1em",focusable:"false",role:"img","aria-label":"icon"},ch={width:null,height:null,focusable:null,role:null,"aria-label":null},lh={animation:Wc(Zi),content:Wc(Zi),flipH:Wc(qi,!1),flipV:Wc(qi,!1),fontScale:Wc(hn,1),rotate:Wc(hn,0),scale:Wc(hn,1),shiftH:Wc(hn,0),shiftV:Wc(hn,0),stacked:Wc(qi,!1),title:Wc(Zi),variant:Wc(Zi)},hh=Ms({name:to,functional:!0,props:lh,render:function(e,t){var a,o=t.data,s=t.props,i=t.children,n=s.animation,r=s.content,c=s.flipH,l=s.flipV,h=s.stacked,d=s.title,m=s.variant,p=Tl(xr(s.fontScale,1),0)||1,u=Tl(xr(s.scale,1),0)||1,f=xr(s.rotate,0),g=xr(s.shiftH,0),v=xr(s.shiftV,0),A=c||l||1!==u,P=A||f,b=g||v,y=!xe(r),w=[P?"translate(8 8)":null,A?"scale(".concat((c?-1:1)*u," ").concat((l?-1:1)*u,")"):null,f?"rotate(".concat(f,")"):null,P?"translate(-8 -8)":null].filter(yt),I=e("g",{attrs:{transform:w.join(" ")||null},domProps:y?{innerHTML:r||""}:{}},i);b&&(I=e("g",{attrs:{transform:"translate(".concat(16*g/16," ").concat(-16*v/16,")")}},[I])),h&&(I=e("g",[I]));var z=d?e("title",d):null,C=[z,I].filter(yt);return e("svg",bs({staticClass:"b-icon bi",class:(a={},nh(a,"text-".concat(m),m),nh(a,"b-icon-animation-".concat(n),n),a),attrs:rh,style:h?{}:{fontSize:1===p?null:"".concat(100*p,"%")}},o,h?{attrs:ch}:{},{attrs:{xmlns:h?null:"http://www.w3.org/2000/svg",fill:"currentColor"}}),C)}});function dh(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function mh(e){for(var t=1;t'),Ah=fh("AlarmFill",''),Ph=fh("AlignBottom",''),bh=fh("AlignCenter",''),yh=fh("AlignEnd",''),wh=fh("AlignMiddle",''),Ih=fh("AlignStart",''),zh=fh("AlignTop",''),Ch=fh("Alt",''),Dh=fh("App",''),Rh=fh("AppIndicator",''),Sh=fh("Archive",''),_h=fh("ArchiveFill",''),kh=fh("Arrow90degDown",''),Mh=fh("Arrow90degLeft",''),Th=fh("Arrow90degRight",''),Vh=fh("Arrow90degUp",''),xh=fh("ArrowBarDown",''),Bh=fh("ArrowBarLeft",''),Lh=fh("ArrowBarRight",''),Oh=fh("ArrowBarUp",''),Eh=fh("ArrowClockwise",''),Uh=fh("ArrowCounterclockwise",''),Fh=fh("ArrowDown",''),Hh=fh("ArrowDownCircle",''),jh=fh("ArrowDownCircleFill",''),Gh=fh("ArrowDownLeft",''),Wh=fh("ArrowDownLeftCircle",''),Nh=fh("ArrowDownLeftCircleFill",''),$h=fh("ArrowDownLeftSquare",''),qh=fh("ArrowDownLeftSquareFill",''),Jh=fh("ArrowDownRight",''),Kh=fh("ArrowDownRightCircle",''),Qh=fh("ArrowDownRightCircleFill",''),Yh=fh("ArrowDownRightSquare",''),Xh=fh("ArrowDownRightSquareFill",''),Zh=fh("ArrowDownShort",''),ed=fh("ArrowDownSquare",''),td=fh("ArrowDownSquareFill",''),ad=fh("ArrowDownUp",''),od=fh("ArrowLeft",''),sd=fh("ArrowLeftCircle",''),id=fh("ArrowLeftCircleFill",''),nd=fh("ArrowLeftRight",''),rd=fh("ArrowLeftShort",''),cd=fh("ArrowLeftSquare",''),ld=fh("ArrowLeftSquareFill",''),hd=fh("ArrowRepeat",''),dd=fh("ArrowReturnLeft",''),md=fh("ArrowReturnRight",''),pd=fh("ArrowRight",''),ud=fh("ArrowRightCircle",''),fd=fh("ArrowRightCircleFill",''),gd=fh("ArrowRightShort",''),vd=fh("ArrowRightSquare",''),Ad=fh("ArrowRightSquareFill",''),Pd=fh("ArrowUp",''),bd=fh("ArrowUpCircle",''),yd=fh("ArrowUpCircleFill",''),wd=fh("ArrowUpLeft",''),Id=fh("ArrowUpLeftCircle",''),zd=fh("ArrowUpLeftCircleFill",''),Cd=fh("ArrowUpLeftSquare",''),Dd=fh("ArrowUpLeftSquareFill",''),Rd=fh("ArrowUpRight",''),Sd=fh("ArrowUpRightCircle",''),_d=fh("ArrowUpRightCircleFill",''),kd=fh("ArrowUpRightSquare",''),Md=fh("ArrowUpRightSquareFill",''),Td=fh("ArrowUpShort",''),Vd=fh("ArrowUpSquare",''),xd=fh("ArrowUpSquareFill",''),Bd=fh("ArrowsAngleContract",''),Ld=fh("ArrowsAngleExpand",''),Od=fh("ArrowsCollapse",''),Ed=fh("ArrowsExpand",''),Ud=fh("ArrowsFullscreen",''),Fd=fh("ArrowsMove",''),Hd=fh("AspectRatio",''),jd=fh("AspectRatioFill",''),Gd=fh("Asterisk",''),Wd=fh("At",''),Nd=fh("Award",''),$d=fh("AwardFill",''),qd=fh("Back",''),Jd=fh("Backspace",''),Kd=fh("BackspaceFill",''),Qd=fh("BackspaceReverse",''),Yd=fh("BackspaceReverseFill",''),Xd=fh("Badge3d",''),Zd=fh("Badge3dFill",''),em=fh("Badge4k",''),tm=fh("Badge4kFill",''),am=fh("Badge8k",''),om=fh("Badge8kFill",''),sm=fh("BadgeAd",''),im=fh("BadgeAdFill",''),nm=fh("BadgeAr",''),rm=fh("BadgeArFill",''),cm=fh("BadgeCc",''),lm=fh("BadgeCcFill",''),hm=fh("BadgeHd",''),dm=fh("BadgeHdFill",''),mm=fh("BadgeTm",''),pm=fh("BadgeTmFill",''),um=fh("BadgeVo",''),fm=fh("BadgeVoFill",''),gm=fh("BadgeVr",''),vm=fh("BadgeVrFill",''),Am=fh("BadgeWc",''),Pm=fh("BadgeWcFill",''),bm=fh("Bag",''),ym=fh("BagCheck",''),wm=fh("BagCheckFill",''),Im=fh("BagDash",''),zm=fh("BagDashFill",''),Cm=fh("BagFill",''),Dm=fh("BagPlus",''),Rm=fh("BagPlusFill",''),Sm=fh("BagX",''),_m=fh("BagXFill",''),km=fh("Bank",''),Mm=fh("Bank2",''),Tm=fh("BarChart",''),Vm=fh("BarChartFill",''),xm=fh("BarChartLine",''),Bm=fh("BarChartLineFill",''),Lm=fh("BarChartSteps",''),Om=fh("Basket",''),Em=fh("Basket2",''),Um=fh("Basket2Fill",''),Fm=fh("Basket3",''),Hm=fh("Basket3Fill",''),jm=fh("BasketFill",''),Gm=fh("Battery",''),Wm=fh("BatteryCharging",''),Nm=fh("BatteryFull",''),$m=fh("BatteryHalf",''),qm=fh("Bell",''),Jm=fh("BellFill",''),Km=fh("BellSlash",''),Qm=fh("BellSlashFill",''),Ym=fh("Bezier",''),Xm=fh("Bezier2",''),Zm=fh("Bicycle",''),ep=fh("Binoculars",''),tp=fh("BinocularsFill",''),ap=fh("BlockquoteLeft",''),op=fh("BlockquoteRight",''),sp=fh("Book",''),ip=fh("BookFill",''),np=fh("BookHalf",''),rp=fh("Bookmark",''),cp=fh("BookmarkCheck",''),lp=fh("BookmarkCheckFill",''),hp=fh("BookmarkDash",''),dp=fh("BookmarkDashFill",''),mp=fh("BookmarkFill",''),pp=fh("BookmarkHeart",''),up=fh("BookmarkHeartFill",''),fp=fh("BookmarkPlus",''),gp=fh("BookmarkPlusFill",''),vp=fh("BookmarkStar",''),Ap=fh("BookmarkStarFill",''),Pp=fh("BookmarkX",''),bp=fh("BookmarkXFill",''),yp=fh("Bookmarks",''),wp=fh("BookmarksFill",''),Ip=fh("Bookshelf",''),zp=fh("Bootstrap",''),Cp=fh("BootstrapFill",''),Dp=fh("BootstrapReboot",''),Rp=fh("Border",''),Sp=fh("BorderAll",''),_p=fh("BorderBottom",''),kp=fh("BorderCenter",''),Mp=fh("BorderInner",''),Tp=fh("BorderLeft",''),Vp=fh("BorderMiddle",''),xp=fh("BorderOuter",''),Bp=fh("BorderRight",''),Lp=fh("BorderStyle",''),Op=fh("BorderTop",''),Ep=fh("BorderWidth",''),Up=fh("BoundingBox",''),Fp=fh("BoundingBoxCircles",''),Hp=fh("Box",''),jp=fh("BoxArrowDown",''),Gp=fh("BoxArrowDownLeft",''),Wp=fh("BoxArrowDownRight",''),Np=fh("BoxArrowInDown",''),$p=fh("BoxArrowInDownLeft",''),qp=fh("BoxArrowInDownRight",''),Jp=fh("BoxArrowInLeft",''),Kp=fh("BoxArrowInRight",''),Qp=fh("BoxArrowInUp",''),Yp=fh("BoxArrowInUpLeft",''),Xp=fh("BoxArrowInUpRight",''),Zp=fh("BoxArrowLeft",''),eu=fh("BoxArrowRight",''),tu=fh("BoxArrowUp",''),au=fh("BoxArrowUpLeft",''),ou=fh("BoxArrowUpRight",''),su=fh("BoxSeam",''),iu=fh("Braces",''),nu=fh("Bricks",''),ru=fh("Briefcase",''),cu=fh("BriefcaseFill",''),lu=fh("BrightnessAltHigh",''),hu=fh("BrightnessAltHighFill",''),du=fh("BrightnessAltLow",''),mu=fh("BrightnessAltLowFill",''),pu=fh("BrightnessHigh",''),uu=fh("BrightnessHighFill",''),fu=fh("BrightnessLow",''),gu=fh("BrightnessLowFill",''),vu=fh("Broadcast",''),Au=fh("BroadcastPin",''),Pu=fh("Brush",''),bu=fh("BrushFill",''),yu=fh("Bucket",''),wu=fh("BucketFill",''),Iu=fh("Bug",''),zu=fh("BugFill",''),Cu=fh("Building",''),Du=fh("Bullseye",''),Ru=fh("Calculator",''),Su=fh("CalculatorFill",''),_u=fh("Calendar",''),ku=fh("Calendar2",''),Mu=fh("Calendar2Check",''),Tu=fh("Calendar2CheckFill",''),Vu=fh("Calendar2Date",''),xu=fh("Calendar2DateFill",''),Bu=fh("Calendar2Day",''),Lu=fh("Calendar2DayFill",''),Ou=fh("Calendar2Event",''),Eu=fh("Calendar2EventFill",''),Uu=fh("Calendar2Fill",''),Fu=fh("Calendar2Minus",''),Hu=fh("Calendar2MinusFill",''),ju=fh("Calendar2Month",''),Gu=fh("Calendar2MonthFill",''),Wu=fh("Calendar2Plus",''),Nu=fh("Calendar2PlusFill",''),$u=fh("Calendar2Range",''),qu=fh("Calendar2RangeFill",''),Ju=fh("Calendar2Week",''),Ku=fh("Calendar2WeekFill",''),Qu=fh("Calendar2X",''),Yu=fh("Calendar2XFill",''),Xu=fh("Calendar3",''),Zu=fh("Calendar3Event",''),ef=fh("Calendar3EventFill",''),tf=fh("Calendar3Fill",''),af=fh("Calendar3Range",''),of=fh("Calendar3RangeFill",''),sf=fh("Calendar3Week",''),nf=fh("Calendar3WeekFill",''),rf=fh("Calendar4",''),cf=fh("Calendar4Event",''),lf=fh("Calendar4Range",''),hf=fh("Calendar4Week",''),df=fh("CalendarCheck",''),mf=fh("CalendarCheckFill",''),pf=fh("CalendarDate",''),uf=fh("CalendarDateFill",''),ff=fh("CalendarDay",''),gf=fh("CalendarDayFill",''),vf=fh("CalendarEvent",''),Af=fh("CalendarEventFill",''),Pf=fh("CalendarFill",''),bf=fh("CalendarMinus",''),yf=fh("CalendarMinusFill",''),wf=fh("CalendarMonth",''),If=fh("CalendarMonthFill",''),zf=fh("CalendarPlus",''),Cf=fh("CalendarPlusFill",''),Df=fh("CalendarRange",''),Rf=fh("CalendarRangeFill",''),Sf=fh("CalendarWeek",''),_f=fh("CalendarWeekFill",''),kf=fh("CalendarX",''),Mf=fh("CalendarXFill",''),Tf=fh("Camera",''),Vf=fh("Camera2",''),xf=fh("CameraFill",''),Bf=fh("CameraReels",''),Lf=fh("CameraReelsFill",''),Of=fh("CameraVideo",''),Ef=fh("CameraVideoFill",''),Uf=fh("CameraVideoOff",''),Ff=fh("CameraVideoOffFill",''),Hf=fh("Capslock",''),jf=fh("CapslockFill",''),Gf=fh("CardChecklist",''),Wf=fh("CardHeading",''),Nf=fh("CardImage",''),$f=fh("CardList",''),qf=fh("CardText",''),Jf=fh("CaretDown",''),Kf=fh("CaretDownFill",''),Qf=fh("CaretDownSquare",''),Yf=fh("CaretDownSquareFill",''),Xf=fh("CaretLeft",''),Zf=fh("CaretLeftFill",''),eg=fh("CaretLeftSquare",''),tg=fh("CaretLeftSquareFill",''),ag=fh("CaretRight",''),og=fh("CaretRightFill",''),sg=fh("CaretRightSquare",''),ig=fh("CaretRightSquareFill",''),ng=fh("CaretUp",''),rg=fh("CaretUpFill",''),cg=fh("CaretUpSquare",''),lg=fh("CaretUpSquareFill",''),hg=fh("Cart",''),dg=fh("Cart2",''),mg=fh("Cart3",''),pg=fh("Cart4",''),ug=fh("CartCheck",''),fg=fh("CartCheckFill",''),gg=fh("CartDash",''),vg=fh("CartDashFill",''),Ag=fh("CartFill",''),Pg=fh("CartPlus",''),bg=fh("CartPlusFill",''),yg=fh("CartX",''),wg=fh("CartXFill",''),Ig=fh("Cash",''),zg=fh("CashCoin",''),Cg=fh("CashStack",''),Dg=fh("Cast",''),Rg=fh("Chat",''),Sg=fh("ChatDots",''),_g=fh("ChatDotsFill",''),kg=fh("ChatFill",''),Mg=fh("ChatLeft",''),Tg=fh("ChatLeftDots",''),Vg=fh("ChatLeftDotsFill",''),xg=fh("ChatLeftFill",''),Bg=fh("ChatLeftQuote",''),Lg=fh("ChatLeftQuoteFill",''),Og=fh("ChatLeftText",''),Eg=fh("ChatLeftTextFill",''),Ug=fh("ChatQuote",''),Fg=fh("ChatQuoteFill",''),Hg=fh("ChatRight",''),jg=fh("ChatRightDots",''),Gg=fh("ChatRightDotsFill",''),Wg=fh("ChatRightFill",''),Ng=fh("ChatRightQuote",''),$g=fh("ChatRightQuoteFill",''),qg=fh("ChatRightText",''),Jg=fh("ChatRightTextFill",''),Kg=fh("ChatSquare",''),Qg=fh("ChatSquareDots",''),Yg=fh("ChatSquareDotsFill",''),Xg=fh("ChatSquareFill",''),Zg=fh("ChatSquareQuote",''),ev=fh("ChatSquareQuoteFill",''),tv=fh("ChatSquareText",''),av=fh("ChatSquareTextFill",''),ov=fh("ChatText",''),sv=fh("ChatTextFill",''),iv=fh("Check",''),nv=fh("Check2",''),rv=fh("Check2All",''),cv=fh("Check2Circle",''),lv=fh("Check2Square",''),hv=fh("CheckAll",''),dv=fh("CheckCircle",''),mv=fh("CheckCircleFill",''),pv=fh("CheckLg",''),uv=fh("CheckSquare",''),fv=fh("CheckSquareFill",''),gv=fh("ChevronBarContract",''),vv=fh("ChevronBarDown",''),Av=fh("ChevronBarExpand",''),Pv=fh("ChevronBarLeft",''),bv=fh("ChevronBarRight",''),yv=fh("ChevronBarUp",''),wv=fh("ChevronCompactDown",''),Iv=fh("ChevronCompactLeft",''),zv=fh("ChevronCompactRight",''),Cv=fh("ChevronCompactUp",''),Dv=fh("ChevronContract",''),Rv=fh("ChevronDoubleDown",''),Sv=fh("ChevronDoubleLeft",''),_v=fh("ChevronDoubleRight",''),kv=fh("ChevronDoubleUp",''),Mv=fh("ChevronDown",''),Tv=fh("ChevronExpand",''),Vv=fh("ChevronLeft",''),xv=fh("ChevronRight",''),Bv=fh("ChevronUp",''),Lv=fh("Circle",''),Ov=fh("CircleFill",''),Ev=fh("CircleHalf",''),Uv=fh("CircleSquare",''),Fv=fh("Clipboard",''),Hv=fh("ClipboardCheck",''),jv=fh("ClipboardData",''),Gv=fh("ClipboardMinus",''),Wv=fh("ClipboardPlus",''),Nv=fh("ClipboardX",''),$v=fh("Clock",''),qv=fh("ClockFill",''),Jv=fh("ClockHistory",''),Kv=fh("Cloud",''),Qv=fh("CloudArrowDown",''),Yv=fh("CloudArrowDownFill",''),Xv=fh("CloudArrowUp",''),Zv=fh("CloudArrowUpFill",''),eA=fh("CloudCheck",''),tA=fh("CloudCheckFill",''),aA=fh("CloudDownload",''),oA=fh("CloudDownloadFill",''),sA=fh("CloudDrizzle",''),iA=fh("CloudDrizzleFill",''),nA=fh("CloudFill",''),rA=fh("CloudFog",''),cA=fh("CloudFog2",''),lA=fh("CloudFog2Fill",''),hA=fh("CloudFogFill",''),dA=fh("CloudHail",''),mA=fh("CloudHailFill",''),pA=fh("CloudHaze",''),uA=fh("CloudHaze1",''),fA=fh("CloudHaze2Fill",''),gA=fh("CloudHazeFill",''),vA=fh("CloudLightning",''),AA=fh("CloudLightningFill",''),PA=fh("CloudLightningRain",''),bA=fh("CloudLightningRainFill",''),yA=fh("CloudMinus",''),wA=fh("CloudMinusFill",''),IA=fh("CloudMoon",''),zA=fh("CloudMoonFill",''),CA=fh("CloudPlus",''),DA=fh("CloudPlusFill",''),RA=fh("CloudRain",''),SA=fh("CloudRainFill",''),_A=fh("CloudRainHeavy",''),kA=fh("CloudRainHeavyFill",''),MA=fh("CloudSlash",''),TA=fh("CloudSlashFill",''),VA=fh("CloudSleet",''),xA=fh("CloudSleetFill",''),BA=fh("CloudSnow",''),LA=fh("CloudSnowFill",''),OA=fh("CloudSun",''),EA=fh("CloudSunFill",''),UA=fh("CloudUpload",''),FA=fh("CloudUploadFill",''),HA=fh("Clouds",''),jA=fh("CloudsFill",''),GA=fh("Cloudy",''),WA=fh("CloudyFill",''),NA=fh("Code",''),$A=fh("CodeSlash",''),qA=fh("CodeSquare",''),JA=fh("Coin",''),KA=fh("Collection",''),QA=fh("CollectionFill",''),YA=fh("CollectionPlay",''),XA=fh("CollectionPlayFill",''),ZA=fh("Columns",''),eP=fh("ColumnsGap",''),tP=fh("Command",''),aP=fh("Compass",''),oP=fh("CompassFill",''),sP=fh("Cone",''),iP=fh("ConeStriped",''),nP=fh("Controller",''),rP=fh("Cpu",''),cP=fh("CpuFill",''),lP=fh("CreditCard",''),hP=fh("CreditCard2Back",''),dP=fh("CreditCard2BackFill",''),mP=fh("CreditCard2Front",''),pP=fh("CreditCard2FrontFill",''),uP=fh("CreditCardFill",''),fP=fh("Crop",''),gP=fh("Cup",''),vP=fh("CupFill",''),AP=fh("CupStraw",''),PP=fh("CurrencyBitcoin",''),bP=fh("CurrencyDollar",''),yP=fh("CurrencyEuro",''),wP=fh("CurrencyExchange",''),IP=fh("CurrencyPound",''),zP=fh("CurrencyYen",''),CP=fh("Cursor",''),DP=fh("CursorFill",''),RP=fh("CursorText",''),SP=fh("Dash",''),_P=fh("DashCircle",''),kP=fh("DashCircleDotted",''),MP=fh("DashCircleFill",''),TP=fh("DashLg",''),VP=fh("DashSquare",''),xP=fh("DashSquareDotted",''),BP=fh("DashSquareFill",''),LP=fh("Diagram2",''),OP=fh("Diagram2Fill",''),EP=fh("Diagram3",''),UP=fh("Diagram3Fill",''),FP=fh("Diamond",''),HP=fh("DiamondFill",''),jP=fh("DiamondHalf",''),GP=fh("Dice1",''),WP=fh("Dice1Fill",''),NP=fh("Dice2",''),$P=fh("Dice2Fill",''),qP=fh("Dice3",''),JP=fh("Dice3Fill",''),KP=fh("Dice4",''),QP=fh("Dice4Fill",''),YP=fh("Dice5",''),XP=fh("Dice5Fill",''),ZP=fh("Dice6",''),eb=fh("Dice6Fill",''),tb=fh("Disc",''),ab=fh("DiscFill",''),ob=fh("Discord",''),sb=fh("Display",''),ib=fh("DisplayFill",''),nb=fh("DistributeHorizontal",''),rb=fh("DistributeVertical",''),cb=fh("DoorClosed",''),lb=fh("DoorClosedFill",''),hb=fh("DoorOpen",''),db=fh("DoorOpenFill",''),mb=fh("Dot",''),pb=fh("Download",''),ub=fh("Droplet",''),fb=fh("DropletFill",''),gb=fh("DropletHalf",''),vb=fh("Earbuds",''),Ab=fh("Easel",''),Pb=fh("EaselFill",''),bb=fh("Egg",''),yb=fh("EggFill",''),wb=fh("EggFried",''),Ib=fh("Eject",''),zb=fh("EjectFill",''),Cb=fh("EmojiAngry",''),Db=fh("EmojiAngryFill",''),Rb=fh("EmojiDizzy",''),Sb=fh("EmojiDizzyFill",''),_b=fh("EmojiExpressionless",''),kb=fh("EmojiExpressionlessFill",''),Mb=fh("EmojiFrown",''),Tb=fh("EmojiFrownFill",''),Vb=fh("EmojiHeartEyes",''),xb=fh("EmojiHeartEyesFill",''),Bb=fh("EmojiLaughing",''),Lb=fh("EmojiLaughingFill",''),Ob=fh("EmojiNeutral",''),Eb=fh("EmojiNeutralFill",''),Ub=fh("EmojiSmile",''),Fb=fh("EmojiSmileFill",''),Hb=fh("EmojiSmileUpsideDown",''),jb=fh("EmojiSmileUpsideDownFill",''),Gb=fh("EmojiSunglasses",''),Wb=fh("EmojiSunglassesFill",''),Nb=fh("EmojiWink",''),$b=fh("EmojiWinkFill",''),qb=fh("Envelope",''),Jb=fh("EnvelopeFill",''),Kb=fh("EnvelopeOpen",''),Qb=fh("EnvelopeOpenFill",''),Yb=fh("Eraser",''),Xb=fh("EraserFill",''),Zb=fh("Exclamation",''),ey=fh("ExclamationCircle",''),ty=fh("ExclamationCircleFill",''),ay=fh("ExclamationDiamond",''),oy=fh("ExclamationDiamondFill",''),sy=fh("ExclamationLg",''),iy=fh("ExclamationOctagon",''),ny=fh("ExclamationOctagonFill",''),ry=fh("ExclamationSquare",''),cy=fh("ExclamationSquareFill",''),ly=fh("ExclamationTriangle",''),hy=fh("ExclamationTriangleFill",''),dy=fh("Exclude",''),my=fh("Eye",''),py=fh("EyeFill",''),uy=fh("EyeSlash",''),fy=fh("EyeSlashFill",''),gy=fh("Eyedropper",''),vy=fh("Eyeglasses",''),Ay=fh("Facebook",''),Py=fh("File",''),by=fh("FileArrowDown",''),yy=fh("FileArrowDownFill",''),wy=fh("FileArrowUp",''),Iy=fh("FileArrowUpFill",''),zy=fh("FileBarGraph",''),Cy=fh("FileBarGraphFill",''),Dy=fh("FileBinary",''),Ry=fh("FileBinaryFill",''),Sy=fh("FileBreak",''),_y=fh("FileBreakFill",''),ky=fh("FileCheck",''),My=fh("FileCheckFill",''),Ty=fh("FileCode",''),Vy=fh("FileCodeFill",''),xy=fh("FileDiff",''),By=fh("FileDiffFill",''),Ly=fh("FileEarmark",''),Oy=fh("FileEarmarkArrowDown",''),Ey=fh("FileEarmarkArrowDownFill",''),Uy=fh("FileEarmarkArrowUp",''),Fy=fh("FileEarmarkArrowUpFill",''),Hy=fh("FileEarmarkBarGraph",''),jy=fh("FileEarmarkBarGraphFill",''),Gy=fh("FileEarmarkBinary",''),Wy=fh("FileEarmarkBinaryFill",''),Ny=fh("FileEarmarkBreak",''),$y=fh("FileEarmarkBreakFill",''),qy=fh("FileEarmarkCheck",''),Jy=fh("FileEarmarkCheckFill",''),Ky=fh("FileEarmarkCode",''),Qy=fh("FileEarmarkCodeFill",''),Yy=fh("FileEarmarkDiff",''),Xy=fh("FileEarmarkDiffFill",''),Zy=fh("FileEarmarkEasel",''),ew=fh("FileEarmarkEaselFill",''),tw=fh("FileEarmarkExcel",''),aw=fh("FileEarmarkExcelFill",''),ow=fh("FileEarmarkFill",''),sw=fh("FileEarmarkFont",''),iw=fh("FileEarmarkFontFill",''),nw=fh("FileEarmarkImage",''),rw=fh("FileEarmarkImageFill",''),cw=fh("FileEarmarkLock",''),lw=fh("FileEarmarkLock2",''),hw=fh("FileEarmarkLock2Fill",''),dw=fh("FileEarmarkLockFill",''),mw=fh("FileEarmarkMedical",''),pw=fh("FileEarmarkMedicalFill",''),uw=fh("FileEarmarkMinus",''),fw=fh("FileEarmarkMinusFill",''),gw=fh("FileEarmarkMusic",''),vw=fh("FileEarmarkMusicFill",''),Aw=fh("FileEarmarkPdf",''),Pw=fh("FileEarmarkPdfFill",''),bw=fh("FileEarmarkPerson",''),yw=fh("FileEarmarkPersonFill",''),ww=fh("FileEarmarkPlay",''),Iw=fh("FileEarmarkPlayFill",''),zw=fh("FileEarmarkPlus",''),Cw=fh("FileEarmarkPlusFill",''),Dw=fh("FileEarmarkPost",''),Rw=fh("FileEarmarkPostFill",''),Sw=fh("FileEarmarkPpt",''),_w=fh("FileEarmarkPptFill",''),kw=fh("FileEarmarkRichtext",''),Mw=fh("FileEarmarkRichtextFill",''),Tw=fh("FileEarmarkRuled",''),Vw=fh("FileEarmarkRuledFill",''),xw=fh("FileEarmarkSlides",''),Bw=fh("FileEarmarkSlidesFill",''),Lw=fh("FileEarmarkSpreadsheet",''),Ow=fh("FileEarmarkSpreadsheetFill",''),Ew=fh("FileEarmarkText",''),Uw=fh("FileEarmarkTextFill",''),Fw=fh("FileEarmarkWord",''),Hw=fh("FileEarmarkWordFill",''),jw=fh("FileEarmarkX",''),Gw=fh("FileEarmarkXFill",''),Ww=fh("FileEarmarkZip",''),Nw=fh("FileEarmarkZipFill",''),$w=fh("FileEasel",''),qw=fh("FileEaselFill",''),Jw=fh("FileExcel",''),Kw=fh("FileExcelFill",''),Qw=fh("FileFill",''),Yw=fh("FileFont",''),Xw=fh("FileFontFill",''),Zw=fh("FileImage",''),eI=fh("FileImageFill",''),tI=fh("FileLock",''),aI=fh("FileLock2",''),oI=fh("FileLock2Fill",''),sI=fh("FileLockFill",''),iI=fh("FileMedical",''),nI=fh("FileMedicalFill",''),rI=fh("FileMinus",''),cI=fh("FileMinusFill",''),lI=fh("FileMusic",''),hI=fh("FileMusicFill",''),dI=fh("FilePdf",''),mI=fh("FilePdfFill",''),pI=fh("FilePerson",''),uI=fh("FilePersonFill",''),fI=fh("FilePlay",''),gI=fh("FilePlayFill",''),vI=fh("FilePlus",''),AI=fh("FilePlusFill",''),PI=fh("FilePost",''),bI=fh("FilePostFill",''),yI=fh("FilePpt",''),wI=fh("FilePptFill",''),II=fh("FileRichtext",''),zI=fh("FileRichtextFill",''),CI=fh("FileRuled",''),DI=fh("FileRuledFill",''),RI=fh("FileSlides",''),SI=fh("FileSlidesFill",''),_I=fh("FileSpreadsheet",''),kI=fh("FileSpreadsheetFill",''),MI=fh("FileText",''),TI=fh("FileTextFill",''),VI=fh("FileWord",''),xI=fh("FileWordFill",''),BI=fh("FileX",''),LI=fh("FileXFill",''),OI=fh("FileZip",''),EI=fh("FileZipFill",''),UI=fh("Files",''),FI=fh("FilesAlt",''),HI=fh("Film",''),jI=fh("Filter",''),GI=fh("FilterCircle",''),WI=fh("FilterCircleFill",''),NI=fh("FilterLeft",''),$I=fh("FilterRight",''),qI=fh("FilterSquare",''),JI=fh("FilterSquareFill",''),KI=fh("Flag",''),QI=fh("FlagFill",''),YI=fh("Flower1",''),XI=fh("Flower2",''),ZI=fh("Flower3",''),ez=fh("Folder",''),tz=fh("Folder2",''),az=fh("Folder2Open",''),oz=fh("FolderCheck",''),sz=fh("FolderFill",''),iz=fh("FolderMinus",''),nz=fh("FolderPlus",''),rz=fh("FolderSymlink",''),cz=fh("FolderSymlinkFill",''),lz=fh("FolderX",''),hz=fh("Fonts",''),dz=fh("Forward",''),mz=fh("ForwardFill",''),pz=fh("Front",''),uz=fh("Fullscreen",''),fz=fh("FullscreenExit",''),gz=fh("Funnel",''),vz=fh("FunnelFill",''),Az=fh("Gear",''),Pz=fh("GearFill",''),bz=fh("GearWide",''),yz=fh("GearWideConnected",''),wz=fh("Gem",''),Iz=fh("GenderAmbiguous",''),zz=fh("GenderFemale",''),Cz=fh("GenderMale",''),Dz=fh("GenderTrans",''),Rz=fh("Geo",''),Sz=fh("GeoAlt",''),_z=fh("GeoAltFill",''),kz=fh("GeoFill",''),Mz=fh("Gift",''),Tz=fh("GiftFill",''),Vz=fh("Github",''),xz=fh("Globe",''),Bz=fh("Globe2",''),Lz=fh("Google",''),Oz=fh("GraphDown",''),Ez=fh("GraphUp",''),Uz=fh("Grid",''),Fz=fh("Grid1x2",''),Hz=fh("Grid1x2Fill",''),jz=fh("Grid3x2",''),Gz=fh("Grid3x2Gap",''),Wz=fh("Grid3x2GapFill",''),Nz=fh("Grid3x3",''),$z=fh("Grid3x3Gap",''),qz=fh("Grid3x3GapFill",''),Jz=fh("GridFill",''),Kz=fh("GripHorizontal",''),Qz=fh("GripVertical",''),Yz=fh("Hammer",''),Xz=fh("HandIndex",''),Zz=fh("HandIndexFill",''),eC=fh("HandIndexThumb",''),tC=fh("HandIndexThumbFill",''),aC=fh("HandThumbsDown",''),oC=fh("HandThumbsDownFill",''),sC=fh("HandThumbsUp",''),iC=fh("HandThumbsUpFill",''),nC=fh("Handbag",''),rC=fh("HandbagFill",''),cC=fh("Hash",''),lC=fh("Hdd",''),hC=fh("HddFill",''),dC=fh("HddNetwork",''),mC=fh("HddNetworkFill",''),pC=fh("HddRack",''),uC=fh("HddRackFill",''),fC=fh("HddStack",''),gC=fh("HddStackFill",''),vC=fh("Headphones",''),AC=fh("Headset",''),PC=fh("HeadsetVr",''),bC=fh("Heart",''),yC=fh("HeartFill",''),wC=fh("HeartHalf",''),IC=fh("Heptagon",''),zC=fh("HeptagonFill",''),CC=fh("HeptagonHalf",''),DC=fh("Hexagon",''),RC=fh("HexagonFill",''),SC=fh("HexagonHalf",''),_C=fh("Hourglass",''),kC=fh("HourglassBottom",''),MC=fh("HourglassSplit",''),TC=fh("HourglassTop",''),VC=fh("House",''),xC=fh("HouseDoor",''),BC=fh("HouseDoorFill",''),LC=fh("HouseFill",''),OC=fh("Hr",''),EC=fh("Hurricane",''),UC=fh("Image",''),FC=fh("ImageAlt",''),HC=fh("ImageFill",''),jC=fh("Images",''),GC=fh("Inbox",''),WC=fh("InboxFill",''),NC=fh("Inboxes",''),$C=fh("InboxesFill",''),qC=fh("Info",''),JC=fh("InfoCircle",''),KC=fh("InfoCircleFill",''),QC=fh("InfoLg",''),YC=fh("InfoSquare",''),XC=fh("InfoSquareFill",''),ZC=fh("InputCursor",''),eD=fh("InputCursorText",''),tD=fh("Instagram",''),aD=fh("Intersect",''),oD=fh("Journal",''),sD=fh("JournalAlbum",''),iD=fh("JournalArrowDown",''),nD=fh("JournalArrowUp",''),rD=fh("JournalBookmark",''),cD=fh("JournalBookmarkFill",''),lD=fh("JournalCheck",''),hD=fh("JournalCode",''),dD=fh("JournalMedical",''),mD=fh("JournalMinus",''),pD=fh("JournalPlus",''),uD=fh("JournalRichtext",''),fD=fh("JournalText",''),gD=fh("JournalX",''),vD=fh("Journals",''),AD=fh("Joystick",''),PD=fh("Justify",''),bD=fh("JustifyLeft",''),yD=fh("JustifyRight",''),wD=fh("Kanban",''),ID=fh("KanbanFill",''),zD=fh("Key",''),CD=fh("KeyFill",''),DD=fh("Keyboard",''),RD=fh("KeyboardFill",''),SD=fh("Ladder",''),_D=fh("Lamp",''),kD=fh("LampFill",''),MD=fh("Laptop",''),TD=fh("LaptopFill",''),VD=fh("LayerBackward",''),xD=fh("LayerForward",''),BD=fh("Layers",''),LD=fh("LayersFill",''),OD=fh("LayersHalf",''),ED=fh("LayoutSidebar",''),UD=fh("LayoutSidebarInset",''),FD=fh("LayoutSidebarInsetReverse",''),HD=fh("LayoutSidebarReverse",''),jD=fh("LayoutSplit",''),GD=fh("LayoutTextSidebar",''),WD=fh("LayoutTextSidebarReverse",''),ND=fh("LayoutTextWindow",''),$D=fh("LayoutTextWindowReverse",''),qD=fh("LayoutThreeColumns",''),JD=fh("LayoutWtf",''),KD=fh("LifePreserver",''),QD=fh("Lightbulb",''),YD=fh("LightbulbFill",''),XD=fh("LightbulbOff",''),ZD=fh("LightbulbOffFill",''),eR=fh("Lightning",''),tR=fh("LightningCharge",''),aR=fh("LightningChargeFill",''),oR=fh("LightningFill",''),sR=fh("Link",''),iR=fh("Link45deg",''),nR=fh("Linkedin",''),rR=fh("List",''),cR=fh("ListCheck",''),lR=fh("ListNested",''),hR=fh("ListOl",''),dR=fh("ListStars",''),mR=fh("ListTask",''),pR=fh("ListUl",''),uR=fh("Lock",''),fR=fh("LockFill",''),gR=fh("Mailbox",''),vR=fh("Mailbox2",''),AR=fh("Map",''),PR=fh("MapFill",''),bR=fh("Markdown",''),yR=fh("MarkdownFill",''),wR=fh("Mask",''),IR=fh("Mastodon",''),zR=fh("Megaphone",''),CR=fh("MegaphoneFill",''),DR=fh("MenuApp",''),RR=fh("MenuAppFill",''),SR=fh("MenuButton",''),_R=fh("MenuButtonFill",''),kR=fh("MenuButtonWide",''),MR=fh("MenuButtonWideFill",''),TR=fh("MenuDown",''),VR=fh("MenuUp",''),xR=fh("Messenger",''),BR=fh("Mic",''),LR=fh("MicFill",''),OR=fh("MicMute",''),ER=fh("MicMuteFill",''),UR=fh("Minecart",''),FR=fh("MinecartLoaded",''),HR=fh("Moisture",''),jR=fh("Moon",''),GR=fh("MoonFill",''),WR=fh("MoonStars",''),NR=fh("MoonStarsFill",''),$R=fh("Mouse",''),qR=fh("Mouse2",''),JR=fh("Mouse2Fill",''),KR=fh("Mouse3",''),QR=fh("Mouse3Fill",''),YR=fh("MouseFill",''),XR=fh("MusicNote",''),ZR=fh("MusicNoteBeamed",''),eS=fh("MusicNoteList",''),tS=fh("MusicPlayer",''),aS=fh("MusicPlayerFill",''),oS=fh("Newspaper",''),sS=fh("NodeMinus",''),iS=fh("NodeMinusFill",''),nS=fh("NodePlus",''),rS=fh("NodePlusFill",''),cS=fh("Nut",''),lS=fh("NutFill",''),hS=fh("Octagon",''),dS=fh("OctagonFill",''),mS=fh("OctagonHalf",''),pS=fh("Option",''),uS=fh("Outlet",''),fS=fh("PaintBucket",''),gS=fh("Palette",''),vS=fh("Palette2",''),AS=fh("PaletteFill",''),PS=fh("Paperclip",''),bS=fh("Paragraph",''),yS=fh("PatchCheck",''),wS=fh("PatchCheckFill",''),IS=fh("PatchExclamation",''),zS=fh("PatchExclamationFill",''),CS=fh("PatchMinus",''),DS=fh("PatchMinusFill",''),RS=fh("PatchPlus",''),SS=fh("PatchPlusFill",''),_S=fh("PatchQuestion",''),kS=fh("PatchQuestionFill",''),MS=fh("Pause",''),TS=fh("PauseBtn",''),VS=fh("PauseBtnFill",''),xS=fh("PauseCircle",''),BS=fh("PauseCircleFill",''),LS=fh("PauseFill",''),OS=fh("Peace",''),ES=fh("PeaceFill",''),US=fh("Pen",''),FS=fh("PenFill",''),HS=fh("Pencil",''),jS=fh("PencilFill",''),GS=fh("PencilSquare",''),WS=fh("Pentagon",''),NS=fh("PentagonFill",''),$S=fh("PentagonHalf",''),qS=fh("People",''),JS=fh("PeopleFill",''),KS=fh("Percent",''),QS=fh("Person",''),YS=fh("PersonBadge",''),XS=fh("PersonBadgeFill",''),ZS=fh("PersonBoundingBox",''),e_=fh("PersonCheck",''),t_=fh("PersonCheckFill",''),a_=fh("PersonCircle",''),o_=fh("PersonDash",''),s_=fh("PersonDashFill",''),i_=fh("PersonFill",''),n_=fh("PersonLinesFill",''),r_=fh("PersonPlus",''),c_=fh("PersonPlusFill",''),l_=fh("PersonSquare",''),h_=fh("PersonX",''),d_=fh("PersonXFill",''),m_=fh("Phone",''),p_=fh("PhoneFill",''),u_=fh("PhoneLandscape",''),f_=fh("PhoneLandscapeFill",''),g_=fh("PhoneVibrate",''),v_=fh("PhoneVibrateFill",''),A_=fh("PieChart",''),P_=fh("PieChartFill",''),b_=fh("PiggyBank",''),y_=fh("PiggyBankFill",''),w_=fh("Pin",''),I_=fh("PinAngle",''),z_=fh("PinAngleFill",''),C_=fh("PinFill",''),D_=fh("PinMap",''),R_=fh("PinMapFill",''),S_=fh("Pip",''),__=fh("PipFill",''),k_=fh("Play",''),M_=fh("PlayBtn",''),T_=fh("PlayBtnFill",''),V_=fh("PlayCircle",''),x_=fh("PlayCircleFill",''),B_=fh("PlayFill",''),L_=fh("Plug",''),O_=fh("PlugFill",''),E_=fh("Plus",''),U_=fh("PlusCircle",''),F_=fh("PlusCircleDotted",''),H_=fh("PlusCircleFill",''),j_=fh("PlusLg",''),G_=fh("PlusSquare",''),W_=fh("PlusSquareDotted",''),N_=fh("PlusSquareFill",''),$_=fh("Power",''),q_=fh("Printer",''),J_=fh("PrinterFill",''),K_=fh("Puzzle",''),Q_=fh("PuzzleFill",''),Y_=fh("Question",''),X_=fh("QuestionCircle",''),Z_=fh("QuestionCircleFill",''),ek=fh("QuestionDiamond",''),tk=fh("QuestionDiamondFill",''),ak=fh("QuestionLg",''),ok=fh("QuestionOctagon",''),sk=fh("QuestionOctagonFill",''),ik=fh("QuestionSquare",''),nk=fh("QuestionSquareFill",''),rk=fh("Rainbow",''),ck=fh("Receipt",''),lk=fh("ReceiptCutoff",''),hk=fh("Reception0",''),dk=fh("Reception1",''),mk=fh("Reception2",''),pk=fh("Reception3",''),uk=fh("Reception4",''),fk=fh("Record",''),gk=fh("Record2",''),vk=fh("Record2Fill",''),Ak=fh("RecordBtn",''),Pk=fh("RecordBtnFill",''),bk=fh("RecordCircle",''),yk=fh("RecordCircleFill",''),wk=fh("RecordFill",''),Ik=fh("Recycle",''),zk=fh("Reddit",''),Ck=fh("Reply",''),Dk=fh("ReplyAll",''),Rk=fh("ReplyAllFill",''),Sk=fh("ReplyFill",''),_k=fh("Rss",''),kk=fh("RssFill",''),Mk=fh("Rulers",''),Tk=fh("Safe",''),Vk=fh("Safe2",''),xk=fh("Safe2Fill",''),Bk=fh("SafeFill",''),Lk=fh("Save",''),Ok=fh("Save2",''),Ek=fh("Save2Fill",''),Uk=fh("SaveFill",''),Fk=fh("Scissors",''),Hk=fh("Screwdriver",''),jk=fh("SdCard",''),Gk=fh("SdCardFill",''),Wk=fh("Search",''),Nk=fh("SegmentedNav",''),$k=fh("Server",''),qk=fh("Share",''),Jk=fh("ShareFill",''),Kk=fh("Shield",''),Qk=fh("ShieldCheck",''),Yk=fh("ShieldExclamation",''),Xk=fh("ShieldFill",''),Zk=fh("ShieldFillCheck",''),eM=fh("ShieldFillExclamation",''),tM=fh("ShieldFillMinus",''),aM=fh("ShieldFillPlus",''),oM=fh("ShieldFillX",''),sM=fh("ShieldLock",''),iM=fh("ShieldLockFill",''),nM=fh("ShieldMinus",''),rM=fh("ShieldPlus",''),cM=fh("ShieldShaded",''),lM=fh("ShieldSlash",''),hM=fh("ShieldSlashFill",''),dM=fh("ShieldX",''),mM=fh("Shift",''),pM=fh("ShiftFill",''),uM=fh("Shop",''),fM=fh("ShopWindow",''),gM=fh("Shuffle",''),vM=fh("Signpost",''),AM=fh("Signpost2",''),PM=fh("Signpost2Fill",''),bM=fh("SignpostFill",''),yM=fh("SignpostSplit",''),wM=fh("SignpostSplitFill",''),IM=fh("Sim",''),zM=fh("SimFill",''),CM=fh("SkipBackward",''),DM=fh("SkipBackwardBtn",''),RM=fh("SkipBackwardBtnFill",''),SM=fh("SkipBackwardCircle",''),_M=fh("SkipBackwardCircleFill",''),kM=fh("SkipBackwardFill",''),MM=fh("SkipEnd",''),TM=fh("SkipEndBtn",''),VM=fh("SkipEndBtnFill",''),xM=fh("SkipEndCircle",''),BM=fh("SkipEndCircleFill",''),LM=fh("SkipEndFill",''),OM=fh("SkipForward",''),EM=fh("SkipForwardBtn",''),UM=fh("SkipForwardBtnFill",''),FM=fh("SkipForwardCircle",''),HM=fh("SkipForwardCircleFill",''),jM=fh("SkipForwardFill",''),GM=fh("SkipStart",''),WM=fh("SkipStartBtn",''),NM=fh("SkipStartBtnFill",''),$M=fh("SkipStartCircle",''),qM=fh("SkipStartCircleFill",''),JM=fh("SkipStartFill",''),KM=fh("Skype",''),QM=fh("Slack",''),YM=fh("Slash",''),XM=fh("SlashCircle",''),ZM=fh("SlashCircleFill",''),eT=fh("SlashLg",''),tT=fh("SlashSquare",''),aT=fh("SlashSquareFill",''),oT=fh("Sliders",''),sT=fh("Smartwatch",''),iT=fh("Snow",''),nT=fh("Snow2",''),rT=fh("Snow3",''),cT=fh("SortAlphaDown",''),lT=fh("SortAlphaDownAlt",''),hT=fh("SortAlphaUp",''),dT=fh("SortAlphaUpAlt",''),mT=fh("SortDown",''),pT=fh("SortDownAlt",''),uT=fh("SortNumericDown",''),fT=fh("SortNumericDownAlt",''),gT=fh("SortNumericUp",''),vT=fh("SortNumericUpAlt",''),AT=fh("SortUp",''),PT=fh("SortUpAlt",''),bT=fh("Soundwave",''),yT=fh("Speaker",''),wT=fh("SpeakerFill",''),IT=fh("Speedometer",''),zT=fh("Speedometer2",''),CT=fh("Spellcheck",''),DT=fh("Square",''),RT=fh("SquareFill",''),ST=fh("SquareHalf",''),_T=fh("Stack",''),kT=fh("Star",''),MT=fh("StarFill",''),TT=fh("StarHalf",''),VT=fh("Stars",''),xT=fh("Stickies",''),BT=fh("StickiesFill",''),LT=fh("Sticky",''),OT=fh("StickyFill",''),ET=fh("Stop",''),UT=fh("StopBtn",''),FT=fh("StopBtnFill",''),HT=fh("StopCircle",''),jT=fh("StopCircleFill",''),GT=fh("StopFill",''),WT=fh("Stoplights",''),NT=fh("StoplightsFill",''),$T=fh("Stopwatch",''),qT=fh("StopwatchFill",''),JT=fh("Subtract",''),KT=fh("SuitClub",''),QT=fh("SuitClubFill",''),YT=fh("SuitDiamond",''),XT=fh("SuitDiamondFill",''),ZT=fh("SuitHeart",''),eV=fh("SuitHeartFill",''),tV=fh("SuitSpade",''),aV=fh("SuitSpadeFill",''),oV=fh("Sun",''),sV=fh("SunFill",''),iV=fh("Sunglasses",''),nV=fh("Sunrise",''),rV=fh("SunriseFill",''),cV=fh("Sunset",''),lV=fh("SunsetFill",''),hV=fh("SymmetryHorizontal",''),dV=fh("SymmetryVertical",''),mV=fh("Table",''),pV=fh("Tablet",''),uV=fh("TabletFill",''),fV=fh("TabletLandscape",''),gV=fh("TabletLandscapeFill",''),vV=fh("Tag",''),AV=fh("TagFill",''),PV=fh("Tags",''),bV=fh("TagsFill",''),yV=fh("Telegram",''),wV=fh("Telephone",''),IV=fh("TelephoneFill",''),zV=fh("TelephoneForward",''),CV=fh("TelephoneForwardFill",''),DV=fh("TelephoneInbound",''),RV=fh("TelephoneInboundFill",''),SV=fh("TelephoneMinus",''),_V=fh("TelephoneMinusFill",''),kV=fh("TelephoneOutbound",''),MV=fh("TelephoneOutboundFill",''),TV=fh("TelephonePlus",''),VV=fh("TelephonePlusFill",''),xV=fh("TelephoneX",''),BV=fh("TelephoneXFill",''),LV=fh("Terminal",''),OV=fh("TerminalFill",''),EV=fh("TextCenter",''),UV=fh("TextIndentLeft",''),FV=fh("TextIndentRight",''),HV=fh("TextLeft",''),jV=fh("TextParagraph",''),GV=fh("TextRight",''),WV=fh("Textarea",''),NV=fh("TextareaResize",''),$V=fh("TextareaT",''),qV=fh("Thermometer",''),JV=fh("ThermometerHalf",''),KV=fh("ThermometerHigh",''),QV=fh("ThermometerLow",''),YV=fh("ThermometerSnow",''),XV=fh("ThermometerSun",''),ZV=fh("ThreeDots",''),ex=fh("ThreeDotsVertical",''),tx=fh("Toggle2Off",''),ax=fh("Toggle2On",''),ox=fh("ToggleOff",''),sx=fh("ToggleOn",''),ix=fh("Toggles",''),nx=fh("Toggles2",''),rx=fh("Tools",''),cx=fh("Tornado",''),lx=fh("Translate",''),hx=fh("Trash",''),dx=fh("Trash2",''),mx=fh("Trash2Fill",''),px=fh("TrashFill",''),ux=fh("Tree",''),fx=fh("TreeFill",''),gx=fh("Triangle",''),vx=fh("TriangleFill",''),Ax=fh("TriangleHalf",''),Px=fh("Trophy",''),bx=fh("TrophyFill",''),yx=fh("TropicalStorm",''),wx=fh("Truck",''),Ix=fh("TruckFlatbed",''),zx=fh("Tsunami",''),Cx=fh("Tv",''),Dx=fh("TvFill",''),Rx=fh("Twitch",''),Sx=fh("Twitter",''),_x=fh("Type",''),kx=fh("TypeBold",''),Mx=fh("TypeH1",''),Tx=fh("TypeH2",''),Vx=fh("TypeH3",''),xx=fh("TypeItalic",''),Bx=fh("TypeStrikethrough",''),Lx=fh("TypeUnderline",''),Ox=fh("UiChecks",''),Ex=fh("UiChecksGrid",''),Ux=fh("UiRadios",''),Fx=fh("UiRadiosGrid",''),Hx=fh("Umbrella",''),jx=fh("UmbrellaFill",''),Gx=fh("Union",''),Wx=fh("Unlock",''),Nx=fh("UnlockFill",''),$x=fh("Upc",''),qx=fh("UpcScan",''),Jx=fh("Upload",''),Kx=fh("VectorPen",''),Qx=fh("ViewList",''),Yx=fh("ViewStacked",''),Xx=fh("Vinyl",''),Zx=fh("VinylFill",''),eB=fh("Voicemail",''),tB=fh("VolumeDown",''),aB=fh("VolumeDownFill",''),oB=fh("VolumeMute",''),sB=fh("VolumeMuteFill",''),iB=fh("VolumeOff",''),nB=fh("VolumeOffFill",''),rB=fh("VolumeUp",''),cB=fh("VolumeUpFill",''),lB=fh("Vr",''),hB=fh("Wallet",''),dB=fh("Wallet2",''),mB=fh("WalletFill",''),pB=fh("Watch",''),uB=fh("Water",''),fB=fh("Whatsapp",''),gB=fh("Wifi",''),vB=fh("Wifi1",''),AB=fh("Wifi2",''),PB=fh("WifiOff",''),bB=fh("Wind",''),yB=fh("Window",''),wB=fh("WindowDock",''),IB=fh("WindowSidebar",''),zB=fh("Wrench",''),CB=fh("X",''),DB=fh("XCircle",''),RB=fh("XCircleFill",''),SB=fh("XDiamond",''),_B=fh("XDiamondFill",''),kB=fh("XLg",''),MB=fh("XOctagon",''),TB=fh("XOctagonFill",''),VB=fh("XSquare",''),xB=fh("XSquareFill",''),BB=fh("Youtube",''),LB=fh("ZoomIn",''),OB=fh("ZoomOut",'');function EB(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function UB(e){for(var t=1;t1?a-1:0),s=1;se.length)&&(t=e.length);for(var a=0,o=new Array(t);a0&&void 0!==arguments[0]?arguments[0]:"";return String(e).replace(j,"")},yO=function(e,t){return e?{innerHTML:e}:t?{textContent:t}:{}};function wO(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function IO(e){for(var t=1;t-1&&(t=t.slice(0,a).reverse(),Sc(t[0]))},focusNext:function(e){var t=this.getItems(),a=t.indexOf(e.target);a>-1&&(t=t.slice(a+1),Sc(t[0]))},focusLast:function(){var e=this.getItems().reverse();Sc(e[0])},onFocusin:function(e){var t=this.$el;e.target!==t||hc(t,e.relatedTarget)||(ol(e),this.focusFirst(e))},onKeydown:function(e){var t=e.keyCode,a=e.shiftKey;t===oL||t===XB?(ol(e),a?this.focusFirst(e):this.focusPrev(e)):t!==qB&&t!==tL||(ol(e),a?this.focusLast(e):this.focusNext(e))}},render:function(e){var t=this.keyNav;return e("div",{staticClass:"btn-toolbar",class:{"justify-content-between":this.justify},attrs:{role:"toolbar",tabindex:t?"0":null},on:t?{focusin:this.onFocusin,keydown:this.onKeydown}:{}},[this.normalizeSlot()])}}),NO=Ft({components:{BButtonToolbar:WO,BBtnToolbar:WO}}),$O="gregory",qO="long",JO="narrow",KO="short",QO="2-digit",YO="numeric";function XO(e,t){return oE(e)||aE(e,t)||eE(e,t)||ZO()}function ZO(){throw new TypeError("Invalid attempt to destructure non-iterable instance.\nIn order to be iterable, non-array objects must have a [Symbol.iterator]() method.")}function eE(e,t){if(e){if("string"===typeof e)return tE(e,t);var a=Object.prototype.toString.call(e).slice(8,-1);return"Object"===a&&e.constructor&&(a=e.constructor.name),"Map"===a||"Set"===a?Array.from(e):"Arguments"===a||/^(?:Ui|I)nt(?:8|16|32)(?:Clamped)?Array$/.test(a)?tE(e,t):void 0}}function tE(e,t){(null==t||t>e.length)&&(t=e.length);for(var a=0,o=new Array(t);a1&&void 0!==arguments[1]?arguments[1]:$O;e=Dr(e).filter(yt);var a=new Intl.DateTimeFormat(e,{calendar:t});return a.resolvedOptions().locale},mE=function(e,t){var a=new Intl.DateTimeFormat(e,t);return a.format},pE=function(e,t){return hE(e)===hE(t)},uE=function(e){return e=cE(e),e.setDate(1),e},fE=function(e){return e=cE(e),e.setMonth(e.getMonth()+1),e.setDate(0),e},gE=function(e,t){e=cE(e);var a=e.getMonth();return e.setFullYear(e.getFullYear()+t),e.getMonth()!==a&&e.setDate(0),e},vE=function(e){e=cE(e);var t=e.getMonth();return e.setMonth(t-1),e.getMonth()===t&&e.setDate(0),e},AE=function(e){e=cE(e);var t=e.getMonth();return e.setMonth(t+1),e.getMonth()===(t+2)%12&&e.setDate(0),e},PE=function(e){return gE(e,-1)},bE=function(e){return gE(e,1)},yE=function(e){return gE(e,-10)},wE=function(e){return gE(e,10)},IE=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:null,a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:null;return e=lE(e),t=lE(t)||e,a=lE(a)||e,e?ea?a:e:null},zE=["ar","az","ckb","fa","he","ks","lrc","mzn","ps","sd","te","ug","ur","yi"].map((function(e){return e.toLowerCase()})),CE=function(e){var t=jr(e).toLowerCase().replace(me,"").split("-"),a=t.slice(0,2).join("-"),o=t[0];return Cr(zE,a)||Cr(zE,o)},DE={id:Wc(Zi)},RE=Ms({props:DE,data:function(){return{localId_:null}},computed:{safeId:function(){var e=this.id||this.localId_,t=function(t){return e?(t=String(t||"").replace(/\s+/g,"_"),t?e+"_"+t:e):null};return t}},mounted:function(){var e=this;this.$nextTick((function(){e.localId_="__BVID__".concat(e[Rs])}))}});function SE(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function _E(e){for(var t=1;tt}},dateDisabled:function(){var e=this,t=this.dateOutOfRange;return function(a){a=lE(a);var o=hE(a);return!(!t(a)&&!e.computedDateDisabledFn(o,a))}},formatDateString:function(){return mE(this.calendarLocale,_E(_E({year:YO,month:QO,day:QO},this.dateFormatOptions),{},{hour:void 0,minute:void 0,second:void 0,calendar:$O}))},formatYearMonth:function(){return mE(this.calendarLocale,{year:YO,month:qO,calendar:$O})},formatWeekdayName:function(){return mE(this.calendarLocale,{weekday:qO,calendar:$O})},formatWeekdayNameShort:function(){return mE(this.calendarLocale,{weekday:this.weekdayHeaderFormat||KO,calendar:$O})},formatDay:function(){var e=new Intl.NumberFormat([this.computedLocale],{style:"decimal",minimumIntegerDigits:1,minimumFractionDigits:0,maximumFractionDigits:0,notation:"standard"});return function(t){return e.format(t.getDate())}},prevDecadeDisabled:function(){var e=this.computedMin;return this.disabled||e&&fE(yE(this.activeDate))e},nextYearDisabled:function(){var e=this.computedMax;return this.disabled||e&&uE(bE(this.activeDate))>e},nextDecadeDisabled:function(){var e=this.computedMax;return this.disabled||e&&uE(wE(this.activeDate))>e},calendar:function(){for(var e=[],t=this.calendarFirstDay,a=t.getFullYear(),o=t.getMonth(),s=this.calendarDaysInMonth,i=t.getDay(),n=(this.computedWeekStarts>i?7:0)-this.computedWeekStarts,r=0-n-i,c=0;c<6&&r0);a!==this.visible&&(this.visible=a,this.callback(a),this.once&&this.visible&&(this.doneOnce=!0,this.stop()))}},{key:"stop",value:function(){this.observer&&this.observer.disconnect(),this.observer=null}}]),e}(),RU=function(e){var t=e[CU];t&&t.stop&&t.stop(),delete e[CU]},SU=function(e,t){var a=t.value,o=t.modifiers,s={margin:"0px",once:!1,callback:a};at(o).forEach((function(e){E.test(e)?s.margin="".concat(e,"px"):"once"===e.toLowerCase()&&(s.once=!0)})),RU(e),e[CU]=new DU(e,s),e[CU]._prevModifiers=it(o)},_U=function(e,t,a){var o=t.value,s=t.oldValue,i=t.modifiers;i=it(i),!e||o===s&&e[CU]&&iL(i,e[CU]._prevModifiers)||SU(e,{value:o,modifiers:i},a)},kU=function(e){RU(e)},MU={bind:SU,componentUpdated:_U,unbind:kU};function TU(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function VU(e){for(var t=1;t0||s.removedNodes.length>0))&&(a=!0)}a&&t()}));return o.observe(e,XU({childList:!0,subtree:!0},a)),o};function aF(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function oF(e){for(var t=1;t0),touchStartX:0,touchDeltaX:0}},computed:{numSlides:function(){return this.slides.length}},watch:(eF={},sF(eF,cF,(function(e,t){e!==t&&this.setSlide(Vr(e,0))})),sF(eF,"interval",(function(e,t){e!==t&&(e?(this.pause(!0),this.start(!1)):this.pause(!1))})),sF(eF,"isPaused",(function(e,t){e!==t&&this.$emit(e?gi:Li)})),sF(eF,"index",(function(e,t){e===t||this.isSliding||this.doSlide(e,t)})),eF),created:function(){this.$_interval=null,this.$_animationTimeout=null,this.$_touchTimeout=null,this.$_observer=null,this.isPaused=!(Vr(this.interval,0)>0)},mounted:function(){this.transitionEndEvent=gF(this.$el)||null,this.updateSlides(),this.setObserver(!0)},beforeDestroy:function(){this.clearInterval(),this.clearAnimationTimeout(),this.clearTouchTimeout(),this.setObserver(!1)},methods:{clearInterval:function(e){function t(){return e.apply(this,arguments)}return t.toString=function(){return e.toString()},t}((function(){clearInterval(this.$_interval),this.$_interval=null})),clearAnimationTimeout:function(){clearTimeout(this.$_animationTimeout),this.$_animationTimeout=null},clearTouchTimeout:function(){clearTimeout(this.$_touchTimeout),this.$_touchTimeout=null},setObserver:function(){var e=arguments.length>0&&void 0!==arguments[0]&&arguments[0];this.$_observer&&this.$_observer.disconnect(),this.$_observer=null,e&&(this.$_observer=tF(this.$refs.inner,this.updateSlides.bind(this),{subtree:!1,childList:!0,attributes:!0,attributeFilter:["id"]}))},setSlide:function(e){var t=this,a=arguments.length>1&&void 0!==arguments[1]?arguments[1]:null;if(!(I&&document.visibilityState&&document.hidden)){var o=this.noWrap,s=this.numSlides;e=Bl(e),0!==s&&(this.isSliding?this.$once(Mi,(function(){Qr((function(){return t.setSlide(e,a)}))})):(this.direction=a,this.index=e>=s?o?s-1:0:e<0?o?0:s-1:e,o&&this.index!==e&&this.index!==this[cF]&&this.$emit(lF,this.index)))}},prev:function(){this.setSlide(this.index-1,"prev")},next:function(){this.setSlide(this.index+1,"next")},pause:function(e){e||(this.isPaused=!0),this.clearInterval()},start:function(e){e||(this.isPaused=!1),this.clearInterval(),this.interval&&this.numSlides>1&&(this.$_interval=setInterval(this.next,Tl(1e3,this.interval)))},restart:function(){this.$el.contains(ec())||this.start()},doSlide:function(e,t){var a=this,o=Boolean(this.interval),s=this.calcDirection(this.direction,t,e),i=s.overlayClass,n=s.dirClass,r=this.slides[t],c=this.slides[e];if(r&&c){if(this.isSliding=!0,o&&this.pause(!1),this.$emit(Ti,e),this.$emit(lF,this.index),this.noAnimation)mc(c,"active"),pc(r,"active"),this.isSliding=!1,this.$nextTick((function(){return a.$emit(Mi,e)}));else{mc(c,i),ic(c),mc(r,n),mc(c,n);var l=!1,h=function t(){if(!l){if(l=!0,a.transitionEndEvent){var o=a.transitionEndEvent.split(/\s+/);o.forEach((function(e){return tl(c,e,t,Wi)}))}a.clearAnimationTimeout(),pc(c,n),pc(c,i),mc(c,"active"),pc(r,"active"),pc(r,n),pc(r,i),fc(r,"aria-current","false"),fc(c,"aria-current","true"),fc(r,"aria-hidden","true"),fc(c,"aria-hidden","false"),a.isSliding=!1,a.direction=null,a.$nextTick((function(){return a.$emit(Mi,e)}))}};if(this.transitionEndEvent){var d=this.transitionEndEvent.split(/\s+/);d.forEach((function(e){return el(c,e,h,Wi)}))}this.$_animationTimeout=setTimeout(h,dF)}o&&this.start(!1)}},updateSlides:function(){this.pause(!0),this.slides=nc(".carousel-item",this.$refs.inner);var e=this.slides.length,t=Tl(0,Ml(Bl(this.index),e-1));this.slides.forEach((function(a,o){var s=o+1;o===t?(mc(a,"active"),fc(a,"aria-current","true")):(pc(a,"active"),fc(a,"aria-current","false")),fc(a,"aria-posinset",String(s)),fc(a,"aria-setsize",String(e))})),this.setSlide(t),this.start(this.isPaused)},calcDirection:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:null,t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:0,a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:0;return e?hF[e]:a>t?hF.next:hF.prev},handleClick:function(e,t){var a=e.keyCode;"click"!==e.type&&a!==aL&&a!==KB||(ol(e),t())},handleSwipe:function(){var e=Vl(this.touchDeltaX);if(!(e<=pF)){var t=e/this.touchDeltaX;this.touchDeltaX=0,t>0?this.prev():t<0&&this.next()}},touchStart:function(e){M&&uF[e.pointerType.toUpperCase()]?this.touchStartX=e.clientX:M||(this.touchStartX=e.touches[0].clientX)},touchMove:function(e){e.touches&&e.touches.length>1?this.touchDeltaX=0:this.touchDeltaX=e.touches[0].clientX-this.touchStartX},touchEnd:function(e){M&&uF[e.pointerType.toUpperCase()]&&(this.touchDeltaX=e.clientX-this.touchStartX),this.handleSwipe(),this.pause(!1),this.clearTouchTimeout(),this.$_touchTimeout=setTimeout(this.start,mF+Tl(1e3,this.interval))}},render:function(e){var t=this,a=this.indicators,o=this.background,s=this.noAnimation,i=this.noHoverPause,n=this.noTouch,r=this.index,c=this.isSliding,l=this.pause,h=this.restart,d=this.touchStart,m=this.touchEnd,p=this.safeId("__BV_inner_"),u=e("div",{staticClass:"carousel-inner",attrs:{id:p,role:"list"},ref:"inner"},[this.normalizeSlot()]),f=e();if(this.controls){var g=function(a,o,s){var i=function(e){c?ol(e,{propagation:!1}):t.handleClick(e,s)};return e("a",{staticClass:"carousel-control-".concat(a),attrs:{href:"#",role:"button","aria-controls":p,"aria-disabled":c?"true":null},on:{click:i,keydown:i}},[e("span",{staticClass:"carousel-control-".concat(a,"-icon"),attrs:{"aria-hidden":"true"}}),e("span",{class:"sr-only"},[o])])};f=[g("prev",this.labelPrev,this.prev),g("next",this.labelNext,this.next)]}var v=e("ol",{staticClass:"carousel-indicators",directives:[{name:"show",value:a}],attrs:{id:this.safeId("__BV_indicators_"),"aria-hidden":a?"false":"true","aria-label":this.labelIndicators,"aria-owns":p}},this.slides.map((function(o,s){var i=function(e){t.handleClick(e,(function(){t.setSlide(s)}))};return e("li",{class:{active:s===r},attrs:{role:"button",id:t.safeId("__BV_indicator_".concat(s+1,"_")),tabindex:a?"0":"-1","aria-current":s===r?"true":"false","aria-label":"".concat(t.labelGotoSlide," ").concat(s+1),"aria-describedby":o.id||null,"aria-controls":p},on:{click:i,keydown:i},key:"slide_".concat(s)})}))),A={mouseenter:i?QU:l,mouseleave:i?QU:h,focusin:l,focusout:h,keydown:function(e){if(!/input|textarea/i.test(e.target.tagName)){var a=e.keyCode;a!==XB&&a!==tL||(ol(e),t[a===XB?"prev":"next"]())}}};return k&&!n&&(M?(A["&pointerdown"]=d,A["&pointerup"]=m):(A["&touchstart"]=d,A["&touchmove"]=this.touchMove,A["&touchend"]=m)),e("div",{staticClass:"carousel",class:{slide:!s,"carousel-fade":!s&&this.fade,"pointer-event":k&&M&&!n},style:{background:o},attrs:{role:"region",id:this.safeId(),"aria-busy":c?"true":"false"},on:A},[u,f,v])}});function PF(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function bF(e){for(var t=1;t0?(fc(e,rH,o.join(" ")),Pc(e,dH,"none")):(gc(e,rH),bc(e,dH)),Qr((function(){bH(e,YF(a,t))})),iL(o,e[sH])||(e[sH]=o,o.forEach((function(e){gL(YF(a,t)).$emit(fH,e)})))}},DH={bind:function(e,t,a){e[oH]=!1,e[sH]=[],wH(e,YF(a,t)),CH(e,t,a)},componentUpdated:CH,updated:CH,unbind:function(e,t,a){PH(e),yH(e,YF(a,t)),zH(e,tH),zH(e,aH),zH(e,oH),zH(e,sH),pc(e,XF),pc(e,ZF),gc(e,cH),gc(e,rH),gc(e,lH),bc(e,dH)}},RH=Ft({directives:{VBToggle:DH}}),SH=Ft({components:{BCollapse:QF},plugins:{VBTogglePlugin:RH}}),_H=a("f0bd"),kH="top-start",MH="top-end",TH="bottom-start",VH="bottom-end",xH="right-start",BH="left-start";function LH(e,t){if(!(e instanceof t))throw new TypeError("Cannot call a class as a function")}function OH(e,t){for(var a=0;a1&&void 0!==arguments[1]?arguments[1]:{};if(LH(this,e),!t)throw new TypeError("Failed to construct '".concat(this.constructor.name,"'. 1 argument required, ").concat(arguments.length," given."));Ye(this,e.Defaults,this.constructor.Defaults,a,{type:t}),Ze(this,{type:ht(),cancelable:ht(),nativeEvent:ht(),target:ht(),relatedTarget:ht(),vueTarget:ht(),componentId:ht()});var o=!1;this.preventDefault=function(){this.cancelable&&(o=!0)},et(this,"defaultPrevented",{enumerable:!0,get:function(){return o}})}return EH(e,null,[{key:"Defaults",get:function(){return{type:"",cancelable:!0,nativeEvent:null,target:null,relatedTarget:null,vueTarget:null,componentId:null}}}]),e}(),FH=Ms({data:function(){return{listenForClickOut:!1}},watch:{listenForClickOut:function(e,t){e!==t&&(tl(this.clickOutElement,this.clickOutEventName,this._clickOutHandler,Wi),e&&el(this.clickOutElement,this.clickOutEventName,this._clickOutHandler,Wi))}},beforeCreate:function(){this.clickOutElement=null,this.clickOutEventName=null},mounted:function(){this.clickOutElement||(this.clickOutElement=document),this.clickOutEventName||(this.clickOutEventName="click"),this.listenForClickOut&&el(this.clickOutElement,this.clickOutEventName,this._clickOutHandler,Wi)},beforeDestroy:function(){tl(this.clickOutElement,this.clickOutEventName,this._clickOutHandler,Wi)},methods:{isClickOut:function(e){return!hc(this.$el,e.target)},_clickOutHandler:function(e){this.clickOutHandler&&this.isClickOut(e)&&this.clickOutHandler(e)}}}),HH=Ms({data:function(){return{listenForFocusIn:!1}},watch:{listenForFocusIn:function(e,t){e!==t&&(tl(this.focusInElement,"focusin",this._focusInHandler,Wi),e&&el(this.focusInElement,"focusin",this._focusInHandler,Wi))}},beforeCreate:function(){this.focusInElement=null},mounted:function(){this.focusInElement||(this.focusInElement=document),this.listenForFocusIn&&el(this.focusInElement,"focusin",this._focusInHandler,Wi)},beforeDestroy:function(){tl(this.focusInElement,"focusin",this._focusInHandler,Wi)},methods:{_focusInHandler:function(e){this.focusInHandler&&this.focusInHandler(e)}}}),jH=null;Ss&&(jH=new WeakMap);var GH=function(e,t){Ss&&jH.set(e,t)},WH=function(e){Ss&&jH.delete(e)},NH=function(e){if(!Ss)return e.__vue__;var t=e;while(t){if(jH.has(t))return jH.get(t);t=t.parentNode}return null};function $H(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function qH(e){for(var t=1;t0&&void 0!==arguments[0]&&arguments[0];this.disabled||(this.visible=!1,e&&this.$once(ii,this.focusToggler))},toggle:function(e){e=e||{};var t=e,a=t.type,o=t.keyCode;("click"===a||"keydown"===a&&-1!==[KB,aL,qB].indexOf(o))&&(this.disabled?this.visible=!1:(this.$emit(Bi,e),ol(e),this.visible?this.hide(!0):this.show()))},onMousedown:function(e){ol(e,{propagation:!1})},onKeydown:function(e){var t=e.keyCode;t===QB?this.onEsc(e):t===qB?this.focusNext(e,!1):t===oL&&this.focusNext(e,!0)},onEsc:function(e){this.visible&&(this.visible=!1,ol(e),this.$once(ii,this.focusToggler))},onSplitClick:function(e){this.disabled?this.visible=!1:this.$emit(js,e)},hideHandler:function(e){var t=this,a=e.target;!this.visible||hc(this.$refs.menu,a)||hc(this.toggler,a)||(this.clearHideTimeout(),this.$_hideTimeout=setTimeout((function(){return t.hide()}),this.hideDelay))},clickOutHandler:function(e){this.hideHandler(e)},focusInHandler:function(e){this.hideHandler(e)},focusNext:function(e,t){var a=this,o=e.target;!this.visible||e&&lc(YH,o)||(ol(e),this.$nextTick((function(){var e=a.getItems();if(!(e.length<1)){var s=e.indexOf(o);t&&s>0?s--:!t&&s1&&void 0!==arguments[1]?arguments[1]:null;if(je(e)){var a=It(e,this.valueField),o=It(e,this.textField);return{value:Te(a)?t||o:a,text:bO(String(Te(o)?t:o)),html:It(e,this.htmlField),disabled:Boolean(It(e,this.disabledField))}}return{value:t||e,text:bO(String(e)),disabled:!1}},normalizeOptions:function(e){var t=this;return Fe(e)?e.map((function(e){return t.normalizeOption(e)})):je(e)?(Ct(Kj,this.$options.name),at(e).map((function(a){return t.normalizeOption(e[a]||{},a)}))):[]}}});function Xj(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Zj(e){for(var t=1;t-1:iL(t,e)},isRadio:function(){return!1}},watch:EG({},FG,(function(e,t){iL(e,t)||this.setIndeterminate(e)})),mounted:function(){this.setIndeterminate(this[FG])},methods:{computedLocalCheckedWatcher:function(e,t){if(!iL(e,t)){this.$emit(VG,e);var a=this.$refs.input;a&&this.$emit(HG,a.indeterminate)}},handleChange:function(e){var t=this,a=e.target,o=a.checked,s=a.indeterminate,i=this.value,n=this.uncheckedValue,r=this.computedLocalChecked;if(Fe(r)){var c=fG(r,i);o&&c<0?r=r.concat(i):!o&&c>-1&&(r=r.slice(0,c).concat(r.slice(c+1)))}else r=o?i:n;this.computedLocalChecked=r,this.$nextTick((function(){t.$emit(Fs,r),t.isGroup&&t.bvGroup.$emit(Fs,r),t.$emit(HG,s)}))},setIndeterminate:function(e){Fe(this.computedLocalChecked)&&(e=!1);var t=this.$refs.input;t&&(t.indeterminate=e,this.$emit(HG,e))}}}),WG=Jc(xG,Ua),NG=Ms({name:Ua,mixins:[BG],inject:{getBvGroup:{from:"getBvRadioGroup",default:function(){return function(){return null}}}},props:WG,computed:{bvGroup:function(){return this.getBvGroup()}}});function $G(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function qG(e){for(var t=1;t0&&(c=[e("div",{staticClass:"b-form-date-controls d-flex flex-wrap",class:{"justify-content-between":c.length>1,"justify-content-end":c.length<2}},c)]);var m=e(OE,{staticClass:"b-form-date-calendar w-100",props:zW(zW({},$c(TW,i)),{},{hidden:!this.isVisible,value:t,valueAsDate:!1,width:this.calendarWidth}),on:{selected:this.onSelected,input:this.onInput,context:this.onContext},scopedSlots:nt(n,["nav-prev-decade","nav-prev-year","nav-prev-month","nav-this-month","nav-next-month","nav-next-year","nav-next-decade"]),key:"calendar",ref:"calendar"},c);return e(wW,{staticClass:"b-form-datepicker",props:zW(zW({},$c(VW,i)),{},{formattedValue:t?this.formattedValue:"",id:this.safeId(),lang:this.computedLang,menuClass:[{"bg-dark":s,"text-light":s},this.menuClass],placeholder:r,rtl:this.isRTL,value:t}),on:{show:this.onShow,shown:this.onShown,hidden:this.onHidden},scopedSlots:CW({},Pn,n[Pn]||this.defaultButtonFn),ref:"control"},[m])}}),LW=Ft({components:{BFormDatepicker:BW,BDatepicker:BW}});function OW(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function EW(e){for(var t=1;t1&&void 0!==arguments[1])||arguments[1];return Promise.all(zr(e).filter((function(e){return"file"===e.kind})).map((function(e){var a=qW(e);if(a){if(a.isDirectory&&t)return KW(a.createReader(),"".concat(a.name,"/"));if(a.isFile)return new Promise((function(e){a.file((function(t){t.$path="",e(t)}))}))}return null})).filter(yt))},KW=function e(t){var a=arguments.length>1&&void 0!==arguments[1]?arguments[1]:"";return new Promise((function(o){var s=[],i=function i(){t.readEntries((function(t){0===t.length?o(Promise.all(s).then((function(e){return Sr(e)}))):(s.push(Promise.all(t.map((function(t){if(t){if(t.isDirectory)return e(t.createReader(),"".concat(a).concat(t.name,"/"));if(t.isFile)return new Promise((function(e){t.file((function(t){t.$path="".concat(a).concat(t.name),e(t)}))}))}return null})).filter(yt))),i())}))};i()}))},QW=Jc(lt(EW(EW(EW(EW(EW(EW(EW({},DE),jW),vG),PG),IG),yG),{},{accept:Wc(Zi,""),browseText:Wc(Zi,"Browse"),capture:Wc(qi,!1),directory:Wc(qi,!1),dropPlaceholder:Wc(Zi,"Drop files here"),fileNameFormatter:Wc(Ki),multiple:Wc(qi,!1),noDrop:Wc(qi,!1),noDropPlaceholder:Wc(Zi,"Not allowed"),noTraverse:Wc(qi,!1),placeholder:Wc(Zi,"No file chosen")})),Ba),YW=Ms({name:Ba,mixins:[fL,RE,HW,Tr,AG,zG,bG,Tr],inheritAttrs:!1,props:QW,data:function(){return{files:[],dragging:!1,dropAllowed:!this.noDrop,hasFocus:!1}},computed:{computedAccept:function(){var e=this.accept;return e=(e||"").trim().split(/[,\s]+/).filter(yt),0===e.length?null:e.map((function(e){var t="name",a="^",o="$";U.test(e)?a="":(t="type",Q.test(e)&&(o=".+$",e=e.slice(0,-1))),e=Hr(e);var s=new RegExp("".concat(a).concat(e).concat(o));return{rx:s,prop:t}}))},computedCapture:function(){var e=this.capture;return!0===e||""===e||(e||null)},computedAttrs:function(){var e=this.name,t=this.disabled,a=this.required,o=this.form,s=this.computedCapture,i=this.accept,n=this.multiple,r=this.directory;return EW(EW({},this.bvAttrs),{},{type:"file",id:this.safeId(),name:e,disabled:t,required:a,form:o||null,capture:s,accept:i||null,multiple:n,directory:r,webkitdirectory:r,"aria-required":a?"true":null})},computedFileNameFormatter:function(){var e=this.fileNameFormatter;return Qc(e)?e:this.defaultFileNameFormatter},clonedFiles:function(){return bt(this.files)},flattenedFiles:function(){return _r(this.files)},fileNames:function(){return this.flattenedFiles.map((function(e){return e.name}))},labelContent:function(){if(this.dragging&&!this.noDrop)return this.normalizeSlot(Cn,{allowed:this.dropAllowed})||(this.dropAllowed?this.dropPlaceholder:this.$createElement("span",{staticClass:"text-danger"},this.noDropPlaceholder));if(0===this.files.length)return this.normalizeSlot(lr)||this.placeholder;var e=this.flattenedFiles,t=this.clonedFiles,a=this.fileNames,o=this.computedFileNameFormatter;return this.hasNormalizedSlot(_n)?this.normalizeSlot(_n,{files:e,filesTraversed:t,names:a}):o(e,t,a)}},watch:(DW={},UW(DW,GW,(function(e){(!e||Fe(e)&&0===e.length)&&this.reset()})),UW(DW,"files",(function(e,t){if(!iL(e,t)){var a=this.multiple,o=this.noTraverse,s=!a||o?_r(e):e;this.$emit(WW,a?s:s[0]||null)}})),DW),created:function(){this.$_form=null},mounted:function(){var e=lc("form",this.$el);e&&(el(e,"reset",this.reset,Gi),this.$_form=e)},beforeDestroy:function(){var e=this.$_form;e&&tl(e,"reset",this.reset,Gi)},methods:{isFileValid:function(e){if(!e)return!1;var t=this.computedAccept;return!t||t.some((function(t){return t.rx.test(e[t.prop])}))},isFilesArrayValid:function(e){var t=this;return Fe(e)?e.every((function(e){return t.isFileValid(e)})):this.isFileValid(e)},defaultFileNameFormatter:function(e,t,a){return a.join(", ")},setFiles:function(e){this.dropAllowed=!this.noDrop,this.dragging=!1,this.files=this.multiple?this.directory?e:_r(e):_r(e).slice(0,1)},setInputFiles:function(e){try{var t=new ClipboardEvent("").clipboardData||new DataTransfer;_r(bt(e)).forEach((function(e){delete e.$path,t.items.add(e)})),this.$refs.input.files=t.files}catch(a){}},reset:function(){try{var e=this.$refs.input;e.value="",e.type="",e.type="file"}catch(t){}this.files=[]},handleFiles:function(e){var t=arguments.length>1&&void 0!==arguments[1]&&arguments[1];if(t){var a=e.filter(this.isFilesArrayValid);a.length>0&&(this.setFiles(a),this.setInputFiles(a))}else this.setFiles(e)},focusHandler:function(e){this.plain||"focusout"===e.type?this.hasFocus=!1:this.hasFocus=!0},onChange:function(e){var t=this,a=e.type,o=e.target,s=e.dataTransfer,i=void 0===s?{}:s,n="drop"===a;this.$emit(Fs,e);var r=zr(i.items||[]);if(y&&r.length>0&&!Ve(qW(r[0])))JW(r,this.directory).then((function(e){return t.handleFiles(e,n)}));else{var c=zr(o.files||i.files||[]).map((function(e){return e.$path=e.webkitRelativePath||"",e}));this.handleFiles(c,n)}},onDragenter:function(e){ol(e),this.dragging=!0;var t=e.dataTransfer,a=void 0===t?{}:t;if(this.noDrop||this.disabled||!this.dropAllowed)return a.dropEffect="none",void(this.dropAllowed=!1);a.dropEffect="copy"},onDragover:function(e){ol(e),this.dragging=!0;var t=e.dataTransfer,a=void 0===t?{}:t;if(this.noDrop||this.disabled||!this.dropAllowed)return a.dropEffect="none",void(this.dropAllowed=!1);a.dropEffect="copy"},onDragleave:function(e){var t=this;ol(e),this.$nextTick((function(){t.dragging=!1,t.dropAllowed=!t.noDrop}))},onDrop:function(e){var t=this;ol(e),this.dragging=!1,this.noDrop||this.disabled||!this.dropAllowed?this.$nextTick((function(){t.dropAllowed=!t.noDrop})):this.onChange(e)}},render:function(e){var t=this.custom,a=this.plain,o=this.size,s=this.dragging,i=this.stateClass,n=this.bvAttrs,r=e("input",{class:[{"form-control-file":a,"custom-file-input":t,focus:t&&this.hasFocus},i],style:t?{zIndex:-5}:{},attrs:this.computedAttrs,on:{change:this.onChange,focusin:this.focusHandler,focusout:this.focusHandler,reset:this.reset},ref:"input"});if(a)return r;var c=e("label",{staticClass:"custom-file-label",class:{dragging:s},attrs:{for:this.safeId(),"data-browse":this.browseText||null}},[e("span",{staticClass:"d-block form-file-text",style:{pointerEvents:"none"}},[this.labelContent])]);return e("div",{staticClass:"custom-file b-form-file",class:[UW({},"b-custom-control-".concat(o),o),i,n.class],style:n.style,attrs:{id:this.safeId("_BV_file_outer_")},on:{dragenter:this.onDragenter,dragover:this.onDragover,dragleave:this.onDragleave,drop:this.onDrop}},[r,c])}}),XW=Ft({components:{BFormFile:YW,BFile:YW}}),ZW=function(e){return"\\"+e},eN=function(e){e=jr(e);var t=e.length,a=e.charCodeAt(0);return e.split("").reduce((function(o,s,i){var n=e.charCodeAt(i);return 0===n?o+"�":127===n||n>=1&&n<=31||0===i&&n>=48&&n<=57||1===i&&n>=48&&n<=57&&45===a?o+ZW("".concat(n.toString(16)," ")):0===i&&45===n&&1===t?o+ZW(s):n>=128||45===n||95===n||n>=48&&n<=57||n>=65&&n<=90||n>=97&&n<=122?o+s:o+ZW(s)}),"")};function tN(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function aN(e){for(var t=1;t0||at(this.labelColProps).length>0}},watch:{ariaDescribedby:function(e,t){e!==t&&this.updateAriaDescribedby(e,t)}},mounted:function(){var e=this;this.$nextTick((function(){e.updateAriaDescribedby(e.ariaDescribedby)}))},methods:{getAlignClasses:function(e,t){return Oc().reduce((function(a,o){var s=e[Gc(o,"".concat(t,"Align"))]||null;return s&&a.push(["text",o,s].filter(yt).join("-")),a}),[])},getColProps:function(e,t){return Oc().reduce((function(a,o){var s=e[Gc(o,"".concat(t,"Cols"))];return s=""===s||(s||!1),Le(s)||"auto"===s||(s=Vr(s,0),s=s>0&&s),s&&(a[o||(Le(s)?"col":"cols")]=s),a}),{})},updateAriaDescribedby:function(e,t){var a=this.labelFor;if(I&&a){var o=rc("#".concat(eN(a)),this.$refs.content);if(o){var s="aria-describedby",i=(e||"").split(K),n=(t||"").split(K),r=(vc(o,s)||"").split(K).filter((function(e){return!Cr(n,e)})).concat(i).filter((function(e,t,a){return a.indexOf(e)===t})).filter(yt).join(" ").trim();r?fc(o,s,r):gc(o,s)}}},onLegendClick:function(e){if(!this.labelFor){var t=e.target,a=t?t.tagName:"";if(-1===fN.indexOf(a)){var o=nc(uN,this.$refs.content).filter(oc);1===o.length&&Sc(o[0])}}}},render:function(e){var t=this.computedState,a=this.feedbackAriaLive,o=this.isHorizontal,s=this.labelFor,i=this.normalizeSlot,n=this.safeId,r=this.tooltip,c=n(),l=!s,h=e(),d=i(jn)||this.label,m=d?n("_BV_label_"):null;if(d||o){var p=this.labelSize,u=this.labelColProps,f=l?"legend":"label";this.labelSrOnly?(d&&(h=e(f,{class:"sr-only",attrs:{id:m,for:s||null}},[d])),h=e(o?lN:"div",{props:o?u:{}},[h])):h=e(o?lN:f,{on:l?{click:this.onLegendClick}:{},props:o?dN(dN({},u),{},{tag:f}):{},attrs:{id:m,for:s||null,tabindex:l?"-1":null},class:[l?"bv-no-focus-ring":"",o||l?"col-form-label":"",!o&&l?"pt-0":"",o||l?"":"d-block",p?"col-form-label-".concat(p):"",this.labelAlignClasses,this.labelClass]},[d])}var g=e(),v=i(Hn)||this.invalidFeedback,A=v?n("_BV_feedback_invalid_"):null;v&&(g=e(lG,{props:{ariaLive:a,id:A,state:t,tooltip:r},attrs:{tabindex:v?"-1":null}},[v]));var P=e(),b=i(Ir)||this.validFeedback,y=b?n("_BV_feedback_valid_"):null;b&&(P=e(dG,{props:{ariaLive:a,id:y,state:t,tooltip:r},attrs:{tabindex:b?"-1":null}},[b]));var w=e(),I=i(In)||this.description,z=I?n("_BV_description_"):null;I&&(w=e(rG,{attrs:{id:z,tabindex:"-1"}},[I]));var C=this.ariaDescribedby=[z,!1===t?A:null,!0===t?y:null].filter(yt).join(" ")||null,D=e(o?lN:"div",{props:o?this.contentColProps:{},ref:"content"},[i(wn,{ariaDescribedby:C,descriptionId:z,id:c,labelId:m})||e(),g,P,w]);return e(l?"fieldset":o?pG:"div",{staticClass:"form-group",class:[{"was-validated":this.validated},this.stateClass],attrs:{id:c,disabled:l?this.disabled:null,role:l?null:"group","aria-invalid":this.computedAriaInvalid,"aria-labelledby":l&&o?m:null}},o&&l?[e(pG,[h,D])]:[h,D])}},AN=Ft({components:{BFormGroup:vN,BFormFieldset:vN}}),PN=Ms({computed:{selectionStart:{cache:!1,get:function(){return this.$refs.input.selectionStart},set:function(e){this.$refs.input.selectionStart=e}},selectionEnd:{cache:!1,get:function(){return this.$refs.input.selectionEnd},set:function(e){this.$refs.input.selectionEnd=e}},selectionDirection:{cache:!1,get:function(){return this.$refs.input.selectionDirection},set:function(e){this.$refs.input.selectionDirection=e}}},methods:{select:function(){var e;(e=this.$refs.input).select.apply(e,arguments)},setSelectionRange:function(){var e;(e=this.$refs.input).setSelectionRange.apply(e,arguments)},setRangeText:function(){var e;(e=this.$refs.input).setRangeText.apply(e,arguments)}}});function bN(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function yN(e){for(var t=1;t2&&void 0!==arguments[2]&&arguments[2];return e=jr(e),!this.hasFormatter||this.lazyFormatter&&!a||(e=this.formatter(e,t)),e},modifyValue:function(e){return e=jr(e),this.trim&&(e=e.trim()),this.number&&(e=xr(e,e)),e},updateValue:function(e){var t=this,a=arguments.length>1&&void 0!==arguments[1]&&arguments[1],o=this.lazy;if(!o||a){this.clearDebounce();var s=function(){if(e=t.modifyValue(e),e!==t.vModelValue)t.vModelValue=e,t.$emit(RN,e);else if(t.hasFormatter){var a=t.$refs.input;a&&e!==a.value&&(a.value=e)}},i=this.computedDebounce;i>0&&!o&&!a?this.$_inputDebounceTimer=setTimeout(s,i):s()}},onInput:function(e){if(!e.target.composing){var t=e.target.value,a=this.formatValue(t,e);!1===a||e.defaultPrevented?ol(e,{propagation:!1}):(this.localValue=a,this.updateValue(a),this.$emit(ci,a))}},onChange:function(e){var t=e.target.value,a=this.formatValue(t,e);!1===a||e.defaultPrevented?ol(e,{propagation:!1}):(this.localValue=a,this.updateValue(a,!0),this.$emit(Fs,a))},onBlur:function(e){var t=e.target.value,a=this.formatValue(t,e,!0);!1!==a&&(this.localValue=jr(this.modifyValue(a)),this.updateValue(a,!0)),this.$emit(Es,e)},focus:function(){this.disabled||Sc(this.$el)},blur:function(){this.disabled||_c(this.$el)}}}),kN=Ms({computed:{validity:{cache:!1,get:function(){return this.$refs.input.validity}},validationMessage:{cache:!1,get:function(){return this.$refs.input.validationMessage}},willValidate:{cache:!1,get:function(){return this.$refs.input.willValidate}}},methods:{setCustomValidity:function(){var e;return(e=this.$refs.input).setCustomValidity.apply(e,arguments)},checkValidity:function(){var e;return(e=this.$refs.input).checkValidity.apply(e,arguments)},reportValidity:function(){var e;return(e=this.$refs.input).reportValidity.apply(e,arguments)}}});function MN(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function TN(e){for(var t=1;t=a?"full":t>=a-.5?"half":"empty",h={variant:i,disabled:n,readonly:r};return e("span",{staticClass:"b-rating-star",class:{focused:o&&t===a||!Vr(t)&&a===c,"b-rating-star-empty":"empty"===l,"b-rating-star-half":"half"===l,"b-rating-star-full":"full"===l},attrs:{tabindex:n||r?null:"-1"},on:{click:this.onClick}},[e("span",{staticClass:"b-rating-icon"},[this.normalizeSlot(l,h)])])}}),t$=Jc(lt(GN(GN(GN(GN(GN({},DE),qN),rt(vG,["required","autofocus"])),yG),{},{color:Wc(Zi),iconClear:Wc(Zi,"x"),iconEmpty:Wc(Zi,"star"),iconFull:Wc(Zi,"star-fill"),iconHalf:Wc(Zi,"star-half"),inline:Wc(qi,!1),locale:Wc(on),noBorder:Wc(qi,!1),precision:Wc(hn),readonly:Wc(qi,!1),showClear:Wc(qi,!1),showValue:Wc(qi,!1),showValueMax:Wc(qi,!1),stars:Wc(hn,YN,(function(e){return Vr(e)>=QN})),variant:Wc(Zi)})),Ha),a$=Ms({name:Ha,components:{BIconStar:kT,BIconStarHalf:TT,BIconStarFill:MT,BIconX:CB},mixins:[RE,$N,wG],props:t$,data:function(){var e=xr(this[JN],null),t=XN(this.stars);return{localValue:Ve(e)?null:ZN(e,0,t),hasFocus:!1}},computed:{computedStars:function(){return XN(this.stars)},computedRating:function(){var e=xr(this.localValue,0),t=Vr(this.precision,3);return ZN(xr(e.toFixed(t)),0,this.computedStars)},computedLocale:function(){var e=Dr(this.locale).filter(yt),t=new Intl.NumberFormat(e);return t.resolvedOptions().locale},isInteractive:function(){return!this.disabled&&!this.readonly},isRTL:function(){return CE(this.computedLocale)},formattedRating:function(){var e=Vr(this.precision),t=this.showValueMax,a=this.computedLocale,o={notation:"standard",minimumFractionDigits:isNaN(e)?0:e,maximumFractionDigits:isNaN(e)?3:e},s=this.computedStars.toLocaleString(a),i=this.localValue;return i=Ve(i)?t?"-":"":i.toLocaleString(a,o),t?"".concat(i,"/").concat(s):i}},watch:(xN={},WN(xN,JN,(function(e,t){if(e!==t){var a=xr(e,null);this.localValue=Ve(a)?null:ZN(a,0,this.computedStars)}})),WN(xN,"localValue",(function(e,t){e!==t&&e!==(this.value||0)&&this.$emit(KN,e||null)})),WN(xN,"disabled",(function(e){e&&(this.hasFocus=!1,this.blur())})),xN),methods:{focus:function(){this.disabled||Sc(this.$el)},blur:function(){this.disabled||_c(this.$el)},onKeydown:function(e){var t=e.keyCode;if(this.isInteractive&&Cr([XB,qB,tL,oL],t)){ol(e,{propagation:!1});var a=Vr(this.localValue,0),o=this.showClear?0:1,s=this.computedStars,i=this.isRTL?-1:1;t===XB?this.localValue=ZN(a-i,o,s)||null:t===tL?this.localValue=ZN(a+i,o,s):t===qB?this.localValue=ZN(a-1,o,s)||null:t===oL&&(this.localValue=ZN(a+1,o,s))}},onSelected:function(e){this.isInteractive&&(this.localValue=e)},onFocus:function(e){this.hasFocus=!!this.isInteractive&&"focus"===e.type},renderIcon:function(e){return this.$createElement(WB,{props:{icon:e,variant:this.disabled||this.color?null:this.variant||null}})},iconEmptyFn:function(){return this.renderIcon(this.iconEmpty)},iconHalfFn:function(){return this.renderIcon(this.iconHalf)},iconFullFn:function(){return this.renderIcon(this.iconFull)},iconClearFn:function(){return this.$createElement(WB,{props:{icon:this.iconClear}})}},render:function(e){var t=this,a=this.disabled,o=this.readonly,s=this.name,i=this.form,n=this.inline,r=this.variant,c=this.color,l=this.noBorder,h=this.hasFocus,d=this.computedRating,m=this.computedStars,p=this.formattedRating,u=this.showClear,f=this.isRTL,g=this.isInteractive,v=this.$scopedSlots,A=[];if(u&&!a&&!o){var P=e("span",{staticClass:"b-rating-icon"},[(v[Bn]||this.iconClearFn)()]);A.push(e("span",{staticClass:"b-rating-star b-rating-star-clear flex-grow-1",class:{focused:h&&0===d},attrs:{tabindex:g?"-1":null},on:{click:function(){return t.onSelected(null)}},key:"clear"},[P]))}for(var b=0;b1&&void 0!==arguments[1]?arguments[1]:null;if(je(e)){var a=It(e,this.valueField),o=It(e,this.textField),s=It(e,this.optionsField,null);return Ve(s)?{value:Te(a)?t||o:a,text:String(Te(o)?t:o),html:It(e,this.htmlField),disabled:Boolean(It(e,this.disabledField))}:{label:String(It(e,this.labelField)||o),options:this.normalizeOptions(s)}}return{value:t||e,text:String(e),disabled:!1}}}}),u$=Jc({disabled:Wc(qi,!1),value:Wc(Ni,void 0,!0)},Wa),f$=Ms({name:Wa,functional:!0,props:u$,render:function(e,t){var a=t.props,o=t.data,s=t.children,i=a.value,n=a.disabled;return e("option",bs(o,{attrs:{disabled:n},domProps:{value:i}}),s)}});function g$(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function v$(e){for(var t=1;t0?e:U$},computedInterval:function(){var e=Vr(this.repeatInterval,0);return e>0?e:F$},computedThreshold:function(){return Tl(Vr(this.repeatThreshold,H$),1)},computedStepMultiplier:function(){return Tl(Vr(this.repeatStepMultiplier,j$),1)},computedPrecision:function(){var e=this.computedStep;return Bl(e)===e?0:(e.toString().split(".")[1]||"").length},computedMultiplier:function(){return Ll(10,this.computedPrecision||0)},valueAsFixed:function(){var e=this.localValue;return Ve(e)?"":e.toFixed(this.computedPrecision)},computedLocale:function(){var e=Dr(this.locale).filter(yt),t=new Intl.NumberFormat(e);return t.resolvedOptions().locale},computedRTL:function(){return CE(this.computedLocale)},defaultFormatter:function(){var e=this.computedPrecision,t=new Intl.NumberFormat(this.computedLocale,{style:"decimal",useGrouping:!1,minimumIntegerDigits:1,minimumFractionDigits:e,maximumFractionDigits:e,notation:"standard"});return t.format},computedFormatter:function(){var e=this.formatterFn;return Qc(e)?e:this.defaultFormatter},computedAttrs:function(){return _$(_$({},this.bvAttrs),{},{role:"group",lang:this.computedLocale,tabindex:this.disabled?null:"-1",title:this.ariaLabel})},computedSpinAttrs:function(){var e=this.spinId,t=this.localValue,a=this.computedRequired,o=this.disabled,s=this.state,i=this.computedFormatter,n=!Ve(t);return _$(_$({dir:this.computedRTL?"rtl":"ltr"},this.bvAttrs),{},{id:e,role:"spinbutton",tabindex:o?null:"0","aria-live":"off","aria-label":this.ariaLabel||null,"aria-controls":this.ariaControls||null,"aria-invalid":!1===s||!n&&a?"true":null,"aria-required":a?"true":null,"aria-valuemin":jr(this.computedMin),"aria-valuemax":jr(this.computedMax),"aria-valuenow":n?t:null,"aria-valuetext":n?i(t):null})}},watch:(z$={},k$(z$,x$,(function(e){this.localValue=xr(e,null)})),k$(z$,"localValue",(function(e){this.$emit(B$,e)})),k$(z$,"disabled",(function(e){e&&this.clearRepeat()})),k$(z$,"readonly",(function(e){e&&this.clearRepeat()})),z$),created:function(){this.$_autoDelayTimer=null,this.$_autoRepeatTimer=null,this.$_keyIsDown=!1},beforeDestroy:function(){this.clearRepeat()},deactivated:function(){this.clearRepeat()},methods:{focus:function(){this.disabled||Sc(this.$refs.spinner)},blur:function(){this.disabled||_c(this.$refs.spinner)},emitChange:function(){this.$emit(Fs,this.localValue)},stepValue:function(e){var t=this.localValue;if(!this.disabled&&!Ve(t)){var a=this.computedStep*e,o=this.computedMin,s=this.computedMax,i=this.computedMultiplier,n=this.wrap;t=Ol((t-o)/a)*a+o+a,t=Ol(t*i)/i,this.localValue=t>s?n?o:s:t0&&void 0!==arguments[0]?arguments[0]:1,t=this.localValue;Ve(t)?this.localValue=this.computedMin:this.stepValue(1*e)},stepDown:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:1,t=this.localValue;Ve(t)?this.localValue=this.wrap?this.computedMax:this.computedMin:this.stepValue(-1*e)},onKeydown:function(e){var t=e.keyCode,a=e.altKey,o=e.ctrlKey,s=e.metaKey;if(!(this.disabled||this.readonly||a||o||s)&&Cr(G$,t)){if(ol(e,{propagation:!1}),this.$_keyIsDown)return;this.resetTimers(),Cr([oL,qB],t)?(this.$_keyIsDown=!0,t===oL?this.handleStepRepeat(e,this.stepUp):t===qB&&this.handleStepRepeat(e,this.stepDown)):t===eL?this.stepUp(this.computedStepMultiplier):t===ZB?this.stepDown(this.computedStepMultiplier):t===YB?this.localValue=this.computedMin:t===JB&&(this.localValue=this.computedMax)}},onKeyup:function(e){var t=e.keyCode,a=e.altKey,o=e.ctrlKey,s=e.metaKey;this.disabled||this.readonly||a||o||s||Cr(G$,t)&&(ol(e,{propagation:!1}),this.resetTimers(),this.$_keyIsDown=!1,this.emitChange())},handleStepRepeat:function(e,t){var a=this,o=e||{},s=o.type,i=o.button;if(!this.disabled&&!this.readonly){if("mousedown"===s&&i)return;this.resetTimers(),t(1);var n=this.computedThreshold,r=this.computedStepMultiplier,c=this.computedDelay,l=this.computedInterval;this.$_autoDelayTimer=setTimeout((function(){var e=0;a.$_autoRepeatTimer=setInterval((function(){t(ee.length)&&(t=e.length);for(var a=0,o=new Array(t);a0&&a.indexOf(e)===t}))},vq=function(e){return Oe(e)?e:We(e)&&e.target.value||""},Aq=function(){return{all:[],valid:[],invalid:[],duplicate:[]}},Pq=Jc(lt(nq(nq(nq(nq(nq(nq({},DE),hq),vG),yG),IG),{},{addButtonText:Wc(Zi,"Add"),addButtonVariant:Wc(Zi,"outline-secondary"),addOnChange:Wc(qi,!1),duplicateTagText:Wc(Zi,"Duplicate tag(s)"),feedbackAriaLive:Wc(Zi,"assertive"),ignoreInputFocusSelector:Wc(on,uq),inputAttrs:Wc(Yi,{}),inputClass:Wc(an),inputId:Wc(Zi),inputType:Wc(Zi,"text",(function(e){return Cr(pq,e)})),invalidTagText:Wc(Zi,"Invalid tag(s)"),limit:Wc(Qi),limitTagsText:Wc(Zi,"Tag limit reached"),noAddOnEnter:Wc(qi,!1),noOuterFocus:Wc(qi,!1),noTagRemove:Wc(qi,!1),placeholder:Wc(Zi,"Add tag..."),removeOnDelete:Wc(qi,!1),separator:Wc(on),tagClass:Wc(an),tagPills:Wc(qi,!1),tagRemoveLabel:Wc(Zi,"Remove tag"),tagRemovedLabel:Wc(Zi,"Tag removed"),tagValidator:Wc(Ki),tagVariant:Wc(Zi,"secondary")})),Ja),bq=Ms({name:Ja,mixins:[zL,RE,lq,AG,wG,zG,Tr],props:Pq,data:function(){return{hasFocus:!1,newTag:"",tags:[],removedTags:[],tagsState:Aq(),focusState:null}},computed:{computedInputId:function(){return this.inputId||this.safeId("__input__")},computedInputType:function(){return Cr(pq,this.inputType)?this.inputType:"text"},computedInputAttrs:function(){var e=this.disabled,t=this.form;return nq(nq({},this.inputAttrs),{},{id:this.computedInputId,value:this.newTag,disabled:e,form:t})},computedInputHandlers:function(){return nq(nq({},rt(this.bvListeners,[ai,oi])),{},{blur:this.onInputBlur,change:this.onInputChange,focus:this.onInputFocus,input:this.onInputInput,keydown:this.onInputKeydown,reset:this.reset})},computedSeparator:function(){return Dr(this.separator).filter(Oe).filter(yt).join("")},computedSeparatorRegExp:function(){var e=this.computedSeparator;return e?new RegExp("[".concat(fq(e),"]+")):null},computedJoiner:function(){var e=this.computedSeparator.charAt(0);return" "!==e?"".concat(e," "):e},computeIgnoreInputFocusSelector:function(){return Dr(this.ignoreInputFocusSelector).filter(yt).join(",").trim()},disableAddButton:function(){var e=this,t=Wr(this.newTag);return""===t||!this.splitTags(t).some((function(t){return!Cr(e.tags,t)&&e.validateTag(t)}))},duplicateTags:function(){return this.tagsState.duplicate},hasDuplicateTags:function(){return this.duplicateTags.length>0},invalidTags:function(){return this.tagsState.invalid},hasInvalidTags:function(){return this.invalidTags.length>0},isLimitReached:function(){var e=this.limit;return Ee(e)&&e>=0&&this.tags.length>=e}},watch:(Q$={},rq(Q$,dq,(function(e){this.tags=gq(e)})),rq(Q$,"tags",(function(e,t){iL(e,this[dq])||this.$emit(mq,e),iL(e,t)||(e=Dr(e).filter(yt),t=Dr(t).filter(yt),this.removedTags=t.filter((function(t){return!Cr(e,t)})))})),rq(Q$,"tagsState",(function(e,t){iL(e,t)||this.$emit(xi,e.valid,e.invalid,e.duplicate)})),Q$),created:function(){this.tags=gq(this[dq])},mounted:function(){var e=lc("form",this.$el);e&&el(e,"reset",this.reset,Gi)},beforeDestroy:function(){var e=lc("form",this.$el);e&&tl(e,"reset",this.reset,Gi)},methods:{addTag:function(e){if(e=Oe(e)?e:this.newTag,!this.disabled&&""!==Wr(e)&&!this.isLimitReached){var t=this.parseTags(e);if(t.valid.length>0||0===t.all.length)if(cc(this.getInput(),"select"))this.newTag="";else{var a=[].concat(Z$(t.invalid),Z$(t.duplicate));this.newTag=t.all.filter((function(e){return Cr(a,e)})).join(this.computedJoiner).concat(a.length>0?this.computedJoiner.charAt(0):"")}t.valid.length>0&&(this.tags=Dr(this.tags,t.valid)),this.tagsState=t,this.focus()}},removeTag:function(e){this.disabled||(this.tags=this.tags.filter((function(t){return t!==e})))},reset:function(){var e=this;this.newTag="",this.tags=[],this.$nextTick((function(){e.removedTags=[],e.tagsState=Aq()}))},onInputInput:function(e){if(!(this.disabled||We(e)&&e.target.composing)){var t=vq(e),a=this.computedSeparatorRegExp;this.newTag!==t&&(this.newTag=t),t=Gr(t),a&&a.test(t.slice(-1))?this.addTag():this.tagsState=""===t?Aq():this.parseTags(t)}},onInputChange:function(e){if(!this.disabled&&this.addOnChange){var t=vq(e);this.newTag!==t&&(this.newTag=t),this.addTag()}},onInputKeydown:function(e){if(!this.disabled&&We(e)){var t=e.keyCode,a=e.target.value||"";this.noAddOnEnter||t!==KB?!this.removeOnDelete||t!==NB&&t!==$B||""!==a||(ol(e,{propagation:!1}),this.tags=this.tags.slice(0,-1)):(ol(e,{propagation:!1}),this.addTag())}},onClick:function(e){var t=this,a=this.computeIgnoreInputFocusSelector;a&&lc(a,e.target,!0)||this.$nextTick((function(){t.focus()}))},onInputFocus:function(e){var t=this;"out"!==this.focusState&&(this.focusState="in",this.$nextTick((function(){Qr((function(){t.hasFocus&&(t.$emit(ti,e),t.focusState=null)}))})))},onInputBlur:function(e){var t=this;"in"!==this.focusState&&(this.focusState="out",this.$nextTick((function(){Qr((function(){t.hasFocus||(t.$emit(Es,e),t.focusState=null)}))})))},onFocusin:function(e){this.hasFocus=!0,this.$emit(ai,e)},onFocusout:function(e){this.hasFocus=!1,this.$emit(oi,e)},handleAutofocus:function(){var e=this;this.$nextTick((function(){Qr((function(){e.autofocus&&e.focus()}))}))},focus:function(){this.disabled||Sc(this.getInput())},blur:function(){this.disabled||_c(this.getInput())},splitTags:function(e){e=jr(e);var t=this.computedSeparatorRegExp;return(t?e.split(t):[e]).map(Wr).filter(yt)},parseTags:function(e){var t=this,a=this.splitTags(e),o={all:a,valid:[],invalid:[],duplicate:[]};return a.forEach((function(e){Cr(t.tags,e)||Cr(o.valid,e)?Cr(o.duplicate,e)||o.duplicate.push(e):t.validateTag(e)?o.valid.push(e):Cr(o.invalid,e)||o.invalid.push(e)})),o},validateTag:function(e){var t=this.tagValidator;return!Qc(t)||t(e)},getInput:function(){return rc("#".concat(eN(this.computedInputId)),this.$el)},defaultRender:function(e){var t=e.addButtonText,a=e.addButtonVariant,o=e.addTag,s=e.disableAddButton,i=e.disabled,n=e.duplicateTagText,r=e.inputAttrs,c=e.inputClass,l=e.inputHandlers,h=e.inputType,d=e.invalidTagText,m=e.isDuplicate,p=e.isInvalid,u=e.isLimitReached,f=e.limitTagsText,g=e.noTagRemove,v=e.placeholder,A=e.removeTag,P=e.tagClass,b=e.tagPills,y=e.tagRemoveLabel,w=e.tagVariant,I=e.tags,z=this.$createElement,C=I.map((function(e){return e=jr(e),z(X$,{class:P,props:{disabled:i,noRemove:g,pill:b,removeLabel:y,tag:"li",title:e,variant:w},on:{remove:function(){return A(e)}},key:"tags_".concat(e)},e)})),D=d&&p?this.safeId("__invalid_feedback__"):null,R=n&&m?this.safeId("__duplicate_feedback__"):null,S=f&&u?this.safeId("__limit_feedback__"):null,_=[r["aria-describedby"],D,R,S].filter(yt).join(" "),k=z("input",{staticClass:"b-form-tags-input w-100 flex-grow-1 p-0 m-0 bg-transparent border-0",class:c,style:{outline:0,minWidth:"5rem"},attrs:nq(nq({},r),{},{"aria-describedby":_||null,type:h,placeholder:v||null}),domProps:{value:r.value},on:l,directives:[{name:"model",value:r.value}],ref:"input"}),M=z(XL,{staticClass:"b-form-tags-button py-0",class:{invisible:s},style:{fontSize:"90%"},props:{disabled:s||u,variant:a},on:{click:function(){return o()}},ref:"button"},[this.normalizeSlot(un)||t]),T=this.safeId("__tag_list__"),V=z("li",{staticClass:"b-form-tags-field flex-grow-1",attrs:{role:"none","aria-live":"off","aria-controls":T},key:"tags_field"},[z("div",{staticClass:"d-flex",attrs:{role:"group"}},[k,M])]),x=z("ul",{staticClass:"b-form-tags-list list-unstyled mb-0 d-flex flex-wrap align-items-center",attrs:{id:T},key:"tags_list"},[C,V]),B=z();if(d||n||f){var L=this.feedbackAriaLive,O=this.computedJoiner,E=z();D&&(E=z(lG,{props:{id:D,ariaLive:L,forceShow:!0},key:"tags_invalid_feedback"},[this.invalidTagText,": ",this.invalidTags.join(O)]));var U=z();R&&(U=z(rG,{props:{id:R,ariaLive:L},key:"tags_duplicate_feedback"},[this.duplicateTagText,": ",this.duplicateTags.join(O)]));var F=z();S&&(F=z(rG,{props:{id:S,ariaLive:L},key:"tags_limit_feedback"},[f])),B=z("div",{attrs:{"aria-live":"polite","aria-atomic":"true"},key:"tags_feedback"},[E,U,F])}return[x,B]}},render:function(e){var t=this.name,a=this.disabled,o=this.required,s=this.form,i=this.tags,n=this.computedInputId,r=this.hasFocus,c=this.noOuterFocus,l=nq({tags:i.slice(),inputAttrs:this.computedInputAttrs,inputType:this.computedInputType,inputHandlers:this.computedInputHandlers,removeTag:this.removeTag,addTag:this.addTag,reset:this.reset,inputId:n,isInvalid:this.hasInvalidTags,invalidTags:this.invalidTags.slice(),isDuplicate:this.hasDuplicateTags,duplicateTags:this.duplicateTags.slice(),isLimitReached:this.isLimitReached,disableAddButton:this.disableAddButton},nt(this.$props,["addButtonText","addButtonVariant","disabled","duplicateTagText","form","inputClass","invalidTagText","limit","limitTagsText","noTagRemove","placeholder","required","separator","size","state","tagClass","tagPills","tagRemoveLabel","tagVariant"])),h=this.normalizeSlot(wn,l)||this.defaultRender(l),d=e("output",{staticClass:"sr-only",attrs:{id:this.safeId("__selected_tags__"),role:"status",for:n,"aria-live":r?"polite":"off","aria-atomic":"true","aria-relevant":"additions text"}},this.tags.join(", ")),m=e("div",{staticClass:"sr-only",attrs:{id:this.safeId("__removed_tags__"),role:"status","aria-live":r?"assertive":"off","aria-atomic":"true"}},this.removedTags.length>0?"(".concat(this.tagRemovedLabel,") ").concat(this.removedTags.join(", ")):""),p=e();if(t&&!a){var u=i.length>0;p=(u?i:[""]).map((function(a){return e("input",{class:{"sr-only":!u},attrs:{type:u?"hidden":"text",value:a,required:o,name:t,form:s},key:"tag_input_".concat(a)})}))}return e("div",{staticClass:"b-form-tags form-control h-auto",class:[{focus:r&&!c&&!a,disabled:a},this.sizeFormClass,this.stateClass],attrs:{id:this.safeId(),role:"group",tabindex:a||c?null:"-1","aria-describedby":this.safeId("__selected_tags__")},on:{click:this.onClick,focusin:this.onFocusin,focusout:this.onFocusout}},[d,m,h,p])}}),yq=Ft({components:{BFormTags:bq,BTags:bq,BFormTag:X$,BTag:X$}});function wq(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Iq(e){for(var t=1;td?r:"".concat(d,"px")}},render:function(e){return e("textarea",{class:this.computedClass,style:this.computedStyle,directives:[{name:"b-visible",value:this.visibleCallback,modifiers:{640:!0}}],attrs:this.computedAttrs,domProps:{value:this.localValue},on:this.computedListeners,ref:"input"})}}),Sq=Ft({components:{BFormTextarea:Rq,BTextarea:Rq}});function _q(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function kq(e){for(var t=1;te.length)&&(t=e.length);for(var a=0,o=new Array(t);a1&&void 0!==arguments[1]&&arguments[1];if(Ve(t)||Ve(a)||s&&Ve(o))return"";var i=[t,a,s?o:0];return i.map(Nq).join(":")},Jq=Jc(lt(kq(kq(kq(kq({},DE),Hq),nt(W$,["labelIncrement","labelDecrement"])),{},{ariaLabelledby:Wc(Zi),disabled:Wc(qi,!1),footerTag:Wc(Zi,"footer"),headerTag:Wc(Zi,"header"),hidden:Wc(qi,!1),hideHeader:Wc(qi,!1),hour12:Wc(qi,null),labelAm:Wc(Zi,"AM"),labelAmpm:Wc(Zi,"AM/PM"),labelHours:Wc(Zi,"Hours"),labelMinutes:Wc(Zi,"Minutes"),labelNoTimeSelected:Wc(Zi,"No time selected"),labelPm:Wc(Zi,"PM"),labelSeconds:Wc(Zi,"Seconds"),labelSelected:Wc(Zi,"Selected time"),locale:Wc(on),minutesStep:Wc(hn,1),readonly:Wc(qi,!1),secondsStep:Wc(hn,1),showSeconds:Wc(qi,!1)})),Xo),Kq=Ms({name:Xo,mixins:[RE,Fq,Tr],props:Jq,data:function(){var e=$q(this[jq]||"");return{modelHours:e.hours,modelMinutes:e.minutes,modelSeconds:e.seconds,modelAmpm:e.ampm,isLive:!1}},computed:{computedHMS:function(){var e=this.modelHours,t=this.modelMinutes,a=this.modelSeconds;return qq({hours:e,minutes:t,seconds:a},this.showSeconds)},resolvedOptions:function(){var e=Dr(this.locale).filter(yt),t={hour:Wq,minute:Wq,second:Wq};xe(this.hour12)||(t.hour12=!!this.hour12);var a=new Intl.DateTimeFormat(e,t),o=a.resolvedOptions(),s=o.hour12||!1,i=o.hourCycle||(s?"h12":"h23");return{locale:o.locale,hour12:s,hourCycle:i}},computedLocale:function(){return this.resolvedOptions.locale},computedLang:function(){return(this.computedLocale||"").replace(/-u-.*$/,"")},computedRTL:function(){return CE(this.computedLang)},computedHourCycle:function(){return this.resolvedOptions.hourCycle},is12Hour:function(){return!!this.resolvedOptions.hour12},context:function(){return{locale:this.computedLocale,isRTL:this.computedRTL,hourCycle:this.computedHourCycle,hour12:this.is12Hour,hours:this.modelHours,minutes:this.modelMinutes,seconds:this.showSeconds?this.modelSeconds:0,value:this.computedHMS,formatted:this.formattedTimeString}},valueId:function(){return this.safeId()||null},computedAriaLabelledby:function(){return[this.ariaLabelledby,this.valueId].filter(yt).join(" ")||null},timeFormatter:function(){var e={hour12:this.is12Hour,hourCycle:this.computedHourCycle,hour:Wq,minute:Wq,timeZone:"UTC"};return this.showSeconds&&(e.second=Wq),mE(this.computedLocale,e)},numberFormatter:function(){var e=new Intl.NumberFormat(this.computedLocale,{style:"decimal",minimumIntegerDigits:2,minimumFractionDigits:0,maximumFractionDigits:0,notation:"standard"});return e.format},formattedTimeString:function(){var e=this.modelHours,t=this.modelMinutes,a=this.showSeconds&&this.modelSeconds||0;return this.computedHMS?this.timeFormatter(cE(Date.UTC(0,0,1,e,t,a))):this.labelNoTimeSelected||" "},spinScopedSlots:function(){var e=this.$createElement;return{increment:function(t){var a=t.hasFocus;return e(Bv,{props:{scale:a?1.5:1.25},attrs:{"aria-hidden":"true"}})},decrement:function(t){var a=t.hasFocus;return e(Bv,{props:{flipV:!0,scale:a?1.5:1.25},attrs:{"aria-hidden":"true"}})}}}},watch:(Cq={},Mq(Cq,jq,(function(e,t){if(e!==t&&!iL($q(e),$q(this.computedHMS))){var a=$q(e),o=a.hours,s=a.minutes,i=a.seconds,n=a.ampm;this.modelHours=o,this.modelMinutes=s,this.modelSeconds=i,this.modelAmpm=n}})),Mq(Cq,"computedHMS",(function(e,t){e!==t&&this.$emit(Gq,e)})),Mq(Cq,"context",(function(e,t){iL(e,t)||this.$emit(Ws,e)})),Mq(Cq,"modelAmpm",(function(e,t){var a=this;if(e!==t){var o=Ve(this.modelHours)?0:this.modelHours;this.$nextTick((function(){0===e&&o>11?a.modelHours=o-12:1===e&&o<12&&(a.modelHours=o+12)}))}})),Mq(Cq,"modelHours",(function(e,t){e!==t&&(this.modelAmpm=e>11?1:0)})),Cq),created:function(){var e=this;this.$nextTick((function(){e.$emit(Ws,e.context)}))},mounted:function(){this.setLive(!0)},activated:function(){this.setLive(!0)},deactivated:function(){this.setLive(!1)},beforeDestroy:function(){this.setLive(!1)},methods:{focus:function(){this.disabled||Sc(this.$refs.spinners[0])},blur:function(){if(!this.disabled){var e=ec();hc(this.$el,e)&&_c(e)}},formatHours:function(e){var t=this.computedHourCycle;return e=this.is12Hour&&e>12?e-12:e,e=0===e&&"h12"===t?12:0===e&&"h24"===t?24:12===e&&"h11"===t?0:e,this.numberFormatter(e)},formatMinutes:function(e){return this.numberFormatter(e)},formatSeconds:function(e){return this.numberFormatter(e)},formatAmpm:function(e){return 0===e?this.labelAm:1===e?this.labelPm:""},setHours:function(e){this.modelHours=e},setMinutes:function(e){this.modelMinutes=e},setSeconds:function(e){this.modelSeconds=e},setAmpm:function(e){this.modelAmpm=e},onSpinLeftRight:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:{},t=e.type,a=e.keyCode;if(!this.disabled&&"keydown"===t&&(a===XB||a===tL)){ol(e);var o=this.$refs.spinners||[],s=o.map((function(e){return!!e.hasFocus})).indexOf(!0);s+=a===XB?-1:1,s=s>=o.length?0:s<0?o.length-1:s,Sc(o[s])}},setLive:function(e){var t=this;e?this.$nextTick((function(){Qr((function(){t.isLive=!0}))})):this.isLive=!1}},render:function(e){var t=this;if(this.hidden)return e();var a=this.disabled,o=this.readonly,s=this.computedLocale,i=this.computedAriaLabelledby,n=this.labelIncrement,r=this.labelDecrement,c=this.valueId,l=this.focus,h=[],d=function(i,l,d){var m=arguments.length>3&&void 0!==arguments[3]?arguments[3]:{},p=t.safeId("_spinbutton_".concat(l,"_"))||null;return h.push(p),e(N$,Mq({class:d,props:kq({id:p,placeholder:"--",vertical:!0,required:!0,disabled:a,readonly:o,locale:s,labelIncrement:n,labelDecrement:r,wrap:!0,ariaControls:c,min:0},m),scopedSlots:t.spinScopedSlots,on:{change:i},key:l,ref:"spinners"},_s,!0))},m=function(){return e("div",{staticClass:"d-flex flex-column",class:{"text-muted":a||o},attrs:{"aria-hidden":"true"}},[e(Ov,{props:{shiftV:4,scale:.5}}),e(Ov,{props:{shiftV:-4,scale:.5}})])},p=[];p.push(d(this.setHours,"hours","b-time-hours",{value:this.modelHours,max:23,step:1,formatterFn:this.formatHours,ariaLabel:this.labelHours})),p.push(m()),p.push(d(this.setMinutes,"minutes","b-time-minutes",{value:this.modelMinutes,max:59,step:this.minutesStep||1,formatterFn:this.formatMinutes,ariaLabel:this.labelMinutes})),this.showSeconds&&(p.push(m()),p.push(d(this.setSeconds,"seconds","b-time-seconds",{value:this.modelSeconds,max:59,step:this.secondsStep||1,formatterFn:this.formatSeconds,ariaLabel:this.labelSeconds}))),this.isLive&&this.is12Hour&&p.push(d(this.setAmpm,"ampm","b-time-ampm",{value:this.modelAmpm,max:1,formatterFn:this.formatAmpm,ariaLabel:this.labelAmpm,required:!1})),p=e("div",{staticClass:"d-flex align-items-center justify-content-center mx-auto",attrs:{role:"group",tabindex:a||o?null:"-1","aria-labelledby":i},on:{keydown:this.onSpinLeftRight,click:function(e){e.target===e.currentTarget&&l()}}},p);var u=e("output",{staticClass:"form-control form-control-sm text-center",class:{disabled:a||o},attrs:{id:c,role:"status",for:h.filter(yt).join(" ")||null,tabindex:a?null:"-1","aria-live":this.isLive?"polite":"off","aria-atomic":"true"},on:{click:l,focus:l}},[e("bdi",this.formattedTimeString),this.computedHMS?e("span",{staticClass:"sr-only"}," (".concat(this.labelSelected,") ")):""]),f=e(this.headerTag,{staticClass:"b-time-header",class:{"sr-only":this.hideHeader}},[u]),g=this.normalizeSlot(),v=g?e(this.footerTag,{staticClass:"b-time-footer"},g):e();return e("div",{staticClass:"b-time d-inline-flex flex-column text-center",attrs:{role:"group",lang:this.computedLang||null,"aria-labelledby":i||null,"aria-disabled":a?"true":null,"aria-readonly":o&&!a?"true":null}},[f,p,v])}});function Qq(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Yq(e){for(var t=1;t0&&n.push(e("span"," "));var c=this.labelResetButton;n.push(e(XL,{props:{size:"sm",disabled:a||o,variant:this.resetButtonVariant},attrs:{"aria-label":c||null},on:{click:this.onResetButton},key:"reset-btn"},c))}if(!this.noCloseButton){n.length>0&&n.push(e("span"," "));var l=this.labelCloseButton;n.push(e(XL,{props:{size:"sm",disabled:a,variant:this.closeButtonVariant},attrs:{"aria-label":l||null},on:{click:this.onCloseButton},key:"close-btn"},l))}n.length>0&&(n=[e("div",{staticClass:"b-form-date-controls d-flex flex-wrap",class:{"justify-content-between":n.length>1,"justify-content-end":n.length<2}},n)]);var h=e(Kq,{staticClass:"b-form-time-control",props:Yq(Yq({},$c(sJ,s)),{},{value:t,hidden:!this.isVisible}),on:{input:this.onInput,context:this.onContext},ref:"time"},n);return e(wW,{staticClass:"b-form-timepicker",props:Yq(Yq({},$c(iJ,s)),{},{id:this.safeId(),value:t,formattedValue:t?this.formattedValue:"",placeholder:i,rtl:this.isRTL,lang:this.computedLang}),on:{show:this.onShow,shown:this.onShown,hidden:this.onHidden},scopedSlots:Xq({},Pn,this.$scopedSlots[Pn]||this.defaultButtonFn),ref:"control"},[h])}}),cJ=Ft({components:{BFormTimepicker:rJ,BTimepicker:rJ}}),lJ=Ft({components:{BImg:lU,BImgLazy:UU}}),hJ=Jc({tag:Wc(Zi,"div")},co),dJ=Ms({name:co,functional:!0,props:hJ,render:function(e,t){var a=t.props,o=t.data,s=t.children;return e(a.tag,bs(o,{staticClass:"input-group-text"}),s)}}),mJ=Jc({append:Wc(qi,!1),id:Wc(Zi),isText:Wc(qi,!1),tag:Wc(Zi,"div")},io),pJ=Ms({name:io,functional:!0,props:mJ,render:function(e,t){var a=t.props,o=t.data,s=t.children,i=a.append;return e(a.tag,bs(o,{class:{"input-group-append":i,"input-group-prepend":!i},attrs:{id:a.id}}),a.isText?[e(dJ,s)]:s)}});function uJ(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function fJ(e){for(var t=1;t1&&void 0!==arguments[1]?arguments[1]:null;return e&&e.$options._scopeId||t};function vK(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var AK=Ms({mixins:[fK],computed:{scopedStyleAttrs:function(){var e=gK(this.bvParent);return e?vK({},e,""):{}}}});function PK(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function bK(e){for(var t=1;t2&&void 0!==arguments[2]?arguments[2]:{},o=e.$root?e.$root.$options.bvEventRoot||e.$root:null;return new t(bK(bK({},a),{},{parent:e,bvParent:e,bvEventRoot:o}))},IK=Ms({abstract:!0,name:fs,props:{nodes:Wc(en)},data:function(e){return{updatedNodes:e.nodes}},destroyed:function(){Xr(this.$el)},render:function(e){var t=this.updatedNodes,a=Be(t)?t({}):t;return a=Dr(a).filter(yt),a&&a.length>0&&!a[0].text?a[0]:e()}}),zK={container:Wc([De,Zi],"body"),disabled:Wc(qi,!1),tag:Wc(Zi,"div")},CK=Ms({name:us,mixins:[Tr],props:zK,watch:{disabled:{immediate:!0,handler:function(e){e?this.unmountTarget():this.$nextTick(this.mountTarget)}}},created:function(){this.$_defaultFn=null,this.$_target=null},beforeMount:function(){this.mountTarget()},updated:function(){this.updateTarget()},beforeDestroy:function(){this.unmountTarget(),this.$_defaultFn=null},methods:{getContainer:function(){if(I){var e=this.container;return Oe(e)?rc(e):e}return null},mountTarget:function(){if(!this.$_target){var e=this.getContainer();if(e){var t=document.createElement("div");e.appendChild(t),this.$_target=wK(this,IK,{el:t,propsData:{nodes:Dr(this.normalizeSlot())}})}}},updateTarget:function(){if(I&&this.$_target){var e=this.$scopedSlots.default;this.disabled||(e&&this.$_defaultFn!==e?this.$_target.updatedNodes=e:e||(this.$_target.updatedNodes=this.$slots.default)),this.$_defaultFn=e}},unmountTarget:function(){this.$_target&&this.$_target.$destroy(),this.$_target=null}},render:function(e){if(this.disabled){var t=Dr(this.normalizeSlot()).filter(yt);if(t.length>0&&!t[0].text)return t[0]}return e()}}),DK=Ms({name:us,mixins:[Tr],props:zK,render:function(e){if(this.disabled){var t=Dr(this.normalizeSlot()).filter(yt);if(t.length>0)return t[0]}return e(o["default"].Teleport,{to:this.container},this.normalizeSlot())}}),RK=Ss?DK:CK;function SK(e){return SK="function"==typeof Symbol&&"symbol"==typeof Symbol.iterator?function(e){return typeof e}:function(e){return e&&"function"==typeof Symbol&&e.constructor===Symbol&&e!==Symbol.prototype?"symbol":typeof e},SK(e)}function _K(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function kK(e){for(var t=1;t1&&void 0!==arguments[1]?arguments[1]:{};return TK(this,a),o=t.call(this,e,s),Ze(HK(o),{trigger:ht()}),o}return xK(a,null,[{key:"Defaults",get:function(){return kK(kK({},BK(GK(a),"Defaults",this)),{},{trigger:null})}}]),a}(UH),NK=1040,$K=".fixed-top, .fixed-bottom, .is-fixed, .sticky-top",qK=".sticky-top",JK=".navbar-toggler",KK=Ms({data:function(){return{modals:[],baseZIndex:null,scrollbarWidth:null,isBodyOverflowing:!1}},computed:{modalCount:function(){return this.modals.length},modalsAreOpen:function(){return this.modalCount>0}},watch:{modalCount:function(e,t){I&&(this.getScrollbarWidth(),e>0&&0===t?(this.checkScrollbar(),this.setScrollbar(),mc(document.body,"modal-open")):0===e&&t>0&&(this.resetScrollbar(),pc(document.body,"modal-open")),fc(document.body,"data-modal-open-count",String(e)))},modals:function(e){var t=this;this.checkScrollbar(),Qr((function(){t.updateModals(e||[])}))}},methods:{registerModal:function(e){e&&-1===this.modals.indexOf(e)&&this.modals.push(e)},unregisterModal:function(e){var t=this.modals.indexOf(e);t>-1&&(this.modals.splice(t,1),e._isBeingDestroyed||e._isDestroyed||this.resetModal(e))},getBaseZIndex:function(){if(I&&Ve(this.baseZIndex)){var e=document.createElement("div");mc(e,"modal-backdrop"),mc(e,"d-none"),Pc(e,"display","none"),document.body.appendChild(e),this.baseZIndex=Vr(Ic(e).zIndex,NK),document.body.removeChild(e)}return this.baseZIndex||NK},getScrollbarWidth:function(){if(I&&Ve(this.scrollbarWidth)){var e=document.createElement("div");mc(e,"modal-scrollbar-measure"),document.body.appendChild(e),this.scrollbarWidth=wc(e).width-e.clientWidth,document.body.removeChild(e)}return this.scrollbarWidth||0},updateModals:function(e){var t=this,a=this.getBaseZIndex(),o=this.getScrollbarWidth();e.forEach((function(e,s){e.zIndex=a+s,e.scrollbarWidth=o,e.isTop=s===t.modals.length-1,e.isBodyOverflowing=t.isBodyOverflowing}))},resetModal:function(e){e&&(e.zIndex=this.getBaseZIndex(),e.isTop=!0,e.isBodyOverflowing=!1)},checkScrollbar:function(){var e=wc(document.body),t=e.left,a=e.right;this.isBodyOverflowing=t+a0&&void 0!==arguments[0]&&arguments[0];this.$_observer&&this.$_observer.disconnect(),this.$_observer=null,e&&(this.$_observer=tF(this.$refs.content,this.checkModalOverflow.bind(this),pQ))},updateModel:function(e){e!==this[oQ]&&this.$emit(sQ,e)},buildEvent:function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};return new WK(e,XK(XK({cancelable:!1,target:this.$refs.modal||this.$el||null,relatedTarget:null,trigger:null},t),{},{vueTarget:this,componentId:this.modalId}))},show:function(){if(!this.isVisible&&!this.isOpening)if(this.isClosing)this.$once(ii,this.show);else{this.isOpening=!0,this.$_returnFocus=this.$_returnFocus||this.getActiveElement();var e=this.buildEvent(_i,{cancelable:!0});if(this.emitEvent(e),e.defaultPrevented||this.isVisible)return this.isOpening=!1,void this.updateModel(!1);this.doShow()}},hide:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:"";if(this.isVisible&&!this.isClosing){this.isClosing=!0;var t=this.buildEvent(ni,{cancelable:e!==rQ,trigger:e||null});if(e===dQ?this.$emit(pi,t):e===lQ?this.$emit(Us,t):e===hQ&&this.$emit(Gs,t),this.emitEvent(t),t.defaultPrevented||!this.isVisible)return this.isClosing=!1,void this.updateModel(!0);this.setObserver(!1),this.isVisible=!1,this.updateModel(!1)}},toggle:function(e){e&&(this.$_returnFocus=e),this.isVisible?this.hide(cQ):this.show()},getActiveElement:function(){var e=ec(I?[document.body]:[]);return e&&e.focus?e:null},doShow:function(){var e=this;QK.modalsAreOpen&&this.noStacking?this.listenOnRootOnce(il(vo,ii),this.doShow):(QK.registerModal(this),this.isHidden=!1,this.$nextTick((function(){e.isVisible=!0,e.isOpening=!1,e.updateModel(!0),e.$nextTick((function(){e.setObserver(!0)}))})))},onBeforeEnter:function(){this.isTransitioning=!0,this.setResizeEvent(!0)},onEnter:function(){var e=this;this.isBlock=!0,Qr((function(){Qr((function(){e.isShow=!0}))}))},onAfterEnter:function(){var e=this;this.checkModalOverflow(),this.isTransitioning=!1,Qr((function(){e.emitEvent(e.buildEvent(ki)),e.setEnforceFocus(!0),e.$nextTick((function(){e.focusFirst()}))}))},onBeforeLeave:function(){this.isTransitioning=!0,this.setResizeEvent(!1),this.setEnforceFocus(!1)},onLeave:function(){this.isShow=!1},onAfterLeave:function(){var e=this;this.isBlock=!1,this.isTransitioning=!1,this.isModalOverflowing=!1,this.isHidden=!0,this.$nextTick((function(){e.isClosing=!1,QK.unregisterModal(e),e.returnFocusTo(),e.emitEvent(e.buildEvent(ii))}))},emitEvent:function(e){var t=e.type;this.emitOnRoot(il(vo,t),e,e.componentId),this.$emit(t,e)},onDialogMousedown:function(){var e=this,t=this.$refs.modal,a=function a(o){tl(t,"mouseup",a,Wi),o.target===t&&(e.ignoreBackdropClick=!0)};el(t,"mouseup",a,Wi)},onClickOut:function(e){this.ignoreBackdropClick?this.ignoreBackdropClick=!1:this.isVisible&&!this.noCloseOnBackdrop&&hc(document.body,e.target)&&(hc(this.$refs.content,e.target)||this.hide(iQ))},onOk:function(){this.hide(dQ)},onCancel:function(){this.hide(lQ)},onClose:function(){this.hide(hQ)},onEsc:function(e){e.keyCode===QB&&this.isVisible&&!this.noCloseOnEsc&&this.hide(nQ)},focusHandler:function(e){var t=this.$refs.content,a=e.target;if(!(this.noEnforceFocus||!this.isTop||!this.isVisible||!t||document===a||hc(t,a)||this.computeIgnoreEnforceFocusSelector&&lc(this.computeIgnoreEnforceFocusSelector,a,!0))){var o=Rc(this.$refs.content),s=this.$refs["bottom-trap"],i=this.$refs["top-trap"];if(s&&a===s){if(Sc(o[0]))return}else if(i&&a===i&&Sc(o[o.length-1]))return;Sc(t,{preventScroll:!0})}},setEnforceFocus:function(e){this.listenDocument(e,"focusin",this.focusHandler)},setResizeEvent:function(e){this.listenWindow(e,"resize",this.checkModalOverflow),this.listenWindow(e,"orientationchange",this.checkModalOverflow)},showHandler:function(e,t){e===this.modalId&&(this.$_returnFocus=t||this.getActiveElement(),this.show())},hideHandler:function(e){e===this.modalId&&this.hide("event")},toggleHandler:function(e,t){e===this.modalId&&this.toggle(t)},modalListener:function(e){this.noStacking&&e.vueTarget!==this&&this.hide()},focusFirst:function(){var e=this;I&&Qr((function(){var t=e.$refs.modal,a=e.$refs.content,o=e.getActiveElement();if(t&&a&&(!o||!hc(a,o))){var s=e.$refs["ok-button"],i=e.$refs["cancel-button"],n=e.$refs["close-button"],r=e.autoFocusButton,c=r===dQ&&s?s.$el||s:r===lQ&&i?i.$el||i:r===hQ&&n?n.$el||n:a;Sc(c),c===a&&e.$nextTick((function(){t.scrollTop=0}))}}))},returnFocusTo:function(){var e=this.returnFocus||this.$_returnFocus||null;this.$_returnFocus=null,this.$nextTick((function(){e=Oe(e)?rc(e):e,e&&(e=e.$el||e,Sc(e))}))},checkModalOverflow:function(){if(this.isVisible){var e=this.$refs.modal;this.isModalOverflowing=e.scrollHeight>document.documentElement.clientHeight}},makeModal:function(e){var t=e();if(!this.hideHeader){var a=this.normalizeSlot(Kn,this.slotScope);if(!a){var o=e();this.hideHeaderClose||(o=e(ll,{props:{content:this.headerCloseContent,disabled:this.isTransitioning,ariaLabel:this.headerCloseLabel,textVariant:this.headerCloseVariant||this.headerTextVariant},on:{click:this.onClose},ref:"close-button"},[this.normalizeSlot(Qn)])),a=[e(this.titleTag,{staticClass:"modal-title",class:this.titleClasses,attrs:{id:this.modalTitleId},domProps:this.hasNormalizedSlot(Xn)?{}:yO(this.titleHtml,this.title)},this.normalizeSlot(Xn,this.slotScope)),o]}t=e(this.headerTag,{staticClass:"modal-header",class:this.headerClasses,attrs:{id:this.modalHeaderId},ref:"header"},[a])}var s=e("div",{staticClass:"modal-body",class:this.bodyClasses,attrs:{id:this.modalBodyId},ref:"body"},this.normalizeSlot(wn,this.slotScope)),i=e();if(!this.hideFooter){var n=this.normalizeSlot(Jn,this.slotScope);if(!n){var r=e();this.okOnly||(r=e(XL,{props:{variant:this.cancelVariant,size:this.buttonSize,disabled:this.cancelDisabled||this.busy||this.isTransitioning},domProps:this.hasNormalizedSlot(qn)?{}:yO(this.cancelTitleHtml,this.cancelTitle),on:{click:this.onCancel},ref:"cancel-button"},this.normalizeSlot(qn)));var c=e(XL,{props:{variant:this.okVariant,size:this.buttonSize,disabled:this.okDisabled||this.busy||this.isTransitioning},domProps:this.hasNormalizedSlot(Yn)?{}:yO(this.okTitleHtml,this.okTitle),on:{click:this.onOk},ref:"ok-button"},this.normalizeSlot(Yn));n=[r,c]}i=e(this.footerTag,{staticClass:"modal-footer",class:this.footerClasses,attrs:{id:this.modalFooterId},ref:"footer"},[n])}var l=e("div",{staticClass:"modal-content",class:this.contentClass,attrs:{id:this.modalContentId,tabindex:"-1"},ref:"content"},[t,s,i]),h=e(),d=e();this.isVisible&&!this.noEnforceFocus&&(h=e("span",{attrs:{tabindex:"0"},ref:"top-trap"}),d=e("span",{attrs:{tabindex:"0"},ref:"bottom-trap"}));var m=e("div",{staticClass:"modal-dialog",class:this.dialogClasses,on:{mousedown:this.onDialogMousedown},ref:"dialog"},[h,l,d]),p=e("div",{staticClass:"modal",class:this.modalClasses,style:this.modalStyles,attrs:this.computedModalAttrs,on:{keydown:this.onEsc,click:this.onClickOut},directives:[{name:"show",value:this.isVisible}],ref:"modal"},[m]);p=e("transition",{props:{enterClass:"",enterToClass:"",enterActiveClass:"",leaveClass:"",leaveActiveClass:"",leaveToClass:""},on:{beforeEnter:this.onBeforeEnter,enter:this.onEnter,afterEnter:this.onAfterEnter,beforeLeave:this.onBeforeLeave,leave:this.onLeave,afterLeave:this.onAfterLeave}},[p]);var u=e();return!this.hideBackdrop&&this.isVisible&&(u=e("div",{staticClass:"modal-backdrop",attrs:{id:this.modalBackdropId}},this.normalizeSlot($n))),u=e(vl,{props:{noFade:this.noFade}},[u]),e("div",{style:this.modalOuterStyle,attrs:this.computedAttrs,key:"modal-outer-".concat(this[Rs])},[p,u])}},render:function(e){return this.static?this.lazy&&this.isHidden?e():this.makeModal(e):this.isHidden?e():e(RK,[this.makeModal(e)])}}),gQ=nl(vo,_i),vQ="__bv_modal_directive__",AQ=function(e){var t=e.modifiers,a=void 0===t?{}:t,o=e.arg,s=e.value;return Oe(s)?s:Oe(o)?o:at(a).reverse()[0]},PQ=function(e){return e&&cc(e,".dropdown-menu > li, li.nav-item")&&rc("a, button",e)||e},bQ=function(e){e&&"BUTTON"!==e.tagName&&(Ac(e,"role")||fc(e,"role","button"),"A"===e.tagName||Ac(e,"tabindex")||fc(e,"tabindex","0"))},yQ=function(e,t,a){var o=AQ(t),s=PQ(e);if(o&&s){var i=function(e){var s=e.currentTarget;if(!sc(s)){var i=e.type,n=e.keyCode;"click"!==i&&("keydown"!==i||n!==KB&&n!==aL)||gL(YF(a,t)).$emit(gQ,o,s)}};e[vQ]={handler:i,target:o,trigger:s},bQ(s),el(s,"click",i,Gi),"BUTTON"!==s.tagName&&"button"===vc(s,"role")&&el(s,"keydown",i,Gi)}},wQ=function(e){var t=e[vQ]||{},a=t.trigger,o=t.handler;a&&o&&(tl(a,"click",o,Gi),tl(a,"keydown",o,Gi),tl(e,"click",o,Gi),tl(e,"keydown",o,Gi)),delete e[vQ]},IQ=function(e,t,a){var o=e[vQ]||{},s=AQ(t),i=PQ(e);s===o.target&&i===o.trigger||(wQ(e,t,a),yQ(e,t,a)),bQ(i)},zQ=function(){},CQ={inserted:IQ,updated:zQ,componentUpdated:IQ,unbind:wQ};function DQ(e,t){if(!(e instanceof t))throw new TypeError("Cannot call a class as a function")}function RQ(e,t){for(var a=0;ae.length)&&(t=e.length);for(var a=0,o=new Array(t);a2&&void 0!==arguments[2]?arguments[2]:HQ;if(!Dt(EQ)&&!Rt(EQ)){var s=wK(e,t,{propsData:kQ(kQ(kQ({},GQ(Vc(vo))),{},{hideHeaderClose:!0,hideHeader:!(a.title||a.titleHtml)},rt(a,at(jQ))),{},{lazy:!1,busy:!1,visible:!1,noStacking:!1,noEnforceFocus:!1})});return at(jQ).forEach((function(e){Te(a[e])||(s.$slots[jQ[e]]=Dr(a[e]))})),new Promise((function(e,t){var a=!1;s.$once(Ui,(function(){a||t(new Error("BootstrapVue MsgBox destroyed before resolve"))})),s.$on(ni,(function(t){if(!t.defaultPrevented){var s=o(t);t.defaultPrevented||(a=!0,e(s))}}));var i=document.createElement("div");document.body.appendChild(i),s.$mount(i)}))}},o=function(e,t){var o=arguments.length>2&&void 0!==arguments[2]?arguments[2]:{},s=arguments.length>3&&void 0!==arguments[3]?arguments[3]:null;if(t&&!Rt(EQ)&&!Dt(EQ)&&Be(s))return a(e,kQ(kQ({},GQ(o)),{},{msgBoxContent:t}),s)},s=function(){function e(t){DQ(this,e),Ye(this,{_vm:t,_root:gL(t)}),Ze(this,{_vm:ht(),_root:ht()})}return SQ(e,[{key:"show",value:function(e){if(e&&this._root){for(var t,a=arguments.length,o=new Array(a>1?a-1:0),s=1;s1?a-1:0),s=1;s1&&void 0!==arguments[1]?arguments[1]:{},a=kQ(kQ({},t),{},{okOnly:!0,okDisabled:!1,hideFooter:!1,msgBoxContent:e});return o(this._vm,e,a,(function(){return!0}))}},{key:"msgBoxConfirm",value:function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{},a=kQ(kQ({},t),{},{okOnly:!1,okDisabled:!1,cancelDisabled:!1,hideFooter:!1});return o(this._vm,e,a,(function(e){var t=e.trigger;return"ok"===t||"cancel"!==t&&null}))}}]),e}();e.mixin({beforeCreate:function(){this[UQ]=new s(this)}}),ot(e.prototype,EQ)||et(e.prototype,EQ,{get:function(){return this&&this[UQ]||Ct('"'.concat(EQ,'" must be accessed from a Vue instance "this" context.'),vo),this[UQ]}})},NQ=Ft({plugins:{plugin:WQ}}),$Q=Ft({components:{BModal:fQ},directives:{VBModal:CQ},plugins:{BVModalPlugin:NQ}});function qQ(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var JQ=function(e){return e="left"===e?"start":"right"===e?"end":e,"justify-content-".concat(e)},KQ=Jc({align:Wc(Zi),cardHeader:Wc(qi,!1),fill:Wc(qi,!1),justified:Wc(qi,!1),pills:Wc(qi,!1),small:Wc(qi,!1),tabs:Wc(qi,!1),tag:Wc(Zi,"ul"),vertical:Wc(qi,!1)},Po),QQ=Ms({name:Po,functional:!0,props:KQ,render:function(e,t){var a,o=t.props,s=t.data,i=t.children,n=o.tabs,r=o.pills,c=o.vertical,l=o.align,h=o.cardHeader;return e(o.tag,bs(s,{staticClass:"nav",class:(a={"nav-tabs":n,"nav-pills":r&&!n,"card-header-tabs":!c&&h&&n,"card-header-pills":!c&&h&&r&&!n,"flex-column":c,"nav-fill":!c&&o.fill,"nav-justified":!c&&o.justified},qQ(a,JQ(l),!c&&l),qQ(a,"small",o.small),a)}),i)}});function YQ(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function XQ(e){for(var t=1;te.length)&&(t=e.length);for(var a=0,o=new Array(t);a=0&&t<=1})),overlayTag:Wc(Zi,"div"),rounded:Wc(rn,!1),show:Wc(qi,!1),spinnerSmall:Wc(qi,!1),spinnerType:Wc(Zi,"border"),spinnerVariant:Wc(Zi),variant:Wc(Zi,"light"),wrapTag:Wc(Zi,"div"),zIndex:Wc(hn,10)},So),YY=Ms({name:So,mixins:[Tr],props:QY,computed:{computedRounded:function(){var e=this.rounded;return!0===e||""===e?"rounded":e?"rounded-".concat(e):""},computedVariant:function(){var e=this.variant;return e&&!this.bgColor?"bg-".concat(e):""},slotScope:function(){return{spinnerType:this.spinnerType||null,spinnerVariant:this.spinnerVariant||null,spinnerSmall:this.spinnerSmall}}},methods:{defaultOverlayFn:function(e){var t=e.spinnerType,a=e.spinnerVariant,o=e.spinnerSmall;return this.$createElement(WY,{props:{type:t,variant:a,small:o}})}},render:function(e){var t=this,a=this.show,o=this.fixed,s=this.noFade,i=this.noWrap,n=this.slotScope,r=e();if(a){var c=e("div",{staticClass:"position-absolute",class:[this.computedVariant,this.computedRounded],style:$Y($Y({},KY),{},{opacity:this.opacity,backgroundColor:this.bgColor||null,backdropFilter:this.blur?"blur(".concat(this.blur,")"):null})}),l=e("div",{staticClass:"position-absolute",style:this.noCenter?$Y({},KY):{top:"50%",left:"50%",transform:"translateX(-50%) translateY(-50%)"}},[this.normalizeSlot(rr,n)||this.defaultOverlayFn(n)]);r=e(this.overlayTag,{staticClass:"b-overlay",class:{"position-absolute":!i||i&&!o,"position-fixed":i&&o},style:$Y($Y({},KY),{},{zIndex:this.zIndex||10}),on:{click:function(e){return t.$emit(js,e)}},key:"overlay"},[c,l])}return r=e(vl,{props:{noFade:s,appear:!0},on:{"after-enter":function(){return t.$emit(ki)},"after-leave":function(){return t.$emit(ii)}}},[r]),i?r:e(this.wrapTag,{staticClass:"b-overlay-wrap position-relative",attrs:{"aria-busy":a?"true":null}},i?[r]:[this.normalizeSlot(),r])}}),XY=Ft({components:{BOverlay:YY}});function ZY(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function eX(e){for(var t=1;tt?t:a<1?1:a},mX=function(e){if(e.keyCode===aL)return ol(e,{immediatePropagation:!0}),e.currentTarget.click(),!1},pX=Jc(lt(eX(eX({},sX),{},{align:Wc(Zi,"left"),ariaLabel:Wc(Zi,"Pagination"),disabled:Wc(qi,!1),ellipsisClass:Wc(an),ellipsisText:Wc(Zi,"…"),firstClass:Wc(an),firstNumber:Wc(qi,!1),firstText:Wc(Zi,"«"),hideEllipsis:Wc(qi,!1),hideGotoEndButtons:Wc(qi,!1),labelFirstPage:Wc(Zi,"Go to first page"),labelLastPage:Wc(Zi,"Go to last page"),labelNextPage:Wc(Zi,"Go to next page"),labelPage:Wc(ln,"Go to page"),labelPrevPage:Wc(Zi,"Go to previous page"),lastClass:Wc(an),lastNumber:Wc(qi,!1),lastText:Wc(Zi,"»"),limit:Wc(hn,cX,(function(e){return!(Vr(e,0)<1)||(Ct('Prop "limit" must be a number greater than "0"',_o),!1)})),nextClass:Wc(an),nextText:Wc(Zi,"›"),pageClass:Wc(an),pills:Wc(qi,!1),prevClass:Wc(an),prevText:Wc(Zi,"‹"),size:Wc(Zi)})),"pagination"),uX=Ms({mixins:[oX,Tr],props:pX,data:function(){var e=Vr(this[iX],0);return e=e>0?e:-1,{currentPage:e,localNumberOfPages:1,localLimit:cX}},computed:{btnSize:function(){var e=this.size;return e?"pagination-".concat(e):""},alignment:function(){var e=this.align;return"center"===e?"justify-content-center":"end"===e||"right"===e?"justify-content-end":"fill"===e?"text-center":""},styleClass:function(){return this.pills?"b-pagination-pills":""},computedCurrentPage:function(){return dX(this.currentPage,this.localNumberOfPages)},paginationParams:function(){var e=this.localLimit,t=this.localNumberOfPages,a=this.computedCurrentPage,o=this.hideEllipsis,s=this.firstNumber,i=this.lastNumber,n=!1,r=!1,c=e,l=1;t<=e?c=t:arX?(o&&!i||(r=!0,c=e-(s?0:1)),c=Ml(c,e)):t-a+2rX?(o&&!s||(n=!0,c=e-(i?0:1)),l=t-c+1):(e>rX&&(c=e-(o?0:2),n=!(o&&!s),r=!(o&&!i)),l=a-Bl(c/2)),l<1?(l=1,n=!1):l>t-c&&(l=t-c+1,r=!1),n&&s&&l<4&&(c+=2,l=1,n=!1);var h=l+c-1;return r&&i&&h>t-3&&(c+=h===t-2?2:3,r=!1),e<=rX&&(s&&1===l?c=Ml(c+1,t,e+1):i&&t===l+c-1&&(l=Tl(l-1,1),c=Ml(t-l+1,t,e+1))),c=Ml(c,t-l+1),{showFirstDots:n,showLastDots:r,numberOfLinks:c,startNumber:l}},pageList:function(){var e=this.paginationParams,t=e.numberOfLinks,a=e.startNumber,o=this.computedCurrentPage,s=lX(a,t);if(s.length>3){var i=o-a,n="bv-d-xs-down-none";if(0===i)for(var r=3;ri+1;h--)s[h].classes=n}}return s}},watch:(JY={},tX(JY,iX,(function(e,t){e!==t&&(this.currentPage=dX(e,this.localNumberOfPages))})),tX(JY,"currentPage",(function(e,t){e!==t&&this.$emit(nX,e>0?e:null)})),tX(JY,"limit",(function(e,t){e!==t&&(this.localLimit=hX(e))})),JY),created:function(){var e=this;this.localLimit=hX(this.limit),this.$nextTick((function(){e.currentPage=e.currentPage>e.localNumberOfPages?e.localNumberOfPages:e.currentPage}))},methods:{handleKeyNav:function(e){var t=e.keyCode,a=e.shiftKey;this.isNav||(t===XB||t===oL?(ol(e,{propagation:!1}),a?this.focusFirst():this.focusPrev()):t!==tL&&t!==qB||(ol(e,{propagation:!1}),a?this.focusLast():this.focusNext()))},getButtons:function(){return nc("button.page-link, a.page-link",this.$el).filter((function(e){return oc(e)}))},focusCurrent:function(){var e=this;this.$nextTick((function(){var t=e.getButtons().find((function(t){return Vr(vc(t,"aria-posinset"),0)===e.computedCurrentPage}));Sc(t)||e.focusFirst()}))},focusFirst:function(){var e=this;this.$nextTick((function(){var t=e.getButtons().find((function(e){return!sc(e)}));Sc(t)}))},focusLast:function(){var e=this;this.$nextTick((function(){var t=e.getButtons().reverse().find((function(e){return!sc(e)}));Sc(t)}))},focusPrev:function(){var e=this;this.$nextTick((function(){var t=e.getButtons(),a=t.indexOf(ec());a>0&&!sc(t[a-1])&&Sc(t[a-1])}))},focusNext:function(){var e=this;this.$nextTick((function(){var t=e.getButtons(),a=t.indexOf(ec());ar,u=a<1?1:a>r?r:a,v={disabled:m,page:u,index:u-1},A=t.normalizeSlot(i,v)||jr(c)||e(),P=e(m?"span":n?EL:"button",{staticClass:"page-link",class:{"flex-grow-1":!n&&!m&&p},props:m||!n?{}:t.linkProps(a),attrs:{role:n?null:"menuitem",type:n||m?null:"button",tabindex:m||n?null:"-1","aria-label":s,"aria-controls":Jl(t).ariaControls||null,"aria-disabled":m?"true":null},on:m?{}:{"!click":function(e){t.onClick(e,a)},keydown:mX}},[A]);return e("li",{key:d,staticClass:"page-item",class:[{disabled:m,"flex-fill":p,"d-flex":p&&!n&&!m},l],attrs:{role:n?null:"presentation","aria-hidden":m?"true":null}},[P])},A=function(a){return e("li",{staticClass:"page-item",class:["disabled","bv-d-xs-down-none",p?"flex-fill":"",t.ellipsisClass],attrs:{role:"separator"},key:"ellipsis-".concat(a?"last":"first")},[e("span",{staticClass:"page-link"},[t.normalizeSlot(Dn)||jr(t.ellipsisText)||e()])])},P=function(a,i){var c=a.number,l=f(c)&&!g,h=o?null:l||g&&0===i?"0":"-1",d={role:n?null:"menuitemradio",type:n||o?null:"button","aria-disabled":o?"true":null,"aria-controls":Jl(t).ariaControls||null,"aria-label":Qc(s)?s(c):"".concat(Be(s)?s():s," ").concat(c),"aria-checked":n?null:l?"true":"false","aria-current":n&&l?"page":null,"aria-posinset":n?null:c,"aria-setsize":n?null:r,tabindex:n?null:h},m=jr(t.makePage(c)),u={page:c,index:c-1,content:m,active:l,disabled:o},v=e(o?"span":n?EL:"button",{props:o||!n?{}:t.linkProps(c),staticClass:"page-link",class:{"flex-grow-1":!n&&!o&&p},attrs:d,on:o?{}:{"!click":function(e){t.onClick(e,c)},keydown:mX}},[t.normalizeSlot(cr,u)||m]);return e("li",{staticClass:"page-item",class:[{disabled:o,active:l,"flex-fill":p,"d-flex":p&&!n&&!o},a.classes,t.pageClass],attrs:{role:n?null:"presentation"},key:"page-".concat(c)},[v])},b=e();this.firstNumber||this.hideGotoEndButtons||(b=v(1,this.labelFirstPage,Mn,this.firstText,this.firstClass,1,"pagination-goto-first")),u.push(b),u.push(v(c-1,this.labelPrevPage,dr,this.prevText,this.prevClass,1,"pagination-goto-prev")),u.push(this.firstNumber&&1!==l[0]?P({number:1},0):e()),u.push(d?A(!1):e()),this.pageList.forEach((function(e,a){var o=d&&t.firstNumber&&1!==l[0]?1:0;u.push(P(e,a+o))})),u.push(m?A(!0):e()),u.push(this.lastNumber&&l[l.length-1]!==r?P({number:r},-1):e()),u.push(v(c+1,this.labelNextPage,nr,this.nextText,this.nextClass,r,"pagination-goto-next"));var y=e();this.lastNumber||this.hideGotoEndButtons||(y=v(r,this.labelLastPage,Gn,this.lastText,this.lastClass,r,"pagination-goto-last")),u.push(y);var w=e("ul",{staticClass:"pagination",class:["b-pagination",this.btnSize,this.alignment,this.styleClass],attrs:{role:n?null:"menubar","aria-disabled":o?"true":"false","aria-label":n?null:i||null},on:n?{}:{keydown:this.handleKeyNav},ref:"ul"},u);return n?e("nav",{attrs:{"aria-disabled":o?"true":null,"aria-hidden":o?"true":"false","aria-label":n&&i||null}},[w]):w}});function fX(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function gX(e){for(var t=1;te.numberOfPages)&&(this.currentPage=1),this.localNumberOfPages=e.numberOfPages}},created:function(){var e=this;this.localNumberOfPages=this.numberOfPages;var t=Vr(this[iX],0);t>0?this.currentPage=t:this.$nextTick((function(){e.currentPage=0}))},methods:{onClick:function(e,t){var a=this;if(t!==this.currentPage){var o=e.target,s=new UH(fi,{cancelable:!0,vueTarget:this,target:o});this.$emit(s.type,s,t),s.defaultPrevented||(this.currentPage=t,this.$emit(Fs,this.currentPage),this.$nextTick((function(){oc(o)&&a.$el.contains(o)?Sc(o):a.focusCurrent()})))}},makePage:function(e){return e},linkProps:function(){return{}}}}),zX=Ft({components:{BPagination:IX}});function CX(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function DX(e){for(var t=1;t0?this.localNumberOfPages=this.pages.length:this.localNumberOfPages=SX(this.numberOfPages),this.$nextTick((function(){e.guessCurrentPage()}))},onClick:function(e,t){var a=this;if(t!==this.currentPage){var o=e.currentTarget||e.target,s=new UH(fi,{cancelable:!0,vueTarget:this,target:o});this.$emit(s.type,s,t),s.defaultPrevented||(Qr((function(){a.currentPage=t,a.$emit(Fs,t)})),this.$nextTick((function(){_c(o)})))}},getPageInfo:function(e){if(!Fe(this.pages)||0===this.pages.length||Te(this.pages[e-1])){var t="".concat(this.baseUrl).concat(e);return{link:this.useRouter?{path:t}:t,text:jr(e)}}var a=this.pages[e-1];if(He(a)){var o=a.link;return{link:He(o)?o:this.useRouter?{path:o}:o,text:jr(a.text||e)}}return{link:jr(a),text:jr(e)}},makePage:function(e){var t=this.pageGen,a=this.getPageInfo(e);return Qc(t)?t(e,a):a.text},makeLink:function(e){var t=this.linkGen,a=this.getPageInfo(e);return Qc(t)?t(e,a):a.link},linkProps:function(e){var t=$c(_X,this),a=this.makeLink(e);return this.useRouter||He(a)?t.to=a:t.href=a,t},resolveLink:function(){var e,t=arguments.length>0&&void 0!==arguments[0]?arguments[0]:"";try{e=document.createElement("a"),e.href=ih({to:t},"a","/","/"),document.body.appendChild(e);var a=e,o=a.pathname,s=a.hash,i=a.search;return document.body.removeChild(e),{path:o,hash:s,query:eh(i)}}catch(n){try{e&&e.parentNode&&e.parentNode.removeChild(e)}catch(r){}return{}}},resolveRoute:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:"";try{var t=this.$router.resolve(e,this.$route).route;return{path:t.path,hash:t.hash,query:t.query}}catch(a){return{}}},guessCurrentPage:function(){var e=this.$router,t=this.$route,a=this.computedValue;if(!this.noPageDetect&&!a&&(I||!I&&e))for(var o=e&&t?{path:t.path,hash:t.hash,query:t.query}:{},s=I?window.location||document.location:null,i=s?{path:s.pathname,hash:s.hash,query:eh(s.search)}:{},n=1;!a&&n<=this.localNumberOfPages;n++){var r=this.makeLink(n);a=e&&(He(r)||this.useRouter)?iL(this.resolveRoute(r),o)?n:null:I?iL(this.resolveLink(r),i)?n:null:-1}this.currentPage=a>0?a:0}}}),TX=Ft({components:{BPaginationNav:MX}}),VX={AUTO:"auto",TOP:"top",RIGHT:"right",BOTTOM:"bottom",LEFT:"left",TOPLEFT:"top",TOPRIGHT:"top",RIGHTTOP:"right",RIGHTBOTTOM:"right",BOTTOMLEFT:"bottom",BOTTOMRIGHT:"bottom",LEFTTOP:"left",LEFTBOTTOM:"left"},xX={AUTO:0,TOPLEFT:-1,TOP:0,TOPRIGHT:1,RIGHTTOP:-1,RIGHT:0,RIGHTBOTTOM:1,BOTTOMLEFT:-1,BOTTOM:0,BOTTOMRIGHT:1,LEFTTOP:-1,LEFT:0,LEFTBOTTOM:1},BX={arrowPadding:Wc(hn,6),boundary:Wc([De,Zi],"scrollParent"),boundaryPadding:Wc(hn,5),fallbackPlacement:Wc(on,"flip"),offset:Wc(hn,0),placement:Wc(Zi,"top"),target:Wc([De,Re])},LX=Ms({name:cs,mixins:[fK],props:BX,data:function(){return{noFade:!1,localShow:!0,attachment:this.getAttachment(this.placement)}},computed:{templateType:function(){return"unknown"},popperConfig:function(){var e=this,t=this.placement;return{placement:this.getAttachment(t),modifiers:{offset:{offset:this.getOffset(t)},flip:{behavior:this.fallbackPlacement},arrow:{element:".arrow"},preventOverflow:{padding:this.boundaryPadding,boundariesElement:this.boundary}},onCreate:function(t){t.originalPlacement!==t.placement&&e.popperPlacementChange(t)},onUpdate:function(t){e.popperPlacementChange(t)}}}},created:function(){var e=this;this.$_popper=null,this.localShow=!0,this.$on(_i,(function(t){e.popperCreate(t)}));var t=function(){e.$nextTick((function(){Qr((function(){e.$destroy()}))}))};this.bvParent.$once(Ui,t),this.$once(ii,t)},beforeMount:function(){this.attachment=this.getAttachment(this.placement)},updated:function(){this.updatePopper()},beforeDestroy:function(){this.destroyPopper()},destroyed:function(){var e=this.$el;e&&e.parentNode&&e.parentNode.removeChild(e)},methods:{hide:function(){this.localShow=!1},getAttachment:function(e){return VX[String(e).toUpperCase()]||"auto"},getOffset:function(e){if(!this.offset){var t=this.$refs.arrow||rc(".arrow",this.$el),a=xr(Ic(t).width,0)+xr(this.arrowPadding,0);switch(xX[String(e).toUpperCase()]||0){case 1:return"+50%p - ".concat(a,"px");case-1:return"-50%p + ".concat(a,"px");default:return 0}}return this.offset},popperCreate:function(e){this.destroyPopper(),this.$_popper=new _H["a"](this.target,e,this.popperConfig)},destroyPopper:function(){this.$_popper&&this.$_popper.destroy(),this.$_popper=null},updatePopper:function(){this.$_popper&&this.$_popper.scheduleUpdate()},popperPlacementChange:function(e){this.attachment=this.getAttachment(e.placement)},renderTemplate:function(e){return e("div")}},render:function(e){var t=this,a=this.noFade;return e(vl,{props:{appear:!0,noFade:a},on:{beforeEnter:function(e){return t.$emit(_i,e)},afterEnter:function(e){return t.$emit(ki,e)},beforeLeave:function(e){return t.$emit(ni,e)},afterLeave:function(e){return t.$emit(ii,e)}}},[this.localShow?this.renderTemplate(e):e()])}});function OX(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function EX(e){for(var t=1;t0&&void 0!==arguments[0]?arguments[0]:{},a=!1;at(eZ).forEach((function(o){Te(t[o])||e[o]===t[o]||(e[o]=t[o],"title"===o&&(a=!0))})),a&&this.localShow&&this.fixTitle()},createTemplateAndShow:function(){var e=this.getContainer(),t=this.getTemplate(),a=this.$_tip=wK(this,t,{propsData:{id:this.computedId,html:this.html,placement:this.placement,fallbackPlacement:this.fallbackPlacement,target:this.getPlacementTarget(),boundary:this.getBoundary(),offset:Vr(this.offset,0),arrowPadding:Vr(this.arrowPadding,0),boundaryPadding:Vr(this.boundaryPadding,0)}});this.handleTemplateUpdate(),a.$once(_i,this.onTemplateShow),a.$once(ki,this.onTemplateShown),a.$once(ni,this.onTemplateHide),a.$once(ii,this.onTemplateHidden),a.$once(Ui,this.destroyTemplate),a.$on(ai,this.handleEvent),a.$on(oi,this.handleEvent),a.$on(hi,this.handleEvent),a.$on(di,this.handleEvent),a.$mount(e.appendChild(document.createElement("div")))},hideTemplate:function(){this.$_tip&&this.$_tip.hide(),this.clearActiveTriggers(),this.$_hoverState=""},destroyTemplate:function(){this.setWhileOpenListeners(!1),this.clearHoverTimeout(),this.$_hoverState="",this.clearActiveTriggers(),this.localPlacementTarget=null;try{this.$_tip.$destroy()}catch(e){}this.$_tip=null,this.removeAriaDescribedby(),this.restoreTitle(),this.localShow=!1},getTemplateElement:function(){return this.$_tip?this.$_tip.$el:null},handleTemplateUpdate:function(){var e=this,t=this.$_tip;if(t){var a=["title","content","variant","customClass","noFade","interactive"];a.forEach((function(a){t[a]!==e[a]&&(t[a]=e[a])}))}},show:function(){var e=this.getTarget();if(e&&hc(document.body,e)&&oc(e)&&!this.dropdownOpen()&&(!xe(this.title)&&""!==this.title||!xe(this.content)&&""!==this.content)&&!this.$_tip&&!this.localShow){this.localShow=!0;var t=this.buildEvent(_i,{cancelable:!0});this.emitEvent(t),t.defaultPrevented?this.destroyTemplate():(this.fixTitle(),this.addAriaDescribedby(),this.createTemplateAndShow())}},hide:function(){var e=arguments.length>0&&void 0!==arguments[0]&&arguments[0],t=this.getTemplateElement();if(t&&this.localShow){var a=this.buildEvent(ni,{cancelable:!e});this.emitEvent(a),a.defaultPrevented||this.hideTemplate()}else this.restoreTitle()},forceHide:function(){var e=this.getTemplateElement();e&&this.localShow&&(this.setWhileOpenListeners(!1),this.clearHoverTimeout(),this.$_hoverState="",this.clearActiveTriggers(),this.$_tip&&(this.$_tip.noFade=!0),this.hide(!0))},enable:function(){this.$_enabled=!0,this.emitEvent(this.buildEvent(Xs))},disable:function(){this.$_enabled=!1,this.emitEvent(this.buildEvent(Js))},onTemplateShow:function(){this.setWhileOpenListeners(!0)},onTemplateShown:function(){var e=this.$_hoverState;this.$_hoverState="","out"===e&&this.leave(null),this.emitEvent(this.buildEvent(ki))},onTemplateHide:function(){this.setWhileOpenListeners(!1)},onTemplateHidden:function(){this.destroyTemplate(),this.emitEvent(this.buildEvent(ii))},getTarget:function(){var e=this.target;return Oe(e)?e=dc(e.replace(/^#/,"")):Be(e)?e=e():e&&(e=e.$el||e),Zr(e)?e:null},getPlacementTarget:function(){return this.getTarget()},getTargetId:function(){var e=this.getTarget();return e&&e.id?e.id:null},getContainer:function(){var e=!!this.container&&(this.container.$el||this.container),t=document.body,a=this.getTarget();return!1===e?lc(QX,a)||t:Oe(e)&&dc(e.replace(/^#/,""))||t},getBoundary:function(){return this.boundary?this.boundary.$el||this.boundary:"scrollParent"},isInModal:function(){var e=this.getTarget();return e&&lc(qX,e)},isDropdown:function(){var e=this.getTarget();return e&&uc(e,YX)},dropdownOpen:function(){var e=this.getTarget();return this.isDropdown()&&e&&rc(XX,e)},clearHoverTimeout:function(){clearTimeout(this.$_hoverTimeout),this.$_hoverTimeout=null},clearVisibilityInterval:function(){clearInterval(this.$_visibleInterval),this.$_visibleInterval=null},clearActiveTriggers:function(){for(var e in this.activeTrigger)this.activeTrigger[e]=!1},addAriaDescribedby:function(){var e=this.getTarget(),t=vc(e,"aria-describedby")||"";t=t.split(/\s+/).concat(this.computedId).join(" ").trim(),fc(e,"aria-describedby",t)},removeAriaDescribedby:function(){var e=this,t=this.getTarget(),a=vc(t,"aria-describedby")||"";a=a.split(/\s+/).filter((function(t){return t!==e.computedId})).join(" ").trim(),a?fc(t,"aria-describedby",a):gc(t,"aria-describedby")},fixTitle:function(){var e=this.getTarget();if(Ac(e,"title")){var t=vc(e,"title");fc(e,"title",""),t&&fc(e,ZX,t)}},restoreTitle:function(){var e=this.getTarget();if(Ac(e,ZX)){var t=vc(e,ZX);gc(e,ZX),t&&fc(e,"title",t)}},buildEvent:function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};return new UH(e,GX({cancelable:!1,target:this.getTarget(),relatedTarget:this.getTemplateElement()||null,componentId:this.computedId,vueTarget:this},t))},emitEvent:function(e){var t=e.type;this.emitOnRoot(il(this.templateType,t),e),this.$emit(t,e)},listen:function(){var e=this,t=this.getTarget();t&&(this.setRootListener(!0),this.computedTriggers.forEach((function(a){"click"===a?el(t,"click",e.handleEvent,Wi):"focus"===a?(el(t,"focusin",e.handleEvent,Wi),el(t,"focusout",e.handleEvent,Wi)):"blur"===a?el(t,"focusout",e.handleEvent,Wi):"hover"===a&&(el(t,"mouseenter",e.handleEvent,Wi),el(t,"mouseleave",e.handleEvent,Wi))}),this))},unListen:function(){var e=this,t=["click","focusin","focusout","mouseenter","mouseleave"],a=this.getTarget();this.setRootListener(!1),t.forEach((function(t){a&&tl(a,t,e.handleEvent,Wi)}),this)},setRootListener:function(e){var t=e?"listenOnRoot":"listenOffRoot",a=this.templateType;this[t](nl(a,ni),this.doHide),this[t](nl(a,_i),this.doShow),this[t](nl(a,qs),this.doDisable),this[t](nl(a,Ys),this.doEnable)},setWhileOpenListeners:function(e){this.setModalListener(e),this.setDropdownListener(e),this.visibleCheck(e),this.setOnTouchStartListener(e)},visibleCheck:function(e){var t=this;this.clearVisibilityInterval();var a=this.getTarget();e&&(this.$_visibleInterval=setInterval((function(){var e=t.getTemplateElement();!e||!t.localShow||a.parentNode&&oc(a)||t.forceHide()}),100))},setModalListener:function(e){this.isInModal()&&this[e?"listenOnRoot":"listenOffRoot"](JX,this.forceHide)},setOnTouchStartListener:function(e){var t=this;"ontouchstart"in document.documentElement&&zr(document.body.children).forEach((function(a){al(e,a,"mouseover",t.$_noop)}))},setDropdownListener:function(e){var t=this.getTarget();if(t&&this.bvEventRoot&&this.isDropdown){var a=NH(t);a&&a[e?"$on":"$off"](ki,this.forceHide)}},handleEvent:function(e){var t=this.getTarget();if(t&&!sc(t)&&this.$_enabled&&!this.dropdownOpen()){var a=e.type,o=this.computedTriggers;if("click"===a&&Cr(o,"click"))this.click(e);else if("mouseenter"===a&&Cr(o,"hover"))this.enter(e);else if("focusin"===a&&Cr(o,"focus"))this.enter(e);else if("focusout"===a&&(Cr(o,"focus")||Cr(o,"blur"))||"mouseleave"===a&&Cr(o,"hover")){var s=this.getTemplateElement(),i=e.target,n=e.relatedTarget;if(s&&hc(s,i)&&hc(t,n)||s&&hc(t,i)&&hc(s,n)||s&&hc(s,i)&&hc(s,n)||hc(t,i)&&hc(t,n))return;this.leave(e)}}},doHide:function(e){e&&this.getTargetId()!==e&&this.computedId!==e||this.forceHide()},doShow:function(e){e&&this.getTargetId()!==e&&this.computedId!==e||this.show()},doDisable:function(e){e&&this.getTargetId()!==e&&this.computedId!==e||this.disable()},doEnable:function(e){e&&this.getTargetId()!==e&&this.computedId!==e||this.enable()},click:function(e){this.$_enabled&&!this.dropdownOpen()&&(Sc(e.currentTarget),this.activeTrigger.click=!this.activeTrigger.click,this.isWithActiveTrigger?this.enter(null):this.leave(null))},toggle:function(){this.$_enabled&&!this.dropdownOpen()&&(this.localShow?this.leave(null):this.enter(null))},enter:function(){var e=this,t=arguments.length>0&&void 0!==arguments[0]?arguments[0]:null;t&&(this.activeTrigger["focusin"===t.type?"focus":"hover"]=!0),this.localShow||"in"===this.$_hoverState?this.$_hoverState="in":(this.clearHoverTimeout(),this.$_hoverState="in",this.computedDelay.show?(this.fixTitle(),this.$_hoverTimeout=setTimeout((function(){"in"===e.$_hoverState?e.show():e.localShow||e.restoreTitle()}),this.computedDelay.show)):this.show())},leave:function(){var e=this,t=arguments.length>0&&void 0!==arguments[0]?arguments[0]:null;t&&(this.activeTrigger["focusout"===t.type?"focus":"hover"]=!1,"focusout"===t.type&&Cr(this.computedTriggers,"blur")&&(this.activeTrigger.click=!1,this.activeTrigger.hover=!1)),this.isWithActiveTrigger||(this.clearHoverTimeout(),this.$_hoverState="out",this.computedDelay.hide?this.$_hoverTimeout=setTimeout((function(){"out"===e.$_hoverState&&e.hide()}),this.computedDelay.hide):this.hide())}}});function aZ(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function oZ(e){for(var t=1;t0&&e[yZ].updateData(t)}))}var i={title:o.title,content:o.content,triggers:o.trigger,placement:o.placement,fallbackPlacement:o.fallbackPlacement,variant:o.variant,customClass:o.customClass,container:o.container,boundary:o.boundary,delay:o.delay,offset:o.offset,noFade:!o.animation,id:o.id,disabled:o.disabled,html:o.html},n=e[yZ].__bv_prev_data__;if(e[yZ].__bv_prev_data__=i,!iL(i,n)){var r={target:e};at(i).forEach((function(t){i[t]!==n[t]&&(r[t]="title"!==t&&"content"!==t||!Be(i[t])?i[t]:i[t](e))})),e[yZ].updateData(r)}}},LZ=function(e){e[yZ]&&(e[yZ].$destroy(),e[yZ]=null),delete e[yZ]},OZ={bind:function(e,t,a){BZ(e,t,a)},componentUpdated:function(e,t,a){Ls((function(){BZ(e,t,a)}))},unbind:function(e){LZ(e)}},EZ=Ft({directives:{VBPopover:OZ}}),UZ=Ft({components:{BPopover:vZ},plugins:{VBPopoverPlugin:EZ}}),FZ=Jc({animated:Wc(qi,null),label:Wc(Zi),labelHtml:Wc(Zi),max:Wc(hn,null),precision:Wc(hn,null),showProgress:Wc(qi,null),showValue:Wc(qi,null),striped:Wc(qi,null),value:Wc(hn,0),variant:Wc(Zi)},Vo),HZ=Ms({name:Vo,mixins:[Tr],inject:{getBvProgress:{default:function(){return function(){return{}}}}},props:FZ,computed:{bvProgress:function(){return this.getBvProgress()},progressBarClasses:function(){var e=this.computedAnimated,t=this.computedVariant;return[t?"bg-".concat(t):"",this.computedStriped||e?"progress-bar-striped":"",e?"progress-bar-animated":""]},progressBarStyles:function(){return{width:this.computedValue/this.computedMax*100+"%"}},computedValue:function(){return xr(this.value,0)},computedMax:function(){var e=xr(this.max)||xr(this.bvProgress.max,0);return e>0?e:100},computedPrecision:function(){return Tl(Vr(this.precision,Vr(this.bvProgress.precision,0)),0)},computedProgress:function(){var e=this.computedPrecision,t=Ll(10,e);return Br(100*t*this.computedValue/this.computedMax/t,e)},computedVariant:function(){return this.variant||this.bvProgress.variant},computedStriped:function(){return Le(this.striped)?this.striped:this.bvProgress.striped||!1},computedAnimated:function(){return Le(this.animated)?this.animated:this.bvProgress.animated||!1},computedShowProgress:function(){return Le(this.showProgress)?this.showProgress:this.bvProgress.showProgress||!1},computedShowValue:function(){return Le(this.showValue)?this.showValue:this.bvProgress.showValue||!1}},render:function(e){var t,a=this.label,o=this.labelHtml,s=this.computedValue,i=this.computedPrecision,n={};return this.hasNormalizedSlot()?t=this.normalizeSlot():a||o?n=yO(o,a):this.computedShowProgress?t=this.computedProgress:this.computedShowValue&&(t=Br(s,i)),e("div",{staticClass:"progress-bar",class:this.progressBarClasses,style:this.progressBarStyles,attrs:{role:"progressbar","aria-valuemin":"0","aria-valuemax":jr(this.computedMax),"aria-valuenow":Br(s,i)},domProps:n},t)}});function jZ(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function GZ(e){for(var t=1;t0&&void 0!==arguments[0]?arguments[0]:{},t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};this.noCloseOnRouteChange||e.fullPath===t.fullPath||this.hide()})),NZ),created:function(){this.$_returnFocusEl=null},mounted:function(){var e=this;this.listenOnRoot(t0,this.handleToggle),this.listenOnRoot(e0,this.handleSync),this.$nextTick((function(){e.emitState(e.localShow)}))},activated:function(){this.emitSync()},beforeDestroy:function(){this.localShow=!1,this.$_returnFocusEl=null},methods:{hide:function(){this.localShow=!1},emitState:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:this.localShow;this.emitOnRoot(a0,this.safeId(),e)},emitSync:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:this.localShow;this.emitOnRoot(o0,this.safeId(),e)},handleToggle:function(e){e&&e===this.safeId()&&(this.localShow=!this.localShow)},handleSync:function(e){var t=this;e&&e===this.safeId()&&this.$nextTick((function(){t.emitSync(t.localShow)}))},onKeydown:function(e){var t=e.keyCode;!this.noCloseOnEsc&&t===QB&&this.localShow&&this.hide()},onBackdropClick:function(){this.localShow&&!this.noCloseOnBackdrop&&this.hide()},onTopTrapFocus:function(){var e=Rc(this.$refs.content);this.enforceFocus(e.reverse()[0])},onBottomTrapFocus:function(){var e=Rc(this.$refs.content);this.enforceFocus(e[0])},onBeforeEnter:function(){this.$_returnFocusEl=ec(I?[document.body]:[]),this.isOpen=!0},onAfterEnter:function(e){hc(e,ec())||this.enforceFocus(e),this.$emit(ki)},onAfterLeave:function(){this.enforceFocus(this.$_returnFocusEl),this.$_returnFocusEl=null,this.isOpen=!1,this.$emit(ii)},enforceFocus:function(e){this.noEnforceFocus||Sc(e)}},render:function(e){var t,a=this.bgVariant,o=this.width,s=this.textVariant,i=this.localShow,n=""===this.shadow||this.shadow,r=e(this.tag,{staticClass:ZZ,class:[(t={shadow:!0===n},XZ(t,"shadow-".concat(n),n&&!0!==n),XZ(t,"".concat(ZZ,"-right"),this.right),XZ(t,"bg-".concat(a),a),XZ(t,"text-".concat(s),s),t),this.sidebarClass],style:{width:o},attrs:this.computedAttrs,directives:[{name:"show",value:i}],ref:"content"},[f0(e,this)]);r=e("transition",{props:this.transitionProps,on:{beforeEnter:this.onBeforeEnter,afterEnter:this.onAfterEnter,afterLeave:this.onAfterLeave}},[r]);var c=e(vl,{props:{noFade:this.noSlide}},[g0(e,this)]),l=e(),h=e();return this.backdrop&&i&&(l=e("div",{attrs:{tabindex:"0"},on:{focus:this.onTopTrapFocus}}),h=e("div",{attrs:{tabindex:"0"},on:{focus:this.onBottomTrapFocus}})),e("div",{staticClass:"b-sidebar-outer",style:{zIndex:this.zIndex},attrs:{tabindex:"-1"},on:{keydown:this.onKeydown}},[l,r,h,c])}}),A0=Ft({components:{BSidebar:v0},plugins:{VBTogglePlugin:RH}});function P0(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var b0=Jc({animation:Wc(Zi,"wave"),height:Wc(Zi),size:Wc(Zi),type:Wc(Zi,"text"),variant:Wc(Zi),width:Wc(Zi)},Lo),y0=Ms({name:Lo,functional:!0,props:b0,render:function(e,t){var a,o=t.data,s=t.props,i=s.size,n=s.animation,r=s.variant;return e("div",bs(o,{staticClass:"b-skeleton",style:{width:i||s.width,height:i||s.height},class:(a={},P0(a,"b-skeleton-".concat(s.type),!0),P0(a,"b-skeleton-animate-".concat(n),n),P0(a,"bg-".concat(r),r),a)}))}});function w0(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function I0(e){for(var t=1;t0}}});function M0(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var T0={stacked:Wc(rn,!1)},V0=Ms({props:T0,computed:{isStacked:function(){var e=this.stacked;return""===e||e},isStackedAlways:function(){return!0===this.isStacked},stackedTableClasses:function(){var e=this.isStackedAlways;return M0({"b-table-stacked":e},"b-table-stacked-".concat(this.stacked),!e&&this.isStacked)}}});function x0(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function B0(e){for(var t=1;t0&&!n,[i,{"table-striped":this.striped,"table-hover":t,"table-dark":this.dark,"table-bordered":this.bordered,"table-borderless":this.borderless,"table-sm":this.small,border:this.outlined,"b-table-fixed":this.fixed,"b-table-caption-top":this.captionTop,"b-table-no-border-collapse":this.noBorderCollapse},a?"".concat(this.dark?"bg":"table","-").concat(a):"",s,o]},tableAttrs:function(){var e=Jl(this),t=e.computedItems,a=e.filteredItems,o=e.computedFields,s=e.selectableTableAttrs,i=e.computedBusy,n=this.isTableSimple?{}:{"aria-busy":jr(i),"aria-colcount":jr(o.length),"aria-describedby":this.bvAttrs["aria-describedby"]||this.$refs.caption?this.captionId:null},r=t&&a&&a.length>t.length?jr(a.length):null;return B0(B0(B0({"aria-rowcount":r},this.bvAttrs),{},{id:this.safeId(),role:this.bvAttrs.role||"table"},n),s)}},render:function(e){var t=Jl(this),a=t.wrapperClasses,o=t.renderCaption,s=t.renderColgroup,i=t.renderThead,n=t.renderTbody,r=t.renderTfoot,c=[];this.isTableSimple?c.push(this.normalizeSlot()):(c.push(o?o():null),c.push(s?s():null),c.push(i?i():null),c.push(n?n():null),c.push(r?r():null));var l=e("table",{staticClass:"table b-table",class:this.tableClasses,attrs:this.tableAttrs,key:"b-table"},c.filter(yt));return a.length>0?e("div",{class:a,style:this.wrapperStyles,key:"wrap"},[l]):l}});function U0(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function F0(e){for(var t=1;t0},J0=Jc({animation:Wc(Zi),columns:Wc(Qi,5,q0),hideHeader:Wc(qi,!1),rows:Wc(Qi,3,q0),showFooter:Wc(qi,!1),tableProps:Wc(Yi,{})},Uo),K0=Ms({name:Uo,functional:!0,props:J0,render:function(e,t){var a=t.data,o=t.props,s=o.animation,i=o.columns,n=e("th",[e(y0,{props:{animation:s}})]),r=e("tr",Rr(i,n)),c=e("td",[e(y0,{props:{width:"75%",animation:s}})]),l=e("tr",Rr(i,c)),h=e("tbody",Rr(o.rows,l)),d=o.hideHeader?e():e("thead",[r]),m=o.showFooter?e("tfoot",[r]):e();return e(G0,bs(a,{props:N0({},o.tableProps)}),[d,h,m])}}),Q0=Jc({loading:Wc(qi,!1)},Fo),Y0=Ms({name:Fo,functional:!0,props:Q0,render:function(e,t){var a=t.data,o=t.props,s=t.slots,i=t.scopedSlots,n=s(),r=i||{},c={};return o.loading?e("div",bs(a,{attrs:{role:"alert","aria-live":"polite","aria-busy":!0},staticClass:"b-skeleton-wrapper",key:"loading"}),Mr(Nn,c,r,n)):Mr(wn,c,r,n)}}),X0=Ft({components:{BSkeleton:y0,BSkeletonIcon:D0,BSkeletonImg:_0,BSkeletonTable:K0,BSkeletonWrapper:Y0}}),Z0=Ft({components:{BSpinner:WY}});function e1(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function t1(e){for(var t=1;t0?e:null},p1=function(e){return xe(e)||m1(e)>0},u1=Jc({colspan:Wc(hn,null,p1),rowspan:Wc(hn,null,p1),stackedHeading:Wc(Zi),stickyColumn:Wc(qi,!1),variant:Wc(Zi)},Wo),f1=Ms({name:Wo,mixins:[fL,zL,Tr],inject:{getBvTableTr:{default:function(){return function(){return{}}}}},inheritAttrs:!1,props:u1,computed:{bvTableTr:function(){return this.getBvTableTr()},tag:function(){return"td"},inTbody:function(){return this.bvTableTr.inTbody},inThead:function(){return this.bvTableTr.inThead},inTfoot:function(){return this.bvTableTr.inTfoot},isDark:function(){return this.bvTableTr.isDark},isStacked:function(){return this.bvTableTr.isStacked},isStackedCell:function(){return this.inTbody&&this.isStacked},isResponsive:function(){return this.bvTableTr.isResponsive},isStickyHeader:function(){return this.bvTableTr.isStickyHeader},hasStickyHeader:function(){return this.bvTableTr.hasStickyHeader},isStickyColumn:function(){return!this.isStacked&&(this.isResponsive||this.hasStickyHeader)&&this.stickyColumn},rowVariant:function(){return this.bvTableTr.variant},headVariant:function(){return this.bvTableTr.headVariant},footVariant:function(){return this.bvTableTr.footVariant},tableVariant:function(){return this.bvTableTr.tableVariant},computedColspan:function(){return m1(this.colspan)},computedRowspan:function(){return m1(this.rowspan)},cellClasses:function(){var e=this.variant,t=this.headVariant,a=this.isStickyColumn;return(!e&&this.isStickyHeader&&!t||!e&&a&&this.inTfoot&&!this.footVariant||!e&&a&&this.inThead&&!t||!e&&a&&this.inTbody)&&(e=this.rowVariant||this.tableVariant||"b-table-default"),[e?"".concat(this.isDark?"bg":"table","-").concat(e):null,a?"b-table-sticky-column":null]},cellAttrs:function(){var e=this.stackedHeading,t=this.inThead||this.inTfoot,a=this.computedColspan,o=this.computedRowspan,s="cell",i=null;return t?(s="columnheader",i=a>0?"colspan":"col"):tc(this.tag,"th")&&(s="rowheader",i=o>0?"rowgroup":"row"),h1(h1({colspan:a,rowspan:o,role:s,scope:i},this.bvAttrs),{},{"data-label":this.isStackedCell&&!xe(e)?jr(e):null})}},render:function(e){var t=[this.normalizeSlot()];return e(this.tag,{class:this.cellClasses,attrs:this.cellAttrs,on:this.bvListeners},[this.isStackedCell?e("div",[t]):t])}});function g1(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var v1="busy",A1=Fi+v1,P1=g1({},v1,Wc(qi,!1)),b1=Ms({props:P1,data:function(){return{localBusy:!1}},computed:{computedBusy:function(){return this[v1]||this.localBusy}},watch:{localBusy:function(e,t){e!==t&&this.$emit(A1,e)}},methods:{stopIfBusy:function(e){return!!this.computedBusy&&(ol(e),!0)},renderBusy:function(){var e=this.tbodyTrClass,t=this.tbodyTrAttr,a=this.$createElement;return this.computedBusy&&this.hasNormalizedSlot(pr)?a(n1,{staticClass:"b-table-busy-slot",class:[Be(e)?e(null,pr):e],attrs:Be(t)?t(null,pr):t,key:"table-busy-slot"},[a(f1,{props:{colspan:this.computedFields.length||null}},[this.normalizeSlot(pr)])]):null}}}),y1={caption:Wc(Zi),captionHtml:Wc(Zi)},w1=Ms({props:y1,computed:{captionId:function(){return this.isStacked?this.safeId("_caption_"):null}},methods:{renderCaption:function(){var e=this.caption,t=this.captionHtml,a=this.$createElement,o=a(),s=this.hasNormalizedSlot(ur);return(s||e||t)&&(o=a("caption",{attrs:{id:this.captionId},domProps:s?{}:yO(t,e),key:"caption",ref:"caption"},this.normalizeSlot(ur))),o}}}),I1={},z1=Ms({methods:{renderColgroup:function(){var e=this.computedFields,t=this.$createElement,a=t();return this.hasNormalizedSlot(fr)&&(a=t("colgroup",{key:"colgroup"},[this.normalizeSlot(fr,{columns:e.length,fields:e})])),a}}}),C1={emptyFilteredHtml:Wc(Zi),emptyFilteredText:Wc(Zi,"There are no records matching your request"),emptyHtml:Wc(Zi),emptyText:Wc(Zi,"There are no records to show"),showEmpty:Wc(qi,!1)},D1=Ms({props:C1,methods:{renderEmpty:function(){var e=Jl(this),t=e.computedItems,a=e.computedBusy,o=this.$createElement,s=o();if(this.showEmpty&&(!t||0===t.length)&&(!a||!this.hasNormalizedSlot(pr))){var i=this.computedFields,n=this.isFiltered,r=this.emptyText,c=this.emptyHtml,l=this.emptyFilteredText,h=this.emptyFilteredHtml,d=this.tbodyTrClass,m=this.tbodyTrAttr;s=this.normalizeSlot(n?Sn:Rn,{emptyFilteredHtml:h,emptyFilteredText:l,emptyHtml:c,emptyText:r,fields:i,items:t}),s||(s=o("div",{class:["text-center","my-2"],domProps:n?yO(h,l):yO(c,r)})),s=o(f1,{props:{colspan:i.length||null}},[o("div",{attrs:{role:"alert","aria-live":"polite"}},[s])]),s=o(n1,{staticClass:"b-table-empty-row",class:[Be(d)?d(null,"row-empty"):d],attrs:Be(m)?m(null,"row-empty"):m,key:n?"b-empty-filtered-row":"b-empty-row"},[s])}return s}}}),R1=function e(t){return xe(t)?"":He(t)&&!Ge(t)?at(t).sort().map((function(a){return e(t[a])})).filter((function(e){return!!e})).join(" "):jr(t)};function S1(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function _1(e){for(var t=1;t3&&void 0!==arguments[3]?arguments[3]:{},s=at(o).reduce((function(t,a){var s=o[a],i=s.filterByFormatted,n=Be(i)?i:i?s.formatter:null;return Be(n)&&(t[a]=n(e[a],a,e)),t}),it(e)),i=at(s).filter((function(e){return!x1[e]&&!(Fe(t)&&t.length>0&&Cr(t,e))&&!(Fe(a)&&a.length>0&&!Cr(a,e))}));return nt(s,i)},O1=function(e,t,a,o){return He(e)?R1(L1(e,t,a,o)):""};function E1(e){return j1(e)||H1(e)||F1(e)||U1()}function U1(){throw new TypeError("Invalid attempt to spread non-iterable instance.\nIn order to be iterable, non-array objects must have a [Symbol.iterator]() method.")}function F1(e,t){if(e){if("string"===typeof e)return G1(e,t);var a=Object.prototype.toString.call(e).slice(8,-1);return"Object"===a&&e.constructor&&(a=e.constructor.name),"Map"===a||"Set"===a?Array.from(e):"Arguments"===a||/^(?:Ui|I)nt(?:8|16|32)(?:Clamped)?Array$/.test(a)?G1(e,t):void 0}}function H1(e){if("undefined"!==typeof Symbol&&null!=e[Symbol.iterator]||null!=e["@@iterator"])return Array.from(e)}function j1(e){if(Array.isArray(e))return G1(e)}function G1(e,t){(null==t||t>e.length)&&(t=e.length);for(var a=0,o=new Array(t);a0&&Ct(W1,Go),e},localFiltering:function(){return!this.hasProvider||!!this.noProviderFiltering},filteredCheck:function(){var e=this.filteredItems,t=this.localItems,a=this.localFilter;return{filteredItems:e,localItems:t,localFilter:a}},localFilterFn:function(){var e=this.filterFunction;return Qc(e)?e:null},filteredItems:function(){var e=this.localItems,t=this.localFilter,a=this.localFiltering?this.filterFnFactory(this.localFilterFn,t)||this.defaultFilterFnFactory(t):null;return a&&e.length>0?e.filter(a):e}},watch:{computedFilterDebounce:function(e){!e&&this.$_filterTimer&&(this.clearFilterTimer(),this.localFilter=this.filterSanitize(this.filter))},filter:{deep:!0,handler:function(e){var t=this,a=this.computedFilterDebounce;this.clearFilterTimer(),a&&a>0?this.$_filterTimer=setTimeout((function(){t.localFilter=t.filterSanitize(e)}),a):this.localFilter=this.filterSanitize(e)}},filteredCheck:function(e){var t=e.filteredItems,a=e.localFilter,o=!1;a?iL(a,[])||iL(a,{})?o=!1:a&&(o=!0):o=!1,o&&this.$emit(Zs,t,t.length),this.isFiltered=o},isFiltered:function(e,t){if(!1===e&&!0===t){var a=this.localItems;this.$emit(Zs,a,a.length)}}},created:function(){var e=this;this.$_filterTimer=null,this.$nextTick((function(){e.isFiltered=Boolean(e.localFilter)}))},beforeDestroy:function(){this.clearFilterTimer()},methods:{clearFilterTimer:function(){clearTimeout(this.$_filterTimer),this.$_filterTimer=null},filterSanitize:function(e){return!this.localFiltering||this.localFilterFn||Oe(e)||$e(e)?bt(e):""},filterFnFactory:function(e,t){if(!e||!Be(e)||!t||iL(t,[])||iL(t,{}))return null;var a=function(a){return e(a,t)};return a},defaultFilterFnFactory:function(e){var t=this;if(!e||!Oe(e)&&!$e(e))return null;var a=e;if(Oe(a)){var o=Hr(e).replace(J,"\\s+");a=new RegExp(".*".concat(o,".*"),"i")}var s=function(e){return a.lastIndex=0,a.test(O1(e,t.computedFilterIgnored,t.computedFilterIncluded,t.computedFieldsObj))};return s}}}),q1=function(e,t){var a=null;return Oe(t)?a={key:e,label:t}:Be(t)?a={key:e,formatter:t}:He(t)?(a=it(t),a.key=a.key||e):!1!==t&&(a={key:e}),a},J1=function(e,t){var a=[];if(Fe(e)&&e.filter(yt).forEach((function(e){if(Oe(e))a.push({key:e,label:Er(e)});else if(He(e)&&e.key&&Oe(e.key))a.push(it(e));else if(He(e)&&1===at(e).length){var t=at(e)[0],o=q1(t,e[t]);o&&a.push(o)}})),0===a.length&&Fe(t)&&t.length>0){var o=t[0];at(o).forEach((function(e){x1[e]||a.push({key:e,label:Er(e)})}))}var s={};return a.filter((function(e){return!s[e.key]&&(s[e.key]=!0,e.label=Oe(e.label)?e.label:Er(e.key),!0)}))};function K1(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Q1(e){for(var t=1;t0&&e.some(yt)},selectableIsMultiSelect:function(){return this.isSelectable&&Cr(["range","multi"],this.selectMode)},selectableTableClasses:function(){var e,t=this.isSelectable;return e={"b-table-selectable":t},d5(e,"b-table-select-".concat(this.selectMode),t),d5(e,"b-table-selecting",this.selectableHasSelection),d5(e,"b-table-selectable-no-click",t&&!this.hasSelectableRowClick),e},selectableTableAttrs:function(){if(!this.isSelectable)return{};var e=this.bvAttrs.role||f5;return{role:e,"aria-multiselectable":e===f5?jr(this.selectableIsMultiSelect):null}}},watch:{computedItems:function(e,t){var a=!1;if(this.isSelectable&&this.selectedRows.length>0){a=Fe(e)&&Fe(t)&&e.length===t.length;for(var o=0;a&&o=0&&e0&&(this.selectedLastClicked=-1,this.selectedRows=this.selectableIsMultiSelect?Rr(e,!0):[!0])},isRowSelected:function(e){return!(!Ee(e)||!this.selectedRows[e])},clearSelected:function(){this.selectedLastClicked=-1,this.selectedRows=[]},selectableRowClasses:function(e){if(this.isSelectable&&this.isRowSelected(e)){var t=this.selectedVariant;return d5({"b-table-row-selected":!0},"".concat(this.dark?"bg":"table","-").concat(t),t)}return{}},selectableRowAttrs:function(e){return{"aria-selected":this.isSelectable?this.isRowSelected(e)?"true":"false":null}},setSelectionHandlers:function(e){var t=e&&!this.noSelectOnClick?"$on":"$off";this[t](yi,this.selectionHandler),this[t](Zs,this.clearSelected),this[t](Ns,this.clearSelected)},selectionHandler:function(e,t,a){if(this.isSelectable&&!this.noSelectOnClick){var o=this.selectMode,s=this.selectedLastRow,i=this.selectedRows.slice(),n=!i[t];if("single"===o)i=[];else if("range"===o)if(s>-1&&a.shiftKey){for(var r=Ml(s,t);r<=Tl(s,t);r++)i[r]=!0;n=!0}else a.ctrlKey||a.metaKey||(i=[],n=!0),n&&(this.selectedLastRow=t);i[t]=n,this.selectedRows=i}else this.clearSelected()}}}),A5=function(e,t){return e.map((function(e,t){return[t,e]})).sort(function(e,t){return this(e[1],t[1])||e[0]-t[0]}.bind(t)).map((function(e){return e[1]}))},P5=function(e){return xe(e)?"":Ue(e)?xr(e,e):e},b5=function(e,t){var a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:{},o=a.sortBy,s=void 0===o?null:o,i=a.formatter,n=void 0===i?null:i,r=a.locale,c=void 0===r?void 0:r,l=a.localeOptions,h=void 0===l?{}:l,d=a.nullLast,m=void 0!==d&&d,p=It(e,s,null),u=It(t,s,null);return Be(n)&&(p=n(p,s,e),u=n(u,s,t)),p=P5(p),u=P5(u),Ge(p)&&Ge(u)||Ee(p)&&Ee(u)?pu?1:0:m&&""===p&&""!==u?1:m&&""!==p&&""===u?-1:R1(p).localeCompare(R1(u),c,h)};function y5(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function w5(e){for(var t=1;t0&&void 0!==arguments[0]?arguments[0]:document,t=zc();return!!(t&&""!==t.toString().trim()&&t.containsNode&&Zr(e))&&t.containsNode(e,!0)},j5=Jc(u1,Qo),G5=Ms({name:Qo,extends:f1,props:j5,computed:{tag:function(){return"th"}}});function W5(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function N5(e){for(var t=1;te.length)&&(t=e.length);for(var a=0,o=new Array(t);a0&&(P=String((r-1)*c+t+1));var b=jr(It(e,n))||null,y=b||jr(t),w=b?this.safeId("_row_".concat(b)):null,I=Jl(this).selectableRowClasses?this.selectableRowClasses(t):{},z=Jl(this).selectableRowAttrs?this.selectableRowAttrs(t):{},C=Be(l)?l(e,"row"):l,D=Be(h)?h(e,"row"):h;if(g.push(m(n1,$5({class:[C,I,u?"b-table-has-details":""],props:{variant:e[T1]||null},attrs:N5(N5({id:w},D),{},{tabindex:f?"0":null,"data-pk":b||null,"aria-details":v,"aria-owns":v,"aria-rowindex":P},z),on:{mouseenter:this.rowHovered,mouseleave:this.rowUnhovered},key:"__b-table-row-".concat(y,"__"),ref:"item-rows"},_s,!0),A)),u){var R={item:e,index:t,fields:s,toggleDetails:this.toggleDetailsFactory(p,e)};Jl(this).supportsSelectableRows&&(R.rowSelected=this.isRowSelected(t),R.selectRow=function(){return a.selectRow(t)},R.unselectRow=function(){return a.unselectRow(t)});var S=m(f1,{props:{colspan:s.length},class:this.detailsTdClass},[this.normalizeSlot(mr,R)]);i&&g.push(m("tr",{staticClass:"d-none",attrs:{"aria-hidden":"true",role:"presentation"},key:"__b-table-details-stripe__".concat(y)}));var _=Be(this.tbodyTrClass)?this.tbodyTrClass(e,mr):this.tbodyTrClass,k=Be(this.tbodyTrAttr)?this.tbodyTrAttr(e,mr):this.tbodyTrAttr;g.push(m(n1,{staticClass:"b-table-details",class:[_],props:{variant:e[T1]||null},attrs:N5(N5({},k),{},{id:v,tabindex:"-1"}),key:"__b-table-details__".concat(y)},[S]))}else p&&(g.push(m()),i&&g.push(m()));return g}}});function t2(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function a2(e){for(var t=1;t0&&a&&a.length>0?zr(t.children).filter((function(e){return Cr(a,e)})):[]},getTbodyTrIndex:function(e){if(!Zr(e))return-1;var t="TR"===e.tagName?e:lc("tr",e,!0);return t?this.getTbodyTrs().indexOf(t):-1},emitTbodyRowEvent:function(e,t){if(e&&this.hasListener(e)&&t&&t.target){var a=this.getTbodyTrIndex(t.target);if(a>-1){var o=this.computedItems[a];this.$emit(e,o,a,t)}}},tbodyRowEventStopped:function(e){return this.stopIfBusy&&this.stopIfBusy(e)},onTbodyRowKeydown:function(e){var t=e.target,a=e.keyCode;if(!this.tbodyRowEventStopped(e)&&"TR"===t.tagName&&ac(t)&&0===t.tabIndex)if(Cr([KB,aL],a))ol(e),this.onTBodyRowClicked(e);else if(Cr([oL,qB,YB,JB],a)){var o=this.getTbodyTrIndex(t);if(o>-1){ol(e);var s=this.getTbodyTrs(),i=e.shiftKey;a===YB||i&&a===oL?Sc(s[0]):a===JB||i&&a===qB?Sc(s[s.length-1]):a===oL&&o>0?Sc(s[o-1]):a===qB&&oe.length)&&(t=e.length);for(var a=0,o=new Array(t);a0&&void 0!==arguments[0]&&arguments[0],a=Jl(this),o=a.computedFields,s=a.isSortable,i=a.isSelectable,n=a.headVariant,r=a.footVariant,c=a.headRowVariant,l=a.footRowVariant,h=this.$createElement;if(this.isStackedAlways||0===o.length)return h();var d=s||this.hasListener(si),m=i?this.selectAllRows:QU,p=i?this.clearSelected:QU,u=function(a,o){var i=a.label,n=a.labelHtml,r=a.variant,c=a.stickyColumn,l=a.key,u=null;a.label.trim()||a.headerTitle||(u=Er(a.key));var f={};d&&(f.click=function(o){e.headClicked(o,a,t)},f.keydown=function(o){var s=o.keyCode;s!==KB&&s!==aL||e.headClicked(o,a,t)});var g=s?e.sortTheadThAttrs(l,a,t):{},v=s?e.sortTheadThClasses(l,a,t):null,A=s?e.sortTheadThLabel(l,a,t):null,P={class:[{"position-relative":A},e.fieldClasses(a),v],props:{variant:r,stickyColumn:c},style:a.thStyle||{},attrs:D2(D2({tabindex:d&&a.sortable?"0":null,abbr:a.headerAbbr||null,title:a.headerTitle||null,"aria-colindex":o+1,"aria-label":u},e.getThValues(null,l,a.thAttr,t?"foot":"head",{})),g),on:f,key:l},b=[S2(l),S2(l.toLowerCase()),S2()];t&&(b=[_2(l),_2(l.toLowerCase()),_2()].concat(P2(b)));var y={label:i,column:l,field:a,isFoot:t,selectAllRows:m,clearSelected:p},w=e.normalizeSlot(b,y)||h("div",{domProps:yO(n,i)}),I=A?h("span",{staticClass:"sr-only"}," (".concat(A,")")):null;return h(G5,P,[w,I].filter(yt))},f=o.map(u).filter(yt),g=[];if(t)g.push(h(n1,{class:this.tfootTrClass,props:{variant:xe(l)?c:l}},f));else{var v={columns:o.length,fields:o,selectAllRows:m,clearSelected:p};g.push(this.normalizeSlot(Pr,v)||h()),g.push(h(n1,{class:this.theadTrClass,props:{variant:c}},f))}return h(t?d2:A2,{class:(t?this.tfootClass:this.theadClass)||null,props:t?{footVariant:r||n||null}:{headVariant:n||null},key:t?"bv-tfoot":"bv-thead"},g)}}}),T2={},V2=Ms({methods:{renderTopRow:function(){var e=this.computedFields,t=this.stacked,a=this.tbodyTrClass,o=this.tbodyTrAttr,s=this.$createElement;return this.hasNormalizedSlot(wr)&&!0!==t&&""!==t?s(n1,{staticClass:"b-table-top-row",class:[Be(a)?a(null,"row-top"):a],attrs:Be(o)?o(null,"row-top"):o,key:"b-top-row"},[this.normalizeSlot(wr,{columns:e.length,fields:e})]):s()}}});function x2(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function B2(e){for(var t=1;t0&&void 0!==arguments[0])||arguments[0];if(this.$_observer&&this.$_observer.disconnect(),this.$_observer=null,t){var a=function(){e.$nextTick((function(){Qr((function(){e.updateTabs()}))}))};this.$_observer=tF(this.$refs.content,a,{childList:!0,subtree:!1,attributes:!0,attributeFilter:["id"]})}},getTabs:function(){var e=this.registeredTabs,t=[];if(I&&e.length>0){var a=e.map((function(e){return"#".concat(e.safeId())})).join(", ");t=nc(a,this.$el).map((function(e){return e.id})).filter(yt)}return A5(e,(function(e,a){return t.indexOf(e.safeId())-t.indexOf(a.safeId())}))},updateTabs:function(){var e=this.getTabs(),t=e.indexOf(e.slice().reverse().find((function(e){return e.localActive&&!e.disabled})));if(t<0){var a=this.currentTab;a>=e.length?t=e.indexOf(e.slice().reverse().find(s3)):e[a]&&!e[a].disabled&&(t=a)}t<0&&(t=e.indexOf(e.find(s3))),e.forEach((function(e,a){e.localActive=a===t})),this.tabs=e,this.currentTab=t},getButtonForTab:function(e){return(this.$refs.buttons||[]).find((function(t){return t.tab===e}))},updateButton:function(e){var t=this.getButtonForTab(e);t&&t.$forceUpdate&&t.$forceUpdate()},activateTab:function(e){var t=this.currentTab,a=this.tabs,o=!1;if(e){var s=a.indexOf(e);if(s!==t&&s>-1&&!e.disabled){var i=new UH(Os,{cancelable:!0,vueTarget:this,componentId:this.safeId()});this.$emit(i.type,s,t,i),i.defaultPrevented||(this.currentTab=s,o=!0)}}return o||this[a3]===t||this.$emit(o3,t),o},deactivateTab:function(e){return!!e&&this.activateTab(this.tabs.filter((function(t){return t!==e})).find(s3))},focusButton:function(e){var t=this;this.$nextTick((function(){Sc(t.getButtonForTab(e))}))},emitTabClick:function(e,t){We(t)&&e&&e.$emit&&!e.disabled&&e.$emit(js,t)},clickTab:function(e,t){this.activateTab(e),this.emitTabClick(e,t)},firstTab:function(e){var t=this.tabs.find(s3);this.activateTab(t)&&e&&(this.focusButton(t),this.emitTabClick(t,e))},previousTab:function(e){var t=Tl(this.currentTab,0),a=this.tabs.slice(0,t).reverse().find(s3);this.activateTab(a)&&e&&(this.focusButton(a),this.emitTabClick(a,e))},nextTab:function(e){var t=Tl(this.currentTab,-1),a=this.tabs.slice(t+1).find(s3);this.activateTab(a)&&e&&(this.focusButton(a),this.emitTabClick(a,e))},lastTab:function(e){var t=this.tabs.slice().reverse().find(s3);this.activateTab(t)&&e&&(this.focusButton(t),this.emitTabClick(t,e))}},render:function(e){var t=this,a=this.align,o=this.card,s=this.end,i=this.fill,n=this.firstTab,r=this.justified,c=this.lastTab,l=this.nextTab,h=this.noKeyNav,d=this.noNavStyle,m=this.pills,p=this.previousTab,u=this.small,f=this.tabs,g=this.vertical,v=f.find((function(e){return e.localActive&&!e.disabled})),A=f.find((function(e){return!e.disabled})),P=f.map((function(a,o){var s,i=a.safeId,r=null;return h||(r=-1,(a===v||!v&&a===A)&&(r=null)),e(i3,Q2({props:{controls:i?i():null,id:a.controlledBy||(i?i("_BV_tab_button_"):null),noKeyNav:h,posInSet:o+1,setSize:f.length,tab:a,tabIndex:r},on:(s={},Q2(s,js,(function(e){t.clickTab(a,e)})),Q2(s,ei,n),Q2(s,vi,p),Q2(s,mi,l),Q2(s,li,c),s),key:a[Rs]||o,ref:"buttons"},_s,!0))})),b=e(QQ,{class:this.localNavClass,attrs:{role:"tablist",id:this.safeId("_BV_tab_controls_")},props:{fill:i,justified:r,align:a,tabs:!d&&!m,pills:!d&&m,vertical:g,small:u,cardHeader:o&&!g},ref:"nav"},[this.normalizeSlot(vr)||e(),P,this.normalizeSlot(gr)||e()]);b=e("div",{class:[{"card-header":o&&!g&&!s,"card-footer":o&&!g&&s,"col-auto":g},this.navWrapperClass],key:"bv-tabs-nav"},[b]);var y=this.normalizeSlot()||[],w=e();0===y.length&&(w=e("div",{class:["tab-pane","active",{"card-body":o}],key:"bv-empty-tab"},this.normalizeSlot(Rn)));var I=e("div",{staticClass:"tab-content",class:[{col:g},this.contentClass],attrs:{id:this.safeId("_BV_tab_container_")},key:"bv-content",ref:"content"},[y,w]);return e(this.tag,{staticClass:"tabs",class:{row:g,"no-gutters":g&&o},attrs:{id:this.safeId()}},[s?I:e(),b,s?e():I])}});function l3(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function h3(e){for(var t=1;t" with name "'.concat(e,'" already exists in the document.'),es),this.dead=!0):this.doRender=!0},beforeDestroy:function(){this.doRender&&this.emitOnRoot(il(es,$s),this.name)},destroyed:function(){var e=this.$el;e&&e.parentNode&&e.parentNode.removeChild(e)},render:function(e){var t=e("div",{class:["d-none",{"b-dead-toaster":this.dead}]});if(this.doRender){var a=e(P3["PortalTarget"],{staticClass:"b-toaster-slot",props:{name:this.staticName,multiple:!0,tag:"div",slim:!1,transition:b3}});t=e("div",{staticClass:"b-toaster",class:[this.staticName],attrs:{id:this.staticName,role:this.role||null,"aria-live":this.ariaLive,"aria-atomic":this.ariaAtomic}},[a])}return t}});function I3(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function z3(e){for(var t=1;t1&&void 0!==arguments[1]?arguments[1]:{};return new UH(e,z3(z3({cancelable:!1,target:this.$el||null,relatedTarget:null},t),{},{vueTarget:this,componentId:this.safeId()}))},emitEvent:function(e){var t=e.type;this.emitOnRoot(il(Zo,t),e),this.$emit(t,e)},ensureToaster:function(){if(!this.static){var e=this.computedToaster;if(!P3["Wormhole"].hasTarget(e)){var t=document.createElement("div");document.body.appendChild(t);var a=wK(this.bvEventRoot,w3,{propsData:{name:e}});a.$mount(t)}}},startDismissTimer:function(){this.clearDismissTimer(),this.noAutoHide||(this.$_dismissTimer=setTimeout(this.hide,this.resumeDismiss||this.computedDuration),this.dismissStarted=Date.now(),this.resumeDismiss=0)},clearDismissTimer:function(){clearTimeout(this.$_dismissTimer),this.$_dismissTimer=null},setHoverHandler:function(e){var t=this.$refs["b-toast"];al(e,t,"mouseenter",this.onPause,Wi),al(e,t,"mouseleave",this.onUnPause,Wi)},onPause:function(){if(!this.noAutoHide&&!this.noHoverPause&&this.$_dismissTimer&&!this.resumeDismiss){var e=Date.now()-this.dismissStarted;e>0&&(this.clearDismissTimer(),this.resumeDismiss=Tl(this.computedDuration-e,M3))}},onUnPause:function(){this.noAutoHide||this.noHoverPause||!this.resumeDismiss?this.resumeDismiss=this.dismissStarted=0:this.startDismissTimer()},onLinkClick:function(){var e=this;this.$nextTick((function(){Qr((function(){e.hide()}))}))},onBeforeEnter:function(){this.isTransitioning=!0},onAfterEnter:function(){this.isTransitioning=!1;var e=this.buildEvent(ki);this.emitEvent(e),this.startDismissTimer(),this.setHoverHandler(!0)},onBeforeLeave:function(){this.isTransitioning=!0},onAfterLeave:function(){this.isTransitioning=!1,this.order=0,this.resumeDismiss=this.dismissStarted=0;var e=this.buildEvent(ii);this.emitEvent(e),this.doRender=!1},makeToast:function(e){var t=this,a=this.title,o=this.slotScope,s=th(this),i=[],n=this.normalizeSlot(yr,o);n?i.push(n):a&&i.push(e("strong",{staticClass:"mr-2"},a)),this.noCloseButton||i.push(e(ll,{staticClass:"ml-auto mb-1",on:{click:function(){t.hide()}}}));var r=e();i.length>0&&(r=e(this.headerTag,{staticClass:"toast-header",class:this.headerClass},i));var c=e(s?EL:"div",{staticClass:"toast-body",class:this.bodyClass,props:s?$c(T3,this):{},on:s?{click:this.onLinkClick}:{}},this.normalizeSlot(wn,o));return e("div",{staticClass:"toast",class:this.toastClass,attrs:this.computedAttrs,key:"toast-".concat(this[Rs]),ref:"toast"},[r,c])}},render:function(e){if(!this.doRender||!this.isMounted)return e();var t=this.order,a=this.static,o=this.isHiding,s=this.isStatus,i="b-toast-".concat(this[Rs]),n=e("div",{staticClass:"b-toast",class:this.toastClasses,attrs:z3(z3({},a?{}:this.scopedStyleAttrs),{},{id:this.safeId("_toast_outer"),role:o?null:s?"status":"alert","aria-live":o?null:s?"polite":"assertive","aria-atomic":o?null:"true"}),key:i,ref:"b-toast"},[e(vl,{props:{noFade:this.noFade},on:this.transitionHandlers},[this.localShow?this.makeToast(e):e()])]);return e(P3["Portal"],{props:{name:i,to:this.computedToaster,order:t,slim:!0,disabled:a}},[n])}});function B3(e,t){if(!(e instanceof t))throw new TypeError("Cannot call a class as a function")}function L3(e,t){for(var a=0;ae.length)&&(t=e.length);for(var a=0,o=new Array(t);a1&&void 0!==arguments[1]?arguments[1]:{};e&&!Dt(q3)&&a(U3(U3({},Y3(t)),{},{toastContent:e}),this._vm)}},{key:"show",value:function(e){e&&this._root.$emit(nl(Zo,_i),e)}},{key:"hide",value:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:null;this._root.$emit(nl(Zo,ni),e)}}]),e}();e.mixin({beforeCreate:function(){this[J3]=new o(this)}}),ot(e.prototype,q3)||et(e.prototype,q3,{get:function(){return this&&this[J3]||Ct('"'.concat(q3,'" must be accessed from a Vue instance "this" context.'),Zo),this[J3]}})},Z3=Ft({plugins:{plugin:X3}}),e4=Ft({components:{BToast:x3,BToaster:w3},plugins:{BVToastPlugin:Z3}});function t4(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function a4(e){for(var t=1;t=a){var o=this.$targets[this.$targets.length-1];this.$activeTarget!==o&&this.activate(o)}else{if(this.$activeTarget&&e0)return this.$activeTarget=null,void this.clear();for(var s=this.$offsets.length;s--;){var i=this.$activeTarget!==this.$targets[s]&&e>=this.$offsets[s]&&(Te(this.$offsets[s+1])||e0&&this.$root&&this.$root.$emit(G4,e,a)}},{key:"clear",value:function(){var e=this;nc("".concat(this.$selector,", ").concat(E4),this.$el).filter((function(e){return uc(e,B4)})).forEach((function(t){return e.setActiveState(t,!1)}))}},{key:"setActiveState",value:function(e,t){e&&(t?mc(e,B4):pc(e,B4))}}],[{key:"Name",get:function(){return V4}},{key:"Default",get:function(){return $4}},{key:"DefaultType",get:function(){return q4}}]),e}(),X4="__BV_Scrollspy__",Z4=/^\d+$/,e8=/^(auto|position|offset)$/,t8=function(e){var t={};return e.arg&&(t.element="#".concat(e.arg)),at(e.modifiers).forEach((function(e){Z4.test(e)?t.offset=Vr(e,0):e8.test(e)&&(t.method=e)})),Oe(e.value)?t.element=e.value:Ee(e.value)?t.offset=Ol(e.value):He(e.value)&&at(e.value).filter((function(e){return!!Y4.DefaultType[e]})).forEach((function(a){t[a]=e.value[a]})),t},a8=function(e,t,a){if(I){var o=t8(t);e[X4]?e[X4].updateConfig(o,gL(YF(a,t))):e[X4]=new Y4(e,o,gL(YF(a,t)))}},o8=function(e){e[X4]&&(e[X4].dispose(),e[X4]=null,delete e[X4])},s8={bind:function(e,t,a){a8(e,t,a)},inserted:function(e,t,a){a8(e,t,a)},update:function(e,t,a){t.value!==t.oldValue&&a8(e,t,a)},componentUpdated:function(e,t,a){t.value!==t.oldValue&&a8(e,t,a)},unbind:function(e){o8(e)}},i8=Ft({directives:{VBScrollspy:s8}}),n8=Ft({directives:{VBVisible:MU}}),r8=Ft({plugins:{VBHoverPlugin:C4,VBModalPlugin:D4,VBPopoverPlugin:EZ,VBScrollspyPlugin:i8,VBTogglePlugin:RH,VBTooltipPlugin:w4,VBVisiblePlugin:n8}}),c8="BootstrapVue",l8=Et({plugins:{componentsPlugin:z4,directivesPlugin:r8}}),h8={install:l8,NAME:c8},d8=Jc(rt(lh,["content","stacked"]),eo),m8=Ms({name:eo,functional:!0,props:d8,render:function(e,t){var a=t.data,o=t.props,s=t.children;return e(hh,bs(a,{staticClass:"b-iconstack",props:o}),s)}}),p8=Ht({components:{BIcon:WB,BIconstack:m8,BIconBlank:gh,BIconAlarm:vh,BIconAlarmFill:Ah,BIconAlignBottom:Ph,BIconAlignCenter:bh,BIconAlignEnd:yh,BIconAlignMiddle:wh,BIconAlignStart:Ih,BIconAlignTop:zh,BIconAlt:Ch,BIconApp:Dh,BIconAppIndicator:Rh,BIconArchive:Sh,BIconArchiveFill:_h,BIconArrow90degDown:kh,BIconArrow90degLeft:Mh,BIconArrow90degRight:Th,BIconArrow90degUp:Vh,BIconArrowBarDown:xh,BIconArrowBarLeft:Bh,BIconArrowBarRight:Lh,BIconArrowBarUp:Oh,BIconArrowClockwise:Eh,BIconArrowCounterclockwise:Uh,BIconArrowDown:Fh,BIconArrowDownCircle:Hh,BIconArrowDownCircleFill:jh,BIconArrowDownLeft:Gh,BIconArrowDownLeftCircle:Wh,BIconArrowDownLeftCircleFill:Nh,BIconArrowDownLeftSquare:$h,BIconArrowDownLeftSquareFill:qh,BIconArrowDownRight:Jh,BIconArrowDownRightCircle:Kh,BIconArrowDownRightCircleFill:Qh,BIconArrowDownRightSquare:Yh,BIconArrowDownRightSquareFill:Xh,BIconArrowDownShort:Zh,BIconArrowDownSquare:ed,BIconArrowDownSquareFill:td,BIconArrowDownUp:ad,BIconArrowLeft:od,BIconArrowLeftCircle:sd,BIconArrowLeftCircleFill:id,BIconArrowLeftRight:nd,BIconArrowLeftShort:rd,BIconArrowLeftSquare:cd,BIconArrowLeftSquareFill:ld,BIconArrowRepeat:hd,BIconArrowReturnLeft:dd,BIconArrowReturnRight:md,BIconArrowRight:pd,BIconArrowRightCircle:ud,BIconArrowRightCircleFill:fd,BIconArrowRightShort:gd,BIconArrowRightSquare:vd,BIconArrowRightSquareFill:Ad,BIconArrowUp:Pd,BIconArrowUpCircle:bd,BIconArrowUpCircleFill:yd,BIconArrowUpLeft:wd,BIconArrowUpLeftCircle:Id,BIconArrowUpLeftCircleFill:zd,BIconArrowUpLeftSquare:Cd,BIconArrowUpLeftSquareFill:Dd,BIconArrowUpRight:Rd,BIconArrowUpRightCircle:Sd,BIconArrowUpRightCircleFill:_d,BIconArrowUpRightSquare:kd,BIconArrowUpRightSquareFill:Md,BIconArrowUpShort:Td,BIconArrowUpSquare:Vd,BIconArrowUpSquareFill:xd,BIconArrowsAngleContract:Bd,BIconArrowsAngleExpand:Ld,BIconArrowsCollapse:Od,BIconArrowsExpand:Ed,BIconArrowsFullscreen:Ud,BIconArrowsMove:Fd,BIconAspectRatio:Hd,BIconAspectRatioFill:jd,BIconAsterisk:Gd,BIconAt:Wd,BIconAward:Nd,BIconAwardFill:$d,BIconBack:qd,BIconBackspace:Jd,BIconBackspaceFill:Kd,BIconBackspaceReverse:Qd,BIconBackspaceReverseFill:Yd,BIconBadge3d:Xd,BIconBadge3dFill:Zd,BIconBadge4k:em,BIconBadge4kFill:tm,BIconBadge8k:am,BIconBadge8kFill:om,BIconBadgeAd:sm,BIconBadgeAdFill:im,BIconBadgeAr:nm,BIconBadgeArFill:rm,BIconBadgeCc:cm,BIconBadgeCcFill:lm,BIconBadgeHd:hm,BIconBadgeHdFill:dm,BIconBadgeTm:mm,BIconBadgeTmFill:pm,BIconBadgeVo:um,BIconBadgeVoFill:fm,BIconBadgeVr:gm,BIconBadgeVrFill:vm,BIconBadgeWc:Am,BIconBadgeWcFill:Pm,BIconBag:bm,BIconBagCheck:ym,BIconBagCheckFill:wm,BIconBagDash:Im,BIconBagDashFill:zm,BIconBagFill:Cm,BIconBagPlus:Dm,BIconBagPlusFill:Rm,BIconBagX:Sm,BIconBagXFill:_m,BIconBank:km,BIconBank2:Mm,BIconBarChart:Tm,BIconBarChartFill:Vm,BIconBarChartLine:xm,BIconBarChartLineFill:Bm,BIconBarChartSteps:Lm,BIconBasket:Om,BIconBasket2:Em,BIconBasket2Fill:Um,BIconBasket3:Fm,BIconBasket3Fill:Hm,BIconBasketFill:jm,BIconBattery:Gm,BIconBatteryCharging:Wm,BIconBatteryFull:Nm,BIconBatteryHalf:$m,BIconBell:qm,BIconBellFill:Jm,BIconBellSlash:Km,BIconBellSlashFill:Qm,BIconBezier:Ym,BIconBezier2:Xm,BIconBicycle:Zm,BIconBinoculars:ep,BIconBinocularsFill:tp,BIconBlockquoteLeft:ap,BIconBlockquoteRight:op,BIconBook:sp,BIconBookFill:ip,BIconBookHalf:np,BIconBookmark:rp,BIconBookmarkCheck:cp,BIconBookmarkCheckFill:lp,BIconBookmarkDash:hp,BIconBookmarkDashFill:dp,BIconBookmarkFill:mp,BIconBookmarkHeart:pp,BIconBookmarkHeartFill:up,BIconBookmarkPlus:fp,BIconBookmarkPlusFill:gp,BIconBookmarkStar:vp,BIconBookmarkStarFill:Ap,BIconBookmarkX:Pp,BIconBookmarkXFill:bp,BIconBookmarks:yp,BIconBookmarksFill:wp,BIconBookshelf:Ip,BIconBootstrap:zp,BIconBootstrapFill:Cp,BIconBootstrapReboot:Dp,BIconBorder:Rp,BIconBorderAll:Sp,BIconBorderBottom:_p,BIconBorderCenter:kp,BIconBorderInner:Mp,BIconBorderLeft:Tp,BIconBorderMiddle:Vp,BIconBorderOuter:xp,BIconBorderRight:Bp,BIconBorderStyle:Lp,BIconBorderTop:Op,BIconBorderWidth:Ep,BIconBoundingBox:Up,BIconBoundingBoxCircles:Fp,BIconBox:Hp,BIconBoxArrowDown:jp,BIconBoxArrowDownLeft:Gp,BIconBoxArrowDownRight:Wp,BIconBoxArrowInDown:Np,BIconBoxArrowInDownLeft:$p,BIconBoxArrowInDownRight:qp,BIconBoxArrowInLeft:Jp,BIconBoxArrowInRight:Kp,BIconBoxArrowInUp:Qp,BIconBoxArrowInUpLeft:Yp,BIconBoxArrowInUpRight:Xp,BIconBoxArrowLeft:Zp,BIconBoxArrowRight:eu,BIconBoxArrowUp:tu,BIconBoxArrowUpLeft:au,BIconBoxArrowUpRight:ou,BIconBoxSeam:su,BIconBraces:iu,BIconBricks:nu,BIconBriefcase:ru,BIconBriefcaseFill:cu,BIconBrightnessAltHigh:lu,BIconBrightnessAltHighFill:hu,BIconBrightnessAltLow:du,BIconBrightnessAltLowFill:mu,BIconBrightnessHigh:pu,BIconBrightnessHighFill:uu,BIconBrightnessLow:fu,BIconBrightnessLowFill:gu,BIconBroadcast:vu,BIconBroadcastPin:Au,BIconBrush:Pu,BIconBrushFill:bu,BIconBucket:yu,BIconBucketFill:wu,BIconBug:Iu,BIconBugFill:zu,BIconBuilding:Cu,BIconBullseye:Du,BIconCalculator:Ru,BIconCalculatorFill:Su,BIconCalendar:_u,BIconCalendar2:ku,BIconCalendar2Check:Mu,BIconCalendar2CheckFill:Tu,BIconCalendar2Date:Vu,BIconCalendar2DateFill:xu,BIconCalendar2Day:Bu,BIconCalendar2DayFill:Lu,BIconCalendar2Event:Ou,BIconCalendar2EventFill:Eu,BIconCalendar2Fill:Uu,BIconCalendar2Minus:Fu,BIconCalendar2MinusFill:Hu,BIconCalendar2Month:ju,BIconCalendar2MonthFill:Gu,BIconCalendar2Plus:Wu,BIconCalendar2PlusFill:Nu,BIconCalendar2Range:$u,BIconCalendar2RangeFill:qu,BIconCalendar2Week:Ju,BIconCalendar2WeekFill:Ku,BIconCalendar2X:Qu,BIconCalendar2XFill:Yu,BIconCalendar3:Xu,BIconCalendar3Event:Zu,BIconCalendar3EventFill:ef,BIconCalendar3Fill:tf,BIconCalendar3Range:af,BIconCalendar3RangeFill:of,BIconCalendar3Week:sf,BIconCalendar3WeekFill:nf,BIconCalendar4:rf,BIconCalendar4Event:cf,BIconCalendar4Range:lf,BIconCalendar4Week:hf,BIconCalendarCheck:df,BIconCalendarCheckFill:mf,BIconCalendarDate:pf,BIconCalendarDateFill:uf,BIconCalendarDay:ff,BIconCalendarDayFill:gf,BIconCalendarEvent:vf,BIconCalendarEventFill:Af,BIconCalendarFill:Pf,BIconCalendarMinus:bf,BIconCalendarMinusFill:yf,BIconCalendarMonth:wf,BIconCalendarMonthFill:If,BIconCalendarPlus:zf,BIconCalendarPlusFill:Cf,BIconCalendarRange:Df,BIconCalendarRangeFill:Rf,BIconCalendarWeek:Sf,BIconCalendarWeekFill:_f,BIconCalendarX:kf,BIconCalendarXFill:Mf,BIconCamera:Tf,BIconCamera2:Vf,BIconCameraFill:xf,BIconCameraReels:Bf,BIconCameraReelsFill:Lf,BIconCameraVideo:Of,BIconCameraVideoFill:Ef,BIconCameraVideoOff:Uf,BIconCameraVideoOffFill:Ff,BIconCapslock:Hf,BIconCapslockFill:jf,BIconCardChecklist:Gf,BIconCardHeading:Wf,BIconCardImage:Nf,BIconCardList:$f,BIconCardText:qf,BIconCaretDown:Jf,BIconCaretDownFill:Kf,BIconCaretDownSquare:Qf,BIconCaretDownSquareFill:Yf,BIconCaretLeft:Xf,BIconCaretLeftFill:Zf,BIconCaretLeftSquare:eg,BIconCaretLeftSquareFill:tg,BIconCaretRight:ag,BIconCaretRightFill:og,BIconCaretRightSquare:sg,BIconCaretRightSquareFill:ig,BIconCaretUp:ng,BIconCaretUpFill:rg,BIconCaretUpSquare:cg,BIconCaretUpSquareFill:lg,BIconCart:hg,BIconCart2:dg,BIconCart3:mg,BIconCart4:pg,BIconCartCheck:ug,BIconCartCheckFill:fg,BIconCartDash:gg,BIconCartDashFill:vg,BIconCartFill:Ag,BIconCartPlus:Pg,BIconCartPlusFill:bg,BIconCartX:yg,BIconCartXFill:wg,BIconCash:Ig,BIconCashCoin:zg,BIconCashStack:Cg,BIconCast:Dg,BIconChat:Rg,BIconChatDots:Sg,BIconChatDotsFill:_g,BIconChatFill:kg,BIconChatLeft:Mg,BIconChatLeftDots:Tg,BIconChatLeftDotsFill:Vg,BIconChatLeftFill:xg,BIconChatLeftQuote:Bg,BIconChatLeftQuoteFill:Lg,BIconChatLeftText:Og,BIconChatLeftTextFill:Eg,BIconChatQuote:Ug,BIconChatQuoteFill:Fg,BIconChatRight:Hg,BIconChatRightDots:jg,BIconChatRightDotsFill:Gg,BIconChatRightFill:Wg,BIconChatRightQuote:Ng,BIconChatRightQuoteFill:$g,BIconChatRightText:qg,BIconChatRightTextFill:Jg,BIconChatSquare:Kg,BIconChatSquareDots:Qg,BIconChatSquareDotsFill:Yg,BIconChatSquareFill:Xg,BIconChatSquareQuote:Zg,BIconChatSquareQuoteFill:ev,BIconChatSquareText:tv,BIconChatSquareTextFill:av,BIconChatText:ov,BIconChatTextFill:sv,BIconCheck:iv,BIconCheck2:nv,BIconCheck2All:rv,BIconCheck2Circle:cv,BIconCheck2Square:lv,BIconCheckAll:hv,BIconCheckCircle:dv,BIconCheckCircleFill:mv,BIconCheckLg:pv,BIconCheckSquare:uv,BIconCheckSquareFill:fv,BIconChevronBarContract:gv,BIconChevronBarDown:vv,BIconChevronBarExpand:Av,BIconChevronBarLeft:Pv,BIconChevronBarRight:bv,BIconChevronBarUp:yv,BIconChevronCompactDown:wv,BIconChevronCompactLeft:Iv,BIconChevronCompactRight:zv,BIconChevronCompactUp:Cv,BIconChevronContract:Dv,BIconChevronDoubleDown:Rv,BIconChevronDoubleLeft:Sv,BIconChevronDoubleRight:_v,BIconChevronDoubleUp:kv,BIconChevronDown:Mv,BIconChevronExpand:Tv,BIconChevronLeft:Vv,BIconChevronRight:xv,BIconChevronUp:Bv,BIconCircle:Lv,BIconCircleFill:Ov,BIconCircleHalf:Ev,BIconCircleSquare:Uv,BIconClipboard:Fv,BIconClipboardCheck:Hv,BIconClipboardData:jv,BIconClipboardMinus:Gv,BIconClipboardPlus:Wv,BIconClipboardX:Nv,BIconClock:$v,BIconClockFill:qv,BIconClockHistory:Jv,BIconCloud:Kv,BIconCloudArrowDown:Qv,BIconCloudArrowDownFill:Yv,BIconCloudArrowUp:Xv,BIconCloudArrowUpFill:Zv,BIconCloudCheck:eA,BIconCloudCheckFill:tA,BIconCloudDownload:aA,BIconCloudDownloadFill:oA,BIconCloudDrizzle:sA,BIconCloudDrizzleFill:iA,BIconCloudFill:nA,BIconCloudFog:rA,BIconCloudFog2:cA,BIconCloudFog2Fill:lA,BIconCloudFogFill:hA,BIconCloudHail:dA,BIconCloudHailFill:mA,BIconCloudHaze:pA,BIconCloudHaze1:uA,BIconCloudHaze2Fill:fA,BIconCloudHazeFill:gA,BIconCloudLightning:vA,BIconCloudLightningFill:AA,BIconCloudLightningRain:PA,BIconCloudLightningRainFill:bA,BIconCloudMinus:yA,BIconCloudMinusFill:wA,BIconCloudMoon:IA,BIconCloudMoonFill:zA,BIconCloudPlus:CA,BIconCloudPlusFill:DA,BIconCloudRain:RA,BIconCloudRainFill:SA,BIconCloudRainHeavy:_A,BIconCloudRainHeavyFill:kA,BIconCloudSlash:MA,BIconCloudSlashFill:TA,BIconCloudSleet:VA,BIconCloudSleetFill:xA,BIconCloudSnow:BA,BIconCloudSnowFill:LA,BIconCloudSun:OA,BIconCloudSunFill:EA,BIconCloudUpload:UA,BIconCloudUploadFill:FA,BIconClouds:HA,BIconCloudsFill:jA,BIconCloudy:GA,BIconCloudyFill:WA,BIconCode:NA,BIconCodeSlash:$A,BIconCodeSquare:qA,BIconCoin:JA,BIconCollection:KA,BIconCollectionFill:QA,BIconCollectionPlay:YA,BIconCollectionPlayFill:XA,BIconColumns:ZA,BIconColumnsGap:eP,BIconCommand:tP,BIconCompass:aP,BIconCompassFill:oP,BIconCone:sP,BIconConeStriped:iP,BIconController:nP,BIconCpu:rP,BIconCpuFill:cP,BIconCreditCard:lP,BIconCreditCard2Back:hP,BIconCreditCard2BackFill:dP,BIconCreditCard2Front:mP,BIconCreditCard2FrontFill:pP,BIconCreditCardFill:uP,BIconCrop:fP,BIconCup:gP,BIconCupFill:vP,BIconCupStraw:AP,BIconCurrencyBitcoin:PP,BIconCurrencyDollar:bP,BIconCurrencyEuro:yP,BIconCurrencyExchange:wP,BIconCurrencyPound:IP,BIconCurrencyYen:zP,BIconCursor:CP,BIconCursorFill:DP,BIconCursorText:RP,BIconDash:SP,BIconDashCircle:_P,BIconDashCircleDotted:kP,BIconDashCircleFill:MP,BIconDashLg:TP,BIconDashSquare:VP,BIconDashSquareDotted:xP,BIconDashSquareFill:BP,BIconDiagram2:LP,BIconDiagram2Fill:OP,BIconDiagram3:EP,BIconDiagram3Fill:UP,BIconDiamond:FP,BIconDiamondFill:HP,BIconDiamondHalf:jP,BIconDice1:GP,BIconDice1Fill:WP,BIconDice2:NP,BIconDice2Fill:$P,BIconDice3:qP,BIconDice3Fill:JP,BIconDice4:KP,BIconDice4Fill:QP,BIconDice5:YP,BIconDice5Fill:XP,BIconDice6:ZP,BIconDice6Fill:eb,BIconDisc:tb,BIconDiscFill:ab,BIconDiscord:ob,BIconDisplay:sb,BIconDisplayFill:ib,BIconDistributeHorizontal:nb,BIconDistributeVertical:rb,BIconDoorClosed:cb,BIconDoorClosedFill:lb,BIconDoorOpen:hb,BIconDoorOpenFill:db,BIconDot:mb,BIconDownload:pb,BIconDroplet:ub,BIconDropletFill:fb,BIconDropletHalf:gb,BIconEarbuds:vb,BIconEasel:Ab,BIconEaselFill:Pb,BIconEgg:bb,BIconEggFill:yb,BIconEggFried:wb,BIconEject:Ib,BIconEjectFill:zb,BIconEmojiAngry:Cb,BIconEmojiAngryFill:Db,BIconEmojiDizzy:Rb,BIconEmojiDizzyFill:Sb,BIconEmojiExpressionless:_b,BIconEmojiExpressionlessFill:kb,BIconEmojiFrown:Mb,BIconEmojiFrownFill:Tb,BIconEmojiHeartEyes:Vb,BIconEmojiHeartEyesFill:xb,BIconEmojiLaughing:Bb,BIconEmojiLaughingFill:Lb,BIconEmojiNeutral:Ob,BIconEmojiNeutralFill:Eb,BIconEmojiSmile:Ub,BIconEmojiSmileFill:Fb,BIconEmojiSmileUpsideDown:Hb,BIconEmojiSmileUpsideDownFill:jb,BIconEmojiSunglasses:Gb,BIconEmojiSunglassesFill:Wb,BIconEmojiWink:Nb,BIconEmojiWinkFill:$b,BIconEnvelope:qb,BIconEnvelopeFill:Jb,BIconEnvelopeOpen:Kb,BIconEnvelopeOpenFill:Qb,BIconEraser:Yb,BIconEraserFill:Xb,BIconExclamation:Zb,BIconExclamationCircle:ey,BIconExclamationCircleFill:ty,BIconExclamationDiamond:ay,BIconExclamationDiamondFill:oy,BIconExclamationLg:sy,BIconExclamationOctagon:iy,BIconExclamationOctagonFill:ny,BIconExclamationSquare:ry,BIconExclamationSquareFill:cy,BIconExclamationTriangle:ly,BIconExclamationTriangleFill:hy,BIconExclude:dy,BIconEye:my,BIconEyeFill:py,BIconEyeSlash:uy,BIconEyeSlashFill:fy,BIconEyedropper:gy,BIconEyeglasses:vy,BIconFacebook:Ay,BIconFile:Py,BIconFileArrowDown:by,BIconFileArrowDownFill:yy,BIconFileArrowUp:wy,BIconFileArrowUpFill:Iy,BIconFileBarGraph:zy,BIconFileBarGraphFill:Cy,BIconFileBinary:Dy,BIconFileBinaryFill:Ry,BIconFileBreak:Sy,BIconFileBreakFill:_y,BIconFileCheck:ky,BIconFileCheckFill:My,BIconFileCode:Ty,BIconFileCodeFill:Vy,BIconFileDiff:xy,BIconFileDiffFill:By,BIconFileEarmark:Ly,BIconFileEarmarkArrowDown:Oy,BIconFileEarmarkArrowDownFill:Ey,BIconFileEarmarkArrowUp:Uy,BIconFileEarmarkArrowUpFill:Fy,BIconFileEarmarkBarGraph:Hy,BIconFileEarmarkBarGraphFill:jy,BIconFileEarmarkBinary:Gy,BIconFileEarmarkBinaryFill:Wy,BIconFileEarmarkBreak:Ny,BIconFileEarmarkBreakFill:$y,BIconFileEarmarkCheck:qy,BIconFileEarmarkCheckFill:Jy,BIconFileEarmarkCode:Ky,BIconFileEarmarkCodeFill:Qy,BIconFileEarmarkDiff:Yy,BIconFileEarmarkDiffFill:Xy,BIconFileEarmarkEasel:Zy,BIconFileEarmarkEaselFill:ew,BIconFileEarmarkExcel:tw,BIconFileEarmarkExcelFill:aw,BIconFileEarmarkFill:ow,BIconFileEarmarkFont:sw,BIconFileEarmarkFontFill:iw,BIconFileEarmarkImage:nw,BIconFileEarmarkImageFill:rw,BIconFileEarmarkLock:cw,BIconFileEarmarkLock2:lw,BIconFileEarmarkLock2Fill:hw,BIconFileEarmarkLockFill:dw,BIconFileEarmarkMedical:mw,BIconFileEarmarkMedicalFill:pw,BIconFileEarmarkMinus:uw,BIconFileEarmarkMinusFill:fw,BIconFileEarmarkMusic:gw,BIconFileEarmarkMusicFill:vw,BIconFileEarmarkPdf:Aw,BIconFileEarmarkPdfFill:Pw,BIconFileEarmarkPerson:bw,BIconFileEarmarkPersonFill:yw,BIconFileEarmarkPlay:ww,BIconFileEarmarkPlayFill:Iw,BIconFileEarmarkPlus:zw,BIconFileEarmarkPlusFill:Cw,BIconFileEarmarkPost:Dw,BIconFileEarmarkPostFill:Rw,BIconFileEarmarkPpt:Sw,BIconFileEarmarkPptFill:_w,BIconFileEarmarkRichtext:kw,BIconFileEarmarkRichtextFill:Mw,BIconFileEarmarkRuled:Tw,BIconFileEarmarkRuledFill:Vw,BIconFileEarmarkSlides:xw,BIconFileEarmarkSlidesFill:Bw,BIconFileEarmarkSpreadsheet:Lw,BIconFileEarmarkSpreadsheetFill:Ow,BIconFileEarmarkText:Ew,BIconFileEarmarkTextFill:Uw,BIconFileEarmarkWord:Fw,BIconFileEarmarkWordFill:Hw,BIconFileEarmarkX:jw,BIconFileEarmarkXFill:Gw,BIconFileEarmarkZip:Ww,BIconFileEarmarkZipFill:Nw,BIconFileEasel:$w,BIconFileEaselFill:qw,BIconFileExcel:Jw,BIconFileExcelFill:Kw,BIconFileFill:Qw,BIconFileFont:Yw,BIconFileFontFill:Xw,BIconFileImage:Zw,BIconFileImageFill:eI,BIconFileLock:tI,BIconFileLock2:aI,BIconFileLock2Fill:oI,BIconFileLockFill:sI,BIconFileMedical:iI,BIconFileMedicalFill:nI,BIconFileMinus:rI,BIconFileMinusFill:cI,BIconFileMusic:lI,BIconFileMusicFill:hI,BIconFilePdf:dI,BIconFilePdfFill:mI,BIconFilePerson:pI,BIconFilePersonFill:uI,BIconFilePlay:fI,BIconFilePlayFill:gI,BIconFilePlus:vI,BIconFilePlusFill:AI,BIconFilePost:PI,BIconFilePostFill:bI,BIconFilePpt:yI,BIconFilePptFill:wI,BIconFileRichtext:II,BIconFileRichtextFill:zI,BIconFileRuled:CI,BIconFileRuledFill:DI,BIconFileSlides:RI,BIconFileSlidesFill:SI,BIconFileSpreadsheet:_I,BIconFileSpreadsheetFill:kI,BIconFileText:MI,BIconFileTextFill:TI,BIconFileWord:VI,BIconFileWordFill:xI,BIconFileX:BI,BIconFileXFill:LI,BIconFileZip:OI,BIconFileZipFill:EI,BIconFiles:UI,BIconFilesAlt:FI,BIconFilm:HI,BIconFilter:jI,BIconFilterCircle:GI,BIconFilterCircleFill:WI,BIconFilterLeft:NI,BIconFilterRight:$I,BIconFilterSquare:qI,BIconFilterSquareFill:JI,BIconFlag:KI,BIconFlagFill:QI,BIconFlower1:YI,BIconFlower2:XI,BIconFlower3:ZI,BIconFolder:ez,BIconFolder2:tz,BIconFolder2Open:az,BIconFolderCheck:oz,BIconFolderFill:sz,BIconFolderMinus:iz,BIconFolderPlus:nz,BIconFolderSymlink:rz,BIconFolderSymlinkFill:cz,BIconFolderX:lz,BIconFonts:hz,BIconForward:dz,BIconForwardFill:mz,BIconFront:pz,BIconFullscreen:uz,BIconFullscreenExit:fz,BIconFunnel:gz,BIconFunnelFill:vz,BIconGear:Az,BIconGearFill:Pz,BIconGearWide:bz,BIconGearWideConnected:yz,BIconGem:wz,BIconGenderAmbiguous:Iz,BIconGenderFemale:zz,BIconGenderMale:Cz,BIconGenderTrans:Dz,BIconGeo:Rz,BIconGeoAlt:Sz,BIconGeoAltFill:_z,BIconGeoFill:kz,BIconGift:Mz,BIconGiftFill:Tz,BIconGithub:Vz,BIconGlobe:xz,BIconGlobe2:Bz,BIconGoogle:Lz,BIconGraphDown:Oz,BIconGraphUp:Ez,BIconGrid:Uz,BIconGrid1x2:Fz,BIconGrid1x2Fill:Hz,BIconGrid3x2:jz,BIconGrid3x2Gap:Gz,BIconGrid3x2GapFill:Wz,BIconGrid3x3:Nz,BIconGrid3x3Gap:$z,BIconGrid3x3GapFill:qz,BIconGridFill:Jz,BIconGripHorizontal:Kz,BIconGripVertical:Qz,BIconHammer:Yz,BIconHandIndex:Xz,BIconHandIndexFill:Zz,BIconHandIndexThumb:eC,BIconHandIndexThumbFill:tC,BIconHandThumbsDown:aC,BIconHandThumbsDownFill:oC,BIconHandThumbsUp:sC,BIconHandThumbsUpFill:iC,BIconHandbag:nC,BIconHandbagFill:rC,BIconHash:cC,BIconHdd:lC,BIconHddFill:hC,BIconHddNetwork:dC,BIconHddNetworkFill:mC,BIconHddRack:pC,BIconHddRackFill:uC,BIconHddStack:fC,BIconHddStackFill:gC,BIconHeadphones:vC,BIconHeadset:AC,BIconHeadsetVr:PC,BIconHeart:bC,BIconHeartFill:yC,BIconHeartHalf:wC,BIconHeptagon:IC,BIconHeptagonFill:zC,BIconHeptagonHalf:CC,BIconHexagon:DC,BIconHexagonFill:RC,BIconHexagonHalf:SC,BIconHourglass:_C,BIconHourglassBottom:kC,BIconHourglassSplit:MC,BIconHourglassTop:TC,BIconHouse:VC,BIconHouseDoor:xC,BIconHouseDoorFill:BC,BIconHouseFill:LC,BIconHr:OC,BIconHurricane:EC,BIconImage:UC,BIconImageAlt:FC,BIconImageFill:HC,BIconImages:jC,BIconInbox:GC,BIconInboxFill:WC,BIconInboxes:NC,BIconInboxesFill:$C,BIconInfo:qC,BIconInfoCircle:JC,BIconInfoCircleFill:KC,BIconInfoLg:QC,BIconInfoSquare:YC,BIconInfoSquareFill:XC,BIconInputCursor:ZC,BIconInputCursorText:eD,BIconInstagram:tD,BIconIntersect:aD,BIconJournal:oD,BIconJournalAlbum:sD,BIconJournalArrowDown:iD,BIconJournalArrowUp:nD,BIconJournalBookmark:rD,BIconJournalBookmarkFill:cD,BIconJournalCheck:lD,BIconJournalCode:hD,BIconJournalMedical:dD,BIconJournalMinus:mD,BIconJournalPlus:pD,BIconJournalRichtext:uD,BIconJournalText:fD,BIconJournalX:gD,BIconJournals:vD,BIconJoystick:AD,BIconJustify:PD,BIconJustifyLeft:bD,BIconJustifyRight:yD,BIconKanban:wD,BIconKanbanFill:ID,BIconKey:zD,BIconKeyFill:CD,BIconKeyboard:DD,BIconKeyboardFill:RD,BIconLadder:SD,BIconLamp:_D,BIconLampFill:kD,BIconLaptop:MD,BIconLaptopFill:TD,BIconLayerBackward:VD,BIconLayerForward:xD,BIconLayers:BD,BIconLayersFill:LD,BIconLayersHalf:OD,BIconLayoutSidebar:ED,BIconLayoutSidebarInset:UD,BIconLayoutSidebarInsetReverse:FD,BIconLayoutSidebarReverse:HD,BIconLayoutSplit:jD,BIconLayoutTextSidebar:GD,BIconLayoutTextSidebarReverse:WD,BIconLayoutTextWindow:ND,BIconLayoutTextWindowReverse:$D,BIconLayoutThreeColumns:qD,BIconLayoutWtf:JD,BIconLifePreserver:KD,BIconLightbulb:QD,BIconLightbulbFill:YD,BIconLightbulbOff:XD,BIconLightbulbOffFill:ZD,BIconLightning:eR,BIconLightningCharge:tR,BIconLightningChargeFill:aR,BIconLightningFill:oR,BIconLink:sR,BIconLink45deg:iR,BIconLinkedin:nR,BIconList:rR,BIconListCheck:cR,BIconListNested:lR,BIconListOl:hR,BIconListStars:dR,BIconListTask:mR,BIconListUl:pR,BIconLock:uR,BIconLockFill:fR,BIconMailbox:gR,BIconMailbox2:vR,BIconMap:AR,BIconMapFill:PR,BIconMarkdown:bR,BIconMarkdownFill:yR,BIconMask:wR,BIconMastodon:IR,BIconMegaphone:zR,BIconMegaphoneFill:CR,BIconMenuApp:DR,BIconMenuAppFill:RR,BIconMenuButton:SR,BIconMenuButtonFill:_R,BIconMenuButtonWide:kR,BIconMenuButtonWideFill:MR,BIconMenuDown:TR,BIconMenuUp:VR,BIconMessenger:xR,BIconMic:BR,BIconMicFill:LR,BIconMicMute:OR,BIconMicMuteFill:ER,BIconMinecart:UR,BIconMinecartLoaded:FR,BIconMoisture:HR,BIconMoon:jR,BIconMoonFill:GR,BIconMoonStars:WR,BIconMoonStarsFill:NR,BIconMouse:$R,BIconMouse2:qR,BIconMouse2Fill:JR,BIconMouse3:KR,BIconMouse3Fill:QR,BIconMouseFill:YR,BIconMusicNote:XR,BIconMusicNoteBeamed:ZR,BIconMusicNoteList:eS,BIconMusicPlayer:tS,BIconMusicPlayerFill:aS,BIconNewspaper:oS,BIconNodeMinus:sS,BIconNodeMinusFill:iS,BIconNodePlus:nS,BIconNodePlusFill:rS,BIconNut:cS,BIconNutFill:lS,BIconOctagon:hS,BIconOctagonFill:dS,BIconOctagonHalf:mS,BIconOption:pS,BIconOutlet:uS,BIconPaintBucket:fS,BIconPalette:gS,BIconPalette2:vS,BIconPaletteFill:AS,BIconPaperclip:PS,BIconParagraph:bS,BIconPatchCheck:yS,BIconPatchCheckFill:wS,BIconPatchExclamation:IS,BIconPatchExclamationFill:zS,BIconPatchMinus:CS,BIconPatchMinusFill:DS,BIconPatchPlus:RS,BIconPatchPlusFill:SS,BIconPatchQuestion:_S,BIconPatchQuestionFill:kS,BIconPause:MS,BIconPauseBtn:TS,BIconPauseBtnFill:VS,BIconPauseCircle:xS,BIconPauseCircleFill:BS,BIconPauseFill:LS,BIconPeace:OS,BIconPeaceFill:ES,BIconPen:US,BIconPenFill:FS,BIconPencil:HS,BIconPencilFill:jS,BIconPencilSquare:GS,BIconPentagon:WS,BIconPentagonFill:NS,BIconPentagonHalf:$S,BIconPeople:qS,BIconPeopleFill:JS,BIconPercent:KS,BIconPerson:QS,BIconPersonBadge:YS,BIconPersonBadgeFill:XS,BIconPersonBoundingBox:ZS,BIconPersonCheck:e_,BIconPersonCheckFill:t_,BIconPersonCircle:a_,BIconPersonDash:o_,BIconPersonDashFill:s_,BIconPersonFill:i_,BIconPersonLinesFill:n_,BIconPersonPlus:r_,BIconPersonPlusFill:c_,BIconPersonSquare:l_,BIconPersonX:h_,BIconPersonXFill:d_,BIconPhone:m_,BIconPhoneFill:p_,BIconPhoneLandscape:u_,BIconPhoneLandscapeFill:f_,BIconPhoneVibrate:g_,BIconPhoneVibrateFill:v_,BIconPieChart:A_,BIconPieChartFill:P_,BIconPiggyBank:b_,BIconPiggyBankFill:y_,BIconPin:w_,BIconPinAngle:I_,BIconPinAngleFill:z_,BIconPinFill:C_,BIconPinMap:D_,BIconPinMapFill:R_,BIconPip:S_,BIconPipFill:__,BIconPlay:k_,BIconPlayBtn:M_,BIconPlayBtnFill:T_,BIconPlayCircle:V_,BIconPlayCircleFill:x_,BIconPlayFill:B_,BIconPlug:L_,BIconPlugFill:O_,BIconPlus:E_,BIconPlusCircle:U_,BIconPlusCircleDotted:F_,BIconPlusCircleFill:H_,BIconPlusLg:j_,BIconPlusSquare:G_,BIconPlusSquareDotted:W_,BIconPlusSquareFill:N_,BIconPower:$_,BIconPrinter:q_,BIconPrinterFill:J_,BIconPuzzle:K_,BIconPuzzleFill:Q_,BIconQuestion:Y_,BIconQuestionCircle:X_,BIconQuestionCircleFill:Z_,BIconQuestionDiamond:ek,BIconQuestionDiamondFill:tk,BIconQuestionLg:ak,BIconQuestionOctagon:ok,BIconQuestionOctagonFill:sk,BIconQuestionSquare:ik,BIconQuestionSquareFill:nk,BIconRainbow:rk,BIconReceipt:ck,BIconReceiptCutoff:lk,BIconReception0:hk,BIconReception1:dk,BIconReception2:mk,BIconReception3:pk,BIconReception4:uk,BIconRecord:fk,BIconRecord2:gk,BIconRecord2Fill:vk,BIconRecordBtn:Ak,BIconRecordBtnFill:Pk,BIconRecordCircle:bk,BIconRecordCircleFill:yk,BIconRecordFill:wk,BIconRecycle:Ik,BIconReddit:zk,BIconReply:Ck,BIconReplyAll:Dk,BIconReplyAllFill:Rk,BIconReplyFill:Sk,BIconRss:_k,BIconRssFill:kk,BIconRulers:Mk,BIconSafe:Tk,BIconSafe2:Vk,BIconSafe2Fill:xk,BIconSafeFill:Bk,BIconSave:Lk,BIconSave2:Ok,BIconSave2Fill:Ek,BIconSaveFill:Uk,BIconScissors:Fk,BIconScrewdriver:Hk,BIconSdCard:jk,BIconSdCardFill:Gk,BIconSearch:Wk,BIconSegmentedNav:Nk,BIconServer:$k,BIconShare:qk,BIconShareFill:Jk,BIconShield:Kk,BIconShieldCheck:Qk,BIconShieldExclamation:Yk,BIconShieldFill:Xk,BIconShieldFillCheck:Zk,BIconShieldFillExclamation:eM,BIconShieldFillMinus:tM,BIconShieldFillPlus:aM,BIconShieldFillX:oM,BIconShieldLock:sM,BIconShieldLockFill:iM,BIconShieldMinus:nM,BIconShieldPlus:rM,BIconShieldShaded:cM,BIconShieldSlash:lM,BIconShieldSlashFill:hM,BIconShieldX:dM,BIconShift:mM,BIconShiftFill:pM,BIconShop:uM,BIconShopWindow:fM,BIconShuffle:gM,BIconSignpost:vM,BIconSignpost2:AM,BIconSignpost2Fill:PM,BIconSignpostFill:bM,BIconSignpostSplit:yM,BIconSignpostSplitFill:wM,BIconSim:IM,BIconSimFill:zM,BIconSkipBackward:CM,BIconSkipBackwardBtn:DM,BIconSkipBackwardBtnFill:RM,BIconSkipBackwardCircle:SM,BIconSkipBackwardCircleFill:_M,BIconSkipBackwardFill:kM,BIconSkipEnd:MM,BIconSkipEndBtn:TM,BIconSkipEndBtnFill:VM,BIconSkipEndCircle:xM,BIconSkipEndCircleFill:BM,BIconSkipEndFill:LM,BIconSkipForward:OM,BIconSkipForwardBtn:EM,BIconSkipForwardBtnFill:UM,BIconSkipForwardCircle:FM,BIconSkipForwardCircleFill:HM,BIconSkipForwardFill:jM,BIconSkipStart:GM,BIconSkipStartBtn:WM,BIconSkipStartBtnFill:NM,BIconSkipStartCircle:$M,BIconSkipStartCircleFill:qM,BIconSkipStartFill:JM,BIconSkype:KM,BIconSlack:QM,BIconSlash:YM,BIconSlashCircle:XM,BIconSlashCircleFill:ZM,BIconSlashLg:eT,BIconSlashSquare:tT,BIconSlashSquareFill:aT,BIconSliders:oT,BIconSmartwatch:sT,BIconSnow:iT,BIconSnow2:nT,BIconSnow3:rT,BIconSortAlphaDown:cT,BIconSortAlphaDownAlt:lT,BIconSortAlphaUp:hT,BIconSortAlphaUpAlt:dT,BIconSortDown:mT,BIconSortDownAlt:pT,BIconSortNumericDown:uT,BIconSortNumericDownAlt:fT,BIconSortNumericUp:gT,BIconSortNumericUpAlt:vT,BIconSortUp:AT,BIconSortUpAlt:PT,BIconSoundwave:bT,BIconSpeaker:yT,BIconSpeakerFill:wT,BIconSpeedometer:IT,BIconSpeedometer2:zT,BIconSpellcheck:CT,BIconSquare:DT,BIconSquareFill:RT,BIconSquareHalf:ST,BIconStack:_T,BIconStar:kT,BIconStarFill:MT,BIconStarHalf:TT,BIconStars:VT,BIconStickies:xT,BIconStickiesFill:BT,BIconSticky:LT,BIconStickyFill:OT,BIconStop:ET,BIconStopBtn:UT,BIconStopBtnFill:FT,BIconStopCircle:HT,BIconStopCircleFill:jT,BIconStopFill:GT,BIconStoplights:WT,BIconStoplightsFill:NT,BIconStopwatch:$T,BIconStopwatchFill:qT,BIconSubtract:JT,BIconSuitClub:KT,BIconSuitClubFill:QT,BIconSuitDiamond:YT,BIconSuitDiamondFill:XT,BIconSuitHeart:ZT,BIconSuitHeartFill:eV,BIconSuitSpade:tV,BIconSuitSpadeFill:aV,BIconSun:oV,BIconSunFill:sV,BIconSunglasses:iV,BIconSunrise:nV,BIconSunriseFill:rV,BIconSunset:cV,BIconSunsetFill:lV,BIconSymmetryHorizontal:hV,BIconSymmetryVertical:dV,BIconTable:mV,BIconTablet:pV,BIconTabletFill:uV,BIconTabletLandscape:fV,BIconTabletLandscapeFill:gV,BIconTag:vV,BIconTagFill:AV,BIconTags:PV,BIconTagsFill:bV,BIconTelegram:yV,BIconTelephone:wV,BIconTelephoneFill:IV,BIconTelephoneForward:zV,BIconTelephoneForwardFill:CV,BIconTelephoneInbound:DV,BIconTelephoneInboundFill:RV,BIconTelephoneMinus:SV,BIconTelephoneMinusFill:_V,BIconTelephoneOutbound:kV,BIconTelephoneOutboundFill:MV,BIconTelephonePlus:TV,BIconTelephonePlusFill:VV,BIconTelephoneX:xV,BIconTelephoneXFill:BV,BIconTerminal:LV,BIconTerminalFill:OV,BIconTextCenter:EV,BIconTextIndentLeft:UV,BIconTextIndentRight:FV,BIconTextLeft:HV,BIconTextParagraph:jV,BIconTextRight:GV,BIconTextarea:WV,BIconTextareaResize:NV,BIconTextareaT:$V,BIconThermometer:qV,BIconThermometerHalf:JV,BIconThermometerHigh:KV,BIconThermometerLow:QV,BIconThermometerSnow:YV,BIconThermometerSun:XV,BIconThreeDots:ZV,BIconThreeDotsVertical:ex,BIconToggle2Off:tx,BIconToggle2On:ax,BIconToggleOff:ox,BIconToggleOn:sx,BIconToggles:ix,BIconToggles2:nx,BIconTools:rx,BIconTornado:cx,BIconTranslate:lx,BIconTrash:hx,BIconTrash2:dx,BIconTrash2Fill:mx,BIconTrashFill:px,BIconTree:ux,BIconTreeFill:fx,BIconTriangle:gx,BIconTriangleFill:vx,BIconTriangleHalf:Ax,BIconTrophy:Px,BIconTrophyFill:bx,BIconTropicalStorm:yx,BIconTruck:wx,BIconTruckFlatbed:Ix,BIconTsunami:zx,BIconTv:Cx,BIconTvFill:Dx,BIconTwitch:Rx,BIconTwitter:Sx,BIconType:_x,BIconTypeBold:kx,BIconTypeH1:Mx,BIconTypeH2:Tx,BIconTypeH3:Vx,BIconTypeItalic:xx,BIconTypeStrikethrough:Bx,BIconTypeUnderline:Lx,BIconUiChecks:Ox,BIconUiChecksGrid:Ex,BIconUiRadios:Ux,BIconUiRadiosGrid:Fx,BIconUmbrella:Hx,BIconUmbrellaFill:jx,BIconUnion:Gx,BIconUnlock:Wx,BIconUnlockFill:Nx,BIconUpc:$x,BIconUpcScan:qx,BIconUpload:Jx,BIconVectorPen:Kx,BIconViewList:Qx,BIconViewStacked:Yx,BIconVinyl:Xx,BIconVinylFill:Zx,BIconVoicemail:eB,BIconVolumeDown:tB,BIconVolumeDownFill:aB,BIconVolumeMute:oB,BIconVolumeMuteFill:sB,BIconVolumeOff:iB,BIconVolumeOffFill:nB,BIconVolumeUp:rB,BIconVolumeUpFill:cB,BIconVr:lB,BIconWallet:hB,BIconWallet2:dB,BIconWalletFill:mB,BIconWatch:pB,BIconWater:uB,BIconWhatsapp:fB,BIconWifi:gB,BIconWifi1:vB,BIconWifi2:AB,BIconWifiOff:PB,BIconWind:bB,BIconWindow:yB,BIconWindowDock:wB,BIconWindowSidebar:IB,BIconWrench:zB,BIconX:CB,BIconXCircle:DB,BIconXCircleFill:RB,BIconXDiamond:SB,BIconXDiamondFill:_B,BIconXLg:kB,BIconXOctagon:MB,BIconXOctagonFill:TB,BIconXSquare:VB,BIconXSquareFill:xB,BIconYoutube:BB,BIconZoomIn:LB,BIconZoomOut:OB}});function u8(e,t){for(var a in t)e[a]=t[a];return e}var f8=/[!'()*]/g,g8=function(e){return"%"+e.charCodeAt(0).toString(16)},v8=/%2C/g,A8=function(e){return encodeURIComponent(e).replace(f8,g8).replace(v8,",")};function P8(e){try{return decodeURIComponent(e)}catch(t){0}return e}function b8(e,t,a){void 0===t&&(t={});var o,s=a||w8;try{o=s(e||"")}catch(r){o={}}for(var i in t){var n=t[i];o[i]=Array.isArray(n)?n.map(y8):y8(n)}return o}var y8=function(e){return null==e||"object"===typeof e?e:String(e)};function w8(e){var t={};return e=e.trim().replace(/^(\?|#|&)/,""),e?(e.split("&").forEach((function(e){var a=e.replace(/\+/g," ").split("="),o=P8(a.shift()),s=a.length>0?P8(a.join("=")):null;void 0===t[o]?t[o]=s:Array.isArray(t[o])?t[o].push(s):t[o]=[t[o],s]})),t):t}function I8(e){var t=e?Object.keys(e).map((function(t){var a=e[t];if(void 0===a)return"";if(null===a)return A8(t);if(Array.isArray(a)){var o=[];return a.forEach((function(e){void 0!==e&&(null===e?o.push(A8(t)):o.push(A8(t)+"="+A8(e)))})),o.join("&")}return A8(t)+"="+A8(a)})).filter((function(e){return e.length>0})).join("&"):null;return t?"?"+t:""}var z8=/\/?$/;function C8(e,t,a,o){var s=o&&o.options.stringifyQuery,i=t.query||{};try{i=D8(i)}catch(r){}var n={name:t.name||e&&e.name,meta:e&&e.meta||{},path:t.path||"/",hash:t.hash||"",query:i,params:t.params||{},fullPath:_8(t,s),matched:e?S8(e):[]};return a&&(n.redirectedFrom=_8(a,s)),Object.freeze(n)}function D8(e){if(Array.isArray(e))return e.map(D8);if(e&&"object"===typeof e){var t={};for(var a in e)t[a]=D8(e[a]);return t}return e}var R8=C8(null,{path:"/"});function S8(e){var t=[];while(e)t.unshift(e),e=e.parent;return t}function _8(e,t){var a=e.path,o=e.query;void 0===o&&(o={});var s=e.hash;void 0===s&&(s="");var i=t||I8;return(a||"/")+i(o)+s}function k8(e,t,a){return t===R8?e===t:!!t&&(e.path&&t.path?e.path.replace(z8,"")===t.path.replace(z8,"")&&(a||e.hash===t.hash&&M8(e.query,t.query)):!(!e.name||!t.name)&&(e.name===t.name&&(a||e.hash===t.hash&&M8(e.query,t.query)&&M8(e.params,t.params))))}function M8(e,t){if(void 0===e&&(e={}),void 0===t&&(t={}),!e||!t)return e===t;var a=Object.keys(e).sort(),o=Object.keys(t).sort();return a.length===o.length&&a.every((function(a,s){var i=e[a],n=o[s];if(n!==a)return!1;var r=t[a];return null==i||null==r?i===r:"object"===typeof i&&"object"===typeof r?M8(i,r):String(i)===String(r)}))}function T8(e,t){return 0===e.path.replace(z8,"/").indexOf(t.path.replace(z8,"/"))&&(!t.hash||e.hash===t.hash)&&V8(e.query,t.query)}function V8(e,t){for(var a in t)if(!(a in e))return!1;return!0}function x8(e){for(var t=0;t=0&&(t=e.slice(o),e=e.slice(0,o));var s=e.indexOf("?");return s>=0&&(a=e.slice(s+1),e=e.slice(0,s)),{path:e,query:a,hash:t}}function F8(e){return e.replace(/\/(?:\s*\/)+/g,"/")}var H8=Array.isArray||function(e){return"[object Array]"==Object.prototype.toString.call(e)},j8=r7,G8=J8,W8=K8,N8=X8,$8=n7,q8=new RegExp(["(\\\\.)","([\\/.])?(?:(?:\\:(\\w+)(?:\\(((?:\\\\.|[^\\\\()])+)\\))?|\\(((?:\\\\.|[^\\\\()])+)\\))([+*?])?|(\\*))"].join("|"),"g");function J8(e,t){var a,o=[],s=0,i=0,n="",r=t&&t.delimiter||"/";while(null!=(a=q8.exec(e))){var c=a[0],l=a[1],h=a.index;if(n+=e.slice(i,h),i=h+c.length,l)n+=l[1];else{var d=e[i],m=a[2],p=a[3],u=a[4],f=a[5],g=a[6],v=a[7];n&&(o.push(n),n="");var A=null!=m&&null!=d&&d!==m,P="+"===g||"*"===g,b="?"===g||"*"===g,y=a[2]||r,w=u||f;o.push({name:p||s++,prefix:m||"",delimiter:y,optional:b,repeat:P,partial:A,asterisk:!!v,pattern:w?e7(w):v?".*":"[^"+Z8(y)+"]+?"})}}return i1||!b.length)return 0===b.length?e():e("span",{},b)}if("a"===this.tag)P.on=A,P.attrs={href:r,"aria-current":g};else{var y=v7(this.$slots.default);if(y){y.isStatic=!1;var w=y.data=u8({},y.data);for(var I in w.on=w.on||{},w.on){var z=w.on[I];I in A&&(w.on[I]=Array.isArray(z)?z:[z])}for(var C in A)C in w.on?w.on[C].push(A[C]):w.on[C]=v;var D=y.data.attrs=u8({},y.data.attrs);D.href=r,D["aria-current"]=g}else P.on=A}return e(this.tag,P,this.$slots.default)}};function g7(e){if(!(e.metaKey||e.altKey||e.ctrlKey||e.shiftKey)&&!e.defaultPrevented&&(void 0===e.button||0===e.button)){if(e.currentTarget&&e.currentTarget.getAttribute){var t=e.currentTarget.getAttribute("target");if(/\b_blank\b/i.test(t))return}return e.preventDefault&&e.preventDefault(),!0}}function v7(e){if(e)for(var t,a=0;a-1&&(r.params[d]=a.params[d]);return r.path=l7(l.path,r.params,'named route "'+c+'"'),m(l,r,n)}if(r.path){r.params={};for(var p=0;p-1}function o6(e,t){return a6(e)&&e._isRouter&&(null==t||e.type===t)}function s6(e,t,a){var o=function(s){s>=e.length?a():e[s]?t(e[s],(function(){o(s+1)})):o(s+1)};o(0)}function i6(e){return function(t,a,o){var s=!1,i=0,n=null;n6(e,(function(e,t,a,r){if("function"===typeof e&&void 0===e.cid){s=!0,i++;var c,l=h6((function(t){l6(t)&&(t=t.default),e.resolved="function"===typeof t?t:d7.extend(t),a.components[r]=t,i--,i<=0&&o()})),h=h6((function(e){var t="Failed to resolve async component "+r+": "+e;n||(n=a6(e)?e:new Error(t),o(n))}));try{c=e(l,h)}catch(m){h(m)}if(c)if("function"===typeof c.then)c.then(l,h);else{var d=c.component;d&&"function"===typeof d.then&&d.then(l,h)}}})),s||o()}}function n6(e,t){return r6(e.map((function(e){return Object.keys(e.components).map((function(a){return t(e.components[a],e.instances[a],e,a)}))})))}function r6(e){return Array.prototype.concat.apply([],e)}var c6="function"===typeof Symbol&&"symbol"===typeof Symbol.toStringTag;function l6(e){return e.__esModule||c6&&"Module"===e[Symbol.toStringTag]}function h6(e){var t=!1;return function(){var a=[],o=arguments.length;while(o--)a[o]=arguments[o];if(!t)return t=!0,e.apply(this,a)}}var d6=function(e,t){this.router=e,this.base=m6(t),this.current=R8,this.pending=null,this.ready=!1,this.readyCbs=[],this.readyErrorCbs=[],this.errorCbs=[],this.listeners=[]};function m6(e){if(!e)if(P7){var t=document.querySelector("base");e=t&&t.getAttribute("href")||"/",e=e.replace(/^https?:\/\/[^\/]+/,"")}else e="/";return"/"!==e.charAt(0)&&(e="/"+e),e.replace(/\/$/,"")}function p6(e,t){var a,o=Math.max(e.length,t.length);for(a=0;a0)){var t=this.router,a=t.options.scrollBehavior,o=N7&&a;o&&this.listeners.push(V7());var s=function(){var a=e.current,s=w6(e.base);e.current===R8&&s===e._startLocation||e.transitionTo(s,(function(e){o&&x7(t,e,a,!0)}))};window.addEventListener("popstate",s),this.listeners.push((function(){window.removeEventListener("popstate",s)}))}},t.prototype.go=function(e){window.history.go(e)},t.prototype.push=function(e,t,a){var o=this,s=this,i=s.current;this.transitionTo(e,(function(e){$7(F8(o.base+e.fullPath)),x7(o.router,e,i,!1),t&&t(e)}),a)},t.prototype.replace=function(e,t,a){var o=this,s=this,i=s.current;this.transitionTo(e,(function(e){q7(F8(o.base+e.fullPath)),x7(o.router,e,i,!1),t&&t(e)}),a)},t.prototype.ensureURL=function(e){if(w6(this.base)!==this.current.fullPath){var t=F8(this.base+this.current.fullPath);e?$7(t):q7(t)}},t.prototype.getCurrentLocation=function(){return w6(this.base)},t}(d6);function w6(e){var t=window.location.pathname,a=t.toLowerCase(),o=e.toLowerCase();return!e||a!==o&&0!==a.indexOf(F8(o+"/"))||(t=t.slice(e.length)),(t||"/")+window.location.search+window.location.hash}var I6=function(e){function t(t,a,o){e.call(this,t,a),o&&z6(this.base)||C6()}return e&&(t.__proto__=e),t.prototype=Object.create(e&&e.prototype),t.prototype.constructor=t,t.prototype.setupListeners=function(){var e=this;if(!(this.listeners.length>0)){var t=this.router,a=t.options.scrollBehavior,o=N7&&a;o&&this.listeners.push(V7());var s=function(){var t=e.current;C6()&&e.transitionTo(D6(),(function(a){o&&x7(e.router,a,t,!0),N7||_6(a.fullPath)}))},i=N7?"popstate":"hashchange";window.addEventListener(i,s),this.listeners.push((function(){window.removeEventListener(i,s)}))}},t.prototype.push=function(e,t,a){var o=this,s=this,i=s.current;this.transitionTo(e,(function(e){S6(e.fullPath),x7(o.router,e,i,!1),t&&t(e)}),a)},t.prototype.replace=function(e,t,a){var o=this,s=this,i=s.current;this.transitionTo(e,(function(e){_6(e.fullPath),x7(o.router,e,i,!1),t&&t(e)}),a)},t.prototype.go=function(e){window.history.go(e)},t.prototype.ensureURL=function(e){var t=this.current.fullPath;D6()!==t&&(e?S6(t):_6(t))},t.prototype.getCurrentLocation=function(){return D6()},t}(d6);function z6(e){var t=w6(e);if(!/^\/#/.test(t))return window.location.replace(F8(e+"/#"+t)),!0}function C6(){var e=D6();return"/"===e.charAt(0)||(_6("/"+e),!1)}function D6(){var e=window.location.href,t=e.indexOf("#");return t<0?"":(e=e.slice(t+1),e)}function R6(e){var t=window.location.href,a=t.indexOf("#"),o=a>=0?t.slice(0,a):t;return o+"#"+e}function S6(e){N7?$7(R6(e)):window.location.hash=e}function _6(e){N7?q7(R6(e)):window.location.replace(R6(e))}var k6=function(e){function t(t,a){e.call(this,t,a),this.stack=[],this.index=-1}return e&&(t.__proto__=e),t.prototype=Object.create(e&&e.prototype),t.prototype.constructor=t,t.prototype.push=function(e,t,a){var o=this;this.transitionTo(e,(function(e){o.stack=o.stack.slice(0,o.index+1).concat(e),o.index++,t&&t(e)}),a)},t.prototype.replace=function(e,t,a){var o=this;this.transitionTo(e,(function(e){o.stack=o.stack.slice(0,o.index).concat(e),t&&t(e)}),a)},t.prototype.go=function(e){var t=this,a=this.index+e;if(!(a<0||a>=this.stack.length)){var o=this.stack[a];this.confirmTransition(o,(function(){var e=t.current;t.index=a,t.updateRoute(o),t.router.afterHooks.forEach((function(t){t&&t(o,e)}))}),(function(e){o6(e,J7.duplicated)&&(t.index=a)}))}},t.prototype.getCurrentLocation=function(){var e=this.stack[this.stack.length-1];return e?e.fullPath:"/"},t.prototype.ensureURL=function(){},t}(d6),M6=function(e){void 0===e&&(e={}),this.app=null,this.apps=[],this.options=e,this.beforeHooks=[],this.resolveHooks=[],this.afterHooks=[],this.matcher=z7(e.routes||[],this);var t=e.mode||"hash";switch(this.fallback="history"===t&&!N7&&!1!==e.fallback,this.fallback&&(t="hash"),P7||(t="abstract"),this.mode=t,t){case"history":this.history=new y6(this,e.base);break;case"hash":this.history=new I6(this,e.base,this.fallback);break;case"abstract":this.history=new k6(this,e.base);break;default:0}},T6={currentRoute:{configurable:!0}};M6.prototype.match=function(e,t,a){return this.matcher.match(e,t,a)},T6.currentRoute.get=function(){return this.history&&this.history.current},M6.prototype.init=function(e){var t=this;if(this.apps.push(e),e.$once("hook:destroyed",(function(){var a=t.apps.indexOf(e);a>-1&&t.apps.splice(a,1),t.app===e&&(t.app=t.apps[0]||null),t.app||t.history.teardown()})),!this.app){this.app=e;var a=this.history;if(a instanceof y6||a instanceof I6){var o=function(e){var o=a.current,s=t.options.scrollBehavior,i=N7&&s;i&&"fullPath"in e&&x7(t,e,o,!1)},s=function(e){a.setupListeners(),o(e)};a.transitionTo(a.getCurrentLocation(),s,s)}a.listen((function(e){t.apps.forEach((function(t){t._route=e}))}))}},M6.prototype.beforeEach=function(e){return x6(this.beforeHooks,e)},M6.prototype.beforeResolve=function(e){return x6(this.resolveHooks,e)},M6.prototype.afterEach=function(e){return x6(this.afterHooks,e)},M6.prototype.onReady=function(e,t){this.history.onReady(e,t)},M6.prototype.onError=function(e){this.history.onError(e)},M6.prototype.push=function(e,t,a){var o=this;if(!t&&!a&&"undefined"!==typeof Promise)return new Promise((function(t,a){o.history.push(e,t,a)}));this.history.push(e,t,a)},M6.prototype.replace=function(e,t,a){var o=this;if(!t&&!a&&"undefined"!==typeof Promise)return new Promise((function(t,a){o.history.replace(e,t,a)}));this.history.replace(e,t,a)},M6.prototype.go=function(e){this.history.go(e)},M6.prototype.back=function(){this.go(-1)},M6.prototype.forward=function(){this.go(1)},M6.prototype.getMatchedComponents=function(e){var t=e?e.matched?e:this.resolve(e).route:this.currentRoute;return t?[].concat.apply([],t.matched.map((function(e){return Object.keys(e.components).map((function(t){return e.components[t]}))}))):[]},M6.prototype.resolve=function(e,t,a){t=t||this.history.current;var o=h7(e,t,a,this),s=this.match(o,t),i=s.redirectedFrom||s.fullPath,n=this.history.base,r=B6(n,i,this.mode);return{location:o,route:s,href:r,normalizedTo:o,resolved:s}},M6.prototype.getRoutes=function(){return this.matcher.getRoutes()},M6.prototype.addRoute=function(e,t){this.matcher.addRoute(e,t),this.history.current!==R8&&this.history.transitionTo(this.history.getCurrentLocation())},M6.prototype.addRoutes=function(e){this.matcher.addRoutes(e),this.history.current!==R8&&this.history.transitionTo(this.history.getCurrentLocation())},Object.defineProperties(M6.prototype,T6);var V6=M6;function x6(e,t){return e.push(t),function(){var a=e.indexOf(t);a>-1&&e.splice(a,1)}}function B6(e,t,a){var o="hash"===a?"#"+t:t;return e?F8(e+"/"+o):o}M6.install=A7,M6.version="3.6.5",M6.isNavigationFailure=o6,M6.NavigationFailureType=J7,M6.START_LOCATION=R8,P7&&window.Vue&&window.Vue.use(M6);var L6=function(){var e=this,t=e.$createElement,a=e._self._c||t;return a("b-tab",[a("Summary",{attrs:{iam_data:e.iam_data,"policy-filter":e.policyFilter}})],1)},O6=[],E6=function(){var e=this,t=e.$createElement,a=e._self._c||t;return a("div",{staticClass:"report"},[a("b-row",{staticClass:"mb-3"},[a("b-col",[a("h3",[e._v("Executive Summary")]),a("p",[e._v(" This report contains the security assessment results from "),a("a",{attrs:{href:"https://github.com/salesforce/cloudsplaining",rel:"noreferrer"}},[e._v("Cloudsplaining")]),e._v(", which maps out the IAM risk landscape in a report.")]),a("p",[e._v(" The assessment identifies where resource ARN constraints are not used and identifies other risks in IAM policies: ")]),a("ul",[a("li",[e._v("Privilege Escalation")]),a("li",[e._v("Resource Exposure")]),a("li",[e._v("Infrastructure Modification")]),a("li",[e._v("Data Exfiltration")])]),a("p",[e._v(" Remediating these issues, where necessary, will help to limit the blast radius in the case of compromised AWS credentials. ")])])],1),a("b-row",{staticClass:"mb-3"},[a("b-col",{attrs:{lg:"8"}},[a("div",{staticClass:"d-none d-sm-block"},[a("SummaryFindings",{attrs:{"inline-policy-risks":e.inlinePolicyRisks,"customer-managed-policy-risks":e.customerManagedPolicyRisks,"aws-managed-policy-risks":e.awsManagedPolicyRisks}})],1)]),a("b-col",[a("b-table-simple",{attrs:{small:"",responsive:""}},[a("b-thead",{attrs:{"head-variant":"dark"}},[a("b-tr",[a("b-th",[e._v("Risk")]),a("b-th",[e._v("Instances")]),a("b-th",[e._v("Severity")])],1)],1),a("b-tbody",[a("b-tr",[a("b-th",[e._v("Privilege Escalation")]),a("b-td",[e._v(e._s(e.policyRisks.PrivilegeEscalation))]),a("b-td",[e._v(e._s(e.severity.PrivilegeEscalation))])],1),a("b-tr",[a("b-th",[e._v("Data Exfiltration")]),a("b-td",[e._v(e._s(e.policyRisks.DataExfiltration))]),a("b-td",[e._v(e._s(e.severity.DataExfiltration))])],1),a("b-tr",[a("b-th",[e._v("Resource Exposure")]),a("b-td",[e._v(e._s(e.policyRisks.ResourceExposure))]),a("b-td",[e._v(e._s(e.severity.ResourceExposure))])],1),a("b-tr",[a("b-th",[e._v("Credentials Exposure")]),a("b-td",[e._v(e._s(e.policyRisks.CredentialsExposure))]),a("b-td",[e._v(e._s(e.severity.CredentialsExposure))])],1),a("b-tr",[a("b-th",[e._v("Infrastructure Modification")]),a("b-td",[e._v(e._s(e.policyRisks.InfrastructureModification))]),a("b-td",[e._v(e._s(e.severity.InfrastructureModification))])],1)],1)],1)],1)],1)],1)},U6=[],F6=function(){var e=this,t=e.$createElement,a=e._self._c||t;return a("Bar",{attrs:{"chart-options":e.chartOptions,"chart-data":e.chartData,height:e.height,"inline-policy-risks":e.inlinePolicyRisks,"aws-managed-policy-risks":e.awsManagedPolicyRisks,"customer-managed-policy-risks":e.customerManagedPolicyRisks}})},H6=[];
+ */function o(e){return e&&"object"===typeof e&&"default"in e?e["default"]:e}Object.defineProperty(t,"__esModule",{value:!0});var s=o(a("2b0e"));function i(e){return i="function"===typeof Symbol&&"symbol"===typeof Symbol.iterator?function(e){return typeof e}:function(e){return e&&"function"===typeof Symbol&&e.constructor===Symbol&&e!==Symbol.prototype?"symbol":typeof e},i(e)}function n(e){return r(e)||c(e)||l()}function r(e){if(Array.isArray(e)){for(var t=0,a=new Array(e.length);t1&&void 0!==arguments[1]?arguments[1]:{};return e.reduce((function(e,a){var o=a.passengers[0],s="function"===typeof o?o(t):a.passengers;return e.concat(s)}),[])}function p(e,t){return e.map((function(e,t){return[t,e]})).sort((function(e,a){return t(e[1],a[1])||e[0]-a[0]})).map((function(e){return e[1]}))}function u(e,t){return t.reduce((function(t,a){return e.hasOwnProperty(a)&&(t[a]=e[a]),t}),{})}var f={},g={},v={},A=s.extend({data:function(){return{transports:f,targets:g,sources:v,trackInstances:h}},methods:{open:function(e){if(h){var t=e.to,a=e.from,o=e.passengers,i=e.order,n=void 0===i?1/0:i;if(t&&a&&o){var r={to:t,from:a,passengers:d(o),order:n},c=Object.keys(this.transports);-1===c.indexOf(t)&&s.set(this.transports,t,[]);var l=this.$_getTransportIndex(r),m=this.transports[t].slice(0);-1===l?m.push(r):m[l]=r,this.transports[t]=p(m,(function(e,t){return e.order-t.order}))}}},close:function(e){var t=arguments.length>1&&void 0!==arguments[1]&&arguments[1],a=e.to,o=e.from;if(a&&(o||!1!==t)&&this.transports[a])if(t)this.transports[a]=[];else{var s=this.$_getTransportIndex(e);if(s>=0){var i=this.transports[a].slice(0);i.splice(s,1),this.transports[a]=i}}},registerTarget:function(e,t,a){h&&(this.trackInstances&&!a&&this.targets[e]&&console.warn("[portal-vue]: Target ".concat(e," already exists")),this.$set(this.targets,e,Object.freeze([t])))},unregisterTarget:function(e){this.$delete(this.targets,e)},registerSource:function(e,t,a){h&&(this.trackInstances&&!a&&this.sources[e]&&console.warn("[portal-vue]: source ".concat(e," already exists")),this.$set(this.sources,e,Object.freeze([t])))},unregisterSource:function(e){this.$delete(this.sources,e)},hasTarget:function(e){return!(!this.targets[e]||!this.targets[e][0])},hasSource:function(e){return!(!this.sources[e]||!this.sources[e][0])},hasContentFor:function(e){return!!this.transports[e]&&!!this.transports[e].length},$_getTransportIndex:function(e){var t=e.to,a=e.from;for(var o in this.transports[t])if(this.transports[t][o].from===a)return+o;return-1}}}),P=new A(f),b=1,y=s.extend({name:"portal",props:{disabled:{type:Boolean},name:{type:String,default:function(){return String(b++)}},order:{type:Number,default:0},slim:{type:Boolean},slotProps:{type:Object,default:function(){return{}}},tag:{type:String,default:"DIV"},to:{type:String,default:function(){return String(Math.round(1e7*Math.random()))}}},created:function(){var e=this;this.$nextTick((function(){P.registerSource(e.name,e)}))},mounted:function(){this.disabled||this.sendUpdate()},updated:function(){this.disabled?this.clear():this.sendUpdate()},beforeDestroy:function(){P.unregisterSource(this.name),this.clear()},watch:{to:function(e,t){t&&t!==e&&this.clear(t),this.sendUpdate()}},methods:{clear:function(e){var t={from:this.name,to:e||this.to};P.close(t)},normalizeSlots:function(){return this.$scopedSlots.default?[this.$scopedSlots.default]:this.$slots.default},normalizeOwnChildren:function(e){return"function"===typeof e?e(this.slotProps):e},sendUpdate:function(){var e=this.normalizeSlots();if(e){var t={from:this.name,to:this.to,passengers:n(e),order:this.order};P.open(t)}else this.clear()}},render:function(e){var t=this.$slots.default||this.$scopedSlots.default||[],a=this.tag;return t&&this.disabled?t.length<=1&&this.slim?this.normalizeOwnChildren(t)[0]:e(a,[this.normalizeOwnChildren(t)]):this.slim?e():e(a,{class:{"v-portal":!0},style:{display:"none"},key:"v-portal-placeholder"})}}),w=s.extend({name:"portalTarget",props:{multiple:{type:Boolean,default:!1},name:{type:String,required:!0},slim:{type:Boolean,default:!1},slotProps:{type:Object,default:function(){return{}}},tag:{type:String,default:"div"},transition:{type:[String,Object,Function]}},data:function(){return{transports:P.transports,firstRender:!0}},created:function(){var e=this;this.$nextTick((function(){P.registerTarget(e.name,e)}))},watch:{ownTransports:function(){this.$emit("change",this.children().length>0)},name:function(e,t){P.unregisterTarget(t),P.registerTarget(e,this)}},mounted:function(){var e=this;this.transition&&this.$nextTick((function(){e.firstRender=!1}))},beforeDestroy:function(){P.unregisterTarget(this.name)},computed:{ownTransports:function(){var e=this.transports[this.name]||[];return this.multiple?e:0===e.length?[]:[e[e.length-1]]},passengers:function(){return m(this.ownTransports,this.slotProps)}},methods:{children:function(){return 0!==this.passengers.length?this.passengers:this.$scopedSlots.default?this.$scopedSlots.default(this.slotProps):this.$slots.default||[]},noWrapper:function(){var e=this.slim&&!this.transition;return e&&this.children().length>1&&console.warn("[portal-vue]: PortalTarget with `slim` option received more than one child element."),e}},render:function(e){var t=this.noWrapper(),a=this.children(),o=this.transition||this.tag;return t?a[0]:this.slim&&!o?e():e(o,{props:{tag:this.transition&&this.tag?this.tag:void 0},class:{"vue-portal-target":!0}},a)}}),I=0,z=["disabled","name","order","slim","slotProps","tag","to"],C=["multiple","transition"],D=s.extend({name:"MountingPortal",inheritAttrs:!1,props:{append:{type:[Boolean,String]},bail:{type:Boolean},mountTo:{type:String,required:!0},disabled:{type:Boolean},name:{type:String,default:function(){return"mounted_"+String(I++)}},order:{type:Number,default:0},slim:{type:Boolean},slotProps:{type:Object,default:function(){return{}}},tag:{type:String,default:"DIV"},to:{type:String,default:function(){return String(Math.round(1e7*Math.random()))}},multiple:{type:Boolean,default:!1},targetSlim:{type:Boolean},targetSlotProps:{type:Object,default:function(){return{}}},targetTag:{type:String,default:"div"},transition:{type:[String,Object,Function]}},created:function(){if("undefined"!==typeof document){var e=document.querySelector(this.mountTo);if(e){var t=this.$props;if(P.targets[t.name])t.bail?console.warn("[portal-vue]: Target ".concat(t.name," is already mounted.\n Aborting because 'bail: true' is set")):this.portalTarget=P.targets[t.name];else{var a=t.append;if(a){var o="string"===typeof a?a:"DIV",s=document.createElement(o);e.appendChild(s),e=s}var i=u(this.$props,C);i.slim=this.targetSlim,i.tag=this.targetTag,i.slotProps=this.targetSlotProps,i.name=this.to,this.portalTarget=new w({el:e,parent:this.$parent||this,propsData:i})}}else console.error("[portal-vue]: Mount Point '".concat(this.mountTo,"' not found in document"))}},beforeDestroy:function(){var e=this.portalTarget;if(this.append){var t=e.$el;t.parentNode.removeChild(t)}e.$destroy()},render:function(e){if(!this.portalTarget)return console.warn("[portal-vue] Target wasn't mounted"),e();if(!this.$scopedSlots.manual){var t=u(this.$props,z);return e(y,{props:t,attrs:this.$attrs,on:this.$listeners,scopedSlots:this.$scopedSlots},this.$slots.default)}var a=this.$scopedSlots.manual({to:this.to});return Array.isArray(a)&&(a=a[0]),a||e()}});function R(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};e.component(t.portalName||"Portal",y),e.component(t.portalTargetName||"PortalTarget",w),e.component(t.MountingPortalName||"MountingPortal",D)}var S={install:R};t.default=S,t.Portal=y,t.PortalTarget=w,t.MountingPortal=D,t.Wormhole=P},"32bf":function(e,t,a){"use strict";e.exports=function(e){var t,a,o=0,s=e.tokens,i=e.tokens.length;for(t=a=0;t0&&o++,"text"===s[t].type&&t+1s)throw o("Maximum allowed index exceeded");return e}},"384f":function(e,t,a){"use strict";var o=a("e330"),s=a("5388"),i=a("cb27"),n=i.Set,r=i.proto,c=o(r.forEach),l=o(r.keys),h=l(new n).next;e.exports=function(e,t,a){return a?s({iterator:l(e),next:h},t):c(e,t)}},"395e":function(e,t,a){"use strict";var o=a("dc19"),s=a("cb27").has,i=a("8e16"),n=a("7f65"),r=a("5388"),c=a("2a62");e.exports=function(e){var t=o(this),a=n(e);if(i(t)=0&&32===e.pending.charCodeAt(a))if(a>=1&&32===e.pending.charCodeAt(a-1)){i=a-1;while(i>=1&&32===e.pending.charCodeAt(i-1))i--;e.pending=e.pending.slice(0,i),e.push("hardbreak","br",0)}else e.pending=e.pending.slice(0,-1),e.push("softbreak","br",0);else e.push("softbreak","br",0);n++;while(n3)&&!(e.sCount[l]<0)){for(s=!1,i=0,n=h.length;ia.parts.length&&(o.parts.length=a.parts.length)}else{var n=[];for(s=0;s=n)return-1;if(a=e.src.charCodeAt(i++),a<48||a>57)return-1;for(;;){if(i>=n)return-1;if(a=e.src.charCodeAt(i++),!(a>=48&&a<=57)){if(41===a||46===a)break;return-1}if(i-s>=10)return-1}return i=4)return!1;if(e.listIndent>=0&&e.sCount[x]-e.listIndent>=4&&e.sCount[x]=e.blkIndent&&(B=!0),(S=i(e,x))>=0){if(p=!0,k=e.bMarks[x]+e.tShift[x],P=Number(e.src.slice(k,S-1)),B&&1!==P)return!1}else{if(!((S=s(e,x))>=0))return!1;p=!1}if(B&&e.skipSpaces(S)>=e.eMarks[x])return!1;if(o)return!0;A=e.src.charCodeAt(S-1),v=e.tokens.length,p?(V=e.push("ordered_list_open","ol",1),1!==P&&(V.attrs=[["start",P]])):V=e.push("bullet_list_open","ul",1),V.map=g=[x,0],V.markup=String.fromCharCode(A),_=!1,T=e.md.block.ruler.getRules("list"),I=e.parentType,e.parentType="list";while(x=b?1:y-m,d>4&&(d=1),h=m+d,V=e.push("list_item_open","li",1),V.markup=String.fromCharCode(A),V.map=u=[x,0],p&&(V.info=e.src.slice(k,S-1)),D=e.tight,C=e.tShift[x],z=e.sCount[x],w=e.listIndent,e.listIndent=e.blkIndent,e.blkIndent=h,e.tight=!0,e.tShift[x]=c-e.bMarks[x],e.sCount[x]=y,c>=b&&e.isEmpty(x+1)?e.line=Math.min(e.line+2,a):e.md.block.tokenize(e,x,a,!0),e.tight&&!_||(L=!1),_=e.line-x>1&&e.isEmpty(e.line-1),e.blkIndent=e.listIndent,e.listIndent=w,e.tShift[x]=C,e.sCount[x]=z,e.tight=D,V=e.push("list_item_close","li",-1),V.markup=String.fromCharCode(A),x=e.line,u[1]=x,x>=a)break;if(e.sCount[x]=4)break;for(M=!1,l=0,f=T.length;l=e.pos)throw new Error("inline rule didn't increment state.pos");break}}else e.pos=e.posMax;t||e.pos++,r[o]=e.pos}else e.pos=r[o]},n.prototype.tokenize=function(e){var t,a,o,s=this.ruler.getRules(""),i=s.length,n=e.posMax,r=e.md.options.maxNesting;while(e.pos=e.pos)throw new Error("inline rule didn't increment state.pos");break}if(t){if(e.pos>=n)break}else e.pending+=e.src[e.pos++]}e.pending&&e.pushPending()},n.prototype.parse=function(e,t,a,o){var s,i,n,r=new this.State(e,t,a,o);for(this.tokenize(r),i=this.ruler2.getRules(""),n=i.length,s=0;sh)if(l=r[h++],l!==l)return!0}else for(;c>h;h++)if((e||h in r)&&r[h]===a)return e||h||0;return!e&&-1}};e.exports={includes:n(!0),indexOf:n(!1)}},"4fc2":function(e,t){e.exports=/[ \xA0\u1680\u2000-\u200A\u2028\u2029\u202F\u205F\u3000]/},"50c4":function(e,t,a){"use strict";var o=a("5926"),s=Math.min;e.exports=function(e){var t=o(e);return t>0?s(t,9007199254740991):0}},"52d9":function(e,t,a){"use strict";a("14d9");let o=a("fd5f"),s=a("f230"),i=a("54d2");function n(e,t,a){return"role"===a.toLowerCase()?e["roles"][t]:"group"===a.toLowerCase()?e["groups"][t]:"user"===a.toLowerCase()?e["users"][t]:void 0}function r(e,t){let a=[];if("role"===t.toLowerCase()){let t=Object.keys(e["roles"]);for(let o of t)a.push(e["roles"][o]["name"]);return a.sort()}if("group"===t.toLowerCase()){let t=Object.keys(e["groups"]);for(let o of t)a.push(e["groups"][o]["name"]);return a.sort(),a}if("user"===t.toLowerCase()){let t=Object.keys(e["users"]);for(let o of t)a.push(e["users"][o]["name"]);return a.sort(),a}}function c(e,t){let a;return"role"===t.toLowerCase()?(a=Object.keys(e["roles"]),a.sort()):"group"===t.toLowerCase()?(a=Object.keys(e["groups"]),a.sort(),a):"user"===t.toLowerCase()?(a=Object.keys(e["users"]),a.sort(),a):void 0}function l(e,t,a,o){let s,i;"role"===a.toLowerCase()?s="roles":"group"===a.toLowerCase()?s="groups":"user"===a.toLowerCase()&&(s="users"),"inline"===o.toLowerCase()?i="inline_policies":"Customer"===o?i="customer_managed_policies":"AWS"===o&&(i="aws_managed_policies");let n=e[s][t][i],r=Array.from(Object.keys(n));return r.sort(),r}function h(e,t,a,i){let n,r=[],c=l(e,t,a,i);if("inline"===i.toLowerCase())for(n in c)r.push(o.getInlinePolicy(e,c[n])["PolicyName"]);else if("AWS"===i)for(n in c)r.push(s.getManagedPolicyName(e,"AWS",c[n]));else if("Customer"===i)for(n in c)r.push(s.getManagedPolicyName(e,"Customer",c[n]));return r.sort(),r}function d(e,t,a,n){let r=l(e,t,a,"Inline"),c=l(e,t,a,"Customer"),h=l(e,t,a,"AWS"),d=[];if(r.length>0){let t;for(t of r){let a,s=o.getInlinePolicyFindings(e,t,n);for(a of s)a in d||d.push(a)}}if(c.length>0){let t;for(t of c){let a,o=s.getManagedPolicyFindings(e,"Customer",t,n);for(a of o)a in d||d.push(a)}}if(h.length>0){let t;for(t of h){let a,o=s.getManagedPolicyFindings(e,"AWS",t,n);for(a of o)a in d||d.push(a)}}return d.length>0?(d.sort(),d=i.removeDuplicatesFromArray(d),d):[]}t.getPrincipalMetadata=n,t.getPrincipalNames=r,t.getPrincipalIds=c,t.getPrincipalPolicies=l,t.getRiskAssociatedWithPrincipal=d,t.getPrincipalPolicyNames=h},5388:function(e,t,a){"use strict";var o=a("c65b");e.exports=function(e,t,a){var s,i,n=a?e:e.iterator,r=e.next;while(!(s=o(r,n)).done)if(i=t(s.value),void 0!==i)return i}},"54d2":function(e,t,a){"use strict";a("14d9");const o=e=>{let[t,a,o,s,i]=Array(5).fill(0);return Object.keys(e).forEach(n=>{e[n]["PrivilegeEscalation"]["findings"].length>0&&(t+=1),e[n]["DataExfiltration"]["findings"].length>0&&(a+=1),e[n]["ResourceExposure"]["findings"].length>0&&(o+=1),e[n]["InfrastructureModification"]["findings"].length>0&&(s+=1),e[n]["CredentialsExposure"]["findings"].length>0&&(i+=1)}),{PrivilegeEscalation:t,DataExfiltration:a,ResourceExposure:o,CredentialsExposure:i,InfrastructureModification:s}};function s(e){return e=e.replace(/([a-z])([A-Z])/g,"$1 $2"),e=e.replace(/([A-Z])([A-Z][a-z])/g,"$1 $2"),e}function i(e){const t=e=>e&&e.match(/[A-Z]{2,}(?=[A-Z][a-z]+[0-9]*|\b)|[A-Z]?[a-z]+[0-9]*|[A-Z]|[0-9]+/g).map(e=>e.toLowerCase()).join("_");return t(e)}function n(e){const t=e=>e&&e.match(/[A-Z]{2,}(?=[A-Z][a-z]+[0-9]*|\b)|[A-Z]?[a-z]+[0-9]*|[A-Z]|[0-9]+/g).map(e=>e.toLowerCase()).join("-");return t(e)}function r(e){const t=e=>e&&e.match(/[A-Z]{2,}(?=[A-Z][a-z]+[0-9]*|\b)|[A-Z]?[a-z]+[0-9]*|[A-Z]|[0-9]+/g).map(e=>e.charAt(0).toUpperCase()+e.slice(1)).join(" ");return t(e)}function c(e){let t=[];return e.forEach(e=>{t.includes(e)||t.push(e)}),t}function l(e,t="asc"){return function(a,o){if(!a.hasOwnProperty(e)||!o.hasOwnProperty(e))return 0;const s="string"===typeof a[e]?a[e].toUpperCase():a[e],i="string"===typeof o[e]?o[e].toUpperCase():o[e];let n=0;return s>i?n=1:s{const a=e.length<=h?String(e):String(e).slice(-h);return t?`${t}.${a.toLowerCase()}`:a.toLowerCase()};function m(e,t){let a={},o=e.links;for(let s=0;s`\\x00-\\x20]+",i="'[^']*'",n='"[^"]*"',r="(?:"+s+"|"+i+"|"+n+")",c="(?:\\s+"+o+"(?:\\s*=\\s*"+r+")?)",l="<[A-Za-z][A-Za-z0-9\\-]*"+c+"*\\s*\\/?>",h="<\\/[A-Za-z][A-Za-z0-9\\-]*\\s*>",d="\x3c!----\x3e|\x3c!--(?:-?[^>-])(?:-?[^-])*--\x3e",m="<[?][\\s\\S]*?[?]>",p="]*>",u="",f=new RegExp("^(?:"+l+"|"+h+"|"+d+"|"+m+"|"+p+"|"+u+")"),g=new RegExp("^(?:"+l+"|"+h+")");e.exports.HTML_TAG_RE=f,e.exports.HTML_OPEN_CLOSE_TAG_RE=g},5926:function(e,t,a){"use strict";var o=a("b42e");e.exports=function(e){var t=+e;return t!==t||0===t?0:o(t)}},"59ed":function(e,t,a){"use strict";var o=a("1626"),s=a("0d51"),i=TypeError;e.exports=function(e){if(o(e))return e;throw new i(s(e)+" is not a function")}},"5a00":function(e,t,a){"use strict";a.r(t);var o=a("2b0e"),s=function(){var e=this,t=e.$createElement,a=e._self._c||t;return a("div",{attrs:{id:"main"}},[a("b-navbar",{attrs:{toggleable:"md",variant:"faded"}},[a("b-navbar-brand",{attrs:{to:"/summary"}},[e._v(" Cloudsplaining ")]),a("b-navbar-toggle",{attrs:{target:"nav-collapse"}}),a("b-collapse",{attrs:{id:"nav-collapse","is-nav":""}},[a("b-navbar-nav",[a("b-nav-item",{attrs:{to:"/customer-policies"}},[e._v("Customer Policies")]),a("b-nav-item",{attrs:{to:"/inline-policies"}},[e._v("Inline Policies")]),a("b-nav-item",{attrs:{to:"/aws-policies"}},[e._v("AWS Policies")]),a("b-nav-item",{attrs:{to:"/iam-principals"}},[e._v("IAM Principals")]),e.show_guidance_nav?a("b-nav-item",{attrs:{to:"/guidance"}},[e._v("Guidance")]):e._e(),e.show_appendices_nav?a("b-nav-item",{attrs:{to:"/appendices"}},[e._v("Appendices")]):e._e()],1),a("b-navbar-nav",{staticClass:"ml-auto"},[a("b-nav-text",[a("strong",[e._v("Account ID:")]),e._v(" "+e._s(e.account_id)+" | "),a("strong",[e._v("Account Name:")]),e._v(" "+e._s(e.account_name))])],1)],1)],1),a("b-container",{staticClass:"mt-3 pb-3 report"},[a("b-tabs",{attrs:{"nav-class":"d-none"}},[a("router-view")],1)],1),a("b-container",[a("b-row",{staticClass:"mt-5"},[a("b-col",{staticClass:"text-center text-muted"},[e._v(" Report Generated: "+e._s(e.report_generated_time)+" ⋄ Cloudsplaining version: "),a("b-link",{attrs:{href:"https://github.com/salesforce/cloudsplaining"}},[e._v(e._s(e.cloudsplaining_version))])],1)],1)],1)],1)},i=[];const n=a("f230"),r=a("fd5f"),c=a("87dd"),l=a("5e81");function h(e){return n.getManagedPolicyNameMapping(iam_data,e)}function d(){return r.getInlinePolicyNameMapping(iam_data)}function m(e){return c.getTaskTableMapping(iam_data,e)}console.log("process.env.NODE_ENV: production"),!0===isLocalExample?(console.log("isLocalExample is set to: "+isLocalExample),console.log("process.env.NODE_ENV: production"),console.log("Note: a report generated with the Python template will not have isLocalExample set to True, because that uses a separate template.html file, which has isLocalExample set to False."),iam_data=l.sample_iam_data,console.log("IAM Data keys inside the development if statement: "+Object.keys(iam_data)),account_id="12345678912",account_name="example",report_generated_time="2020-09-01",cloudsplaining_version="0.2.2",show_guidance_nav="true",show_appendices_nav="true"):console.log("isLocalExample is set to: "+isLocalExample),console.log("IAM Data keys outside of the NODE_ENV if statements: "+Object.keys(iam_data));var p={name:"App",mounted:function(){setTimeout(()=>this.scrollFix(this.$route.hash),1)},data(){return{sharedState:iam_data,account_id:account_id,account_name:account_name,report_generated_time:report_generated_time,cloudsplaining_version:cloudsplaining_version,show_guidance_nav:"True"===show_guidance_nav,show_appendices_nav:"True"===show_appendices_nav}},computed:{iam_data(){return this.sharedState}},methods:{getManagedPolicyNameMapping:function(e){return h(e)},getInlinePolicyNameMapping:function(){return d()},getTaskTableMapping:function(e){return m(e)},scrollFix:function(e){location.hash=e}},provide(){return{iam_data:this.iam_data,getManagedPolicyNameMapping:this.getManagedPolicyNameMapping,getInlinePolicyNameMapping:this.getInlinePolicyNameMapping}}},u=p;a("259a");function f(e,t,a,o,s,i,n,r){var c,l="function"===typeof e?e.options:e;if(t&&(l.render=t,l.staticRenderFns=a,l._compiled=!0),o&&(l.functional=!0),i&&(l._scopeId="data-v-"+i),n?(c=function(e){e=e||this.$vnode&&this.$vnode.ssrContext||this.parent&&this.parent.$vnode&&this.parent.$vnode.ssrContext,e||"undefined"===typeof __VUE_SSR_CONTEXT__||(e=__VUE_SSR_CONTEXT__),s&&s.call(this,e),e&&e._registeredComponents&&e._registeredComponents.add(n)},l._ssrRegister=c):s&&(c=r?function(){s.call(this,(l.functional?this.parent:this).$root.$options.shadowRoot)}:s),c)if(l.functional){l._injectStyles=c;var h=l.render;l.render=function(e,t){return c.call(t),h(e,t)}}else{var d=l.beforeCreate;l.beforeCreate=d?[].concat(d,c):[c]}return{exports:e,options:l}}var g=f(u,s,i,!1,null,null,null),v=g.exports,A="undefined"!==typeof window,P="undefined"!==typeof document,b="undefined"!==typeof navigator,y="undefined"!==typeof Promise,w="undefined"!==typeof MutationObserver||"undefined"!==typeof WebKitMutationObserver||"undefined"!==typeof MozMutationObserver,I=A&&P&&b,z=A?window:{},C=P?document:{},D=b?navigator:{},R=(D.userAgent||"").toLowerCase(),S=R.indexOf("jsdom")>0,_=(/msie|trident/.test(R),function(){var e=!1;if(I)try{var t={get passive(){e=!0}};z.addEventListener("test",t,t),z.removeEventListener("test",t,t)}catch(a){e=!1}return e}()),k=I&&("ontouchstart"in C.documentElement||D.maxTouchPoints>0),M=I&&Boolean(z.PointerEvent||z.MSPointerEvent),T=I&&"IntersectionObserver"in z&&"IntersectionObserverEntry"in z&&"intersectionRatio"in z.IntersectionObserverEntry.prototype,V="BvConfig",x="$bvConfig",B=["xs","sm","md","lg","xl"],L=/\[(\d+)]/g,O=/^(BV?)/,E=/^\d+$/,U=/^\..+/,F=/^#/,H=/^#[A-Za-z]+[\w\-:.]*$/,j=/(<([^>]+)>)/gi,G=/\B([A-Z])/g,W=/([a-z])([A-Z])/g,N=/^[0-9]*\.?[0-9]+$/,$=/\+/g,q=/[-/\\^$*+?.()|[\]{}]/g,J=/[\s\uFEFF\xA0]+/g,K=/\s+/,Q=/\/\*$/,Y=/(\s|^)(\w)/g,X=/^\s+/,Z=/_/g,ee=/-(\w)/g,te=/^\d+-\d\d?-\d\d?(?:\s|T|$)/,ae=/-|\s|T/,oe=/^([0-1]?[0-9]|2[0-3]):[0-5]?[0-9](:[0-5]?[0-9])?$/,se=/^.*(#[^#]+)$/,ie=/%2C/g,ne=/[!'()*]/g,re=/^(\?|#|&)/,ce=/^\d+(\.\d*)?[/:]\d+(\.\d*)?$/,le=/[/:]/,he=/^col-/,de=/^BIcon/,me=/-u-.+/;function pe(e){return pe="function"==typeof Symbol&&"symbol"==typeof Symbol.iterator?function(e){return typeof e}:function(e){return e&&"function"==typeof Symbol&&e.constructor===Symbol&&e!==Symbol.prototype?"symbol":typeof e},pe(e)}function ue(e,t){if(!(e instanceof t))throw new TypeError("Cannot call a class as a function")}function fe(e,t){if("function"!==typeof t&&null!==t)throw new TypeError("Super expression must either be null or a function");Object.defineProperty(e,"prototype",{value:Object.create(t&&t.prototype,{constructor:{value:e,writable:!0,configurable:!0}}),writable:!1}),t&&Ie(e,t)}function ge(e){var t=ye();return function(){var a,o=ze(e);if(t){var s=ze(this).constructor;a=Reflect.construct(o,arguments,s)}else a=o.apply(this,arguments);return ve(this,a)}}function ve(e,t){if(t&&("object"===pe(t)||"function"===typeof t))return t;if(void 0!==t)throw new TypeError("Derived constructors may only return object or undefined");return Ae(e)}function Ae(e){if(void 0===e)throw new ReferenceError("this hasn't been initialised - super() hasn't been called");return e}function Pe(e){var t="function"===typeof Map?new Map:void 0;return Pe=function(e){if(null===e||!we(e))return e;if("function"!==typeof e)throw new TypeError("Super expression must either be null or a function");if("undefined"!==typeof t){if(t.has(e))return t.get(e);t.set(e,a)}function a(){return be(e,arguments,ze(this).constructor)}return a.prototype=Object.create(e.prototype,{constructor:{value:a,enumerable:!1,writable:!0,configurable:!0}}),Ie(a,e)},Pe(e)}function be(e,t,a){return be=ye()?Reflect.construct:function(e,t,a){var o=[null];o.push.apply(o,t);var s=Function.bind.apply(e,o),i=new s;return a&&Ie(i,a.prototype),i},be.apply(null,arguments)}function ye(){if("undefined"===typeof Reflect||!Reflect.construct)return!1;if(Reflect.construct.sham)return!1;if("function"===typeof Proxy)return!0;try{return Boolean.prototype.valueOf.call(Reflect.construct(Boolean,[],(function(){}))),!0}catch(e){return!1}}function we(e){return-1!==Function.toString.call(e).indexOf("[native code]")}function Ie(e,t){return Ie=Object.setPrototypeOf||function(e,t){return e.__proto__=t,e},Ie(e,t)}function ze(e){return ze=Object.setPrototypeOf?Object.getPrototypeOf:function(e){return e.__proto__||Object.getPrototypeOf(e)},ze(e)}var Ce=A?z.Element:function(e){fe(a,e);var t=ge(a);function a(){return ue(this,a),t.apply(this,arguments)}return a}(Pe(Object)),De=A?z.HTMLElement:function(e){fe(a,e);var t=ge(a);function a(){return ue(this,a),t.apply(this,arguments)}return a}(Ce),Re=A?z.SVGElement:function(e){fe(a,e);var t=ge(a);function a(){return ue(this,a),t.apply(this,arguments)}return a}(Ce),Se=A?z.File:function(e){fe(a,e);var t=ge(a);function a(){return ue(this,a),t.apply(this,arguments)}return a}(Pe(Object));function _e(e){return _e="function"==typeof Symbol&&"symbol"==typeof Symbol.iterator?function(e){return typeof e}:function(e){return e&&"function"==typeof Symbol&&e.constructor===Symbol&&e!==Symbol.prototype?"symbol":typeof e},_e(e)}var ke=function(e){return _e(e)},Me=function(e){return Object.prototype.toString.call(e).slice(8,-1)},Te=function(e){return void 0===e},Ve=function(e){return null===e},xe=function(e){return Te(e)||Ve(e)},Be=function(e){return"function"===ke(e)},Le=function(e){return"boolean"===ke(e)},Oe=function(e){return"string"===ke(e)},Ee=function(e){return"number"===ke(e)},Ue=function(e){return N.test(String(e))},Fe=function(e){return Array.isArray(e)},He=function(e){return null!==e&&"object"===_e(e)},je=function(e){return"[object Object]"===Object.prototype.toString.call(e)},Ge=function(e){return e instanceof Date},We=function(e){return e instanceof Event},Ne=function(e){return e instanceof Se},$e=function(e){return"RegExp"===Me(e)},qe=function(e){return!xe(e)&&Be(e.then)&&Be(e.catch)};function Je(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Ke(e){for(var t=1;te.length)&&(t=e.length);for(var a=0,o=new Array(t);a1&&void 0!==arguments[1]?arguments[1]:t;return Fe(t)?t.reduce((function(t,a){return[].concat(ut(t),[e(a,a)])}),[]):je(t)?at(t).reduce((function(a,o){return mt(mt({},a),{},pt({},o,e(t[o],t[o])))}),{}):a},yt=function(e){return e},wt=function(e,t){var a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:void 0;if(t=Fe(t)?t.join("."):t,!t||!He(e))return a;if(t in e)return e[t];t=String(t).replace(L,".$1");var o=t.split(".").filter(yt);return 0===o.length?a:o.every((function(t){return He(e)&&t in e&&!xe(e=e[t])}))?e:Ve(e)?null:a},It=function(e,t){var a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:null,o=wt(e,t);return xe(o)?a:o},zt=a("938d"),Ct=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:null;Object(zt["a"])()||console.warn("[BootstrapVue warn]: ".concat(t?"".concat(t," - "):"").concat(e))},Dt=function(e){return!I&&(Ct("".concat(e,": Can not be called during SSR.")),!0)},Rt=function(e){return!y&&(Ct("".concat(e,": Requires Promise support.")),!0)},St=function(e){return!w&&(Ct("".concat(e,": Requires MutationObserver support.")),!0)};function _t(e,t){if(!(e instanceof t))throw new TypeError("Cannot call a class as a function")}function kt(e,t){for(var a=0;a0&&void 0!==arguments[0]?arguments[0]:{};if(je(t)){var a=tt(t);a.forEach((function(a){var o=t[a];"breakpoints"===a?!Fe(o)||o.length<2||o.some((function(e){return!Oe(e)||0===e.length}))?Ct('"breakpoints" must be an array of at least 2 breakpoint names',V):e.$_config[a]=bt(o):je(o)&&(e.$_config[a]=tt(o).reduce((function(e,t){return Te(o[t])||(e[t]=bt(o[t])),e}),e.$_config[a]||{}))}))}}},{key:"resetConfig",value:function(){this.$_config={}}},{key:"getConfig",value:function(){return bt(this.$_config)}},{key:"getConfigValue",value:function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:void 0;return bt(wt(this.$_config,e,t))}}]),e}(),Vt=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:{},t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:o["default"];t.prototype[x]=o["default"].prototype[x]=t.prototype[x]||o["default"].prototype[x]||new Tt,t.prototype[x].setConfig(e)};function xt(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Bt(e){for(var t=1;t0&&void 0!==arguments[0]?arguments[0]:{},t=e.components,a=e.directives,o=e.plugins,s=function e(s){var i=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};e.installed||(e.installed=!0,Ot(s),Vt(i,s),Wt(s,t),$t(s,a),jt(s,o))};return s.installed=!1,s},Ut=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:{},t=e.components,a=e.directives,o=e.plugins,s=function e(s){e.installed||(e.installed=!0,Ot(s),Wt(s,t),$t(s,a),jt(s,o))};return s.installed=!1,s},Ft=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:{},t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};return Bt(Bt({},t),{},{install:Et(e)})},Ht=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:{},t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};return Bt(Bt({},t),{},{install:Ut(e)})},jt=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};for(var a in t)a&&t[a]&&e.use(t[a])},Gt=function(e,t,a){e&&t&&a&&e.component(t,a)},Wt=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};for(var a in t)Gt(e,a,t[a])},Nt=function(e,t,a){e&&t&&a&&e.directive(t.replace(/^VB/,"B"),a)},$t=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};for(var a in t)Nt(e,a,t[a])},qt="BAlert",Jt="BAspect",Kt="BAvatar",Qt="BAvatarGroup",Yt="BBadge",Xt="BBreadcrumb",Zt="BBreadcrumbItem",ea="BBreadcrumbLink",ta="BButton",aa="BButtonClose",oa="BButtonGroup",sa="BButtonToolbar",ia="BCalendar",na="BCard",ra="BCardBody",ca="BCardFooter",la="BCardGroup",ha="BCardHeader",da="BCardImg",ma="BCardImgLazy",pa="BCardSubTitle",ua="BCardText",fa="BCardTitle",ga="BCarousel",va="BCarouselSlide",Aa="BCol",Pa="BCollapse",ba="BContainer",ya="BDropdown",wa="BDropdownDivider",Ia="BDropdownForm",za="BDropdownGroup",Ca="BDropdownHeader",Da="BDropdownItem",Ra="BDropdownItemButton",Sa="BDropdownText",_a="BEmbed",ka="BForm",Ma="BFormCheckbox",Ta="BFormCheckboxGroup",Va="BFormDatalist",xa="BFormDatepicker",Ba="BFormFile",La="BFormGroup",Oa="BFormInput",Ea="BFormInvalidFeedback",Ua="BFormRadio",Fa="BFormRadioGroup",Ha="BFormRating",ja="BFormRow",Ga="BFormSelect",Wa="BFormSelectOption",Na="BFormSelectOptionGroup",$a="BFormSpinbutton",qa="BFormTag",Ja="BFormTags",Ka="BFormText",Qa="BFormTextarea",Ya="BFormTimepicker",Xa="BFormValidFeedback",Za="BIcon",eo="BIconstack",to="BIconBase",ao="BImg",oo="BImgLazy",so="BInputGroup",io="BInputGroupAddon",no="BInputGroupAppend",ro="BInputGroupPrepend",co="BInputGroupText",lo="BJumbotron",ho="BLink",mo="BListGroup",po="BListGroupItem",uo="BMedia",fo="BMediaAside",go="BMediaBody",vo="BModal",Ao="BMsgBox",Po="BNav",bo="BNavbar",yo="BNavbarBrand",wo="BNavbarNav",Io="BNavbarToggle",zo="BNavForm",Co="BNavItem",Do="BNavItemDropdown",Ro="BNavText",So="BOverlay",_o="BPagination",ko="BPaginationNav",Mo="BPopover",To="BProgress",Vo="BProgressBar",xo="BRow",Bo="BSidebar",Lo="BSkeleton",Oo="BSkeletonIcon",Eo="BSkeletonImg",Uo="BSkeletonTable",Fo="BSkeletonWrapper",Ho="BSpinner",jo="BTab",Go="BTable",Wo="BTableCell",No="BTableLite",$o="BTableSimple",qo="BTabs",Jo="BTbody",Ko="BTfoot",Qo="BTh",Yo="BThead",Xo="BTime",Zo="BToast",es="BToaster",ts="BTooltip",as="BTr",os="BVCollapse",ss="BVFormBtnLabelControl",is="BVFormRatingStar",ns="BVPopover",rs="BVPopoverTemplate",cs="BVPopper",ls="BVTabButton",hs="BVToastPop",ds="BVTooltip",ms="BVTooltipTemplate",ps="BVTransition",us="BVTransporter",fs="BVTransporterTarget",gs=function(){return(gs=Object.assign||function(e){for(var t,a=1,o=arguments.length;a=0||Object.prototype.propertyIsEnumerable.call(e,a)&&(s[a]=e[a])}return s}function Cs(e,t){if(null==e)return{};var a,o,s={},i=Object.keys(e);for(o=0;o=0||(s[a]=e[a]);return s}function Ds(e){return Ds="function"==typeof Symbol&&"symbol"==typeof Symbol.iterator?function(e){return typeof e}:function(e){return e&&"function"==typeof Symbol&&e.constructor===Symbol&&e!==Symbol.prototype?"symbol":typeof e},Ds(e)}var Rs="_uid",Ss=o["default"].version.startsWith("3"),_s=Ss?"ref_for":"refInFor",ks=["class","staticClass","style","attrs","props","domProps","on","nativeOn","directives","scopedSlots","slot","key","ref","refInFor"],Ms=o["default"].extend.bind(o["default"]);if(Ss){var Ts=o["default"].extend,Vs=["router-link","transition","transition-group"],xs=o["default"].vModelDynamic.created,Bs=o["default"].vModelDynamic.beforeUpdate;o["default"].vModelDynamic.created=function(e,t,a){xs.call(this,e,t,a),e._assign||(e._assign=function(){})},o["default"].vModelDynamic.beforeUpdate=function(e,t,a){Bs.call(this,e,t,a),e._assign||(e._assign=function(){})},Ms=function(e){if("object"===Ds(e)&&e.render&&!e.__alreadyPatched){var t=e.render;e.__alreadyPatched=!0,e.render=function(a){var o=function(e,t,o){var s=void 0===o?[]:[Array.isArray(o)?o.filter(Boolean):o],i="string"===typeof e&&!Vs.includes(e),n=t&&"object"===Ds(t)&&!Array.isArray(t);if(!n)return a.apply(void 0,[e,t].concat(s));var r=t.attrs,c=t.props,l=zs(t,["attrs","props"]),h=ws(ws({},l),{},{attrs:r,props:i?{}:c});return"router-link"!==e||h.slots||h.scopedSlots||(h.scopedSlots={$hasNormal:function(){}}),a.apply(void 0,[e,h].concat(s))};if(e.functional){var s,i,n=arguments[1],r=ws({},n);r.data={attrs:ws({},n.data.attrs||{}),props:ws({},n.data.props||{})},Object.keys(n.data||{}).forEach((function(e){ks.includes(e)?r.data[e]=n.data[e]:e in n.props?r.data.props[e]=n.data[e]:e.startsWith("on")||(r.data.attrs[e]=n.data[e])}));var c=["_ctx"],l=(null===(s=n.children)||void 0===s||null===(i=s.default)||void 0===i?void 0:i.call(s))||n.children;return l&&0===Object.keys(r.children).filter((function(e){return!c.includes(e)})).length?delete r.children:r.children=l,r.data.on=n.listeners,t.call(this,o,r)}return t.call(this,o)}}return Ts.call(this,e)}.bind(o["default"])}var Ls=o["default"].nextTick,Os="activate-tab",Es="blur",Us="cancel",Fs="change",Hs="changed",js="click",Gs="close",Ws="context",Ns="context-changed",$s="destroyed",qs="disable",Js="disabled",Ks="dismissed",Qs="dismiss-count-down",Ys="enable",Xs="enabled",Zs="filtered",ei="first",ti="focus",ai="focusin",oi="focusout",si="head-clicked",ii="hidden",ni="hide",ri="img-error",ci="input",li="last",hi="mouseenter",di="mouseleave",mi="next",pi="ok",ui="open",fi="page-click",gi="paused",vi="prev",Ai="refresh",Pi="refreshed",bi="remove",yi="row-clicked",wi="row-contextmenu",Ii="row-dblclicked",zi="row-hovered",Ci="row-middle-clicked",Di="row-selected",Ri="row-unhovered",Si="selected",_i="show",ki="shown",Mi="sliding-end",Ti="sliding-start",Vi="sort-changed",xi="tag-state",Bi="toggle",Li="unpaused",Oi="update",Ei=Ss?"vnodeBeforeUnmount":"hook:beforeDestroy",Ui=Ss?"vNodeUnmounted":"hook:destroyed",Fi="update:",Hi="bv",ji="::",Gi={passive:!0},Wi={passive:!0,capture:!1},Ni=void 0,$i=Array,qi=Boolean,Ji=Date,Ki=Function,Qi=Number,Yi=Object,Xi=RegExp,Zi=String,en=[$i,Ki],tn=[$i,Yi],an=[$i,Yi,Zi],on=[$i,Zi],sn=[qi,Qi],nn=[qi,Qi,Zi],rn=[qi,Zi],cn=[Ji,Zi],ln=[Ki,Zi],hn=[Qi,Zi],dn=[Qi,Yi,Zi],mn=[Yi,Ki],pn=[Yi,Zi],un="add-button-text",fn="append",gn="aside",vn="badge",An="bottom-row",Pn="button-content",bn="custom-foot",yn="decrement",wn="default",In="description",zn="dismiss",Cn="drop-placeholder",Dn="ellipsis-text",Rn="empty",Sn="emptyfiltered",_n="file-name",kn="first",Mn="first-text",Tn="footer",Vn="header",xn="header-close",Bn="icon-clear",Ln="icon-empty",On="icon-full",En="icon-half",Un="img",Fn="increment",Hn="invalid-feedback",jn="label",Gn="last-text",Wn="lead",Nn="loading",$n="modal-backdrop",qn="modal-cancel",Jn="modal-footer",Kn="modal-header",Qn="modal-header-close",Yn="modal-ok",Xn="modal-title",Zn="nav-next-decade",er="nav-next-month",tr="nav-next-year",ar="nav-prev-decade",or="nav-prev-month",sr="nav-prev-year",ir="nav-this-month",nr="next-text",rr="overlay",cr="page",lr="placeholder",hr="prepend",dr="prev-text",mr="row-details",pr="table-busy",ur="table-caption",fr="table-colgroup",gr="tabs-end",vr="tabs-start",Ar="text",Pr="thead-top",br="title",yr="toast-title",wr="top-row",Ir="valid-feedback",zr=function(){return Array.from.apply(Array,arguments)},Cr=function(e,t){return-1!==e.indexOf(t)},Dr=function(){for(var e=arguments.length,t=new Array(e),a=0;a1&&void 0!==arguments[1]?arguments[1]:{},a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:{};return e=Dr(e).filter(yt),e.some((function(e){return t[e]||a[e]}))},Mr=function(e){var t,a=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{},o=arguments.length>2&&void 0!==arguments[2]?arguments[2]:{},s=arguments.length>3&&void 0!==arguments[3]?arguments[3]:{};e=Dr(e).filter(yt);for(var i=0;i0&&void 0!==arguments[0]?arguments[0]:wn,t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:this.$scopedSlots,a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:this.$slots;return kr(e,t,a)},normalizeSlot:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:wn,t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{},a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:this.$scopedSlots,o=arguments.length>3&&void 0!==arguments[3]?arguments[3]:this.$slots,s=Mr(e,t,a,o);return s?Dr(s):s}}}),Vr=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:NaN,a=parseInt(e,10);return isNaN(a)?t:a},xr=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:NaN,a=parseFloat(e);return isNaN(a)?t:a},Br=function(e,t){return xr(e).toFixed(Vr(t,0))},Lr=function(e){return e.replace(G,"-$1").toLowerCase()},Or=function(e){return e=Lr(e).replace(ee,(function(e,t){return t?t.toUpperCase():""})),e.charAt(0).toUpperCase()+e.slice(1)},Er=function(e){return e.replace(Z," ").replace(W,(function(e,t,a){return t+" "+a})).replace(Y,(function(e,t,a){return t+a.toUpperCase()}))},Ur=function(e){return e=Oe(e)?e.trim():String(e),e.charAt(0).toLowerCase()+e.slice(1)},Fr=function(e){return e=Oe(e)?e.trim():String(e),e.charAt(0).toUpperCase()+e.slice(1)},Hr=function(e){return e.replace(q,"\\$&")},jr=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:2;return xe(e)?"":Fe(e)||je(e)&&e.toString===Object.prototype.toString?JSON.stringify(e,null,t):String(e)},Gr=function(e){return jr(e).replace(X,"")},Wr=function(e){return jr(e).trim()},Nr=function(e){return jr(e).toLowerCase()},$r=Ce.prototype,qr=["button","[href]:not(.disabled)","input","select","textarea","[tabindex]","[contenteditable]"].map((function(e){return"".concat(e,":not(:disabled):not([disabled])")})).join(", "),Jr=$r.matches||$r.msMatchesSelector||$r.webkitMatchesSelector,Kr=$r.closest||function(e){var t=this;do{if(cc(t,e))return t;t=t.parentElement||t.parentNode}while(!Ve(t)&&t.nodeType===Node.ELEMENT_NODE);return null},Qr=(z.requestAnimationFrame||z.webkitRequestAnimationFrame||z.mozRequestAnimationFrame||z.msRequestAnimationFrame||z.oRequestAnimationFrame||function(e){return setTimeout(e,16)}).bind(z),Yr=z.MutationObserver||z.WebKitMutationObserver||z.MozMutationObserver||null,Xr=function(e){return e&&e.parentNode&&e.parentNode.removeChild(e)},Zr=function(e){return!(!e||e.nodeType!==Node.ELEMENT_NODE)},ec=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:[],t=C.activeElement;return t&&!e.some((function(e){return e===t}))?t:null},tc=function(e,t){return jr(e).toLowerCase()===jr(t).toLowerCase()},ac=function(e){return Zr(e)&&e===ec()},oc=function(e){if(!Zr(e)||!e.parentNode||!hc(C.body,e))return!1;if("none"===yc(e,"display"))return!1;var t=wc(e);return!!(t&&t.height>0&&t.width>0)},sc=function(e){return!Zr(e)||e.disabled||Ac(e,"disabled")||uc(e,"disabled")},ic=function(e){return Zr(e)&&e.offsetHeight},nc=function(e,t){return zr((Zr(t)?t:C).querySelectorAll(e))},rc=function(e,t){return(Zr(t)?t:C).querySelector(e)||null},cc=function(e,t){return!!Zr(e)&&Jr.call(e,t)},lc=function(e,t){var a=arguments.length>2&&void 0!==arguments[2]&&arguments[2];if(!Zr(t))return null;var o=Kr.call(t,e);return a?o:o===t?null:o},hc=function(e,t){return!(!e||!Be(e.contains))&&e.contains(t)},dc=function(e){return C.getElementById(/^#/.test(e)?e.slice(1):e)||null},mc=function(e,t){t&&Zr(e)&&e.classList&&e.classList.add(t)},pc=function(e,t){t&&Zr(e)&&e.classList&&e.classList.remove(t)},uc=function(e,t){return!!(t&&Zr(e)&&e.classList)&&e.classList.contains(t)},fc=function(e,t,a){t&&Zr(e)&&e.setAttribute(t,a)},gc=function(e,t){t&&Zr(e)&&e.removeAttribute(t)},vc=function(e,t){return t&&Zr(e)?e.getAttribute(t):null},Ac=function(e,t){return t&&Zr(e)?e.hasAttribute(t):null},Pc=function(e,t,a){t&&Zr(e)&&(e.style[t]=a)},bc=function(e,t){t&&Zr(e)&&(e.style[t]="")},yc=function(e,t){return t&&Zr(e)&&e.style[t]||null},wc=function(e){return Zr(e)?e.getBoundingClientRect():null},Ic=function(e){var t=z.getComputedStyle;return t&&Zr(e)?t(e):{}},zc=function(){var e=z.getSelection;return e?z.getSelection():null},Cc=function(e){var t={top:0,left:0};if(!Zr(e)||0===e.getClientRects().length)return t;var a=wc(e);if(a){var o=e.ownerDocument.defaultView;t.top=a.top+o.pageYOffset,t.left=a.left+o.pageXOffset}return t},Dc=function(e){var t={top:0,left:0};if(!Zr(e))return t;var a={top:0,left:0},o=Ic(e);if("fixed"===o.position)t=wc(e)||t;else{t=Cc(e);var s=e.ownerDocument,i=e.offsetParent||s.documentElement;while(i&&(i===s.body||i===s.documentElement)&&"static"===Ic(i).position)i=i.parentNode;if(i&&i!==e&&i.nodeType===Node.ELEMENT_NODE){a=Cc(i);var n=Ic(i);a.top+=xr(n.borderTopWidth,0),a.left+=xr(n.borderLeftWidth,0)}}return{top:t.top-a.top-xr(o.marginTop,0),left:t.left-a.left-xr(o.marginLeft,0)}},Rc=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:document;return nc(qr,e).filter(oc).filter((function(e){return e.tabIndex>-1&&!e.disabled}))},Sc=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};try{e.focus(t)}catch(a){}return ac(e)},_c=function(e){try{e.blur()}catch(t){}return!ac(e)},kc=function(e){var t=Xe(null);return function(){for(var a=arguments.length,o=new Array(a),s=0;s1&&void 0!==arguments[1]?arguments[1]:void 0,a=Mc[x];return a?a.getConfigValue(e,t):bt(t)},Vc=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:null,a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:void 0;return t?Tc("".concat(e,".").concat(t),a):Tc(e,{})},xc=function(){return Tc("breakpoints",B)},Bc=kc((function(){return xc()})),Lc=function(){return bt(Bc())},Oc=kc((function(){var e=Lc();return e[0]="",e}));function Ec(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Uc(e){for(var t=1;t0&&void 0!==arguments[0]?arguments[0]:Ni,t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:void 0,a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:void 0,o=arguments.length>3&&void 0!==arguments[3]?arguments[3]:void 0,s=!0===a;return o=s?o:a,Uc(Uc(Uc({},e?{type:e}:{}),s?{required:s}:Te(t)?{}:{default:He(t)?function(){return t}:t}),Te(o)?{}:{validator:o})},Nc=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:yt;if(Fe(e))return e.map(t);var a={};for(var o in e)ot(e,o)&&(a[t(o)]=He(e[o])?it(e[o]):e[o]);return a},$c=function(e,t){var a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:yt;return(Fe(e)?e.slice():at(e)).reduce((function(e,o){return e[a(o)]=t[o],e}),{})},qc=function(e,t,a){return Uc(Uc({},bt(e)),{},{default:function(){var o=Vc(a,t,e.default);return Be(o)?o():o}})},Jc=function(e,t){return at(e).reduce((function(a,o){return Uc(Uc({},a),{},Fc({},o,qc(e[o],o,t)))}),{})},Kc=qc({},"","").default.name,Qc=function(e){return Be(e)&&e.name&&e.name!==Kc};function Yc(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var Xc=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{},a=t.type,o=void 0===a?Ni:a,s=t.defaultValue,i=void 0===s?void 0:s,n=t.validator,r=void 0===n?void 0:n,c=t.event,l=void 0===c?ci:c,h=Yc({},e,Wc(o,i,r)),d=Ms({model:{prop:e,event:l},props:h});return{mixin:d,props:h,prop:e,event:l}},Zc=function(e){return _?He(e)?e:{capture:!!e||!1}:!!(He(e)?e.capture:e)},el=function(e,t,a,o){e&&e.addEventListener&&e.addEventListener(t,a,Zc(o))},tl=function(e,t,a,o){e&&e.removeEventListener&&e.removeEventListener(t,a,Zc(o))},al=function(e){for(var t=e?el:tl,a=arguments.length,o=new Array(a>1?a-1:0),s=1;s1&&void 0!==arguments[1]?arguments[1]:{},a=t.preventDefault,o=void 0===a||a,s=t.propagation,i=void 0===s||s,n=t.immediatePropagation,r=void 0!==n&&n;o&&e.preventDefault(),i&&e.stopPropagation(),r&&e.stopImmediatePropagation()},sl=function(e){return Lr(e.replace(O,""))},il=function(e,t){return[Hi,sl(e),t].join(ji)},nl=function(e,t){return[Hi,t,sl(e)].join(ji)};function rl(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var cl=Jc({ariaLabel:Wc(Zi,"Close"),content:Wc(Zi,"×"),disabled:Wc(qi,!1),textVariant:Wc(Zi)},aa),ll=Ms({name:aa,functional:!0,props:cl,render:function(e,t){var a=t.props,o=t.data,s=t.slots,i=t.scopedSlots,n=s(),r=i||{},c={staticClass:"close",class:rl({},"text-".concat(a.textVariant),a.textVariant),attrs:{type:"button",disabled:a.disabled,"aria-label":a.ariaLabel?String(a.ariaLabel):null},on:{click:function(e){a.disabled&&We(e)&&ol(e)}}};return kr(wn,r,n)||(c.domProps={innerHTML:a.content}),e("button",bs(o,c),Mr(wn,{},r,n))}});function hl(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function dl(e){for(var t=1;t0?e:0)},Rl=function(e){return""===e||!0===e||!(Vr(e,0)<1)&&!!e},Sl=Jc(lt(Pl(Pl({},Il),{},{dismissLabel:Wc(Zi,"Close"),dismissible:Wc(qi,!1),fade:Wc(qi,!1),variant:Wc(Zi,"info")})),qt),_l=Ms({name:qt,mixins:[wl,Tr],props:Sl,data:function(){return{countDown:0,localShow:Rl(this[zl])}},watch:(pl={},bl(pl,zl,(function(e){this.countDown=Dl(e),this.localShow=Rl(e)})),bl(pl,"countDown",(function(e){var t=this;this.clearCountDownInterval();var a=this[zl];Ue(a)&&(this.$emit(Qs,e),a!==e&&this.$emit(Cl,e),e>0?(this.localShow=!0,this.$_countDownTimeout=setTimeout((function(){t.countDown--}),1e3)):this.$nextTick((function(){Qr((function(){t.localShow=!1}))})))})),bl(pl,"localShow",(function(e){var t=this[zl];e||!this.dismissible&&!Ue(t)||this.$emit(Ks),Ue(t)||t===e||this.$emit(Cl,e)})),pl),created:function(){this.$_filterTimer=null;var e=this[zl];this.countDown=Dl(e),this.localShow=Rl(e)},beforeDestroy:function(){this.clearCountDownInterval()},methods:{dismiss:function(){this.clearCountDownInterval(),this.countDown=0,this.localShow=!1},clearCountDownInterval:function(){clearTimeout(this.$_countDownTimeout),this.$_countDownTimeout=null}},render:function(e){var t=e();if(this.localShow){var a=this.dismissible,o=this.variant,s=e();a&&(s=e(ll,{attrs:{"aria-label":this.dismissLabel},on:{click:this.dismiss}},[this.normalizeSlot(zn)])),t=e("div",{staticClass:"alert",class:bl({"alert-dismissible":a},"alert-".concat(o),o),attrs:{role:"alert","aria-live":"polite","aria-atomic":!0},key:this[Rs]},[s,this.normalizeSlot()])}return e(vl,{props:{noFade:!this.fade}},[t])}}),kl=Ft({components:{BAlert:_l}}),Ml=Math.min,Tl=Math.max,Vl=Math.abs,xl=Math.ceil,Bl=Math.floor,Ll=Math.pow,Ol=Math.round;function El(e,t){return Gl(e)||jl(e,t)||Fl(e,t)||Ul()}function Ul(){throw new TypeError("Invalid attempt to destructure non-iterable instance.\nIn order to be iterable, non-array objects must have a [Symbol.iterator]() method.")}function Fl(e,t){if(e){if("string"===typeof e)return Hl(e,t);var a=Object.prototype.toString.call(e).slice(8,-1);return"Object"===a&&e.constructor&&(a=e.constructor.name),"Map"===a||"Set"===a?Array.from(e):"Arguments"===a||/^(?:Ui|I)nt(?:8|16|32)(?:Clamped)?Array$/.test(a)?Hl(e,t):void 0}}function Hl(e,t){(null==t||t>e.length)&&(t=e.length);for(var a=0,o=new Array(t);a0&&void 0!==arguments[0]?arguments[0]:{},t=e.target,a=e.rel;return"_blank"===t&&Ve(a)?"noopener":a||null},ih=function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:{},t=e.href,a=e.to,o=arguments.length>1&&void 0!==arguments[1]?arguments[1]:Kl,s=arguments.length>2&&void 0!==arguments[2]?arguments[2]:"#",i=arguments.length>3&&void 0!==arguments[3]?arguments[3]:"/";if(t)return t;if(ah(o))return null;if(Oe(a))return a||i;if(je(a)&&(a.path||a.query||a.hash)){var n=jr(a.path),r=Zl(a.query),c=jr(a.hash);return c=c&&"#"!==c.charAt(0)?"#".concat(c):c,"".concat(n).concat(r).concat(c)||i}return s};function nh(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var rh={viewBox:"0 0 16 16",width:"1em",height:"1em",focusable:"false",role:"img","aria-label":"icon"},ch={width:null,height:null,focusable:null,role:null,"aria-label":null},lh={animation:Wc(Zi),content:Wc(Zi),flipH:Wc(qi,!1),flipV:Wc(qi,!1),fontScale:Wc(hn,1),rotate:Wc(hn,0),scale:Wc(hn,1),shiftH:Wc(hn,0),shiftV:Wc(hn,0),stacked:Wc(qi,!1),title:Wc(Zi),variant:Wc(Zi)},hh=Ms({name:to,functional:!0,props:lh,render:function(e,t){var a,o=t.data,s=t.props,i=t.children,n=s.animation,r=s.content,c=s.flipH,l=s.flipV,h=s.stacked,d=s.title,m=s.variant,p=Tl(xr(s.fontScale,1),0)||1,u=Tl(xr(s.scale,1),0)||1,f=xr(s.rotate,0),g=xr(s.shiftH,0),v=xr(s.shiftV,0),A=c||l||1!==u,P=A||f,b=g||v,y=!xe(r),w=[P?"translate(8 8)":null,A?"scale(".concat((c?-1:1)*u," ").concat((l?-1:1)*u,")"):null,f?"rotate(".concat(f,")"):null,P?"translate(-8 -8)":null].filter(yt),I=e("g",{attrs:{transform:w.join(" ")||null},domProps:y?{innerHTML:r||""}:{}},i);b&&(I=e("g",{attrs:{transform:"translate(".concat(16*g/16," ").concat(-16*v/16,")")}},[I])),h&&(I=e("g",[I]));var z=d?e("title",d):null,C=[z,I].filter(yt);return e("svg",bs({staticClass:"b-icon bi",class:(a={},nh(a,"text-".concat(m),m),nh(a,"b-icon-animation-".concat(n),n),a),attrs:rh,style:h?{}:{fontSize:1===p?null:"".concat(100*p,"%")}},o,h?{attrs:ch}:{},{attrs:{xmlns:h?null:"http://www.w3.org/2000/svg",fill:"currentColor"}}),C)}});function dh(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function mh(e){for(var t=1;t'),Ah=fh("AlarmFill",''),Ph=fh("AlignBottom",''),bh=fh("AlignCenter",''),yh=fh("AlignEnd",''),wh=fh("AlignMiddle",''),Ih=fh("AlignStart",''),zh=fh("AlignTop",''),Ch=fh("Alt",''),Dh=fh("App",''),Rh=fh("AppIndicator",''),Sh=fh("Archive",''),_h=fh("ArchiveFill",''),kh=fh("Arrow90degDown",''),Mh=fh("Arrow90degLeft",''),Th=fh("Arrow90degRight",''),Vh=fh("Arrow90degUp",''),xh=fh("ArrowBarDown",''),Bh=fh("ArrowBarLeft",''),Lh=fh("ArrowBarRight",''),Oh=fh("ArrowBarUp",''),Eh=fh("ArrowClockwise",''),Uh=fh("ArrowCounterclockwise",''),Fh=fh("ArrowDown",''),Hh=fh("ArrowDownCircle",''),jh=fh("ArrowDownCircleFill",''),Gh=fh("ArrowDownLeft",''),Wh=fh("ArrowDownLeftCircle",''),Nh=fh("ArrowDownLeftCircleFill",''),$h=fh("ArrowDownLeftSquare",''),qh=fh("ArrowDownLeftSquareFill",''),Jh=fh("ArrowDownRight",''),Kh=fh("ArrowDownRightCircle",''),Qh=fh("ArrowDownRightCircleFill",''),Yh=fh("ArrowDownRightSquare",''),Xh=fh("ArrowDownRightSquareFill",''),Zh=fh("ArrowDownShort",''),ed=fh("ArrowDownSquare",''),td=fh("ArrowDownSquareFill",''),ad=fh("ArrowDownUp",''),od=fh("ArrowLeft",''),sd=fh("ArrowLeftCircle",''),id=fh("ArrowLeftCircleFill",''),nd=fh("ArrowLeftRight",''),rd=fh("ArrowLeftShort",''),cd=fh("ArrowLeftSquare",''),ld=fh("ArrowLeftSquareFill",''),hd=fh("ArrowRepeat",''),dd=fh("ArrowReturnLeft",''),md=fh("ArrowReturnRight",''),pd=fh("ArrowRight",''),ud=fh("ArrowRightCircle",''),fd=fh("ArrowRightCircleFill",''),gd=fh("ArrowRightShort",''),vd=fh("ArrowRightSquare",''),Ad=fh("ArrowRightSquareFill",''),Pd=fh("ArrowUp",''),bd=fh("ArrowUpCircle",''),yd=fh("ArrowUpCircleFill",''),wd=fh("ArrowUpLeft",''),Id=fh("ArrowUpLeftCircle",''),zd=fh("ArrowUpLeftCircleFill",''),Cd=fh("ArrowUpLeftSquare",''),Dd=fh("ArrowUpLeftSquareFill",''),Rd=fh("ArrowUpRight",''),Sd=fh("ArrowUpRightCircle",''),_d=fh("ArrowUpRightCircleFill",''),kd=fh("ArrowUpRightSquare",''),Md=fh("ArrowUpRightSquareFill",''),Td=fh("ArrowUpShort",''),Vd=fh("ArrowUpSquare",''),xd=fh("ArrowUpSquareFill",''),Bd=fh("ArrowsAngleContract",''),Ld=fh("ArrowsAngleExpand",''),Od=fh("ArrowsCollapse",''),Ed=fh("ArrowsExpand",''),Ud=fh("ArrowsFullscreen",''),Fd=fh("ArrowsMove",''),Hd=fh("AspectRatio",''),jd=fh("AspectRatioFill",''),Gd=fh("Asterisk",''),Wd=fh("At",''),Nd=fh("Award",''),$d=fh("AwardFill",''),qd=fh("Back",''),Jd=fh("Backspace",''),Kd=fh("BackspaceFill",''),Qd=fh("BackspaceReverse",''),Yd=fh("BackspaceReverseFill",''),Xd=fh("Badge3d",''),Zd=fh("Badge3dFill",''),em=fh("Badge4k",''),tm=fh("Badge4kFill",''),am=fh("Badge8k",''),om=fh("Badge8kFill",''),sm=fh("BadgeAd",''),im=fh("BadgeAdFill",''),nm=fh("BadgeAr",''),rm=fh("BadgeArFill",''),cm=fh("BadgeCc",''),lm=fh("BadgeCcFill",''),hm=fh("BadgeHd",''),dm=fh("BadgeHdFill",''),mm=fh("BadgeTm",''),pm=fh("BadgeTmFill",''),um=fh("BadgeVo",''),fm=fh("BadgeVoFill",''),gm=fh("BadgeVr",''),vm=fh("BadgeVrFill",''),Am=fh("BadgeWc",''),Pm=fh("BadgeWcFill",''),bm=fh("Bag",''),ym=fh("BagCheck",''),wm=fh("BagCheckFill",''),Im=fh("BagDash",''),zm=fh("BagDashFill",''),Cm=fh("BagFill",''),Dm=fh("BagPlus",''),Rm=fh("BagPlusFill",''),Sm=fh("BagX",''),_m=fh("BagXFill",''),km=fh("Bank",''),Mm=fh("Bank2",''),Tm=fh("BarChart",''),Vm=fh("BarChartFill",''),xm=fh("BarChartLine",''),Bm=fh("BarChartLineFill",''),Lm=fh("BarChartSteps",''),Om=fh("Basket",''),Em=fh("Basket2",''),Um=fh("Basket2Fill",''),Fm=fh("Basket3",''),Hm=fh("Basket3Fill",''),jm=fh("BasketFill",''),Gm=fh("Battery",''),Wm=fh("BatteryCharging",''),Nm=fh("BatteryFull",''),$m=fh("BatteryHalf",''),qm=fh("Bell",''),Jm=fh("BellFill",''),Km=fh("BellSlash",''),Qm=fh("BellSlashFill",''),Ym=fh("Bezier",''),Xm=fh("Bezier2",''),Zm=fh("Bicycle",''),ep=fh("Binoculars",''),tp=fh("BinocularsFill",''),ap=fh("BlockquoteLeft",''),op=fh("BlockquoteRight",''),sp=fh("Book",''),ip=fh("BookFill",''),np=fh("BookHalf",''),rp=fh("Bookmark",''),cp=fh("BookmarkCheck",''),lp=fh("BookmarkCheckFill",''),hp=fh("BookmarkDash",''),dp=fh("BookmarkDashFill",''),mp=fh("BookmarkFill",''),pp=fh("BookmarkHeart",''),up=fh("BookmarkHeartFill",''),fp=fh("BookmarkPlus",''),gp=fh("BookmarkPlusFill",''),vp=fh("BookmarkStar",''),Ap=fh("BookmarkStarFill",''),Pp=fh("BookmarkX",''),bp=fh("BookmarkXFill",''),yp=fh("Bookmarks",''),wp=fh("BookmarksFill",''),Ip=fh("Bookshelf",''),zp=fh("Bootstrap",''),Cp=fh("BootstrapFill",''),Dp=fh("BootstrapReboot",''),Rp=fh("Border",''),Sp=fh("BorderAll",''),_p=fh("BorderBottom",''),kp=fh("BorderCenter",''),Mp=fh("BorderInner",''),Tp=fh("BorderLeft",''),Vp=fh("BorderMiddle",''),xp=fh("BorderOuter",''),Bp=fh("BorderRight",''),Lp=fh("BorderStyle",''),Op=fh("BorderTop",''),Ep=fh("BorderWidth",''),Up=fh("BoundingBox",''),Fp=fh("BoundingBoxCircles",''),Hp=fh("Box",''),jp=fh("BoxArrowDown",''),Gp=fh("BoxArrowDownLeft",''),Wp=fh("BoxArrowDownRight",''),Np=fh("BoxArrowInDown",''),$p=fh("BoxArrowInDownLeft",''),qp=fh("BoxArrowInDownRight",''),Jp=fh("BoxArrowInLeft",''),Kp=fh("BoxArrowInRight",''),Qp=fh("BoxArrowInUp",''),Yp=fh("BoxArrowInUpLeft",''),Xp=fh("BoxArrowInUpRight",''),Zp=fh("BoxArrowLeft",''),eu=fh("BoxArrowRight",''),tu=fh("BoxArrowUp",''),au=fh("BoxArrowUpLeft",''),ou=fh("BoxArrowUpRight",''),su=fh("BoxSeam",''),iu=fh("Braces",''),nu=fh("Bricks",''),ru=fh("Briefcase",''),cu=fh("BriefcaseFill",''),lu=fh("BrightnessAltHigh",''),hu=fh("BrightnessAltHighFill",''),du=fh("BrightnessAltLow",''),mu=fh("BrightnessAltLowFill",''),pu=fh("BrightnessHigh",''),uu=fh("BrightnessHighFill",''),fu=fh("BrightnessLow",''),gu=fh("BrightnessLowFill",''),vu=fh("Broadcast",''),Au=fh("BroadcastPin",''),Pu=fh("Brush",''),bu=fh("BrushFill",''),yu=fh("Bucket",''),wu=fh("BucketFill",''),Iu=fh("Bug",''),zu=fh("BugFill",''),Cu=fh("Building",''),Du=fh("Bullseye",''),Ru=fh("Calculator",''),Su=fh("CalculatorFill",''),_u=fh("Calendar",''),ku=fh("Calendar2",''),Mu=fh("Calendar2Check",''),Tu=fh("Calendar2CheckFill",''),Vu=fh("Calendar2Date",''),xu=fh("Calendar2DateFill",''),Bu=fh("Calendar2Day",''),Lu=fh("Calendar2DayFill",''),Ou=fh("Calendar2Event",''),Eu=fh("Calendar2EventFill",''),Uu=fh("Calendar2Fill",''),Fu=fh("Calendar2Minus",''),Hu=fh("Calendar2MinusFill",''),ju=fh("Calendar2Month",''),Gu=fh("Calendar2MonthFill",''),Wu=fh("Calendar2Plus",''),Nu=fh("Calendar2PlusFill",''),$u=fh("Calendar2Range",''),qu=fh("Calendar2RangeFill",''),Ju=fh("Calendar2Week",''),Ku=fh("Calendar2WeekFill",''),Qu=fh("Calendar2X",''),Yu=fh("Calendar2XFill",''),Xu=fh("Calendar3",''),Zu=fh("Calendar3Event",''),ef=fh("Calendar3EventFill",''),tf=fh("Calendar3Fill",''),af=fh("Calendar3Range",''),of=fh("Calendar3RangeFill",''),sf=fh("Calendar3Week",''),nf=fh("Calendar3WeekFill",''),rf=fh("Calendar4",''),cf=fh("Calendar4Event",''),lf=fh("Calendar4Range",''),hf=fh("Calendar4Week",''),df=fh("CalendarCheck",''),mf=fh("CalendarCheckFill",''),pf=fh("CalendarDate",''),uf=fh("CalendarDateFill",''),ff=fh("CalendarDay",''),gf=fh("CalendarDayFill",''),vf=fh("CalendarEvent",''),Af=fh("CalendarEventFill",''),Pf=fh("CalendarFill",''),bf=fh("CalendarMinus",''),yf=fh("CalendarMinusFill",''),wf=fh("CalendarMonth",''),If=fh("CalendarMonthFill",''),zf=fh("CalendarPlus",''),Cf=fh("CalendarPlusFill",''),Df=fh("CalendarRange",''),Rf=fh("CalendarRangeFill",''),Sf=fh("CalendarWeek",''),_f=fh("CalendarWeekFill",''),kf=fh("CalendarX",''),Mf=fh("CalendarXFill",''),Tf=fh("Camera",''),Vf=fh("Camera2",''),xf=fh("CameraFill",''),Bf=fh("CameraReels",''),Lf=fh("CameraReelsFill",''),Of=fh("CameraVideo",''),Ef=fh("CameraVideoFill",''),Uf=fh("CameraVideoOff",''),Ff=fh("CameraVideoOffFill",''),Hf=fh("Capslock",''),jf=fh("CapslockFill",''),Gf=fh("CardChecklist",''),Wf=fh("CardHeading",''),Nf=fh("CardImage",''),$f=fh("CardList",''),qf=fh("CardText",''),Jf=fh("CaretDown",''),Kf=fh("CaretDownFill",''),Qf=fh("CaretDownSquare",''),Yf=fh("CaretDownSquareFill",''),Xf=fh("CaretLeft",''),Zf=fh("CaretLeftFill",''),eg=fh("CaretLeftSquare",''),tg=fh("CaretLeftSquareFill",''),ag=fh("CaretRight",''),og=fh("CaretRightFill",''),sg=fh("CaretRightSquare",''),ig=fh("CaretRightSquareFill",''),ng=fh("CaretUp",''),rg=fh("CaretUpFill",''),cg=fh("CaretUpSquare",''),lg=fh("CaretUpSquareFill",''),hg=fh("Cart",''),dg=fh("Cart2",''),mg=fh("Cart3",''),pg=fh("Cart4",''),ug=fh("CartCheck",''),fg=fh("CartCheckFill",''),gg=fh("CartDash",''),vg=fh("CartDashFill",''),Ag=fh("CartFill",''),Pg=fh("CartPlus",''),bg=fh("CartPlusFill",''),yg=fh("CartX",''),wg=fh("CartXFill",''),Ig=fh("Cash",''),zg=fh("CashCoin",''),Cg=fh("CashStack",''),Dg=fh("Cast",''),Rg=fh("Chat",''),Sg=fh("ChatDots",''),_g=fh("ChatDotsFill",''),kg=fh("ChatFill",''),Mg=fh("ChatLeft",''),Tg=fh("ChatLeftDots",''),Vg=fh("ChatLeftDotsFill",''),xg=fh("ChatLeftFill",''),Bg=fh("ChatLeftQuote",''),Lg=fh("ChatLeftQuoteFill",''),Og=fh("ChatLeftText",''),Eg=fh("ChatLeftTextFill",''),Ug=fh("ChatQuote",''),Fg=fh("ChatQuoteFill",''),Hg=fh("ChatRight",''),jg=fh("ChatRightDots",''),Gg=fh("ChatRightDotsFill",''),Wg=fh("ChatRightFill",''),Ng=fh("ChatRightQuote",''),$g=fh("ChatRightQuoteFill",''),qg=fh("ChatRightText",''),Jg=fh("ChatRightTextFill",''),Kg=fh("ChatSquare",''),Qg=fh("ChatSquareDots",''),Yg=fh("ChatSquareDotsFill",''),Xg=fh("ChatSquareFill",''),Zg=fh("ChatSquareQuote",''),ev=fh("ChatSquareQuoteFill",''),tv=fh("ChatSquareText",''),av=fh("ChatSquareTextFill",''),ov=fh("ChatText",''),sv=fh("ChatTextFill",''),iv=fh("Check",''),nv=fh("Check2",''),rv=fh("Check2All",''),cv=fh("Check2Circle",''),lv=fh("Check2Square",''),hv=fh("CheckAll",''),dv=fh("CheckCircle",''),mv=fh("CheckCircleFill",''),pv=fh("CheckLg",''),uv=fh("CheckSquare",''),fv=fh("CheckSquareFill",''),gv=fh("ChevronBarContract",''),vv=fh("ChevronBarDown",''),Av=fh("ChevronBarExpand",''),Pv=fh("ChevronBarLeft",''),bv=fh("ChevronBarRight",''),yv=fh("ChevronBarUp",''),wv=fh("ChevronCompactDown",''),Iv=fh("ChevronCompactLeft",''),zv=fh("ChevronCompactRight",''),Cv=fh("ChevronCompactUp",''),Dv=fh("ChevronContract",''),Rv=fh("ChevronDoubleDown",''),Sv=fh("ChevronDoubleLeft",''),_v=fh("ChevronDoubleRight",''),kv=fh("ChevronDoubleUp",''),Mv=fh("ChevronDown",''),Tv=fh("ChevronExpand",''),Vv=fh("ChevronLeft",''),xv=fh("ChevronRight",''),Bv=fh("ChevronUp",''),Lv=fh("Circle",''),Ov=fh("CircleFill",''),Ev=fh("CircleHalf",''),Uv=fh("CircleSquare",''),Fv=fh("Clipboard",''),Hv=fh("ClipboardCheck",''),jv=fh("ClipboardData",''),Gv=fh("ClipboardMinus",''),Wv=fh("ClipboardPlus",''),Nv=fh("ClipboardX",''),$v=fh("Clock",''),qv=fh("ClockFill",''),Jv=fh("ClockHistory",''),Kv=fh("Cloud",''),Qv=fh("CloudArrowDown",''),Yv=fh("CloudArrowDownFill",''),Xv=fh("CloudArrowUp",''),Zv=fh("CloudArrowUpFill",''),eA=fh("CloudCheck",''),tA=fh("CloudCheckFill",''),aA=fh("CloudDownload",''),oA=fh("CloudDownloadFill",''),sA=fh("CloudDrizzle",''),iA=fh("CloudDrizzleFill",''),nA=fh("CloudFill",''),rA=fh("CloudFog",''),cA=fh("CloudFog2",''),lA=fh("CloudFog2Fill",''),hA=fh("CloudFogFill",''),dA=fh("CloudHail",''),mA=fh("CloudHailFill",''),pA=fh("CloudHaze",''),uA=fh("CloudHaze1",''),fA=fh("CloudHaze2Fill",''),gA=fh("CloudHazeFill",''),vA=fh("CloudLightning",''),AA=fh("CloudLightningFill",''),PA=fh("CloudLightningRain",''),bA=fh("CloudLightningRainFill",''),yA=fh("CloudMinus",''),wA=fh("CloudMinusFill",''),IA=fh("CloudMoon",''),zA=fh("CloudMoonFill",''),CA=fh("CloudPlus",''),DA=fh("CloudPlusFill",''),RA=fh("CloudRain",''),SA=fh("CloudRainFill",''),_A=fh("CloudRainHeavy",''),kA=fh("CloudRainHeavyFill",''),MA=fh("CloudSlash",''),TA=fh("CloudSlashFill",''),VA=fh("CloudSleet",''),xA=fh("CloudSleetFill",''),BA=fh("CloudSnow",''),LA=fh("CloudSnowFill",''),OA=fh("CloudSun",''),EA=fh("CloudSunFill",''),UA=fh("CloudUpload",''),FA=fh("CloudUploadFill",''),HA=fh("Clouds",''),jA=fh("CloudsFill",''),GA=fh("Cloudy",''),WA=fh("CloudyFill",''),NA=fh("Code",''),$A=fh("CodeSlash",''),qA=fh("CodeSquare",''),JA=fh("Coin",''),KA=fh("Collection",''),QA=fh("CollectionFill",''),YA=fh("CollectionPlay",''),XA=fh("CollectionPlayFill",''),ZA=fh("Columns",''),eP=fh("ColumnsGap",''),tP=fh("Command",''),aP=fh("Compass",''),oP=fh("CompassFill",''),sP=fh("Cone",''),iP=fh("ConeStriped",''),nP=fh("Controller",''),rP=fh("Cpu",''),cP=fh("CpuFill",''),lP=fh("CreditCard",''),hP=fh("CreditCard2Back",''),dP=fh("CreditCard2BackFill",''),mP=fh("CreditCard2Front",''),pP=fh("CreditCard2FrontFill",''),uP=fh("CreditCardFill",''),fP=fh("Crop",''),gP=fh("Cup",''),vP=fh("CupFill",''),AP=fh("CupStraw",''),PP=fh("CurrencyBitcoin",''),bP=fh("CurrencyDollar",''),yP=fh("CurrencyEuro",''),wP=fh("CurrencyExchange",''),IP=fh("CurrencyPound",''),zP=fh("CurrencyYen",''),CP=fh("Cursor",''),DP=fh("CursorFill",''),RP=fh("CursorText",''),SP=fh("Dash",''),_P=fh("DashCircle",''),kP=fh("DashCircleDotted",''),MP=fh("DashCircleFill",''),TP=fh("DashLg",''),VP=fh("DashSquare",''),xP=fh("DashSquareDotted",''),BP=fh("DashSquareFill",''),LP=fh("Diagram2",''),OP=fh("Diagram2Fill",''),EP=fh("Diagram3",''),UP=fh("Diagram3Fill",''),FP=fh("Diamond",''),HP=fh("DiamondFill",''),jP=fh("DiamondHalf",''),GP=fh("Dice1",''),WP=fh("Dice1Fill",''),NP=fh("Dice2",''),$P=fh("Dice2Fill",''),qP=fh("Dice3",''),JP=fh("Dice3Fill",''),KP=fh("Dice4",''),QP=fh("Dice4Fill",''),YP=fh("Dice5",''),XP=fh("Dice5Fill",''),ZP=fh("Dice6",''),eb=fh("Dice6Fill",''),tb=fh("Disc",''),ab=fh("DiscFill",''),ob=fh("Discord",''),sb=fh("Display",''),ib=fh("DisplayFill",''),nb=fh("DistributeHorizontal",''),rb=fh("DistributeVertical",''),cb=fh("DoorClosed",''),lb=fh("DoorClosedFill",''),hb=fh("DoorOpen",''),db=fh("DoorOpenFill",''),mb=fh("Dot",''),pb=fh("Download",''),ub=fh("Droplet",''),fb=fh("DropletFill",''),gb=fh("DropletHalf",''),vb=fh("Earbuds",''),Ab=fh("Easel",''),Pb=fh("EaselFill",''),bb=fh("Egg",''),yb=fh("EggFill",''),wb=fh("EggFried",''),Ib=fh("Eject",''),zb=fh("EjectFill",''),Cb=fh("EmojiAngry",''),Db=fh("EmojiAngryFill",''),Rb=fh("EmojiDizzy",''),Sb=fh("EmojiDizzyFill",''),_b=fh("EmojiExpressionless",''),kb=fh("EmojiExpressionlessFill",''),Mb=fh("EmojiFrown",''),Tb=fh("EmojiFrownFill",''),Vb=fh("EmojiHeartEyes",''),xb=fh("EmojiHeartEyesFill",''),Bb=fh("EmojiLaughing",''),Lb=fh("EmojiLaughingFill",''),Ob=fh("EmojiNeutral",''),Eb=fh("EmojiNeutralFill",''),Ub=fh("EmojiSmile",''),Fb=fh("EmojiSmileFill",''),Hb=fh("EmojiSmileUpsideDown",''),jb=fh("EmojiSmileUpsideDownFill",''),Gb=fh("EmojiSunglasses",''),Wb=fh("EmojiSunglassesFill",''),Nb=fh("EmojiWink",''),$b=fh("EmojiWinkFill",''),qb=fh("Envelope",''),Jb=fh("EnvelopeFill",''),Kb=fh("EnvelopeOpen",''),Qb=fh("EnvelopeOpenFill",''),Yb=fh("Eraser",''),Xb=fh("EraserFill",''),Zb=fh("Exclamation",''),ey=fh("ExclamationCircle",''),ty=fh("ExclamationCircleFill",''),ay=fh("ExclamationDiamond",''),oy=fh("ExclamationDiamondFill",''),sy=fh("ExclamationLg",''),iy=fh("ExclamationOctagon",''),ny=fh("ExclamationOctagonFill",''),ry=fh("ExclamationSquare",''),cy=fh("ExclamationSquareFill",''),ly=fh("ExclamationTriangle",''),hy=fh("ExclamationTriangleFill",''),dy=fh("Exclude",''),my=fh("Eye",''),py=fh("EyeFill",''),uy=fh("EyeSlash",''),fy=fh("EyeSlashFill",''),gy=fh("Eyedropper",''),vy=fh("Eyeglasses",''),Ay=fh("Facebook",''),Py=fh("File",''),by=fh("FileArrowDown",''),yy=fh("FileArrowDownFill",''),wy=fh("FileArrowUp",''),Iy=fh("FileArrowUpFill",''),zy=fh("FileBarGraph",''),Cy=fh("FileBarGraphFill",''),Dy=fh("FileBinary",''),Ry=fh("FileBinaryFill",''),Sy=fh("FileBreak",''),_y=fh("FileBreakFill",''),ky=fh("FileCheck",''),My=fh("FileCheckFill",''),Ty=fh("FileCode",''),Vy=fh("FileCodeFill",''),xy=fh("FileDiff",''),By=fh("FileDiffFill",''),Ly=fh("FileEarmark",''),Oy=fh("FileEarmarkArrowDown",''),Ey=fh("FileEarmarkArrowDownFill",''),Uy=fh("FileEarmarkArrowUp",''),Fy=fh("FileEarmarkArrowUpFill",''),Hy=fh("FileEarmarkBarGraph",''),jy=fh("FileEarmarkBarGraphFill",''),Gy=fh("FileEarmarkBinary",''),Wy=fh("FileEarmarkBinaryFill",''),Ny=fh("FileEarmarkBreak",''),$y=fh("FileEarmarkBreakFill",''),qy=fh("FileEarmarkCheck",''),Jy=fh("FileEarmarkCheckFill",''),Ky=fh("FileEarmarkCode",''),Qy=fh("FileEarmarkCodeFill",''),Yy=fh("FileEarmarkDiff",''),Xy=fh("FileEarmarkDiffFill",''),Zy=fh("FileEarmarkEasel",''),ew=fh("FileEarmarkEaselFill",''),tw=fh("FileEarmarkExcel",''),aw=fh("FileEarmarkExcelFill",''),ow=fh("FileEarmarkFill",''),sw=fh("FileEarmarkFont",''),iw=fh("FileEarmarkFontFill",''),nw=fh("FileEarmarkImage",''),rw=fh("FileEarmarkImageFill",''),cw=fh("FileEarmarkLock",''),lw=fh("FileEarmarkLock2",''),hw=fh("FileEarmarkLock2Fill",''),dw=fh("FileEarmarkLockFill",''),mw=fh("FileEarmarkMedical",''),pw=fh("FileEarmarkMedicalFill",''),uw=fh("FileEarmarkMinus",''),fw=fh("FileEarmarkMinusFill",''),gw=fh("FileEarmarkMusic",''),vw=fh("FileEarmarkMusicFill",''),Aw=fh("FileEarmarkPdf",''),Pw=fh("FileEarmarkPdfFill",''),bw=fh("FileEarmarkPerson",''),yw=fh("FileEarmarkPersonFill",''),ww=fh("FileEarmarkPlay",''),Iw=fh("FileEarmarkPlayFill",''),zw=fh("FileEarmarkPlus",''),Cw=fh("FileEarmarkPlusFill",''),Dw=fh("FileEarmarkPost",''),Rw=fh("FileEarmarkPostFill",''),Sw=fh("FileEarmarkPpt",''),_w=fh("FileEarmarkPptFill",''),kw=fh("FileEarmarkRichtext",''),Mw=fh("FileEarmarkRichtextFill",''),Tw=fh("FileEarmarkRuled",''),Vw=fh("FileEarmarkRuledFill",''),xw=fh("FileEarmarkSlides",''),Bw=fh("FileEarmarkSlidesFill",''),Lw=fh("FileEarmarkSpreadsheet",''),Ow=fh("FileEarmarkSpreadsheetFill",''),Ew=fh("FileEarmarkText",''),Uw=fh("FileEarmarkTextFill",''),Fw=fh("FileEarmarkWord",''),Hw=fh("FileEarmarkWordFill",''),jw=fh("FileEarmarkX",''),Gw=fh("FileEarmarkXFill",''),Ww=fh("FileEarmarkZip",''),Nw=fh("FileEarmarkZipFill",''),$w=fh("FileEasel",''),qw=fh("FileEaselFill",''),Jw=fh("FileExcel",''),Kw=fh("FileExcelFill",''),Qw=fh("FileFill",''),Yw=fh("FileFont",''),Xw=fh("FileFontFill",''),Zw=fh("FileImage",''),eI=fh("FileImageFill",''),tI=fh("FileLock",''),aI=fh("FileLock2",''),oI=fh("FileLock2Fill",''),sI=fh("FileLockFill",''),iI=fh("FileMedical",''),nI=fh("FileMedicalFill",''),rI=fh("FileMinus",''),cI=fh("FileMinusFill",''),lI=fh("FileMusic",''),hI=fh("FileMusicFill",''),dI=fh("FilePdf",''),mI=fh("FilePdfFill",''),pI=fh("FilePerson",''),uI=fh("FilePersonFill",''),fI=fh("FilePlay",''),gI=fh("FilePlayFill",''),vI=fh("FilePlus",''),AI=fh("FilePlusFill",''),PI=fh("FilePost",''),bI=fh("FilePostFill",''),yI=fh("FilePpt",''),wI=fh("FilePptFill",''),II=fh("FileRichtext",''),zI=fh("FileRichtextFill",''),CI=fh("FileRuled",''),DI=fh("FileRuledFill",''),RI=fh("FileSlides",''),SI=fh("FileSlidesFill",''),_I=fh("FileSpreadsheet",''),kI=fh("FileSpreadsheetFill",''),MI=fh("FileText",''),TI=fh("FileTextFill",''),VI=fh("FileWord",''),xI=fh("FileWordFill",''),BI=fh("FileX",''),LI=fh("FileXFill",''),OI=fh("FileZip",''),EI=fh("FileZipFill",''),UI=fh("Files",''),FI=fh("FilesAlt",''),HI=fh("Film",''),jI=fh("Filter",''),GI=fh("FilterCircle",''),WI=fh("FilterCircleFill",''),NI=fh("FilterLeft",''),$I=fh("FilterRight",''),qI=fh("FilterSquare",''),JI=fh("FilterSquareFill",''),KI=fh("Flag",''),QI=fh("FlagFill",''),YI=fh("Flower1",''),XI=fh("Flower2",''),ZI=fh("Flower3",''),ez=fh("Folder",''),tz=fh("Folder2",''),az=fh("Folder2Open",''),oz=fh("FolderCheck",''),sz=fh("FolderFill",''),iz=fh("FolderMinus",''),nz=fh("FolderPlus",''),rz=fh("FolderSymlink",''),cz=fh("FolderSymlinkFill",''),lz=fh("FolderX",''),hz=fh("Fonts",''),dz=fh("Forward",''),mz=fh("ForwardFill",''),pz=fh("Front",''),uz=fh("Fullscreen",''),fz=fh("FullscreenExit",''),gz=fh("Funnel",''),vz=fh("FunnelFill",''),Az=fh("Gear",''),Pz=fh("GearFill",''),bz=fh("GearWide",''),yz=fh("GearWideConnected",''),wz=fh("Gem",''),Iz=fh("GenderAmbiguous",''),zz=fh("GenderFemale",''),Cz=fh("GenderMale",''),Dz=fh("GenderTrans",''),Rz=fh("Geo",''),Sz=fh("GeoAlt",''),_z=fh("GeoAltFill",''),kz=fh("GeoFill",''),Mz=fh("Gift",''),Tz=fh("GiftFill",''),Vz=fh("Github",''),xz=fh("Globe",''),Bz=fh("Globe2",''),Lz=fh("Google",''),Oz=fh("GraphDown",''),Ez=fh("GraphUp",''),Uz=fh("Grid",''),Fz=fh("Grid1x2",''),Hz=fh("Grid1x2Fill",''),jz=fh("Grid3x2",''),Gz=fh("Grid3x2Gap",''),Wz=fh("Grid3x2GapFill",''),Nz=fh("Grid3x3",''),$z=fh("Grid3x3Gap",''),qz=fh("Grid3x3GapFill",''),Jz=fh("GridFill",''),Kz=fh("GripHorizontal",''),Qz=fh("GripVertical",''),Yz=fh("Hammer",''),Xz=fh("HandIndex",''),Zz=fh("HandIndexFill",''),eC=fh("HandIndexThumb",''),tC=fh("HandIndexThumbFill",''),aC=fh("HandThumbsDown",''),oC=fh("HandThumbsDownFill",''),sC=fh("HandThumbsUp",''),iC=fh("HandThumbsUpFill",''),nC=fh("Handbag",''),rC=fh("HandbagFill",''),cC=fh("Hash",''),lC=fh("Hdd",''),hC=fh("HddFill",''),dC=fh("HddNetwork",''),mC=fh("HddNetworkFill",''),pC=fh("HddRack",''),uC=fh("HddRackFill",''),fC=fh("HddStack",''),gC=fh("HddStackFill",''),vC=fh("Headphones",''),AC=fh("Headset",''),PC=fh("HeadsetVr",''),bC=fh("Heart",''),yC=fh("HeartFill",''),wC=fh("HeartHalf",''),IC=fh("Heptagon",''),zC=fh("HeptagonFill",''),CC=fh("HeptagonHalf",''),DC=fh("Hexagon",''),RC=fh("HexagonFill",''),SC=fh("HexagonHalf",''),_C=fh("Hourglass",''),kC=fh("HourglassBottom",''),MC=fh("HourglassSplit",''),TC=fh("HourglassTop",''),VC=fh("House",''),xC=fh("HouseDoor",''),BC=fh("HouseDoorFill",''),LC=fh("HouseFill",''),OC=fh("Hr",''),EC=fh("Hurricane",''),UC=fh("Image",''),FC=fh("ImageAlt",''),HC=fh("ImageFill",''),jC=fh("Images",''),GC=fh("Inbox",''),WC=fh("InboxFill",''),NC=fh("Inboxes",''),$C=fh("InboxesFill",''),qC=fh("Info",''),JC=fh("InfoCircle",''),KC=fh("InfoCircleFill",''),QC=fh("InfoLg",''),YC=fh("InfoSquare",''),XC=fh("InfoSquareFill",''),ZC=fh("InputCursor",''),eD=fh("InputCursorText",''),tD=fh("Instagram",''),aD=fh("Intersect",''),oD=fh("Journal",''),sD=fh("JournalAlbum",''),iD=fh("JournalArrowDown",''),nD=fh("JournalArrowUp",''),rD=fh("JournalBookmark",''),cD=fh("JournalBookmarkFill",''),lD=fh("JournalCheck",''),hD=fh("JournalCode",''),dD=fh("JournalMedical",''),mD=fh("JournalMinus",''),pD=fh("JournalPlus",''),uD=fh("JournalRichtext",''),fD=fh("JournalText",''),gD=fh("JournalX",''),vD=fh("Journals",''),AD=fh("Joystick",''),PD=fh("Justify",''),bD=fh("JustifyLeft",''),yD=fh("JustifyRight",''),wD=fh("Kanban",''),ID=fh("KanbanFill",''),zD=fh("Key",''),CD=fh("KeyFill",''),DD=fh("Keyboard",''),RD=fh("KeyboardFill",''),SD=fh("Ladder",''),_D=fh("Lamp",''),kD=fh("LampFill",''),MD=fh("Laptop",''),TD=fh("LaptopFill",''),VD=fh("LayerBackward",''),xD=fh("LayerForward",''),BD=fh("Layers",''),LD=fh("LayersFill",''),OD=fh("LayersHalf",''),ED=fh("LayoutSidebar",''),UD=fh("LayoutSidebarInset",''),FD=fh("LayoutSidebarInsetReverse",''),HD=fh("LayoutSidebarReverse",''),jD=fh("LayoutSplit",''),GD=fh("LayoutTextSidebar",''),WD=fh("LayoutTextSidebarReverse",''),ND=fh("LayoutTextWindow",''),$D=fh("LayoutTextWindowReverse",''),qD=fh("LayoutThreeColumns",''),JD=fh("LayoutWtf",''),KD=fh("LifePreserver",''),QD=fh("Lightbulb",''),YD=fh("LightbulbFill",''),XD=fh("LightbulbOff",''),ZD=fh("LightbulbOffFill",''),eR=fh("Lightning",''),tR=fh("LightningCharge",''),aR=fh("LightningChargeFill",''),oR=fh("LightningFill",''),sR=fh("Link",''),iR=fh("Link45deg",''),nR=fh("Linkedin",''),rR=fh("List",''),cR=fh("ListCheck",''),lR=fh("ListNested",''),hR=fh("ListOl",''),dR=fh("ListStars",''),mR=fh("ListTask",''),pR=fh("ListUl",''),uR=fh("Lock",''),fR=fh("LockFill",''),gR=fh("Mailbox",''),vR=fh("Mailbox2",''),AR=fh("Map",''),PR=fh("MapFill",''),bR=fh("Markdown",''),yR=fh("MarkdownFill",''),wR=fh("Mask",''),IR=fh("Mastodon",''),zR=fh("Megaphone",''),CR=fh("MegaphoneFill",''),DR=fh("MenuApp",''),RR=fh("MenuAppFill",''),SR=fh("MenuButton",''),_R=fh("MenuButtonFill",''),kR=fh("MenuButtonWide",''),MR=fh("MenuButtonWideFill",''),TR=fh("MenuDown",''),VR=fh("MenuUp",''),xR=fh("Messenger",''),BR=fh("Mic",''),LR=fh("MicFill",''),OR=fh("MicMute",''),ER=fh("MicMuteFill",''),UR=fh("Minecart",''),FR=fh("MinecartLoaded",''),HR=fh("Moisture",''),jR=fh("Moon",''),GR=fh("MoonFill",''),WR=fh("MoonStars",''),NR=fh("MoonStarsFill",''),$R=fh("Mouse",''),qR=fh("Mouse2",''),JR=fh("Mouse2Fill",''),KR=fh("Mouse3",''),QR=fh("Mouse3Fill",''),YR=fh("MouseFill",''),XR=fh("MusicNote",''),ZR=fh("MusicNoteBeamed",''),eS=fh("MusicNoteList",''),tS=fh("MusicPlayer",''),aS=fh("MusicPlayerFill",''),oS=fh("Newspaper",''),sS=fh("NodeMinus",''),iS=fh("NodeMinusFill",''),nS=fh("NodePlus",''),rS=fh("NodePlusFill",''),cS=fh("Nut",''),lS=fh("NutFill",''),hS=fh("Octagon",''),dS=fh("OctagonFill",''),mS=fh("OctagonHalf",''),pS=fh("Option",''),uS=fh("Outlet",''),fS=fh("PaintBucket",''),gS=fh("Palette",''),vS=fh("Palette2",''),AS=fh("PaletteFill",''),PS=fh("Paperclip",''),bS=fh("Paragraph",''),yS=fh("PatchCheck",''),wS=fh("PatchCheckFill",''),IS=fh("PatchExclamation",''),zS=fh("PatchExclamationFill",''),CS=fh("PatchMinus",''),DS=fh("PatchMinusFill",''),RS=fh("PatchPlus",''),SS=fh("PatchPlusFill",''),_S=fh("PatchQuestion",''),kS=fh("PatchQuestionFill",''),MS=fh("Pause",''),TS=fh("PauseBtn",''),VS=fh("PauseBtnFill",''),xS=fh("PauseCircle",''),BS=fh("PauseCircleFill",''),LS=fh("PauseFill",''),OS=fh("Peace",''),ES=fh("PeaceFill",''),US=fh("Pen",''),FS=fh("PenFill",''),HS=fh("Pencil",''),jS=fh("PencilFill",''),GS=fh("PencilSquare",''),WS=fh("Pentagon",''),NS=fh("PentagonFill",''),$S=fh("PentagonHalf",''),qS=fh("People",''),JS=fh("PeopleFill",''),KS=fh("Percent",''),QS=fh("Person",''),YS=fh("PersonBadge",''),XS=fh("PersonBadgeFill",''),ZS=fh("PersonBoundingBox",''),e_=fh("PersonCheck",''),t_=fh("PersonCheckFill",''),a_=fh("PersonCircle",''),o_=fh("PersonDash",''),s_=fh("PersonDashFill",''),i_=fh("PersonFill",''),n_=fh("PersonLinesFill",''),r_=fh("PersonPlus",''),c_=fh("PersonPlusFill",''),l_=fh("PersonSquare",''),h_=fh("PersonX",''),d_=fh("PersonXFill",''),m_=fh("Phone",''),p_=fh("PhoneFill",''),u_=fh("PhoneLandscape",''),f_=fh("PhoneLandscapeFill",''),g_=fh("PhoneVibrate",''),v_=fh("PhoneVibrateFill",''),A_=fh("PieChart",''),P_=fh("PieChartFill",''),b_=fh("PiggyBank",''),y_=fh("PiggyBankFill",''),w_=fh("Pin",''),I_=fh("PinAngle",''),z_=fh("PinAngleFill",''),C_=fh("PinFill",''),D_=fh("PinMap",''),R_=fh("PinMapFill",''),S_=fh("Pip",''),__=fh("PipFill",''),k_=fh("Play",''),M_=fh("PlayBtn",''),T_=fh("PlayBtnFill",''),V_=fh("PlayCircle",''),x_=fh("PlayCircleFill",''),B_=fh("PlayFill",''),L_=fh("Plug",''),O_=fh("PlugFill",''),E_=fh("Plus",''),U_=fh("PlusCircle",''),F_=fh("PlusCircleDotted",''),H_=fh("PlusCircleFill",''),j_=fh("PlusLg",''),G_=fh("PlusSquare",''),W_=fh("PlusSquareDotted",''),N_=fh("PlusSquareFill",''),$_=fh("Power",''),q_=fh("Printer",''),J_=fh("PrinterFill",''),K_=fh("Puzzle",''),Q_=fh("PuzzleFill",''),Y_=fh("Question",''),X_=fh("QuestionCircle",''),Z_=fh("QuestionCircleFill",''),ek=fh("QuestionDiamond",''),tk=fh("QuestionDiamondFill",''),ak=fh("QuestionLg",''),ok=fh("QuestionOctagon",''),sk=fh("QuestionOctagonFill",''),ik=fh("QuestionSquare",''),nk=fh("QuestionSquareFill",''),rk=fh("Rainbow",''),ck=fh("Receipt",''),lk=fh("ReceiptCutoff",''),hk=fh("Reception0",''),dk=fh("Reception1",''),mk=fh("Reception2",''),pk=fh("Reception3",''),uk=fh("Reception4",''),fk=fh("Record",''),gk=fh("Record2",''),vk=fh("Record2Fill",''),Ak=fh("RecordBtn",''),Pk=fh("RecordBtnFill",''),bk=fh("RecordCircle",''),yk=fh("RecordCircleFill",''),wk=fh("RecordFill",''),Ik=fh("Recycle",''),zk=fh("Reddit",''),Ck=fh("Reply",''),Dk=fh("ReplyAll",''),Rk=fh("ReplyAllFill",''),Sk=fh("ReplyFill",''),_k=fh("Rss",''),kk=fh("RssFill",''),Mk=fh("Rulers",''),Tk=fh("Safe",''),Vk=fh("Safe2",''),xk=fh("Safe2Fill",''),Bk=fh("SafeFill",''),Lk=fh("Save",''),Ok=fh("Save2",''),Ek=fh("Save2Fill",''),Uk=fh("SaveFill",''),Fk=fh("Scissors",''),Hk=fh("Screwdriver",''),jk=fh("SdCard",''),Gk=fh("SdCardFill",''),Wk=fh("Search",''),Nk=fh("SegmentedNav",''),$k=fh("Server",''),qk=fh("Share",''),Jk=fh("ShareFill",''),Kk=fh("Shield",''),Qk=fh("ShieldCheck",''),Yk=fh("ShieldExclamation",''),Xk=fh("ShieldFill",''),Zk=fh("ShieldFillCheck",''),eM=fh("ShieldFillExclamation",''),tM=fh("ShieldFillMinus",''),aM=fh("ShieldFillPlus",''),oM=fh("ShieldFillX",''),sM=fh("ShieldLock",''),iM=fh("ShieldLockFill",''),nM=fh("ShieldMinus",''),rM=fh("ShieldPlus",''),cM=fh("ShieldShaded",''),lM=fh("ShieldSlash",''),hM=fh("ShieldSlashFill",''),dM=fh("ShieldX",''),mM=fh("Shift",''),pM=fh("ShiftFill",''),uM=fh("Shop",''),fM=fh("ShopWindow",''),gM=fh("Shuffle",''),vM=fh("Signpost",''),AM=fh("Signpost2",''),PM=fh("Signpost2Fill",''),bM=fh("SignpostFill",''),yM=fh("SignpostSplit",''),wM=fh("SignpostSplitFill",''),IM=fh("Sim",''),zM=fh("SimFill",''),CM=fh("SkipBackward",''),DM=fh("SkipBackwardBtn",''),RM=fh("SkipBackwardBtnFill",''),SM=fh("SkipBackwardCircle",''),_M=fh("SkipBackwardCircleFill",''),kM=fh("SkipBackwardFill",''),MM=fh("SkipEnd",''),TM=fh("SkipEndBtn",''),VM=fh("SkipEndBtnFill",''),xM=fh("SkipEndCircle",''),BM=fh("SkipEndCircleFill",''),LM=fh("SkipEndFill",''),OM=fh("SkipForward",''),EM=fh("SkipForwardBtn",''),UM=fh("SkipForwardBtnFill",''),FM=fh("SkipForwardCircle",''),HM=fh("SkipForwardCircleFill",''),jM=fh("SkipForwardFill",''),GM=fh("SkipStart",''),WM=fh("SkipStartBtn",''),NM=fh("SkipStartBtnFill",''),$M=fh("SkipStartCircle",''),qM=fh("SkipStartCircleFill",''),JM=fh("SkipStartFill",''),KM=fh("Skype",''),QM=fh("Slack",''),YM=fh("Slash",''),XM=fh("SlashCircle",''),ZM=fh("SlashCircleFill",''),eT=fh("SlashLg",''),tT=fh("SlashSquare",''),aT=fh("SlashSquareFill",''),oT=fh("Sliders",''),sT=fh("Smartwatch",''),iT=fh("Snow",''),nT=fh("Snow2",''),rT=fh("Snow3",''),cT=fh("SortAlphaDown",''),lT=fh("SortAlphaDownAlt",''),hT=fh("SortAlphaUp",''),dT=fh("SortAlphaUpAlt",''),mT=fh("SortDown",''),pT=fh("SortDownAlt",''),uT=fh("SortNumericDown",''),fT=fh("SortNumericDownAlt",''),gT=fh("SortNumericUp",''),vT=fh("SortNumericUpAlt",''),AT=fh("SortUp",''),PT=fh("SortUpAlt",''),bT=fh("Soundwave",''),yT=fh("Speaker",''),wT=fh("SpeakerFill",''),IT=fh("Speedometer",''),zT=fh("Speedometer2",''),CT=fh("Spellcheck",''),DT=fh("Square",''),RT=fh("SquareFill",''),ST=fh("SquareHalf",''),_T=fh("Stack",''),kT=fh("Star",''),MT=fh("StarFill",''),TT=fh("StarHalf",''),VT=fh("Stars",''),xT=fh("Stickies",''),BT=fh("StickiesFill",''),LT=fh("Sticky",''),OT=fh("StickyFill",''),ET=fh("Stop",''),UT=fh("StopBtn",''),FT=fh("StopBtnFill",''),HT=fh("StopCircle",''),jT=fh("StopCircleFill",''),GT=fh("StopFill",''),WT=fh("Stoplights",''),NT=fh("StoplightsFill",''),$T=fh("Stopwatch",''),qT=fh("StopwatchFill",''),JT=fh("Subtract",''),KT=fh("SuitClub",''),QT=fh("SuitClubFill",''),YT=fh("SuitDiamond",''),XT=fh("SuitDiamondFill",''),ZT=fh("SuitHeart",''),eV=fh("SuitHeartFill",''),tV=fh("SuitSpade",''),aV=fh("SuitSpadeFill",''),oV=fh("Sun",''),sV=fh("SunFill",''),iV=fh("Sunglasses",''),nV=fh("Sunrise",''),rV=fh("SunriseFill",''),cV=fh("Sunset",''),lV=fh("SunsetFill",''),hV=fh("SymmetryHorizontal",''),dV=fh("SymmetryVertical",''),mV=fh("Table",''),pV=fh("Tablet",''),uV=fh("TabletFill",''),fV=fh("TabletLandscape",''),gV=fh("TabletLandscapeFill",''),vV=fh("Tag",''),AV=fh("TagFill",''),PV=fh("Tags",''),bV=fh("TagsFill",''),yV=fh("Telegram",''),wV=fh("Telephone",''),IV=fh("TelephoneFill",''),zV=fh("TelephoneForward",''),CV=fh("TelephoneForwardFill",''),DV=fh("TelephoneInbound",''),RV=fh("TelephoneInboundFill",''),SV=fh("TelephoneMinus",''),_V=fh("TelephoneMinusFill",''),kV=fh("TelephoneOutbound",''),MV=fh("TelephoneOutboundFill",''),TV=fh("TelephonePlus",''),VV=fh("TelephonePlusFill",''),xV=fh("TelephoneX",''),BV=fh("TelephoneXFill",''),LV=fh("Terminal",''),OV=fh("TerminalFill",''),EV=fh("TextCenter",''),UV=fh("TextIndentLeft",''),FV=fh("TextIndentRight",''),HV=fh("TextLeft",''),jV=fh("TextParagraph",''),GV=fh("TextRight",''),WV=fh("Textarea",''),NV=fh("TextareaResize",''),$V=fh("TextareaT",''),qV=fh("Thermometer",''),JV=fh("ThermometerHalf",''),KV=fh("ThermometerHigh",''),QV=fh("ThermometerLow",''),YV=fh("ThermometerSnow",''),XV=fh("ThermometerSun",''),ZV=fh("ThreeDots",''),ex=fh("ThreeDotsVertical",''),tx=fh("Toggle2Off",''),ax=fh("Toggle2On",''),ox=fh("ToggleOff",''),sx=fh("ToggleOn",''),ix=fh("Toggles",''),nx=fh("Toggles2",''),rx=fh("Tools",''),cx=fh("Tornado",''),lx=fh("Translate",''),hx=fh("Trash",''),dx=fh("Trash2",''),mx=fh("Trash2Fill",''),px=fh("TrashFill",''),ux=fh("Tree",''),fx=fh("TreeFill",''),gx=fh("Triangle",''),vx=fh("TriangleFill",''),Ax=fh("TriangleHalf",''),Px=fh("Trophy",''),bx=fh("TrophyFill",''),yx=fh("TropicalStorm",''),wx=fh("Truck",''),Ix=fh("TruckFlatbed",''),zx=fh("Tsunami",''),Cx=fh("Tv",''),Dx=fh("TvFill",''),Rx=fh("Twitch",''),Sx=fh("Twitter",''),_x=fh("Type",''),kx=fh("TypeBold",''),Mx=fh("TypeH1",''),Tx=fh("TypeH2",''),Vx=fh("TypeH3",''),xx=fh("TypeItalic",''),Bx=fh("TypeStrikethrough",''),Lx=fh("TypeUnderline",''),Ox=fh("UiChecks",''),Ex=fh("UiChecksGrid",''),Ux=fh("UiRadios",''),Fx=fh("UiRadiosGrid",''),Hx=fh("Umbrella",''),jx=fh("UmbrellaFill",''),Gx=fh("Union",''),Wx=fh("Unlock",''),Nx=fh("UnlockFill",''),$x=fh("Upc",''),qx=fh("UpcScan",''),Jx=fh("Upload",''),Kx=fh("VectorPen",''),Qx=fh("ViewList",''),Yx=fh("ViewStacked",''),Xx=fh("Vinyl",''),Zx=fh("VinylFill",''),eB=fh("Voicemail",''),tB=fh("VolumeDown",''),aB=fh("VolumeDownFill",''),oB=fh("VolumeMute",''),sB=fh("VolumeMuteFill",''),iB=fh("VolumeOff",''),nB=fh("VolumeOffFill",''),rB=fh("VolumeUp",''),cB=fh("VolumeUpFill",''),lB=fh("Vr",''),hB=fh("Wallet",''),dB=fh("Wallet2",''),mB=fh("WalletFill",''),pB=fh("Watch",''),uB=fh("Water",''),fB=fh("Whatsapp",''),gB=fh("Wifi",''),vB=fh("Wifi1",''),AB=fh("Wifi2",''),PB=fh("WifiOff",''),bB=fh("Wind",''),yB=fh("Window",''),wB=fh("WindowDock",''),IB=fh("WindowSidebar",''),zB=fh("Wrench",''),CB=fh("X",''),DB=fh("XCircle",''),RB=fh("XCircleFill",''),SB=fh("XDiamond",''),_B=fh("XDiamondFill",''),kB=fh("XLg",''),MB=fh("XOctagon",''),TB=fh("XOctagonFill",''),VB=fh("XSquare",''),xB=fh("XSquareFill",''),BB=fh("Youtube",''),LB=fh("ZoomIn",''),OB=fh("ZoomOut",'');function EB(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function UB(e){for(var t=1;t1?a-1:0),s=1;se.length)&&(t=e.length);for(var a=0,o=new Array(t);a0&&void 0!==arguments[0]?arguments[0]:"";return String(e).replace(j,"")},yO=function(e,t){return e?{innerHTML:e}:t?{textContent:t}:{}};function wO(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function IO(e){for(var t=1;t-1&&(t=t.slice(0,a).reverse(),Sc(t[0]))},focusNext:function(e){var t=this.getItems(),a=t.indexOf(e.target);a>-1&&(t=t.slice(a+1),Sc(t[0]))},focusLast:function(){var e=this.getItems().reverse();Sc(e[0])},onFocusin:function(e){var t=this.$el;e.target!==t||hc(t,e.relatedTarget)||(ol(e),this.focusFirst(e))},onKeydown:function(e){var t=e.keyCode,a=e.shiftKey;t===oL||t===XB?(ol(e),a?this.focusFirst(e):this.focusPrev(e)):t!==qB&&t!==tL||(ol(e),a?this.focusLast(e):this.focusNext(e))}},render:function(e){var t=this.keyNav;return e("div",{staticClass:"btn-toolbar",class:{"justify-content-between":this.justify},attrs:{role:"toolbar",tabindex:t?"0":null},on:t?{focusin:this.onFocusin,keydown:this.onKeydown}:{}},[this.normalizeSlot()])}}),NO=Ft({components:{BButtonToolbar:WO,BBtnToolbar:WO}}),$O="gregory",qO="long",JO="narrow",KO="short",QO="2-digit",YO="numeric";function XO(e,t){return oE(e)||aE(e,t)||eE(e,t)||ZO()}function ZO(){throw new TypeError("Invalid attempt to destructure non-iterable instance.\nIn order to be iterable, non-array objects must have a [Symbol.iterator]() method.")}function eE(e,t){if(e){if("string"===typeof e)return tE(e,t);var a=Object.prototype.toString.call(e).slice(8,-1);return"Object"===a&&e.constructor&&(a=e.constructor.name),"Map"===a||"Set"===a?Array.from(e):"Arguments"===a||/^(?:Ui|I)nt(?:8|16|32)(?:Clamped)?Array$/.test(a)?tE(e,t):void 0}}function tE(e,t){(null==t||t>e.length)&&(t=e.length);for(var a=0,o=new Array(t);a1&&void 0!==arguments[1]?arguments[1]:$O;e=Dr(e).filter(yt);var a=new Intl.DateTimeFormat(e,{calendar:t});return a.resolvedOptions().locale},mE=function(e,t){var a=new Intl.DateTimeFormat(e,t);return a.format},pE=function(e,t){return hE(e)===hE(t)},uE=function(e){return e=cE(e),e.setDate(1),e},fE=function(e){return e=cE(e),e.setMonth(e.getMonth()+1),e.setDate(0),e},gE=function(e,t){e=cE(e);var a=e.getMonth();return e.setFullYear(e.getFullYear()+t),e.getMonth()!==a&&e.setDate(0),e},vE=function(e){e=cE(e);var t=e.getMonth();return e.setMonth(t-1),e.getMonth()===t&&e.setDate(0),e},AE=function(e){e=cE(e);var t=e.getMonth();return e.setMonth(t+1),e.getMonth()===(t+2)%12&&e.setDate(0),e},PE=function(e){return gE(e,-1)},bE=function(e){return gE(e,1)},yE=function(e){return gE(e,-10)},wE=function(e){return gE(e,10)},IE=function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:null,a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:null;return e=lE(e),t=lE(t)||e,a=lE(a)||e,e?ea?a:e:null},zE=["ar","az","ckb","fa","he","ks","lrc","mzn","ps","sd","te","ug","ur","yi"].map((function(e){return e.toLowerCase()})),CE=function(e){var t=jr(e).toLowerCase().replace(me,"").split("-"),a=t.slice(0,2).join("-"),o=t[0];return Cr(zE,a)||Cr(zE,o)},DE={id:Wc(Zi)},RE=Ms({props:DE,data:function(){return{localId_:null}},computed:{safeId:function(){var e=this.id||this.localId_,t=function(t){return e?(t=String(t||"").replace(/\s+/g,"_"),t?e+"_"+t:e):null};return t}},mounted:function(){var e=this;this.$nextTick((function(){e.localId_="__BVID__".concat(e[Rs])}))}});function SE(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function _E(e){for(var t=1;tt}},dateDisabled:function(){var e=this,t=this.dateOutOfRange;return function(a){a=lE(a);var o=hE(a);return!(!t(a)&&!e.computedDateDisabledFn(o,a))}},formatDateString:function(){return mE(this.calendarLocale,_E(_E({year:YO,month:QO,day:QO},this.dateFormatOptions),{},{hour:void 0,minute:void 0,second:void 0,calendar:$O}))},formatYearMonth:function(){return mE(this.calendarLocale,{year:YO,month:qO,calendar:$O})},formatWeekdayName:function(){return mE(this.calendarLocale,{weekday:qO,calendar:$O})},formatWeekdayNameShort:function(){return mE(this.calendarLocale,{weekday:this.weekdayHeaderFormat||KO,calendar:$O})},formatDay:function(){var e=new Intl.NumberFormat([this.computedLocale],{style:"decimal",minimumIntegerDigits:1,minimumFractionDigits:0,maximumFractionDigits:0,notation:"standard"});return function(t){return e.format(t.getDate())}},prevDecadeDisabled:function(){var e=this.computedMin;return this.disabled||e&&fE(yE(this.activeDate))e},nextYearDisabled:function(){var e=this.computedMax;return this.disabled||e&&uE(bE(this.activeDate))>e},nextDecadeDisabled:function(){var e=this.computedMax;return this.disabled||e&&uE(wE(this.activeDate))>e},calendar:function(){for(var e=[],t=this.calendarFirstDay,a=t.getFullYear(),o=t.getMonth(),s=this.calendarDaysInMonth,i=t.getDay(),n=(this.computedWeekStarts>i?7:0)-this.computedWeekStarts,r=0-n-i,c=0;c<6&&r0);a!==this.visible&&(this.visible=a,this.callback(a),this.once&&this.visible&&(this.doneOnce=!0,this.stop()))}},{key:"stop",value:function(){this.observer&&this.observer.disconnect(),this.observer=null}}]),e}(),RU=function(e){var t=e[CU];t&&t.stop&&t.stop(),delete e[CU]},SU=function(e,t){var a=t.value,o=t.modifiers,s={margin:"0px",once:!1,callback:a};at(o).forEach((function(e){E.test(e)?s.margin="".concat(e,"px"):"once"===e.toLowerCase()&&(s.once=!0)})),RU(e),e[CU]=new DU(e,s),e[CU]._prevModifiers=it(o)},_U=function(e,t,a){var o=t.value,s=t.oldValue,i=t.modifiers;i=it(i),!e||o===s&&e[CU]&&iL(i,e[CU]._prevModifiers)||SU(e,{value:o,modifiers:i},a)},kU=function(e){RU(e)},MU={bind:SU,componentUpdated:_U,unbind:kU};function TU(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function VU(e){for(var t=1;t0||s.removedNodes.length>0))&&(a=!0)}a&&t()}));return o.observe(e,XU({childList:!0,subtree:!0},a)),o};function aF(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function oF(e){for(var t=1;t0),touchStartX:0,touchDeltaX:0}},computed:{numSlides:function(){return this.slides.length}},watch:(eF={},sF(eF,cF,(function(e,t){e!==t&&this.setSlide(Vr(e,0))})),sF(eF,"interval",(function(e,t){e!==t&&(e?(this.pause(!0),this.start(!1)):this.pause(!1))})),sF(eF,"isPaused",(function(e,t){e!==t&&this.$emit(e?gi:Li)})),sF(eF,"index",(function(e,t){e===t||this.isSliding||this.doSlide(e,t)})),eF),created:function(){this.$_interval=null,this.$_animationTimeout=null,this.$_touchTimeout=null,this.$_observer=null,this.isPaused=!(Vr(this.interval,0)>0)},mounted:function(){this.transitionEndEvent=gF(this.$el)||null,this.updateSlides(),this.setObserver(!0)},beforeDestroy:function(){this.clearInterval(),this.clearAnimationTimeout(),this.clearTouchTimeout(),this.setObserver(!1)},methods:{clearInterval:function(e){function t(){return e.apply(this,arguments)}return t.toString=function(){return e.toString()},t}((function(){clearInterval(this.$_interval),this.$_interval=null})),clearAnimationTimeout:function(){clearTimeout(this.$_animationTimeout),this.$_animationTimeout=null},clearTouchTimeout:function(){clearTimeout(this.$_touchTimeout),this.$_touchTimeout=null},setObserver:function(){var e=arguments.length>0&&void 0!==arguments[0]&&arguments[0];this.$_observer&&this.$_observer.disconnect(),this.$_observer=null,e&&(this.$_observer=tF(this.$refs.inner,this.updateSlides.bind(this),{subtree:!1,childList:!0,attributes:!0,attributeFilter:["id"]}))},setSlide:function(e){var t=this,a=arguments.length>1&&void 0!==arguments[1]?arguments[1]:null;if(!(I&&document.visibilityState&&document.hidden)){var o=this.noWrap,s=this.numSlides;e=Bl(e),0!==s&&(this.isSliding?this.$once(Mi,(function(){Qr((function(){return t.setSlide(e,a)}))})):(this.direction=a,this.index=e>=s?o?s-1:0:e<0?o?0:s-1:e,o&&this.index!==e&&this.index!==this[cF]&&this.$emit(lF,this.index)))}},prev:function(){this.setSlide(this.index-1,"prev")},next:function(){this.setSlide(this.index+1,"next")},pause:function(e){e||(this.isPaused=!0),this.clearInterval()},start:function(e){e||(this.isPaused=!1),this.clearInterval(),this.interval&&this.numSlides>1&&(this.$_interval=setInterval(this.next,Tl(1e3,this.interval)))},restart:function(){this.$el.contains(ec())||this.start()},doSlide:function(e,t){var a=this,o=Boolean(this.interval),s=this.calcDirection(this.direction,t,e),i=s.overlayClass,n=s.dirClass,r=this.slides[t],c=this.slides[e];if(r&&c){if(this.isSliding=!0,o&&this.pause(!1),this.$emit(Ti,e),this.$emit(lF,this.index),this.noAnimation)mc(c,"active"),pc(r,"active"),this.isSliding=!1,this.$nextTick((function(){return a.$emit(Mi,e)}));else{mc(c,i),ic(c),mc(r,n),mc(c,n);var l=!1,h=function t(){if(!l){if(l=!0,a.transitionEndEvent){var o=a.transitionEndEvent.split(/\s+/);o.forEach((function(e){return tl(c,e,t,Wi)}))}a.clearAnimationTimeout(),pc(c,n),pc(c,i),mc(c,"active"),pc(r,"active"),pc(r,n),pc(r,i),fc(r,"aria-current","false"),fc(c,"aria-current","true"),fc(r,"aria-hidden","true"),fc(c,"aria-hidden","false"),a.isSliding=!1,a.direction=null,a.$nextTick((function(){return a.$emit(Mi,e)}))}};if(this.transitionEndEvent){var d=this.transitionEndEvent.split(/\s+/);d.forEach((function(e){return el(c,e,h,Wi)}))}this.$_animationTimeout=setTimeout(h,dF)}o&&this.start(!1)}},updateSlides:function(){this.pause(!0),this.slides=nc(".carousel-item",this.$refs.inner);var e=this.slides.length,t=Tl(0,Ml(Bl(this.index),e-1));this.slides.forEach((function(a,o){var s=o+1;o===t?(mc(a,"active"),fc(a,"aria-current","true")):(pc(a,"active"),fc(a,"aria-current","false")),fc(a,"aria-posinset",String(s)),fc(a,"aria-setsize",String(e))})),this.setSlide(t),this.start(this.isPaused)},calcDirection:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:null,t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:0,a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:0;return e?hF[e]:a>t?hF.next:hF.prev},handleClick:function(e,t){var a=e.keyCode;"click"!==e.type&&a!==aL&&a!==KB||(ol(e),t())},handleSwipe:function(){var e=Vl(this.touchDeltaX);if(!(e<=pF)){var t=e/this.touchDeltaX;this.touchDeltaX=0,t>0?this.prev():t<0&&this.next()}},touchStart:function(e){M&&uF[e.pointerType.toUpperCase()]?this.touchStartX=e.clientX:M||(this.touchStartX=e.touches[0].clientX)},touchMove:function(e){e.touches&&e.touches.length>1?this.touchDeltaX=0:this.touchDeltaX=e.touches[0].clientX-this.touchStartX},touchEnd:function(e){M&&uF[e.pointerType.toUpperCase()]&&(this.touchDeltaX=e.clientX-this.touchStartX),this.handleSwipe(),this.pause(!1),this.clearTouchTimeout(),this.$_touchTimeout=setTimeout(this.start,mF+Tl(1e3,this.interval))}},render:function(e){var t=this,a=this.indicators,o=this.background,s=this.noAnimation,i=this.noHoverPause,n=this.noTouch,r=this.index,c=this.isSliding,l=this.pause,h=this.restart,d=this.touchStart,m=this.touchEnd,p=this.safeId("__BV_inner_"),u=e("div",{staticClass:"carousel-inner",attrs:{id:p,role:"list"},ref:"inner"},[this.normalizeSlot()]),f=e();if(this.controls){var g=function(a,o,s){var i=function(e){c?ol(e,{propagation:!1}):t.handleClick(e,s)};return e("a",{staticClass:"carousel-control-".concat(a),attrs:{href:"#",role:"button","aria-controls":p,"aria-disabled":c?"true":null},on:{click:i,keydown:i}},[e("span",{staticClass:"carousel-control-".concat(a,"-icon"),attrs:{"aria-hidden":"true"}}),e("span",{class:"sr-only"},[o])])};f=[g("prev",this.labelPrev,this.prev),g("next",this.labelNext,this.next)]}var v=e("ol",{staticClass:"carousel-indicators",directives:[{name:"show",value:a}],attrs:{id:this.safeId("__BV_indicators_"),"aria-hidden":a?"false":"true","aria-label":this.labelIndicators,"aria-owns":p}},this.slides.map((function(o,s){var i=function(e){t.handleClick(e,(function(){t.setSlide(s)}))};return e("li",{class:{active:s===r},attrs:{role:"button",id:t.safeId("__BV_indicator_".concat(s+1,"_")),tabindex:a?"0":"-1","aria-current":s===r?"true":"false","aria-label":"".concat(t.labelGotoSlide," ").concat(s+1),"aria-describedby":o.id||null,"aria-controls":p},on:{click:i,keydown:i},key:"slide_".concat(s)})}))),A={mouseenter:i?QU:l,mouseleave:i?QU:h,focusin:l,focusout:h,keydown:function(e){if(!/input|textarea/i.test(e.target.tagName)){var a=e.keyCode;a!==XB&&a!==tL||(ol(e),t[a===XB?"prev":"next"]())}}};return k&&!n&&(M?(A["&pointerdown"]=d,A["&pointerup"]=m):(A["&touchstart"]=d,A["&touchmove"]=this.touchMove,A["&touchend"]=m)),e("div",{staticClass:"carousel",class:{slide:!s,"carousel-fade":!s&&this.fade,"pointer-event":k&&M&&!n},style:{background:o},attrs:{role:"region",id:this.safeId(),"aria-busy":c?"true":"false"},on:A},[u,f,v])}});function PF(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function bF(e){for(var t=1;t0?(fc(e,rH,o.join(" ")),Pc(e,dH,"none")):(gc(e,rH),bc(e,dH)),Qr((function(){bH(e,YF(a,t))})),iL(o,e[sH])||(e[sH]=o,o.forEach((function(e){gL(YF(a,t)).$emit(fH,e)})))}},DH={bind:function(e,t,a){e[oH]=!1,e[sH]=[],wH(e,YF(a,t)),CH(e,t,a)},componentUpdated:CH,updated:CH,unbind:function(e,t,a){PH(e),yH(e,YF(a,t)),zH(e,tH),zH(e,aH),zH(e,oH),zH(e,sH),pc(e,XF),pc(e,ZF),gc(e,cH),gc(e,rH),gc(e,lH),bc(e,dH)}},RH=Ft({directives:{VBToggle:DH}}),SH=Ft({components:{BCollapse:QF},plugins:{VBTogglePlugin:RH}}),_H=a("f0bd"),kH="top-start",MH="top-end",TH="bottom-start",VH="bottom-end",xH="right-start",BH="left-start";function LH(e,t){if(!(e instanceof t))throw new TypeError("Cannot call a class as a function")}function OH(e,t){for(var a=0;a1&&void 0!==arguments[1]?arguments[1]:{};if(LH(this,e),!t)throw new TypeError("Failed to construct '".concat(this.constructor.name,"'. 1 argument required, ").concat(arguments.length," given."));Ye(this,e.Defaults,this.constructor.Defaults,a,{type:t}),Ze(this,{type:ht(),cancelable:ht(),nativeEvent:ht(),target:ht(),relatedTarget:ht(),vueTarget:ht(),componentId:ht()});var o=!1;this.preventDefault=function(){this.cancelable&&(o=!0)},et(this,"defaultPrevented",{enumerable:!0,get:function(){return o}})}return EH(e,null,[{key:"Defaults",get:function(){return{type:"",cancelable:!0,nativeEvent:null,target:null,relatedTarget:null,vueTarget:null,componentId:null}}}]),e}(),FH=Ms({data:function(){return{listenForClickOut:!1}},watch:{listenForClickOut:function(e,t){e!==t&&(tl(this.clickOutElement,this.clickOutEventName,this._clickOutHandler,Wi),e&&el(this.clickOutElement,this.clickOutEventName,this._clickOutHandler,Wi))}},beforeCreate:function(){this.clickOutElement=null,this.clickOutEventName=null},mounted:function(){this.clickOutElement||(this.clickOutElement=document),this.clickOutEventName||(this.clickOutEventName="click"),this.listenForClickOut&&el(this.clickOutElement,this.clickOutEventName,this._clickOutHandler,Wi)},beforeDestroy:function(){tl(this.clickOutElement,this.clickOutEventName,this._clickOutHandler,Wi)},methods:{isClickOut:function(e){return!hc(this.$el,e.target)},_clickOutHandler:function(e){this.clickOutHandler&&this.isClickOut(e)&&this.clickOutHandler(e)}}}),HH=Ms({data:function(){return{listenForFocusIn:!1}},watch:{listenForFocusIn:function(e,t){e!==t&&(tl(this.focusInElement,"focusin",this._focusInHandler,Wi),e&&el(this.focusInElement,"focusin",this._focusInHandler,Wi))}},beforeCreate:function(){this.focusInElement=null},mounted:function(){this.focusInElement||(this.focusInElement=document),this.listenForFocusIn&&el(this.focusInElement,"focusin",this._focusInHandler,Wi)},beforeDestroy:function(){tl(this.focusInElement,"focusin",this._focusInHandler,Wi)},methods:{_focusInHandler:function(e){this.focusInHandler&&this.focusInHandler(e)}}}),jH=null;Ss&&(jH=new WeakMap);var GH=function(e,t){Ss&&jH.set(e,t)},WH=function(e){Ss&&jH.delete(e)},NH=function(e){if(!Ss)return e.__vue__;var t=e;while(t){if(jH.has(t))return jH.get(t);t=t.parentNode}return null};function $H(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function qH(e){for(var t=1;t0&&void 0!==arguments[0]&&arguments[0];this.disabled||(this.visible=!1,e&&this.$once(ii,this.focusToggler))},toggle:function(e){e=e||{};var t=e,a=t.type,o=t.keyCode;("click"===a||"keydown"===a&&-1!==[KB,aL,qB].indexOf(o))&&(this.disabled?this.visible=!1:(this.$emit(Bi,e),ol(e),this.visible?this.hide(!0):this.show()))},onMousedown:function(e){ol(e,{propagation:!1})},onKeydown:function(e){var t=e.keyCode;t===QB?this.onEsc(e):t===qB?this.focusNext(e,!1):t===oL&&this.focusNext(e,!0)},onEsc:function(e){this.visible&&(this.visible=!1,ol(e),this.$once(ii,this.focusToggler))},onSplitClick:function(e){this.disabled?this.visible=!1:this.$emit(js,e)},hideHandler:function(e){var t=this,a=e.target;!this.visible||hc(this.$refs.menu,a)||hc(this.toggler,a)||(this.clearHideTimeout(),this.$_hideTimeout=setTimeout((function(){return t.hide()}),this.hideDelay))},clickOutHandler:function(e){this.hideHandler(e)},focusInHandler:function(e){this.hideHandler(e)},focusNext:function(e,t){var a=this,o=e.target;!this.visible||e&&lc(YH,o)||(ol(e),this.$nextTick((function(){var e=a.getItems();if(!(e.length<1)){var s=e.indexOf(o);t&&s>0?s--:!t&&s1&&void 0!==arguments[1]?arguments[1]:null;if(je(e)){var a=It(e,this.valueField),o=It(e,this.textField);return{value:Te(a)?t||o:a,text:bO(String(Te(o)?t:o)),html:It(e,this.htmlField),disabled:Boolean(It(e,this.disabledField))}}return{value:t||e,text:bO(String(e)),disabled:!1}},normalizeOptions:function(e){var t=this;return Fe(e)?e.map((function(e){return t.normalizeOption(e)})):je(e)?(Ct(Kj,this.$options.name),at(e).map((function(a){return t.normalizeOption(e[a]||{},a)}))):[]}}});function Xj(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Zj(e){for(var t=1;t-1:iL(t,e)},isRadio:function(){return!1}},watch:EG({},FG,(function(e,t){iL(e,t)||this.setIndeterminate(e)})),mounted:function(){this.setIndeterminate(this[FG])},methods:{computedLocalCheckedWatcher:function(e,t){if(!iL(e,t)){this.$emit(VG,e);var a=this.$refs.input;a&&this.$emit(HG,a.indeterminate)}},handleChange:function(e){var t=this,a=e.target,o=a.checked,s=a.indeterminate,i=this.value,n=this.uncheckedValue,r=this.computedLocalChecked;if(Fe(r)){var c=fG(r,i);o&&c<0?r=r.concat(i):!o&&c>-1&&(r=r.slice(0,c).concat(r.slice(c+1)))}else r=o?i:n;this.computedLocalChecked=r,this.$nextTick((function(){t.$emit(Fs,r),t.isGroup&&t.bvGroup.$emit(Fs,r),t.$emit(HG,s)}))},setIndeterminate:function(e){Fe(this.computedLocalChecked)&&(e=!1);var t=this.$refs.input;t&&(t.indeterminate=e,this.$emit(HG,e))}}}),WG=Jc(xG,Ua),NG=Ms({name:Ua,mixins:[BG],inject:{getBvGroup:{from:"getBvRadioGroup",default:function(){return function(){return null}}}},props:WG,computed:{bvGroup:function(){return this.getBvGroup()}}});function $G(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function qG(e){for(var t=1;t0&&(c=[e("div",{staticClass:"b-form-date-controls d-flex flex-wrap",class:{"justify-content-between":c.length>1,"justify-content-end":c.length<2}},c)]);var m=e(OE,{staticClass:"b-form-date-calendar w-100",props:zW(zW({},$c(TW,i)),{},{hidden:!this.isVisible,value:t,valueAsDate:!1,width:this.calendarWidth}),on:{selected:this.onSelected,input:this.onInput,context:this.onContext},scopedSlots:nt(n,["nav-prev-decade","nav-prev-year","nav-prev-month","nav-this-month","nav-next-month","nav-next-year","nav-next-decade"]),key:"calendar",ref:"calendar"},c);return e(wW,{staticClass:"b-form-datepicker",props:zW(zW({},$c(VW,i)),{},{formattedValue:t?this.formattedValue:"",id:this.safeId(),lang:this.computedLang,menuClass:[{"bg-dark":s,"text-light":s},this.menuClass],placeholder:r,rtl:this.isRTL,value:t}),on:{show:this.onShow,shown:this.onShown,hidden:this.onHidden},scopedSlots:CW({},Pn,n[Pn]||this.defaultButtonFn),ref:"control"},[m])}}),LW=Ft({components:{BFormDatepicker:BW,BDatepicker:BW}});function OW(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function EW(e){for(var t=1;t1&&void 0!==arguments[1])||arguments[1];return Promise.all(zr(e).filter((function(e){return"file"===e.kind})).map((function(e){var a=qW(e);if(a){if(a.isDirectory&&t)return KW(a.createReader(),"".concat(a.name,"/"));if(a.isFile)return new Promise((function(e){a.file((function(t){t.$path="",e(t)}))}))}return null})).filter(yt))},KW=function e(t){var a=arguments.length>1&&void 0!==arguments[1]?arguments[1]:"";return new Promise((function(o){var s=[],i=function i(){t.readEntries((function(t){0===t.length?o(Promise.all(s).then((function(e){return Sr(e)}))):(s.push(Promise.all(t.map((function(t){if(t){if(t.isDirectory)return e(t.createReader(),"".concat(a).concat(t.name,"/"));if(t.isFile)return new Promise((function(e){t.file((function(t){t.$path="".concat(a).concat(t.name),e(t)}))}))}return null})).filter(yt))),i())}))};i()}))},QW=Jc(lt(EW(EW(EW(EW(EW(EW(EW({},DE),jW),vG),PG),IG),yG),{},{accept:Wc(Zi,""),browseText:Wc(Zi,"Browse"),capture:Wc(qi,!1),directory:Wc(qi,!1),dropPlaceholder:Wc(Zi,"Drop files here"),fileNameFormatter:Wc(Ki),multiple:Wc(qi,!1),noDrop:Wc(qi,!1),noDropPlaceholder:Wc(Zi,"Not allowed"),noTraverse:Wc(qi,!1),placeholder:Wc(Zi,"No file chosen")})),Ba),YW=Ms({name:Ba,mixins:[fL,RE,HW,Tr,AG,zG,bG,Tr],inheritAttrs:!1,props:QW,data:function(){return{files:[],dragging:!1,dropAllowed:!this.noDrop,hasFocus:!1}},computed:{computedAccept:function(){var e=this.accept;return e=(e||"").trim().split(/[,\s]+/).filter(yt),0===e.length?null:e.map((function(e){var t="name",a="^",o="$";U.test(e)?a="":(t="type",Q.test(e)&&(o=".+$",e=e.slice(0,-1))),e=Hr(e);var s=new RegExp("".concat(a).concat(e).concat(o));return{rx:s,prop:t}}))},computedCapture:function(){var e=this.capture;return!0===e||""===e||(e||null)},computedAttrs:function(){var e=this.name,t=this.disabled,a=this.required,o=this.form,s=this.computedCapture,i=this.accept,n=this.multiple,r=this.directory;return EW(EW({},this.bvAttrs),{},{type:"file",id:this.safeId(),name:e,disabled:t,required:a,form:o||null,capture:s,accept:i||null,multiple:n,directory:r,webkitdirectory:r,"aria-required":a?"true":null})},computedFileNameFormatter:function(){var e=this.fileNameFormatter;return Qc(e)?e:this.defaultFileNameFormatter},clonedFiles:function(){return bt(this.files)},flattenedFiles:function(){return _r(this.files)},fileNames:function(){return this.flattenedFiles.map((function(e){return e.name}))},labelContent:function(){if(this.dragging&&!this.noDrop)return this.normalizeSlot(Cn,{allowed:this.dropAllowed})||(this.dropAllowed?this.dropPlaceholder:this.$createElement("span",{staticClass:"text-danger"},this.noDropPlaceholder));if(0===this.files.length)return this.normalizeSlot(lr)||this.placeholder;var e=this.flattenedFiles,t=this.clonedFiles,a=this.fileNames,o=this.computedFileNameFormatter;return this.hasNormalizedSlot(_n)?this.normalizeSlot(_n,{files:e,filesTraversed:t,names:a}):o(e,t,a)}},watch:(DW={},UW(DW,GW,(function(e){(!e||Fe(e)&&0===e.length)&&this.reset()})),UW(DW,"files",(function(e,t){if(!iL(e,t)){var a=this.multiple,o=this.noTraverse,s=!a||o?_r(e):e;this.$emit(WW,a?s:s[0]||null)}})),DW),created:function(){this.$_form=null},mounted:function(){var e=lc("form",this.$el);e&&(el(e,"reset",this.reset,Gi),this.$_form=e)},beforeDestroy:function(){var e=this.$_form;e&&tl(e,"reset",this.reset,Gi)},methods:{isFileValid:function(e){if(!e)return!1;var t=this.computedAccept;return!t||t.some((function(t){return t.rx.test(e[t.prop])}))},isFilesArrayValid:function(e){var t=this;return Fe(e)?e.every((function(e){return t.isFileValid(e)})):this.isFileValid(e)},defaultFileNameFormatter:function(e,t,a){return a.join(", ")},setFiles:function(e){this.dropAllowed=!this.noDrop,this.dragging=!1,this.files=this.multiple?this.directory?e:_r(e):_r(e).slice(0,1)},setInputFiles:function(e){try{var t=new ClipboardEvent("").clipboardData||new DataTransfer;_r(bt(e)).forEach((function(e){delete e.$path,t.items.add(e)})),this.$refs.input.files=t.files}catch(a){}},reset:function(){try{var e=this.$refs.input;e.value="",e.type="",e.type="file"}catch(t){}this.files=[]},handleFiles:function(e){var t=arguments.length>1&&void 0!==arguments[1]&&arguments[1];if(t){var a=e.filter(this.isFilesArrayValid);a.length>0&&(this.setFiles(a),this.setInputFiles(a))}else this.setFiles(e)},focusHandler:function(e){this.plain||"focusout"===e.type?this.hasFocus=!1:this.hasFocus=!0},onChange:function(e){var t=this,a=e.type,o=e.target,s=e.dataTransfer,i=void 0===s?{}:s,n="drop"===a;this.$emit(Fs,e);var r=zr(i.items||[]);if(y&&r.length>0&&!Ve(qW(r[0])))JW(r,this.directory).then((function(e){return t.handleFiles(e,n)}));else{var c=zr(o.files||i.files||[]).map((function(e){return e.$path=e.webkitRelativePath||"",e}));this.handleFiles(c,n)}},onDragenter:function(e){ol(e),this.dragging=!0;var t=e.dataTransfer,a=void 0===t?{}:t;if(this.noDrop||this.disabled||!this.dropAllowed)return a.dropEffect="none",void(this.dropAllowed=!1);a.dropEffect="copy"},onDragover:function(e){ol(e),this.dragging=!0;var t=e.dataTransfer,a=void 0===t?{}:t;if(this.noDrop||this.disabled||!this.dropAllowed)return a.dropEffect="none",void(this.dropAllowed=!1);a.dropEffect="copy"},onDragleave:function(e){var t=this;ol(e),this.$nextTick((function(){t.dragging=!1,t.dropAllowed=!t.noDrop}))},onDrop:function(e){var t=this;ol(e),this.dragging=!1,this.noDrop||this.disabled||!this.dropAllowed?this.$nextTick((function(){t.dropAllowed=!t.noDrop})):this.onChange(e)}},render:function(e){var t=this.custom,a=this.plain,o=this.size,s=this.dragging,i=this.stateClass,n=this.bvAttrs,r=e("input",{class:[{"form-control-file":a,"custom-file-input":t,focus:t&&this.hasFocus},i],style:t?{zIndex:-5}:{},attrs:this.computedAttrs,on:{change:this.onChange,focusin:this.focusHandler,focusout:this.focusHandler,reset:this.reset},ref:"input"});if(a)return r;var c=e("label",{staticClass:"custom-file-label",class:{dragging:s},attrs:{for:this.safeId(),"data-browse":this.browseText||null}},[e("span",{staticClass:"d-block form-file-text",style:{pointerEvents:"none"}},[this.labelContent])]);return e("div",{staticClass:"custom-file b-form-file",class:[UW({},"b-custom-control-".concat(o),o),i,n.class],style:n.style,attrs:{id:this.safeId("_BV_file_outer_")},on:{dragenter:this.onDragenter,dragover:this.onDragover,dragleave:this.onDragleave,drop:this.onDrop}},[r,c])}}),XW=Ft({components:{BFormFile:YW,BFile:YW}}),ZW=function(e){return"\\"+e},eN=function(e){e=jr(e);var t=e.length,a=e.charCodeAt(0);return e.split("").reduce((function(o,s,i){var n=e.charCodeAt(i);return 0===n?o+"�":127===n||n>=1&&n<=31||0===i&&n>=48&&n<=57||1===i&&n>=48&&n<=57&&45===a?o+ZW("".concat(n.toString(16)," ")):0===i&&45===n&&1===t?o+ZW(s):n>=128||45===n||95===n||n>=48&&n<=57||n>=65&&n<=90||n>=97&&n<=122?o+s:o+ZW(s)}),"")};function tN(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function aN(e){for(var t=1;t0||at(this.labelColProps).length>0}},watch:{ariaDescribedby:function(e,t){e!==t&&this.updateAriaDescribedby(e,t)}},mounted:function(){var e=this;this.$nextTick((function(){e.updateAriaDescribedby(e.ariaDescribedby)}))},methods:{getAlignClasses:function(e,t){return Oc().reduce((function(a,o){var s=e[Gc(o,"".concat(t,"Align"))]||null;return s&&a.push(["text",o,s].filter(yt).join("-")),a}),[])},getColProps:function(e,t){return Oc().reduce((function(a,o){var s=e[Gc(o,"".concat(t,"Cols"))];return s=""===s||(s||!1),Le(s)||"auto"===s||(s=Vr(s,0),s=s>0&&s),s&&(a[o||(Le(s)?"col":"cols")]=s),a}),{})},updateAriaDescribedby:function(e,t){var a=this.labelFor;if(I&&a){var o=rc("#".concat(eN(a)),this.$refs.content);if(o){var s="aria-describedby",i=(e||"").split(K),n=(t||"").split(K),r=(vc(o,s)||"").split(K).filter((function(e){return!Cr(n,e)})).concat(i).filter((function(e,t,a){return a.indexOf(e)===t})).filter(yt).join(" ").trim();r?fc(o,s,r):gc(o,s)}}},onLegendClick:function(e){if(!this.labelFor){var t=e.target,a=t?t.tagName:"";if(-1===fN.indexOf(a)){var o=nc(uN,this.$refs.content).filter(oc);1===o.length&&Sc(o[0])}}}},render:function(e){var t=this.computedState,a=this.feedbackAriaLive,o=this.isHorizontal,s=this.labelFor,i=this.normalizeSlot,n=this.safeId,r=this.tooltip,c=n(),l=!s,h=e(),d=i(jn)||this.label,m=d?n("_BV_label_"):null;if(d||o){var p=this.labelSize,u=this.labelColProps,f=l?"legend":"label";this.labelSrOnly?(d&&(h=e(f,{class:"sr-only",attrs:{id:m,for:s||null}},[d])),h=e(o?lN:"div",{props:o?u:{}},[h])):h=e(o?lN:f,{on:l?{click:this.onLegendClick}:{},props:o?dN(dN({},u),{},{tag:f}):{},attrs:{id:m,for:s||null,tabindex:l?"-1":null},class:[l?"bv-no-focus-ring":"",o||l?"col-form-label":"",!o&&l?"pt-0":"",o||l?"":"d-block",p?"col-form-label-".concat(p):"",this.labelAlignClasses,this.labelClass]},[d])}var g=e(),v=i(Hn)||this.invalidFeedback,A=v?n("_BV_feedback_invalid_"):null;v&&(g=e(lG,{props:{ariaLive:a,id:A,state:t,tooltip:r},attrs:{tabindex:v?"-1":null}},[v]));var P=e(),b=i(Ir)||this.validFeedback,y=b?n("_BV_feedback_valid_"):null;b&&(P=e(dG,{props:{ariaLive:a,id:y,state:t,tooltip:r},attrs:{tabindex:b?"-1":null}},[b]));var w=e(),I=i(In)||this.description,z=I?n("_BV_description_"):null;I&&(w=e(rG,{attrs:{id:z,tabindex:"-1"}},[I]));var C=this.ariaDescribedby=[z,!1===t?A:null,!0===t?y:null].filter(yt).join(" ")||null,D=e(o?lN:"div",{props:o?this.contentColProps:{},ref:"content"},[i(wn,{ariaDescribedby:C,descriptionId:z,id:c,labelId:m})||e(),g,P,w]);return e(l?"fieldset":o?pG:"div",{staticClass:"form-group",class:[{"was-validated":this.validated},this.stateClass],attrs:{id:c,disabled:l?this.disabled:null,role:l?null:"group","aria-invalid":this.computedAriaInvalid,"aria-labelledby":l&&o?m:null}},o&&l?[e(pG,[h,D])]:[h,D])}},AN=Ft({components:{BFormGroup:vN,BFormFieldset:vN}}),PN=Ms({computed:{selectionStart:{cache:!1,get:function(){return this.$refs.input.selectionStart},set:function(e){this.$refs.input.selectionStart=e}},selectionEnd:{cache:!1,get:function(){return this.$refs.input.selectionEnd},set:function(e){this.$refs.input.selectionEnd=e}},selectionDirection:{cache:!1,get:function(){return this.$refs.input.selectionDirection},set:function(e){this.$refs.input.selectionDirection=e}}},methods:{select:function(){var e;(e=this.$refs.input).select.apply(e,arguments)},setSelectionRange:function(){var e;(e=this.$refs.input).setSelectionRange.apply(e,arguments)},setRangeText:function(){var e;(e=this.$refs.input).setRangeText.apply(e,arguments)}}});function bN(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function yN(e){for(var t=1;t2&&void 0!==arguments[2]&&arguments[2];return e=jr(e),!this.hasFormatter||this.lazyFormatter&&!a||(e=this.formatter(e,t)),e},modifyValue:function(e){return e=jr(e),this.trim&&(e=e.trim()),this.number&&(e=xr(e,e)),e},updateValue:function(e){var t=this,a=arguments.length>1&&void 0!==arguments[1]&&arguments[1],o=this.lazy;if(!o||a){this.clearDebounce();var s=function(){if(e=t.modifyValue(e),e!==t.vModelValue)t.vModelValue=e,t.$emit(RN,e);else if(t.hasFormatter){var a=t.$refs.input;a&&e!==a.value&&(a.value=e)}},i=this.computedDebounce;i>0&&!o&&!a?this.$_inputDebounceTimer=setTimeout(s,i):s()}},onInput:function(e){if(!e.target.composing){var t=e.target.value,a=this.formatValue(t,e);!1===a||e.defaultPrevented?ol(e,{propagation:!1}):(this.localValue=a,this.updateValue(a),this.$emit(ci,a))}},onChange:function(e){var t=e.target.value,a=this.formatValue(t,e);!1===a||e.defaultPrevented?ol(e,{propagation:!1}):(this.localValue=a,this.updateValue(a,!0),this.$emit(Fs,a))},onBlur:function(e){var t=e.target.value,a=this.formatValue(t,e,!0);!1!==a&&(this.localValue=jr(this.modifyValue(a)),this.updateValue(a,!0)),this.$emit(Es,e)},focus:function(){this.disabled||Sc(this.$el)},blur:function(){this.disabled||_c(this.$el)}}}),kN=Ms({computed:{validity:{cache:!1,get:function(){return this.$refs.input.validity}},validationMessage:{cache:!1,get:function(){return this.$refs.input.validationMessage}},willValidate:{cache:!1,get:function(){return this.$refs.input.willValidate}}},methods:{setCustomValidity:function(){var e;return(e=this.$refs.input).setCustomValidity.apply(e,arguments)},checkValidity:function(){var e;return(e=this.$refs.input).checkValidity.apply(e,arguments)},reportValidity:function(){var e;return(e=this.$refs.input).reportValidity.apply(e,arguments)}}});function MN(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function TN(e){for(var t=1;t=a?"full":t>=a-.5?"half":"empty",h={variant:i,disabled:n,readonly:r};return e("span",{staticClass:"b-rating-star",class:{focused:o&&t===a||!Vr(t)&&a===c,"b-rating-star-empty":"empty"===l,"b-rating-star-half":"half"===l,"b-rating-star-full":"full"===l},attrs:{tabindex:n||r?null:"-1"},on:{click:this.onClick}},[e("span",{staticClass:"b-rating-icon"},[this.normalizeSlot(l,h)])])}}),t$=Jc(lt(GN(GN(GN(GN(GN({},DE),qN),rt(vG,["required","autofocus"])),yG),{},{color:Wc(Zi),iconClear:Wc(Zi,"x"),iconEmpty:Wc(Zi,"star"),iconFull:Wc(Zi,"star-fill"),iconHalf:Wc(Zi,"star-half"),inline:Wc(qi,!1),locale:Wc(on),noBorder:Wc(qi,!1),precision:Wc(hn),readonly:Wc(qi,!1),showClear:Wc(qi,!1),showValue:Wc(qi,!1),showValueMax:Wc(qi,!1),stars:Wc(hn,YN,(function(e){return Vr(e)>=QN})),variant:Wc(Zi)})),Ha),a$=Ms({name:Ha,components:{BIconStar:kT,BIconStarHalf:TT,BIconStarFill:MT,BIconX:CB},mixins:[RE,$N,wG],props:t$,data:function(){var e=xr(this[JN],null),t=XN(this.stars);return{localValue:Ve(e)?null:ZN(e,0,t),hasFocus:!1}},computed:{computedStars:function(){return XN(this.stars)},computedRating:function(){var e=xr(this.localValue,0),t=Vr(this.precision,3);return ZN(xr(e.toFixed(t)),0,this.computedStars)},computedLocale:function(){var e=Dr(this.locale).filter(yt),t=new Intl.NumberFormat(e);return t.resolvedOptions().locale},isInteractive:function(){return!this.disabled&&!this.readonly},isRTL:function(){return CE(this.computedLocale)},formattedRating:function(){var e=Vr(this.precision),t=this.showValueMax,a=this.computedLocale,o={notation:"standard",minimumFractionDigits:isNaN(e)?0:e,maximumFractionDigits:isNaN(e)?3:e},s=this.computedStars.toLocaleString(a),i=this.localValue;return i=Ve(i)?t?"-":"":i.toLocaleString(a,o),t?"".concat(i,"/").concat(s):i}},watch:(xN={},WN(xN,JN,(function(e,t){if(e!==t){var a=xr(e,null);this.localValue=Ve(a)?null:ZN(a,0,this.computedStars)}})),WN(xN,"localValue",(function(e,t){e!==t&&e!==(this.value||0)&&this.$emit(KN,e||null)})),WN(xN,"disabled",(function(e){e&&(this.hasFocus=!1,this.blur())})),xN),methods:{focus:function(){this.disabled||Sc(this.$el)},blur:function(){this.disabled||_c(this.$el)},onKeydown:function(e){var t=e.keyCode;if(this.isInteractive&&Cr([XB,qB,tL,oL],t)){ol(e,{propagation:!1});var a=Vr(this.localValue,0),o=this.showClear?0:1,s=this.computedStars,i=this.isRTL?-1:1;t===XB?this.localValue=ZN(a-i,o,s)||null:t===tL?this.localValue=ZN(a+i,o,s):t===qB?this.localValue=ZN(a-1,o,s)||null:t===oL&&(this.localValue=ZN(a+1,o,s))}},onSelected:function(e){this.isInteractive&&(this.localValue=e)},onFocus:function(e){this.hasFocus=!!this.isInteractive&&"focus"===e.type},renderIcon:function(e){return this.$createElement(WB,{props:{icon:e,variant:this.disabled||this.color?null:this.variant||null}})},iconEmptyFn:function(){return this.renderIcon(this.iconEmpty)},iconHalfFn:function(){return this.renderIcon(this.iconHalf)},iconFullFn:function(){return this.renderIcon(this.iconFull)},iconClearFn:function(){return this.$createElement(WB,{props:{icon:this.iconClear}})}},render:function(e){var t=this,a=this.disabled,o=this.readonly,s=this.name,i=this.form,n=this.inline,r=this.variant,c=this.color,l=this.noBorder,h=this.hasFocus,d=this.computedRating,m=this.computedStars,p=this.formattedRating,u=this.showClear,f=this.isRTL,g=this.isInteractive,v=this.$scopedSlots,A=[];if(u&&!a&&!o){var P=e("span",{staticClass:"b-rating-icon"},[(v[Bn]||this.iconClearFn)()]);A.push(e("span",{staticClass:"b-rating-star b-rating-star-clear flex-grow-1",class:{focused:h&&0===d},attrs:{tabindex:g?"-1":null},on:{click:function(){return t.onSelected(null)}},key:"clear"},[P]))}for(var b=0;b1&&void 0!==arguments[1]?arguments[1]:null;if(je(e)){var a=It(e,this.valueField),o=It(e,this.textField),s=It(e,this.optionsField,null);return Ve(s)?{value:Te(a)?t||o:a,text:String(Te(o)?t:o),html:It(e,this.htmlField),disabled:Boolean(It(e,this.disabledField))}:{label:String(It(e,this.labelField)||o),options:this.normalizeOptions(s)}}return{value:t||e,text:String(e),disabled:!1}}}}),u$=Jc({disabled:Wc(qi,!1),value:Wc(Ni,void 0,!0)},Wa),f$=Ms({name:Wa,functional:!0,props:u$,render:function(e,t){var a=t.props,o=t.data,s=t.children,i=a.value,n=a.disabled;return e("option",bs(o,{attrs:{disabled:n},domProps:{value:i}}),s)}});function g$(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function v$(e){for(var t=1;t0?e:U$},computedInterval:function(){var e=Vr(this.repeatInterval,0);return e>0?e:F$},computedThreshold:function(){return Tl(Vr(this.repeatThreshold,H$),1)},computedStepMultiplier:function(){return Tl(Vr(this.repeatStepMultiplier,j$),1)},computedPrecision:function(){var e=this.computedStep;return Bl(e)===e?0:(e.toString().split(".")[1]||"").length},computedMultiplier:function(){return Ll(10,this.computedPrecision||0)},valueAsFixed:function(){var e=this.localValue;return Ve(e)?"":e.toFixed(this.computedPrecision)},computedLocale:function(){var e=Dr(this.locale).filter(yt),t=new Intl.NumberFormat(e);return t.resolvedOptions().locale},computedRTL:function(){return CE(this.computedLocale)},defaultFormatter:function(){var e=this.computedPrecision,t=new Intl.NumberFormat(this.computedLocale,{style:"decimal",useGrouping:!1,minimumIntegerDigits:1,minimumFractionDigits:e,maximumFractionDigits:e,notation:"standard"});return t.format},computedFormatter:function(){var e=this.formatterFn;return Qc(e)?e:this.defaultFormatter},computedAttrs:function(){return _$(_$({},this.bvAttrs),{},{role:"group",lang:this.computedLocale,tabindex:this.disabled?null:"-1",title:this.ariaLabel})},computedSpinAttrs:function(){var e=this.spinId,t=this.localValue,a=this.computedRequired,o=this.disabled,s=this.state,i=this.computedFormatter,n=!Ve(t);return _$(_$({dir:this.computedRTL?"rtl":"ltr"},this.bvAttrs),{},{id:e,role:"spinbutton",tabindex:o?null:"0","aria-live":"off","aria-label":this.ariaLabel||null,"aria-controls":this.ariaControls||null,"aria-invalid":!1===s||!n&&a?"true":null,"aria-required":a?"true":null,"aria-valuemin":jr(this.computedMin),"aria-valuemax":jr(this.computedMax),"aria-valuenow":n?t:null,"aria-valuetext":n?i(t):null})}},watch:(z$={},k$(z$,x$,(function(e){this.localValue=xr(e,null)})),k$(z$,"localValue",(function(e){this.$emit(B$,e)})),k$(z$,"disabled",(function(e){e&&this.clearRepeat()})),k$(z$,"readonly",(function(e){e&&this.clearRepeat()})),z$),created:function(){this.$_autoDelayTimer=null,this.$_autoRepeatTimer=null,this.$_keyIsDown=!1},beforeDestroy:function(){this.clearRepeat()},deactivated:function(){this.clearRepeat()},methods:{focus:function(){this.disabled||Sc(this.$refs.spinner)},blur:function(){this.disabled||_c(this.$refs.spinner)},emitChange:function(){this.$emit(Fs,this.localValue)},stepValue:function(e){var t=this.localValue;if(!this.disabled&&!Ve(t)){var a=this.computedStep*e,o=this.computedMin,s=this.computedMax,i=this.computedMultiplier,n=this.wrap;t=Ol((t-o)/a)*a+o+a,t=Ol(t*i)/i,this.localValue=t>s?n?o:s:t0&&void 0!==arguments[0]?arguments[0]:1,t=this.localValue;Ve(t)?this.localValue=this.computedMin:this.stepValue(1*e)},stepDown:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:1,t=this.localValue;Ve(t)?this.localValue=this.wrap?this.computedMax:this.computedMin:this.stepValue(-1*e)},onKeydown:function(e){var t=e.keyCode,a=e.altKey,o=e.ctrlKey,s=e.metaKey;if(!(this.disabled||this.readonly||a||o||s)&&Cr(G$,t)){if(ol(e,{propagation:!1}),this.$_keyIsDown)return;this.resetTimers(),Cr([oL,qB],t)?(this.$_keyIsDown=!0,t===oL?this.handleStepRepeat(e,this.stepUp):t===qB&&this.handleStepRepeat(e,this.stepDown)):t===eL?this.stepUp(this.computedStepMultiplier):t===ZB?this.stepDown(this.computedStepMultiplier):t===YB?this.localValue=this.computedMin:t===JB&&(this.localValue=this.computedMax)}},onKeyup:function(e){var t=e.keyCode,a=e.altKey,o=e.ctrlKey,s=e.metaKey;this.disabled||this.readonly||a||o||s||Cr(G$,t)&&(ol(e,{propagation:!1}),this.resetTimers(),this.$_keyIsDown=!1,this.emitChange())},handleStepRepeat:function(e,t){var a=this,o=e||{},s=o.type,i=o.button;if(!this.disabled&&!this.readonly){if("mousedown"===s&&i)return;this.resetTimers(),t(1);var n=this.computedThreshold,r=this.computedStepMultiplier,c=this.computedDelay,l=this.computedInterval;this.$_autoDelayTimer=setTimeout((function(){var e=0;a.$_autoRepeatTimer=setInterval((function(){t(ee.length)&&(t=e.length);for(var a=0,o=new Array(t);a0&&a.indexOf(e)===t}))},vq=function(e){return Oe(e)?e:We(e)&&e.target.value||""},Aq=function(){return{all:[],valid:[],invalid:[],duplicate:[]}},Pq=Jc(lt(nq(nq(nq(nq(nq(nq({},DE),hq),vG),yG),IG),{},{addButtonText:Wc(Zi,"Add"),addButtonVariant:Wc(Zi,"outline-secondary"),addOnChange:Wc(qi,!1),duplicateTagText:Wc(Zi,"Duplicate tag(s)"),feedbackAriaLive:Wc(Zi,"assertive"),ignoreInputFocusSelector:Wc(on,uq),inputAttrs:Wc(Yi,{}),inputClass:Wc(an),inputId:Wc(Zi),inputType:Wc(Zi,"text",(function(e){return Cr(pq,e)})),invalidTagText:Wc(Zi,"Invalid tag(s)"),limit:Wc(Qi),limitTagsText:Wc(Zi,"Tag limit reached"),noAddOnEnter:Wc(qi,!1),noOuterFocus:Wc(qi,!1),noTagRemove:Wc(qi,!1),placeholder:Wc(Zi,"Add tag..."),removeOnDelete:Wc(qi,!1),separator:Wc(on),tagClass:Wc(an),tagPills:Wc(qi,!1),tagRemoveLabel:Wc(Zi,"Remove tag"),tagRemovedLabel:Wc(Zi,"Tag removed"),tagValidator:Wc(Ki),tagVariant:Wc(Zi,"secondary")})),Ja),bq=Ms({name:Ja,mixins:[zL,RE,lq,AG,wG,zG,Tr],props:Pq,data:function(){return{hasFocus:!1,newTag:"",tags:[],removedTags:[],tagsState:Aq(),focusState:null}},computed:{computedInputId:function(){return this.inputId||this.safeId("__input__")},computedInputType:function(){return Cr(pq,this.inputType)?this.inputType:"text"},computedInputAttrs:function(){var e=this.disabled,t=this.form;return nq(nq({},this.inputAttrs),{},{id:this.computedInputId,value:this.newTag,disabled:e,form:t})},computedInputHandlers:function(){return nq(nq({},rt(this.bvListeners,[ai,oi])),{},{blur:this.onInputBlur,change:this.onInputChange,focus:this.onInputFocus,input:this.onInputInput,keydown:this.onInputKeydown,reset:this.reset})},computedSeparator:function(){return Dr(this.separator).filter(Oe).filter(yt).join("")},computedSeparatorRegExp:function(){var e=this.computedSeparator;return e?new RegExp("[".concat(fq(e),"]+")):null},computedJoiner:function(){var e=this.computedSeparator.charAt(0);return" "!==e?"".concat(e," "):e},computeIgnoreInputFocusSelector:function(){return Dr(this.ignoreInputFocusSelector).filter(yt).join(",").trim()},disableAddButton:function(){var e=this,t=Wr(this.newTag);return""===t||!this.splitTags(t).some((function(t){return!Cr(e.tags,t)&&e.validateTag(t)}))},duplicateTags:function(){return this.tagsState.duplicate},hasDuplicateTags:function(){return this.duplicateTags.length>0},invalidTags:function(){return this.tagsState.invalid},hasInvalidTags:function(){return this.invalidTags.length>0},isLimitReached:function(){var e=this.limit;return Ee(e)&&e>=0&&this.tags.length>=e}},watch:(Q$={},rq(Q$,dq,(function(e){this.tags=gq(e)})),rq(Q$,"tags",(function(e,t){iL(e,this[dq])||this.$emit(mq,e),iL(e,t)||(e=Dr(e).filter(yt),t=Dr(t).filter(yt),this.removedTags=t.filter((function(t){return!Cr(e,t)})))})),rq(Q$,"tagsState",(function(e,t){iL(e,t)||this.$emit(xi,e.valid,e.invalid,e.duplicate)})),Q$),created:function(){this.tags=gq(this[dq])},mounted:function(){var e=lc("form",this.$el);e&&el(e,"reset",this.reset,Gi)},beforeDestroy:function(){var e=lc("form",this.$el);e&&tl(e,"reset",this.reset,Gi)},methods:{addTag:function(e){if(e=Oe(e)?e:this.newTag,!this.disabled&&""!==Wr(e)&&!this.isLimitReached){var t=this.parseTags(e);if(t.valid.length>0||0===t.all.length)if(cc(this.getInput(),"select"))this.newTag="";else{var a=[].concat(Z$(t.invalid),Z$(t.duplicate));this.newTag=t.all.filter((function(e){return Cr(a,e)})).join(this.computedJoiner).concat(a.length>0?this.computedJoiner.charAt(0):"")}t.valid.length>0&&(this.tags=Dr(this.tags,t.valid)),this.tagsState=t,this.focus()}},removeTag:function(e){this.disabled||(this.tags=this.tags.filter((function(t){return t!==e})))},reset:function(){var e=this;this.newTag="",this.tags=[],this.$nextTick((function(){e.removedTags=[],e.tagsState=Aq()}))},onInputInput:function(e){if(!(this.disabled||We(e)&&e.target.composing)){var t=vq(e),a=this.computedSeparatorRegExp;this.newTag!==t&&(this.newTag=t),t=Gr(t),a&&a.test(t.slice(-1))?this.addTag():this.tagsState=""===t?Aq():this.parseTags(t)}},onInputChange:function(e){if(!this.disabled&&this.addOnChange){var t=vq(e);this.newTag!==t&&(this.newTag=t),this.addTag()}},onInputKeydown:function(e){if(!this.disabled&&We(e)){var t=e.keyCode,a=e.target.value||"";this.noAddOnEnter||t!==KB?!this.removeOnDelete||t!==NB&&t!==$B||""!==a||(ol(e,{propagation:!1}),this.tags=this.tags.slice(0,-1)):(ol(e,{propagation:!1}),this.addTag())}},onClick:function(e){var t=this,a=this.computeIgnoreInputFocusSelector;a&&lc(a,e.target,!0)||this.$nextTick((function(){t.focus()}))},onInputFocus:function(e){var t=this;"out"!==this.focusState&&(this.focusState="in",this.$nextTick((function(){Qr((function(){t.hasFocus&&(t.$emit(ti,e),t.focusState=null)}))})))},onInputBlur:function(e){var t=this;"in"!==this.focusState&&(this.focusState="out",this.$nextTick((function(){Qr((function(){t.hasFocus||(t.$emit(Es,e),t.focusState=null)}))})))},onFocusin:function(e){this.hasFocus=!0,this.$emit(ai,e)},onFocusout:function(e){this.hasFocus=!1,this.$emit(oi,e)},handleAutofocus:function(){var e=this;this.$nextTick((function(){Qr((function(){e.autofocus&&e.focus()}))}))},focus:function(){this.disabled||Sc(this.getInput())},blur:function(){this.disabled||_c(this.getInput())},splitTags:function(e){e=jr(e);var t=this.computedSeparatorRegExp;return(t?e.split(t):[e]).map(Wr).filter(yt)},parseTags:function(e){var t=this,a=this.splitTags(e),o={all:a,valid:[],invalid:[],duplicate:[]};return a.forEach((function(e){Cr(t.tags,e)||Cr(o.valid,e)?Cr(o.duplicate,e)||o.duplicate.push(e):t.validateTag(e)?o.valid.push(e):Cr(o.invalid,e)||o.invalid.push(e)})),o},validateTag:function(e){var t=this.tagValidator;return!Qc(t)||t(e)},getInput:function(){return rc("#".concat(eN(this.computedInputId)),this.$el)},defaultRender:function(e){var t=e.addButtonText,a=e.addButtonVariant,o=e.addTag,s=e.disableAddButton,i=e.disabled,n=e.duplicateTagText,r=e.inputAttrs,c=e.inputClass,l=e.inputHandlers,h=e.inputType,d=e.invalidTagText,m=e.isDuplicate,p=e.isInvalid,u=e.isLimitReached,f=e.limitTagsText,g=e.noTagRemove,v=e.placeholder,A=e.removeTag,P=e.tagClass,b=e.tagPills,y=e.tagRemoveLabel,w=e.tagVariant,I=e.tags,z=this.$createElement,C=I.map((function(e){return e=jr(e),z(X$,{class:P,props:{disabled:i,noRemove:g,pill:b,removeLabel:y,tag:"li",title:e,variant:w},on:{remove:function(){return A(e)}},key:"tags_".concat(e)},e)})),D=d&&p?this.safeId("__invalid_feedback__"):null,R=n&&m?this.safeId("__duplicate_feedback__"):null,S=f&&u?this.safeId("__limit_feedback__"):null,_=[r["aria-describedby"],D,R,S].filter(yt).join(" "),k=z("input",{staticClass:"b-form-tags-input w-100 flex-grow-1 p-0 m-0 bg-transparent border-0",class:c,style:{outline:0,minWidth:"5rem"},attrs:nq(nq({},r),{},{"aria-describedby":_||null,type:h,placeholder:v||null}),domProps:{value:r.value},on:l,directives:[{name:"model",value:r.value}],ref:"input"}),M=z(XL,{staticClass:"b-form-tags-button py-0",class:{invisible:s},style:{fontSize:"90%"},props:{disabled:s||u,variant:a},on:{click:function(){return o()}},ref:"button"},[this.normalizeSlot(un)||t]),T=this.safeId("__tag_list__"),V=z("li",{staticClass:"b-form-tags-field flex-grow-1",attrs:{role:"none","aria-live":"off","aria-controls":T},key:"tags_field"},[z("div",{staticClass:"d-flex",attrs:{role:"group"}},[k,M])]),x=z("ul",{staticClass:"b-form-tags-list list-unstyled mb-0 d-flex flex-wrap align-items-center",attrs:{id:T},key:"tags_list"},[C,V]),B=z();if(d||n||f){var L=this.feedbackAriaLive,O=this.computedJoiner,E=z();D&&(E=z(lG,{props:{id:D,ariaLive:L,forceShow:!0},key:"tags_invalid_feedback"},[this.invalidTagText,": ",this.invalidTags.join(O)]));var U=z();R&&(U=z(rG,{props:{id:R,ariaLive:L},key:"tags_duplicate_feedback"},[this.duplicateTagText,": ",this.duplicateTags.join(O)]));var F=z();S&&(F=z(rG,{props:{id:S,ariaLive:L},key:"tags_limit_feedback"},[f])),B=z("div",{attrs:{"aria-live":"polite","aria-atomic":"true"},key:"tags_feedback"},[E,U,F])}return[x,B]}},render:function(e){var t=this.name,a=this.disabled,o=this.required,s=this.form,i=this.tags,n=this.computedInputId,r=this.hasFocus,c=this.noOuterFocus,l=nq({tags:i.slice(),inputAttrs:this.computedInputAttrs,inputType:this.computedInputType,inputHandlers:this.computedInputHandlers,removeTag:this.removeTag,addTag:this.addTag,reset:this.reset,inputId:n,isInvalid:this.hasInvalidTags,invalidTags:this.invalidTags.slice(),isDuplicate:this.hasDuplicateTags,duplicateTags:this.duplicateTags.slice(),isLimitReached:this.isLimitReached,disableAddButton:this.disableAddButton},nt(this.$props,["addButtonText","addButtonVariant","disabled","duplicateTagText","form","inputClass","invalidTagText","limit","limitTagsText","noTagRemove","placeholder","required","separator","size","state","tagClass","tagPills","tagRemoveLabel","tagVariant"])),h=this.normalizeSlot(wn,l)||this.defaultRender(l),d=e("output",{staticClass:"sr-only",attrs:{id:this.safeId("__selected_tags__"),role:"status",for:n,"aria-live":r?"polite":"off","aria-atomic":"true","aria-relevant":"additions text"}},this.tags.join(", ")),m=e("div",{staticClass:"sr-only",attrs:{id:this.safeId("__removed_tags__"),role:"status","aria-live":r?"assertive":"off","aria-atomic":"true"}},this.removedTags.length>0?"(".concat(this.tagRemovedLabel,") ").concat(this.removedTags.join(", ")):""),p=e();if(t&&!a){var u=i.length>0;p=(u?i:[""]).map((function(a){return e("input",{class:{"sr-only":!u},attrs:{type:u?"hidden":"text",value:a,required:o,name:t,form:s},key:"tag_input_".concat(a)})}))}return e("div",{staticClass:"b-form-tags form-control h-auto",class:[{focus:r&&!c&&!a,disabled:a},this.sizeFormClass,this.stateClass],attrs:{id:this.safeId(),role:"group",tabindex:a||c?null:"-1","aria-describedby":this.safeId("__selected_tags__")},on:{click:this.onClick,focusin:this.onFocusin,focusout:this.onFocusout}},[d,m,h,p])}}),yq=Ft({components:{BFormTags:bq,BTags:bq,BFormTag:X$,BTag:X$}});function wq(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Iq(e){for(var t=1;td?r:"".concat(d,"px")}},render:function(e){return e("textarea",{class:this.computedClass,style:this.computedStyle,directives:[{name:"b-visible",value:this.visibleCallback,modifiers:{640:!0}}],attrs:this.computedAttrs,domProps:{value:this.localValue},on:this.computedListeners,ref:"input"})}}),Sq=Ft({components:{BFormTextarea:Rq,BTextarea:Rq}});function _q(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function kq(e){for(var t=1;te.length)&&(t=e.length);for(var a=0,o=new Array(t);a1&&void 0!==arguments[1]&&arguments[1];if(Ve(t)||Ve(a)||s&&Ve(o))return"";var i=[t,a,s?o:0];return i.map(Nq).join(":")},Jq=Jc(lt(kq(kq(kq(kq({},DE),Hq),nt(W$,["labelIncrement","labelDecrement"])),{},{ariaLabelledby:Wc(Zi),disabled:Wc(qi,!1),footerTag:Wc(Zi,"footer"),headerTag:Wc(Zi,"header"),hidden:Wc(qi,!1),hideHeader:Wc(qi,!1),hour12:Wc(qi,null),labelAm:Wc(Zi,"AM"),labelAmpm:Wc(Zi,"AM/PM"),labelHours:Wc(Zi,"Hours"),labelMinutes:Wc(Zi,"Minutes"),labelNoTimeSelected:Wc(Zi,"No time selected"),labelPm:Wc(Zi,"PM"),labelSeconds:Wc(Zi,"Seconds"),labelSelected:Wc(Zi,"Selected time"),locale:Wc(on),minutesStep:Wc(hn,1),readonly:Wc(qi,!1),secondsStep:Wc(hn,1),showSeconds:Wc(qi,!1)})),Xo),Kq=Ms({name:Xo,mixins:[RE,Fq,Tr],props:Jq,data:function(){var e=$q(this[jq]||"");return{modelHours:e.hours,modelMinutes:e.minutes,modelSeconds:e.seconds,modelAmpm:e.ampm,isLive:!1}},computed:{computedHMS:function(){var e=this.modelHours,t=this.modelMinutes,a=this.modelSeconds;return qq({hours:e,minutes:t,seconds:a},this.showSeconds)},resolvedOptions:function(){var e=Dr(this.locale).filter(yt),t={hour:Wq,minute:Wq,second:Wq};xe(this.hour12)||(t.hour12=!!this.hour12);var a=new Intl.DateTimeFormat(e,t),o=a.resolvedOptions(),s=o.hour12||!1,i=o.hourCycle||(s?"h12":"h23");return{locale:o.locale,hour12:s,hourCycle:i}},computedLocale:function(){return this.resolvedOptions.locale},computedLang:function(){return(this.computedLocale||"").replace(/-u-.*$/,"")},computedRTL:function(){return CE(this.computedLang)},computedHourCycle:function(){return this.resolvedOptions.hourCycle},is12Hour:function(){return!!this.resolvedOptions.hour12},context:function(){return{locale:this.computedLocale,isRTL:this.computedRTL,hourCycle:this.computedHourCycle,hour12:this.is12Hour,hours:this.modelHours,minutes:this.modelMinutes,seconds:this.showSeconds?this.modelSeconds:0,value:this.computedHMS,formatted:this.formattedTimeString}},valueId:function(){return this.safeId()||null},computedAriaLabelledby:function(){return[this.ariaLabelledby,this.valueId].filter(yt).join(" ")||null},timeFormatter:function(){var e={hour12:this.is12Hour,hourCycle:this.computedHourCycle,hour:Wq,minute:Wq,timeZone:"UTC"};return this.showSeconds&&(e.second=Wq),mE(this.computedLocale,e)},numberFormatter:function(){var e=new Intl.NumberFormat(this.computedLocale,{style:"decimal",minimumIntegerDigits:2,minimumFractionDigits:0,maximumFractionDigits:0,notation:"standard"});return e.format},formattedTimeString:function(){var e=this.modelHours,t=this.modelMinutes,a=this.showSeconds&&this.modelSeconds||0;return this.computedHMS?this.timeFormatter(cE(Date.UTC(0,0,1,e,t,a))):this.labelNoTimeSelected||" "},spinScopedSlots:function(){var e=this.$createElement;return{increment:function(t){var a=t.hasFocus;return e(Bv,{props:{scale:a?1.5:1.25},attrs:{"aria-hidden":"true"}})},decrement:function(t){var a=t.hasFocus;return e(Bv,{props:{flipV:!0,scale:a?1.5:1.25},attrs:{"aria-hidden":"true"}})}}}},watch:(Cq={},Mq(Cq,jq,(function(e,t){if(e!==t&&!iL($q(e),$q(this.computedHMS))){var a=$q(e),o=a.hours,s=a.minutes,i=a.seconds,n=a.ampm;this.modelHours=o,this.modelMinutes=s,this.modelSeconds=i,this.modelAmpm=n}})),Mq(Cq,"computedHMS",(function(e,t){e!==t&&this.$emit(Gq,e)})),Mq(Cq,"context",(function(e,t){iL(e,t)||this.$emit(Ws,e)})),Mq(Cq,"modelAmpm",(function(e,t){var a=this;if(e!==t){var o=Ve(this.modelHours)?0:this.modelHours;this.$nextTick((function(){0===e&&o>11?a.modelHours=o-12:1===e&&o<12&&(a.modelHours=o+12)}))}})),Mq(Cq,"modelHours",(function(e,t){e!==t&&(this.modelAmpm=e>11?1:0)})),Cq),created:function(){var e=this;this.$nextTick((function(){e.$emit(Ws,e.context)}))},mounted:function(){this.setLive(!0)},activated:function(){this.setLive(!0)},deactivated:function(){this.setLive(!1)},beforeDestroy:function(){this.setLive(!1)},methods:{focus:function(){this.disabled||Sc(this.$refs.spinners[0])},blur:function(){if(!this.disabled){var e=ec();hc(this.$el,e)&&_c(e)}},formatHours:function(e){var t=this.computedHourCycle;return e=this.is12Hour&&e>12?e-12:e,e=0===e&&"h12"===t?12:0===e&&"h24"===t?24:12===e&&"h11"===t?0:e,this.numberFormatter(e)},formatMinutes:function(e){return this.numberFormatter(e)},formatSeconds:function(e){return this.numberFormatter(e)},formatAmpm:function(e){return 0===e?this.labelAm:1===e?this.labelPm:""},setHours:function(e){this.modelHours=e},setMinutes:function(e){this.modelMinutes=e},setSeconds:function(e){this.modelSeconds=e},setAmpm:function(e){this.modelAmpm=e},onSpinLeftRight:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:{},t=e.type,a=e.keyCode;if(!this.disabled&&"keydown"===t&&(a===XB||a===tL)){ol(e);var o=this.$refs.spinners||[],s=o.map((function(e){return!!e.hasFocus})).indexOf(!0);s+=a===XB?-1:1,s=s>=o.length?0:s<0?o.length-1:s,Sc(o[s])}},setLive:function(e){var t=this;e?this.$nextTick((function(){Qr((function(){t.isLive=!0}))})):this.isLive=!1}},render:function(e){var t=this;if(this.hidden)return e();var a=this.disabled,o=this.readonly,s=this.computedLocale,i=this.computedAriaLabelledby,n=this.labelIncrement,r=this.labelDecrement,c=this.valueId,l=this.focus,h=[],d=function(i,l,d){var m=arguments.length>3&&void 0!==arguments[3]?arguments[3]:{},p=t.safeId("_spinbutton_".concat(l,"_"))||null;return h.push(p),e(N$,Mq({class:d,props:kq({id:p,placeholder:"--",vertical:!0,required:!0,disabled:a,readonly:o,locale:s,labelIncrement:n,labelDecrement:r,wrap:!0,ariaControls:c,min:0},m),scopedSlots:t.spinScopedSlots,on:{change:i},key:l,ref:"spinners"},_s,!0))},m=function(){return e("div",{staticClass:"d-flex flex-column",class:{"text-muted":a||o},attrs:{"aria-hidden":"true"}},[e(Ov,{props:{shiftV:4,scale:.5}}),e(Ov,{props:{shiftV:-4,scale:.5}})])},p=[];p.push(d(this.setHours,"hours","b-time-hours",{value:this.modelHours,max:23,step:1,formatterFn:this.formatHours,ariaLabel:this.labelHours})),p.push(m()),p.push(d(this.setMinutes,"minutes","b-time-minutes",{value:this.modelMinutes,max:59,step:this.minutesStep||1,formatterFn:this.formatMinutes,ariaLabel:this.labelMinutes})),this.showSeconds&&(p.push(m()),p.push(d(this.setSeconds,"seconds","b-time-seconds",{value:this.modelSeconds,max:59,step:this.secondsStep||1,formatterFn:this.formatSeconds,ariaLabel:this.labelSeconds}))),this.isLive&&this.is12Hour&&p.push(d(this.setAmpm,"ampm","b-time-ampm",{value:this.modelAmpm,max:1,formatterFn:this.formatAmpm,ariaLabel:this.labelAmpm,required:!1})),p=e("div",{staticClass:"d-flex align-items-center justify-content-center mx-auto",attrs:{role:"group",tabindex:a||o?null:"-1","aria-labelledby":i},on:{keydown:this.onSpinLeftRight,click:function(e){e.target===e.currentTarget&&l()}}},p);var u=e("output",{staticClass:"form-control form-control-sm text-center",class:{disabled:a||o},attrs:{id:c,role:"status",for:h.filter(yt).join(" ")||null,tabindex:a?null:"-1","aria-live":this.isLive?"polite":"off","aria-atomic":"true"},on:{click:l,focus:l}},[e("bdi",this.formattedTimeString),this.computedHMS?e("span",{staticClass:"sr-only"}," (".concat(this.labelSelected,") ")):""]),f=e(this.headerTag,{staticClass:"b-time-header",class:{"sr-only":this.hideHeader}},[u]),g=this.normalizeSlot(),v=g?e(this.footerTag,{staticClass:"b-time-footer"},g):e();return e("div",{staticClass:"b-time d-inline-flex flex-column text-center",attrs:{role:"group",lang:this.computedLang||null,"aria-labelledby":i||null,"aria-disabled":a?"true":null,"aria-readonly":o&&!a?"true":null}},[f,p,v])}});function Qq(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Yq(e){for(var t=1;t0&&n.push(e("span"," "));var c=this.labelResetButton;n.push(e(XL,{props:{size:"sm",disabled:a||o,variant:this.resetButtonVariant},attrs:{"aria-label":c||null},on:{click:this.onResetButton},key:"reset-btn"},c))}if(!this.noCloseButton){n.length>0&&n.push(e("span"," "));var l=this.labelCloseButton;n.push(e(XL,{props:{size:"sm",disabled:a,variant:this.closeButtonVariant},attrs:{"aria-label":l||null},on:{click:this.onCloseButton},key:"close-btn"},l))}n.length>0&&(n=[e("div",{staticClass:"b-form-date-controls d-flex flex-wrap",class:{"justify-content-between":n.length>1,"justify-content-end":n.length<2}},n)]);var h=e(Kq,{staticClass:"b-form-time-control",props:Yq(Yq({},$c(sJ,s)),{},{value:t,hidden:!this.isVisible}),on:{input:this.onInput,context:this.onContext},ref:"time"},n);return e(wW,{staticClass:"b-form-timepicker",props:Yq(Yq({},$c(iJ,s)),{},{id:this.safeId(),value:t,formattedValue:t?this.formattedValue:"",placeholder:i,rtl:this.isRTL,lang:this.computedLang}),on:{show:this.onShow,shown:this.onShown,hidden:this.onHidden},scopedSlots:Xq({},Pn,this.$scopedSlots[Pn]||this.defaultButtonFn),ref:"control"},[h])}}),cJ=Ft({components:{BFormTimepicker:rJ,BTimepicker:rJ}}),lJ=Ft({components:{BImg:lU,BImgLazy:UU}}),hJ=Jc({tag:Wc(Zi,"div")},co),dJ=Ms({name:co,functional:!0,props:hJ,render:function(e,t){var a=t.props,o=t.data,s=t.children;return e(a.tag,bs(o,{staticClass:"input-group-text"}),s)}}),mJ=Jc({append:Wc(qi,!1),id:Wc(Zi),isText:Wc(qi,!1),tag:Wc(Zi,"div")},io),pJ=Ms({name:io,functional:!0,props:mJ,render:function(e,t){var a=t.props,o=t.data,s=t.children,i=a.append;return e(a.tag,bs(o,{class:{"input-group-append":i,"input-group-prepend":!i},attrs:{id:a.id}}),a.isText?[e(dJ,s)]:s)}});function uJ(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function fJ(e){for(var t=1;t1&&void 0!==arguments[1]?arguments[1]:null;return e&&e.$options._scopeId||t};function vK(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var AK=Ms({mixins:[fK],computed:{scopedStyleAttrs:function(){var e=gK(this.bvParent);return e?vK({},e,""):{}}}});function PK(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function bK(e){for(var t=1;t2&&void 0!==arguments[2]?arguments[2]:{},o=e.$root?e.$root.$options.bvEventRoot||e.$root:null;return new t(bK(bK({},a),{},{parent:e,bvParent:e,bvEventRoot:o}))},IK=Ms({abstract:!0,name:fs,props:{nodes:Wc(en)},data:function(e){return{updatedNodes:e.nodes}},destroyed:function(){Xr(this.$el)},render:function(e){var t=this.updatedNodes,a=Be(t)?t({}):t;return a=Dr(a).filter(yt),a&&a.length>0&&!a[0].text?a[0]:e()}}),zK={container:Wc([De,Zi],"body"),disabled:Wc(qi,!1),tag:Wc(Zi,"div")},CK=Ms({name:us,mixins:[Tr],props:zK,watch:{disabled:{immediate:!0,handler:function(e){e?this.unmountTarget():this.$nextTick(this.mountTarget)}}},created:function(){this.$_defaultFn=null,this.$_target=null},beforeMount:function(){this.mountTarget()},updated:function(){this.updateTarget()},beforeDestroy:function(){this.unmountTarget(),this.$_defaultFn=null},methods:{getContainer:function(){if(I){var e=this.container;return Oe(e)?rc(e):e}return null},mountTarget:function(){if(!this.$_target){var e=this.getContainer();if(e){var t=document.createElement("div");e.appendChild(t),this.$_target=wK(this,IK,{el:t,propsData:{nodes:Dr(this.normalizeSlot())}})}}},updateTarget:function(){if(I&&this.$_target){var e=this.$scopedSlots.default;this.disabled||(e&&this.$_defaultFn!==e?this.$_target.updatedNodes=e:e||(this.$_target.updatedNodes=this.$slots.default)),this.$_defaultFn=e}},unmountTarget:function(){this.$_target&&this.$_target.$destroy(),this.$_target=null}},render:function(e){if(this.disabled){var t=Dr(this.normalizeSlot()).filter(yt);if(t.length>0&&!t[0].text)return t[0]}return e()}}),DK=Ms({name:us,mixins:[Tr],props:zK,render:function(e){if(this.disabled){var t=Dr(this.normalizeSlot()).filter(yt);if(t.length>0)return t[0]}return e(o["default"].Teleport,{to:this.container},this.normalizeSlot())}}),RK=Ss?DK:CK;function SK(e){return SK="function"==typeof Symbol&&"symbol"==typeof Symbol.iterator?function(e){return typeof e}:function(e){return e&&"function"==typeof Symbol&&e.constructor===Symbol&&e!==Symbol.prototype?"symbol":typeof e},SK(e)}function _K(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function kK(e){for(var t=1;t1&&void 0!==arguments[1]?arguments[1]:{};return TK(this,a),o=t.call(this,e,s),Ze(HK(o),{trigger:ht()}),o}return xK(a,null,[{key:"Defaults",get:function(){return kK(kK({},BK(GK(a),"Defaults",this)),{},{trigger:null})}}]),a}(UH),NK=1040,$K=".fixed-top, .fixed-bottom, .is-fixed, .sticky-top",qK=".sticky-top",JK=".navbar-toggler",KK=Ms({data:function(){return{modals:[],baseZIndex:null,scrollbarWidth:null,isBodyOverflowing:!1}},computed:{modalCount:function(){return this.modals.length},modalsAreOpen:function(){return this.modalCount>0}},watch:{modalCount:function(e,t){I&&(this.getScrollbarWidth(),e>0&&0===t?(this.checkScrollbar(),this.setScrollbar(),mc(document.body,"modal-open")):0===e&&t>0&&(this.resetScrollbar(),pc(document.body,"modal-open")),fc(document.body,"data-modal-open-count",String(e)))},modals:function(e){var t=this;this.checkScrollbar(),Qr((function(){t.updateModals(e||[])}))}},methods:{registerModal:function(e){e&&-1===this.modals.indexOf(e)&&this.modals.push(e)},unregisterModal:function(e){var t=this.modals.indexOf(e);t>-1&&(this.modals.splice(t,1),e._isBeingDestroyed||e._isDestroyed||this.resetModal(e))},getBaseZIndex:function(){if(I&&Ve(this.baseZIndex)){var e=document.createElement("div");mc(e,"modal-backdrop"),mc(e,"d-none"),Pc(e,"display","none"),document.body.appendChild(e),this.baseZIndex=Vr(Ic(e).zIndex,NK),document.body.removeChild(e)}return this.baseZIndex||NK},getScrollbarWidth:function(){if(I&&Ve(this.scrollbarWidth)){var e=document.createElement("div");mc(e,"modal-scrollbar-measure"),document.body.appendChild(e),this.scrollbarWidth=wc(e).width-e.clientWidth,document.body.removeChild(e)}return this.scrollbarWidth||0},updateModals:function(e){var t=this,a=this.getBaseZIndex(),o=this.getScrollbarWidth();e.forEach((function(e,s){e.zIndex=a+s,e.scrollbarWidth=o,e.isTop=s===t.modals.length-1,e.isBodyOverflowing=t.isBodyOverflowing}))},resetModal:function(e){e&&(e.zIndex=this.getBaseZIndex(),e.isTop=!0,e.isBodyOverflowing=!1)},checkScrollbar:function(){var e=wc(document.body),t=e.left,a=e.right;this.isBodyOverflowing=t+a0&&void 0!==arguments[0]&&arguments[0];this.$_observer&&this.$_observer.disconnect(),this.$_observer=null,e&&(this.$_observer=tF(this.$refs.content,this.checkModalOverflow.bind(this),pQ))},updateModel:function(e){e!==this[oQ]&&this.$emit(sQ,e)},buildEvent:function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};return new WK(e,XK(XK({cancelable:!1,target:this.$refs.modal||this.$el||null,relatedTarget:null,trigger:null},t),{},{vueTarget:this,componentId:this.modalId}))},show:function(){if(!this.isVisible&&!this.isOpening)if(this.isClosing)this.$once(ii,this.show);else{this.isOpening=!0,this.$_returnFocus=this.$_returnFocus||this.getActiveElement();var e=this.buildEvent(_i,{cancelable:!0});if(this.emitEvent(e),e.defaultPrevented||this.isVisible)return this.isOpening=!1,void this.updateModel(!1);this.doShow()}},hide:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:"";if(this.isVisible&&!this.isClosing){this.isClosing=!0;var t=this.buildEvent(ni,{cancelable:e!==rQ,trigger:e||null});if(e===dQ?this.$emit(pi,t):e===lQ?this.$emit(Us,t):e===hQ&&this.$emit(Gs,t),this.emitEvent(t),t.defaultPrevented||!this.isVisible)return this.isClosing=!1,void this.updateModel(!0);this.setObserver(!1),this.isVisible=!1,this.updateModel(!1)}},toggle:function(e){e&&(this.$_returnFocus=e),this.isVisible?this.hide(cQ):this.show()},getActiveElement:function(){var e=ec(I?[document.body]:[]);return e&&e.focus?e:null},doShow:function(){var e=this;QK.modalsAreOpen&&this.noStacking?this.listenOnRootOnce(il(vo,ii),this.doShow):(QK.registerModal(this),this.isHidden=!1,this.$nextTick((function(){e.isVisible=!0,e.isOpening=!1,e.updateModel(!0),e.$nextTick((function(){e.setObserver(!0)}))})))},onBeforeEnter:function(){this.isTransitioning=!0,this.setResizeEvent(!0)},onEnter:function(){var e=this;this.isBlock=!0,Qr((function(){Qr((function(){e.isShow=!0}))}))},onAfterEnter:function(){var e=this;this.checkModalOverflow(),this.isTransitioning=!1,Qr((function(){e.emitEvent(e.buildEvent(ki)),e.setEnforceFocus(!0),e.$nextTick((function(){e.focusFirst()}))}))},onBeforeLeave:function(){this.isTransitioning=!0,this.setResizeEvent(!1),this.setEnforceFocus(!1)},onLeave:function(){this.isShow=!1},onAfterLeave:function(){var e=this;this.isBlock=!1,this.isTransitioning=!1,this.isModalOverflowing=!1,this.isHidden=!0,this.$nextTick((function(){e.isClosing=!1,QK.unregisterModal(e),e.returnFocusTo(),e.emitEvent(e.buildEvent(ii))}))},emitEvent:function(e){var t=e.type;this.emitOnRoot(il(vo,t),e,e.componentId),this.$emit(t,e)},onDialogMousedown:function(){var e=this,t=this.$refs.modal,a=function a(o){tl(t,"mouseup",a,Wi),o.target===t&&(e.ignoreBackdropClick=!0)};el(t,"mouseup",a,Wi)},onClickOut:function(e){this.ignoreBackdropClick?this.ignoreBackdropClick=!1:this.isVisible&&!this.noCloseOnBackdrop&&hc(document.body,e.target)&&(hc(this.$refs.content,e.target)||this.hide(iQ))},onOk:function(){this.hide(dQ)},onCancel:function(){this.hide(lQ)},onClose:function(){this.hide(hQ)},onEsc:function(e){e.keyCode===QB&&this.isVisible&&!this.noCloseOnEsc&&this.hide(nQ)},focusHandler:function(e){var t=this.$refs.content,a=e.target;if(!(this.noEnforceFocus||!this.isTop||!this.isVisible||!t||document===a||hc(t,a)||this.computeIgnoreEnforceFocusSelector&&lc(this.computeIgnoreEnforceFocusSelector,a,!0))){var o=Rc(this.$refs.content),s=this.$refs["bottom-trap"],i=this.$refs["top-trap"];if(s&&a===s){if(Sc(o[0]))return}else if(i&&a===i&&Sc(o[o.length-1]))return;Sc(t,{preventScroll:!0})}},setEnforceFocus:function(e){this.listenDocument(e,"focusin",this.focusHandler)},setResizeEvent:function(e){this.listenWindow(e,"resize",this.checkModalOverflow),this.listenWindow(e,"orientationchange",this.checkModalOverflow)},showHandler:function(e,t){e===this.modalId&&(this.$_returnFocus=t||this.getActiveElement(),this.show())},hideHandler:function(e){e===this.modalId&&this.hide("event")},toggleHandler:function(e,t){e===this.modalId&&this.toggle(t)},modalListener:function(e){this.noStacking&&e.vueTarget!==this&&this.hide()},focusFirst:function(){var e=this;I&&Qr((function(){var t=e.$refs.modal,a=e.$refs.content,o=e.getActiveElement();if(t&&a&&(!o||!hc(a,o))){var s=e.$refs["ok-button"],i=e.$refs["cancel-button"],n=e.$refs["close-button"],r=e.autoFocusButton,c=r===dQ&&s?s.$el||s:r===lQ&&i?i.$el||i:r===hQ&&n?n.$el||n:a;Sc(c),c===a&&e.$nextTick((function(){t.scrollTop=0}))}}))},returnFocusTo:function(){var e=this.returnFocus||this.$_returnFocus||null;this.$_returnFocus=null,this.$nextTick((function(){e=Oe(e)?rc(e):e,e&&(e=e.$el||e,Sc(e))}))},checkModalOverflow:function(){if(this.isVisible){var e=this.$refs.modal;this.isModalOverflowing=e.scrollHeight>document.documentElement.clientHeight}},makeModal:function(e){var t=e();if(!this.hideHeader){var a=this.normalizeSlot(Kn,this.slotScope);if(!a){var o=e();this.hideHeaderClose||(o=e(ll,{props:{content:this.headerCloseContent,disabled:this.isTransitioning,ariaLabel:this.headerCloseLabel,textVariant:this.headerCloseVariant||this.headerTextVariant},on:{click:this.onClose},ref:"close-button"},[this.normalizeSlot(Qn)])),a=[e(this.titleTag,{staticClass:"modal-title",class:this.titleClasses,attrs:{id:this.modalTitleId},domProps:this.hasNormalizedSlot(Xn)?{}:yO(this.titleHtml,this.title)},this.normalizeSlot(Xn,this.slotScope)),o]}t=e(this.headerTag,{staticClass:"modal-header",class:this.headerClasses,attrs:{id:this.modalHeaderId},ref:"header"},[a])}var s=e("div",{staticClass:"modal-body",class:this.bodyClasses,attrs:{id:this.modalBodyId},ref:"body"},this.normalizeSlot(wn,this.slotScope)),i=e();if(!this.hideFooter){var n=this.normalizeSlot(Jn,this.slotScope);if(!n){var r=e();this.okOnly||(r=e(XL,{props:{variant:this.cancelVariant,size:this.buttonSize,disabled:this.cancelDisabled||this.busy||this.isTransitioning},domProps:this.hasNormalizedSlot(qn)?{}:yO(this.cancelTitleHtml,this.cancelTitle),on:{click:this.onCancel},ref:"cancel-button"},this.normalizeSlot(qn)));var c=e(XL,{props:{variant:this.okVariant,size:this.buttonSize,disabled:this.okDisabled||this.busy||this.isTransitioning},domProps:this.hasNormalizedSlot(Yn)?{}:yO(this.okTitleHtml,this.okTitle),on:{click:this.onOk},ref:"ok-button"},this.normalizeSlot(Yn));n=[r,c]}i=e(this.footerTag,{staticClass:"modal-footer",class:this.footerClasses,attrs:{id:this.modalFooterId},ref:"footer"},[n])}var l=e("div",{staticClass:"modal-content",class:this.contentClass,attrs:{id:this.modalContentId,tabindex:"-1"},ref:"content"},[t,s,i]),h=e(),d=e();this.isVisible&&!this.noEnforceFocus&&(h=e("span",{attrs:{tabindex:"0"},ref:"top-trap"}),d=e("span",{attrs:{tabindex:"0"},ref:"bottom-trap"}));var m=e("div",{staticClass:"modal-dialog",class:this.dialogClasses,on:{mousedown:this.onDialogMousedown},ref:"dialog"},[h,l,d]),p=e("div",{staticClass:"modal",class:this.modalClasses,style:this.modalStyles,attrs:this.computedModalAttrs,on:{keydown:this.onEsc,click:this.onClickOut},directives:[{name:"show",value:this.isVisible}],ref:"modal"},[m]);p=e("transition",{props:{enterClass:"",enterToClass:"",enterActiveClass:"",leaveClass:"",leaveActiveClass:"",leaveToClass:""},on:{beforeEnter:this.onBeforeEnter,enter:this.onEnter,afterEnter:this.onAfterEnter,beforeLeave:this.onBeforeLeave,leave:this.onLeave,afterLeave:this.onAfterLeave}},[p]);var u=e();return!this.hideBackdrop&&this.isVisible&&(u=e("div",{staticClass:"modal-backdrop",attrs:{id:this.modalBackdropId}},this.normalizeSlot($n))),u=e(vl,{props:{noFade:this.noFade}},[u]),e("div",{style:this.modalOuterStyle,attrs:this.computedAttrs,key:"modal-outer-".concat(this[Rs])},[p,u])}},render:function(e){return this.static?this.lazy&&this.isHidden?e():this.makeModal(e):this.isHidden?e():e(RK,[this.makeModal(e)])}}),gQ=nl(vo,_i),vQ="__bv_modal_directive__",AQ=function(e){var t=e.modifiers,a=void 0===t?{}:t,o=e.arg,s=e.value;return Oe(s)?s:Oe(o)?o:at(a).reverse()[0]},PQ=function(e){return e&&cc(e,".dropdown-menu > li, li.nav-item")&&rc("a, button",e)||e},bQ=function(e){e&&"BUTTON"!==e.tagName&&(Ac(e,"role")||fc(e,"role","button"),"A"===e.tagName||Ac(e,"tabindex")||fc(e,"tabindex","0"))},yQ=function(e,t,a){var o=AQ(t),s=PQ(e);if(o&&s){var i=function(e){var s=e.currentTarget;if(!sc(s)){var i=e.type,n=e.keyCode;"click"!==i&&("keydown"!==i||n!==KB&&n!==aL)||gL(YF(a,t)).$emit(gQ,o,s)}};e[vQ]={handler:i,target:o,trigger:s},bQ(s),el(s,"click",i,Gi),"BUTTON"!==s.tagName&&"button"===vc(s,"role")&&el(s,"keydown",i,Gi)}},wQ=function(e){var t=e[vQ]||{},a=t.trigger,o=t.handler;a&&o&&(tl(a,"click",o,Gi),tl(a,"keydown",o,Gi),tl(e,"click",o,Gi),tl(e,"keydown",o,Gi)),delete e[vQ]},IQ=function(e,t,a){var o=e[vQ]||{},s=AQ(t),i=PQ(e);s===o.target&&i===o.trigger||(wQ(e,t,a),yQ(e,t,a)),bQ(i)},zQ=function(){},CQ={inserted:IQ,updated:zQ,componentUpdated:IQ,unbind:wQ};function DQ(e,t){if(!(e instanceof t))throw new TypeError("Cannot call a class as a function")}function RQ(e,t){for(var a=0;ae.length)&&(t=e.length);for(var a=0,o=new Array(t);a2&&void 0!==arguments[2]?arguments[2]:HQ;if(!Dt(EQ)&&!Rt(EQ)){var s=wK(e,t,{propsData:kQ(kQ(kQ({},GQ(Vc(vo))),{},{hideHeaderClose:!0,hideHeader:!(a.title||a.titleHtml)},rt(a,at(jQ))),{},{lazy:!1,busy:!1,visible:!1,noStacking:!1,noEnforceFocus:!1})});return at(jQ).forEach((function(e){Te(a[e])||(s.$slots[jQ[e]]=Dr(a[e]))})),new Promise((function(e,t){var a=!1;s.$once(Ui,(function(){a||t(new Error("BootstrapVue MsgBox destroyed before resolve"))})),s.$on(ni,(function(t){if(!t.defaultPrevented){var s=o(t);t.defaultPrevented||(a=!0,e(s))}}));var i=document.createElement("div");document.body.appendChild(i),s.$mount(i)}))}},o=function(e,t){var o=arguments.length>2&&void 0!==arguments[2]?arguments[2]:{},s=arguments.length>3&&void 0!==arguments[3]?arguments[3]:null;if(t&&!Rt(EQ)&&!Dt(EQ)&&Be(s))return a(e,kQ(kQ({},GQ(o)),{},{msgBoxContent:t}),s)},s=function(){function e(t){DQ(this,e),Ye(this,{_vm:t,_root:gL(t)}),Ze(this,{_vm:ht(),_root:ht()})}return SQ(e,[{key:"show",value:function(e){if(e&&this._root){for(var t,a=arguments.length,o=new Array(a>1?a-1:0),s=1;s1?a-1:0),s=1;s1&&void 0!==arguments[1]?arguments[1]:{},a=kQ(kQ({},t),{},{okOnly:!0,okDisabled:!1,hideFooter:!1,msgBoxContent:e});return o(this._vm,e,a,(function(){return!0}))}},{key:"msgBoxConfirm",value:function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{},a=kQ(kQ({},t),{},{okOnly:!1,okDisabled:!1,cancelDisabled:!1,hideFooter:!1});return o(this._vm,e,a,(function(e){var t=e.trigger;return"ok"===t||"cancel"!==t&&null}))}}]),e}();e.mixin({beforeCreate:function(){this[UQ]=new s(this)}}),ot(e.prototype,EQ)||et(e.prototype,EQ,{get:function(){return this&&this[UQ]||Ct('"'.concat(EQ,'" must be accessed from a Vue instance "this" context.'),vo),this[UQ]}})},NQ=Ft({plugins:{plugin:WQ}}),$Q=Ft({components:{BModal:fQ},directives:{VBModal:CQ},plugins:{BVModalPlugin:NQ}});function qQ(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var JQ=function(e){return e="left"===e?"start":"right"===e?"end":e,"justify-content-".concat(e)},KQ=Jc({align:Wc(Zi),cardHeader:Wc(qi,!1),fill:Wc(qi,!1),justified:Wc(qi,!1),pills:Wc(qi,!1),small:Wc(qi,!1),tabs:Wc(qi,!1),tag:Wc(Zi,"ul"),vertical:Wc(qi,!1)},Po),QQ=Ms({name:Po,functional:!0,props:KQ,render:function(e,t){var a,o=t.props,s=t.data,i=t.children,n=o.tabs,r=o.pills,c=o.vertical,l=o.align,h=o.cardHeader;return e(o.tag,bs(s,{staticClass:"nav",class:(a={"nav-tabs":n,"nav-pills":r&&!n,"card-header-tabs":!c&&h&&n,"card-header-pills":!c&&h&&r&&!n,"flex-column":c,"nav-fill":!c&&o.fill,"nav-justified":!c&&o.justified},qQ(a,JQ(l),!c&&l),qQ(a,"small",o.small),a)}),i)}});function YQ(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function XQ(e){for(var t=1;te.length)&&(t=e.length);for(var a=0,o=new Array(t);a=0&&t<=1})),overlayTag:Wc(Zi,"div"),rounded:Wc(rn,!1),show:Wc(qi,!1),spinnerSmall:Wc(qi,!1),spinnerType:Wc(Zi,"border"),spinnerVariant:Wc(Zi),variant:Wc(Zi,"light"),wrapTag:Wc(Zi,"div"),zIndex:Wc(hn,10)},So),YY=Ms({name:So,mixins:[Tr],props:QY,computed:{computedRounded:function(){var e=this.rounded;return!0===e||""===e?"rounded":e?"rounded-".concat(e):""},computedVariant:function(){var e=this.variant;return e&&!this.bgColor?"bg-".concat(e):""},slotScope:function(){return{spinnerType:this.spinnerType||null,spinnerVariant:this.spinnerVariant||null,spinnerSmall:this.spinnerSmall}}},methods:{defaultOverlayFn:function(e){var t=e.spinnerType,a=e.spinnerVariant,o=e.spinnerSmall;return this.$createElement(WY,{props:{type:t,variant:a,small:o}})}},render:function(e){var t=this,a=this.show,o=this.fixed,s=this.noFade,i=this.noWrap,n=this.slotScope,r=e();if(a){var c=e("div",{staticClass:"position-absolute",class:[this.computedVariant,this.computedRounded],style:$Y($Y({},KY),{},{opacity:this.opacity,backgroundColor:this.bgColor||null,backdropFilter:this.blur?"blur(".concat(this.blur,")"):null})}),l=e("div",{staticClass:"position-absolute",style:this.noCenter?$Y({},KY):{top:"50%",left:"50%",transform:"translateX(-50%) translateY(-50%)"}},[this.normalizeSlot(rr,n)||this.defaultOverlayFn(n)]);r=e(this.overlayTag,{staticClass:"b-overlay",class:{"position-absolute":!i||i&&!o,"position-fixed":i&&o},style:$Y($Y({},KY),{},{zIndex:this.zIndex||10}),on:{click:function(e){return t.$emit(js,e)}},key:"overlay"},[c,l])}return r=e(vl,{props:{noFade:s,appear:!0},on:{"after-enter":function(){return t.$emit(ki)},"after-leave":function(){return t.$emit(ii)}}},[r]),i?r:e(this.wrapTag,{staticClass:"b-overlay-wrap position-relative",attrs:{"aria-busy":a?"true":null}},i?[r]:[this.normalizeSlot(),r])}}),XY=Ft({components:{BOverlay:YY}});function ZY(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function eX(e){for(var t=1;tt?t:a<1?1:a},mX=function(e){if(e.keyCode===aL)return ol(e,{immediatePropagation:!0}),e.currentTarget.click(),!1},pX=Jc(lt(eX(eX({},sX),{},{align:Wc(Zi,"left"),ariaLabel:Wc(Zi,"Pagination"),disabled:Wc(qi,!1),ellipsisClass:Wc(an),ellipsisText:Wc(Zi,"…"),firstClass:Wc(an),firstNumber:Wc(qi,!1),firstText:Wc(Zi,"«"),hideEllipsis:Wc(qi,!1),hideGotoEndButtons:Wc(qi,!1),labelFirstPage:Wc(Zi,"Go to first page"),labelLastPage:Wc(Zi,"Go to last page"),labelNextPage:Wc(Zi,"Go to next page"),labelPage:Wc(ln,"Go to page"),labelPrevPage:Wc(Zi,"Go to previous page"),lastClass:Wc(an),lastNumber:Wc(qi,!1),lastText:Wc(Zi,"»"),limit:Wc(hn,cX,(function(e){return!(Vr(e,0)<1)||(Ct('Prop "limit" must be a number greater than "0"',_o),!1)})),nextClass:Wc(an),nextText:Wc(Zi,"›"),pageClass:Wc(an),pills:Wc(qi,!1),prevClass:Wc(an),prevText:Wc(Zi,"‹"),size:Wc(Zi)})),"pagination"),uX=Ms({mixins:[oX,Tr],props:pX,data:function(){var e=Vr(this[iX],0);return e=e>0?e:-1,{currentPage:e,localNumberOfPages:1,localLimit:cX}},computed:{btnSize:function(){var e=this.size;return e?"pagination-".concat(e):""},alignment:function(){var e=this.align;return"center"===e?"justify-content-center":"end"===e||"right"===e?"justify-content-end":"fill"===e?"text-center":""},styleClass:function(){return this.pills?"b-pagination-pills":""},computedCurrentPage:function(){return dX(this.currentPage,this.localNumberOfPages)},paginationParams:function(){var e=this.localLimit,t=this.localNumberOfPages,a=this.computedCurrentPage,o=this.hideEllipsis,s=this.firstNumber,i=this.lastNumber,n=!1,r=!1,c=e,l=1;t<=e?c=t:arX?(o&&!i||(r=!0,c=e-(s?0:1)),c=Ml(c,e)):t-a+2rX?(o&&!s||(n=!0,c=e-(i?0:1)),l=t-c+1):(e>rX&&(c=e-(o?0:2),n=!(o&&!s),r=!(o&&!i)),l=a-Bl(c/2)),l<1?(l=1,n=!1):l>t-c&&(l=t-c+1,r=!1),n&&s&&l<4&&(c+=2,l=1,n=!1);var h=l+c-1;return r&&i&&h>t-3&&(c+=h===t-2?2:3,r=!1),e<=rX&&(s&&1===l?c=Ml(c+1,t,e+1):i&&t===l+c-1&&(l=Tl(l-1,1),c=Ml(t-l+1,t,e+1))),c=Ml(c,t-l+1),{showFirstDots:n,showLastDots:r,numberOfLinks:c,startNumber:l}},pageList:function(){var e=this.paginationParams,t=e.numberOfLinks,a=e.startNumber,o=this.computedCurrentPage,s=lX(a,t);if(s.length>3){var i=o-a,n="bv-d-xs-down-none";if(0===i)for(var r=3;ri+1;h--)s[h].classes=n}}return s}},watch:(JY={},tX(JY,iX,(function(e,t){e!==t&&(this.currentPage=dX(e,this.localNumberOfPages))})),tX(JY,"currentPage",(function(e,t){e!==t&&this.$emit(nX,e>0?e:null)})),tX(JY,"limit",(function(e,t){e!==t&&(this.localLimit=hX(e))})),JY),created:function(){var e=this;this.localLimit=hX(this.limit),this.$nextTick((function(){e.currentPage=e.currentPage>e.localNumberOfPages?e.localNumberOfPages:e.currentPage}))},methods:{handleKeyNav:function(e){var t=e.keyCode,a=e.shiftKey;this.isNav||(t===XB||t===oL?(ol(e,{propagation:!1}),a?this.focusFirst():this.focusPrev()):t!==tL&&t!==qB||(ol(e,{propagation:!1}),a?this.focusLast():this.focusNext()))},getButtons:function(){return nc("button.page-link, a.page-link",this.$el).filter((function(e){return oc(e)}))},focusCurrent:function(){var e=this;this.$nextTick((function(){var t=e.getButtons().find((function(t){return Vr(vc(t,"aria-posinset"),0)===e.computedCurrentPage}));Sc(t)||e.focusFirst()}))},focusFirst:function(){var e=this;this.$nextTick((function(){var t=e.getButtons().find((function(e){return!sc(e)}));Sc(t)}))},focusLast:function(){var e=this;this.$nextTick((function(){var t=e.getButtons().reverse().find((function(e){return!sc(e)}));Sc(t)}))},focusPrev:function(){var e=this;this.$nextTick((function(){var t=e.getButtons(),a=t.indexOf(ec());a>0&&!sc(t[a-1])&&Sc(t[a-1])}))},focusNext:function(){var e=this;this.$nextTick((function(){var t=e.getButtons(),a=t.indexOf(ec());ar,u=a<1?1:a>r?r:a,v={disabled:m,page:u,index:u-1},A=t.normalizeSlot(i,v)||jr(c)||e(),P=e(m?"span":n?EL:"button",{staticClass:"page-link",class:{"flex-grow-1":!n&&!m&&p},props:m||!n?{}:t.linkProps(a),attrs:{role:n?null:"menuitem",type:n||m?null:"button",tabindex:m||n?null:"-1","aria-label":s,"aria-controls":Jl(t).ariaControls||null,"aria-disabled":m?"true":null},on:m?{}:{"!click":function(e){t.onClick(e,a)},keydown:mX}},[A]);return e("li",{key:d,staticClass:"page-item",class:[{disabled:m,"flex-fill":p,"d-flex":p&&!n&&!m},l],attrs:{role:n?null:"presentation","aria-hidden":m?"true":null}},[P])},A=function(a){return e("li",{staticClass:"page-item",class:["disabled","bv-d-xs-down-none",p?"flex-fill":"",t.ellipsisClass],attrs:{role:"separator"},key:"ellipsis-".concat(a?"last":"first")},[e("span",{staticClass:"page-link"},[t.normalizeSlot(Dn)||jr(t.ellipsisText)||e()])])},P=function(a,i){var c=a.number,l=f(c)&&!g,h=o?null:l||g&&0===i?"0":"-1",d={role:n?null:"menuitemradio",type:n||o?null:"button","aria-disabled":o?"true":null,"aria-controls":Jl(t).ariaControls||null,"aria-label":Qc(s)?s(c):"".concat(Be(s)?s():s," ").concat(c),"aria-checked":n?null:l?"true":"false","aria-current":n&&l?"page":null,"aria-posinset":n?null:c,"aria-setsize":n?null:r,tabindex:n?null:h},m=jr(t.makePage(c)),u={page:c,index:c-1,content:m,active:l,disabled:o},v=e(o?"span":n?EL:"button",{props:o||!n?{}:t.linkProps(c),staticClass:"page-link",class:{"flex-grow-1":!n&&!o&&p},attrs:d,on:o?{}:{"!click":function(e){t.onClick(e,c)},keydown:mX}},[t.normalizeSlot(cr,u)||m]);return e("li",{staticClass:"page-item",class:[{disabled:o,active:l,"flex-fill":p,"d-flex":p&&!n&&!o},a.classes,t.pageClass],attrs:{role:n?null:"presentation"},key:"page-".concat(c)},[v])},b=e();this.firstNumber||this.hideGotoEndButtons||(b=v(1,this.labelFirstPage,Mn,this.firstText,this.firstClass,1,"pagination-goto-first")),u.push(b),u.push(v(c-1,this.labelPrevPage,dr,this.prevText,this.prevClass,1,"pagination-goto-prev")),u.push(this.firstNumber&&1!==l[0]?P({number:1},0):e()),u.push(d?A(!1):e()),this.pageList.forEach((function(e,a){var o=d&&t.firstNumber&&1!==l[0]?1:0;u.push(P(e,a+o))})),u.push(m?A(!0):e()),u.push(this.lastNumber&&l[l.length-1]!==r?P({number:r},-1):e()),u.push(v(c+1,this.labelNextPage,nr,this.nextText,this.nextClass,r,"pagination-goto-next"));var y=e();this.lastNumber||this.hideGotoEndButtons||(y=v(r,this.labelLastPage,Gn,this.lastText,this.lastClass,r,"pagination-goto-last")),u.push(y);var w=e("ul",{staticClass:"pagination",class:["b-pagination",this.btnSize,this.alignment,this.styleClass],attrs:{role:n?null:"menubar","aria-disabled":o?"true":"false","aria-label":n?null:i||null},on:n?{}:{keydown:this.handleKeyNav},ref:"ul"},u);return n?e("nav",{attrs:{"aria-disabled":o?"true":null,"aria-hidden":o?"true":"false","aria-label":n&&i||null}},[w]):w}});function fX(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function gX(e){for(var t=1;te.numberOfPages)&&(this.currentPage=1),this.localNumberOfPages=e.numberOfPages}},created:function(){var e=this;this.localNumberOfPages=this.numberOfPages;var t=Vr(this[iX],0);t>0?this.currentPage=t:this.$nextTick((function(){e.currentPage=0}))},methods:{onClick:function(e,t){var a=this;if(t!==this.currentPage){var o=e.target,s=new UH(fi,{cancelable:!0,vueTarget:this,target:o});this.$emit(s.type,s,t),s.defaultPrevented||(this.currentPage=t,this.$emit(Fs,this.currentPage),this.$nextTick((function(){oc(o)&&a.$el.contains(o)?Sc(o):a.focusCurrent()})))}},makePage:function(e){return e},linkProps:function(){return{}}}}),zX=Ft({components:{BPagination:IX}});function CX(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function DX(e){for(var t=1;t0?this.localNumberOfPages=this.pages.length:this.localNumberOfPages=SX(this.numberOfPages),this.$nextTick((function(){e.guessCurrentPage()}))},onClick:function(e,t){var a=this;if(t!==this.currentPage){var o=e.currentTarget||e.target,s=new UH(fi,{cancelable:!0,vueTarget:this,target:o});this.$emit(s.type,s,t),s.defaultPrevented||(Qr((function(){a.currentPage=t,a.$emit(Fs,t)})),this.$nextTick((function(){_c(o)})))}},getPageInfo:function(e){if(!Fe(this.pages)||0===this.pages.length||Te(this.pages[e-1])){var t="".concat(this.baseUrl).concat(e);return{link:this.useRouter?{path:t}:t,text:jr(e)}}var a=this.pages[e-1];if(He(a)){var o=a.link;return{link:He(o)?o:this.useRouter?{path:o}:o,text:jr(a.text||e)}}return{link:jr(a),text:jr(e)}},makePage:function(e){var t=this.pageGen,a=this.getPageInfo(e);return Qc(t)?t(e,a):a.text},makeLink:function(e){var t=this.linkGen,a=this.getPageInfo(e);return Qc(t)?t(e,a):a.link},linkProps:function(e){var t=$c(_X,this),a=this.makeLink(e);return this.useRouter||He(a)?t.to=a:t.href=a,t},resolveLink:function(){var e,t=arguments.length>0&&void 0!==arguments[0]?arguments[0]:"";try{e=document.createElement("a"),e.href=ih({to:t},"a","/","/"),document.body.appendChild(e);var a=e,o=a.pathname,s=a.hash,i=a.search;return document.body.removeChild(e),{path:o,hash:s,query:eh(i)}}catch(n){try{e&&e.parentNode&&e.parentNode.removeChild(e)}catch(r){}return{}}},resolveRoute:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:"";try{var t=this.$router.resolve(e,this.$route).route;return{path:t.path,hash:t.hash,query:t.query}}catch(a){return{}}},guessCurrentPage:function(){var e=this.$router,t=this.$route,a=this.computedValue;if(!this.noPageDetect&&!a&&(I||!I&&e))for(var o=e&&t?{path:t.path,hash:t.hash,query:t.query}:{},s=I?window.location||document.location:null,i=s?{path:s.pathname,hash:s.hash,query:eh(s.search)}:{},n=1;!a&&n<=this.localNumberOfPages;n++){var r=this.makeLink(n);a=e&&(He(r)||this.useRouter)?iL(this.resolveRoute(r),o)?n:null:I?iL(this.resolveLink(r),i)?n:null:-1}this.currentPage=a>0?a:0}}}),TX=Ft({components:{BPaginationNav:MX}}),VX={AUTO:"auto",TOP:"top",RIGHT:"right",BOTTOM:"bottom",LEFT:"left",TOPLEFT:"top",TOPRIGHT:"top",RIGHTTOP:"right",RIGHTBOTTOM:"right",BOTTOMLEFT:"bottom",BOTTOMRIGHT:"bottom",LEFTTOP:"left",LEFTBOTTOM:"left"},xX={AUTO:0,TOPLEFT:-1,TOP:0,TOPRIGHT:1,RIGHTTOP:-1,RIGHT:0,RIGHTBOTTOM:1,BOTTOMLEFT:-1,BOTTOM:0,BOTTOMRIGHT:1,LEFTTOP:-1,LEFT:0,LEFTBOTTOM:1},BX={arrowPadding:Wc(hn,6),boundary:Wc([De,Zi],"scrollParent"),boundaryPadding:Wc(hn,5),fallbackPlacement:Wc(on,"flip"),offset:Wc(hn,0),placement:Wc(Zi,"top"),target:Wc([De,Re])},LX=Ms({name:cs,mixins:[fK],props:BX,data:function(){return{noFade:!1,localShow:!0,attachment:this.getAttachment(this.placement)}},computed:{templateType:function(){return"unknown"},popperConfig:function(){var e=this,t=this.placement;return{placement:this.getAttachment(t),modifiers:{offset:{offset:this.getOffset(t)},flip:{behavior:this.fallbackPlacement},arrow:{element:".arrow"},preventOverflow:{padding:this.boundaryPadding,boundariesElement:this.boundary}},onCreate:function(t){t.originalPlacement!==t.placement&&e.popperPlacementChange(t)},onUpdate:function(t){e.popperPlacementChange(t)}}}},created:function(){var e=this;this.$_popper=null,this.localShow=!0,this.$on(_i,(function(t){e.popperCreate(t)}));var t=function(){e.$nextTick((function(){Qr((function(){e.$destroy()}))}))};this.bvParent.$once(Ui,t),this.$once(ii,t)},beforeMount:function(){this.attachment=this.getAttachment(this.placement)},updated:function(){this.updatePopper()},beforeDestroy:function(){this.destroyPopper()},destroyed:function(){var e=this.$el;e&&e.parentNode&&e.parentNode.removeChild(e)},methods:{hide:function(){this.localShow=!1},getAttachment:function(e){return VX[String(e).toUpperCase()]||"auto"},getOffset:function(e){if(!this.offset){var t=this.$refs.arrow||rc(".arrow",this.$el),a=xr(Ic(t).width,0)+xr(this.arrowPadding,0);switch(xX[String(e).toUpperCase()]||0){case 1:return"+50%p - ".concat(a,"px");case-1:return"-50%p + ".concat(a,"px");default:return 0}}return this.offset},popperCreate:function(e){this.destroyPopper(),this.$_popper=new _H["a"](this.target,e,this.popperConfig)},destroyPopper:function(){this.$_popper&&this.$_popper.destroy(),this.$_popper=null},updatePopper:function(){this.$_popper&&this.$_popper.scheduleUpdate()},popperPlacementChange:function(e){this.attachment=this.getAttachment(e.placement)},renderTemplate:function(e){return e("div")}},render:function(e){var t=this,a=this.noFade;return e(vl,{props:{appear:!0,noFade:a},on:{beforeEnter:function(e){return t.$emit(_i,e)},afterEnter:function(e){return t.$emit(ki,e)},beforeLeave:function(e){return t.$emit(ni,e)},afterLeave:function(e){return t.$emit(ii,e)}}},[this.localShow?this.renderTemplate(e):e()])}});function OX(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function EX(e){for(var t=1;t0&&void 0!==arguments[0]?arguments[0]:{},a=!1;at(eZ).forEach((function(o){Te(t[o])||e[o]===t[o]||(e[o]=t[o],"title"===o&&(a=!0))})),a&&this.localShow&&this.fixTitle()},createTemplateAndShow:function(){var e=this.getContainer(),t=this.getTemplate(),a=this.$_tip=wK(this,t,{propsData:{id:this.computedId,html:this.html,placement:this.placement,fallbackPlacement:this.fallbackPlacement,target:this.getPlacementTarget(),boundary:this.getBoundary(),offset:Vr(this.offset,0),arrowPadding:Vr(this.arrowPadding,0),boundaryPadding:Vr(this.boundaryPadding,0)}});this.handleTemplateUpdate(),a.$once(_i,this.onTemplateShow),a.$once(ki,this.onTemplateShown),a.$once(ni,this.onTemplateHide),a.$once(ii,this.onTemplateHidden),a.$once(Ui,this.destroyTemplate),a.$on(ai,this.handleEvent),a.$on(oi,this.handleEvent),a.$on(hi,this.handleEvent),a.$on(di,this.handleEvent),a.$mount(e.appendChild(document.createElement("div")))},hideTemplate:function(){this.$_tip&&this.$_tip.hide(),this.clearActiveTriggers(),this.$_hoverState=""},destroyTemplate:function(){this.setWhileOpenListeners(!1),this.clearHoverTimeout(),this.$_hoverState="",this.clearActiveTriggers(),this.localPlacementTarget=null;try{this.$_tip.$destroy()}catch(e){}this.$_tip=null,this.removeAriaDescribedby(),this.restoreTitle(),this.localShow=!1},getTemplateElement:function(){return this.$_tip?this.$_tip.$el:null},handleTemplateUpdate:function(){var e=this,t=this.$_tip;if(t){var a=["title","content","variant","customClass","noFade","interactive"];a.forEach((function(a){t[a]!==e[a]&&(t[a]=e[a])}))}},show:function(){var e=this.getTarget();if(e&&hc(document.body,e)&&oc(e)&&!this.dropdownOpen()&&(!xe(this.title)&&""!==this.title||!xe(this.content)&&""!==this.content)&&!this.$_tip&&!this.localShow){this.localShow=!0;var t=this.buildEvent(_i,{cancelable:!0});this.emitEvent(t),t.defaultPrevented?this.destroyTemplate():(this.fixTitle(),this.addAriaDescribedby(),this.createTemplateAndShow())}},hide:function(){var e=arguments.length>0&&void 0!==arguments[0]&&arguments[0],t=this.getTemplateElement();if(t&&this.localShow){var a=this.buildEvent(ni,{cancelable:!e});this.emitEvent(a),a.defaultPrevented||this.hideTemplate()}else this.restoreTitle()},forceHide:function(){var e=this.getTemplateElement();e&&this.localShow&&(this.setWhileOpenListeners(!1),this.clearHoverTimeout(),this.$_hoverState="",this.clearActiveTriggers(),this.$_tip&&(this.$_tip.noFade=!0),this.hide(!0))},enable:function(){this.$_enabled=!0,this.emitEvent(this.buildEvent(Xs))},disable:function(){this.$_enabled=!1,this.emitEvent(this.buildEvent(Js))},onTemplateShow:function(){this.setWhileOpenListeners(!0)},onTemplateShown:function(){var e=this.$_hoverState;this.$_hoverState="","out"===e&&this.leave(null),this.emitEvent(this.buildEvent(ki))},onTemplateHide:function(){this.setWhileOpenListeners(!1)},onTemplateHidden:function(){this.destroyTemplate(),this.emitEvent(this.buildEvent(ii))},getTarget:function(){var e=this.target;return Oe(e)?e=dc(e.replace(/^#/,"")):Be(e)?e=e():e&&(e=e.$el||e),Zr(e)?e:null},getPlacementTarget:function(){return this.getTarget()},getTargetId:function(){var e=this.getTarget();return e&&e.id?e.id:null},getContainer:function(){var e=!!this.container&&(this.container.$el||this.container),t=document.body,a=this.getTarget();return!1===e?lc(QX,a)||t:Oe(e)&&dc(e.replace(/^#/,""))||t},getBoundary:function(){return this.boundary?this.boundary.$el||this.boundary:"scrollParent"},isInModal:function(){var e=this.getTarget();return e&&lc(qX,e)},isDropdown:function(){var e=this.getTarget();return e&&uc(e,YX)},dropdownOpen:function(){var e=this.getTarget();return this.isDropdown()&&e&&rc(XX,e)},clearHoverTimeout:function(){clearTimeout(this.$_hoverTimeout),this.$_hoverTimeout=null},clearVisibilityInterval:function(){clearInterval(this.$_visibleInterval),this.$_visibleInterval=null},clearActiveTriggers:function(){for(var e in this.activeTrigger)this.activeTrigger[e]=!1},addAriaDescribedby:function(){var e=this.getTarget(),t=vc(e,"aria-describedby")||"";t=t.split(/\s+/).concat(this.computedId).join(" ").trim(),fc(e,"aria-describedby",t)},removeAriaDescribedby:function(){var e=this,t=this.getTarget(),a=vc(t,"aria-describedby")||"";a=a.split(/\s+/).filter((function(t){return t!==e.computedId})).join(" ").trim(),a?fc(t,"aria-describedby",a):gc(t,"aria-describedby")},fixTitle:function(){var e=this.getTarget();if(Ac(e,"title")){var t=vc(e,"title");fc(e,"title",""),t&&fc(e,ZX,t)}},restoreTitle:function(){var e=this.getTarget();if(Ac(e,ZX)){var t=vc(e,ZX);gc(e,ZX),t&&fc(e,"title",t)}},buildEvent:function(e){var t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};return new UH(e,GX({cancelable:!1,target:this.getTarget(),relatedTarget:this.getTemplateElement()||null,componentId:this.computedId,vueTarget:this},t))},emitEvent:function(e){var t=e.type;this.emitOnRoot(il(this.templateType,t),e),this.$emit(t,e)},listen:function(){var e=this,t=this.getTarget();t&&(this.setRootListener(!0),this.computedTriggers.forEach((function(a){"click"===a?el(t,"click",e.handleEvent,Wi):"focus"===a?(el(t,"focusin",e.handleEvent,Wi),el(t,"focusout",e.handleEvent,Wi)):"blur"===a?el(t,"focusout",e.handleEvent,Wi):"hover"===a&&(el(t,"mouseenter",e.handleEvent,Wi),el(t,"mouseleave",e.handleEvent,Wi))}),this))},unListen:function(){var e=this,t=["click","focusin","focusout","mouseenter","mouseleave"],a=this.getTarget();this.setRootListener(!1),t.forEach((function(t){a&&tl(a,t,e.handleEvent,Wi)}),this)},setRootListener:function(e){var t=e?"listenOnRoot":"listenOffRoot",a=this.templateType;this[t](nl(a,ni),this.doHide),this[t](nl(a,_i),this.doShow),this[t](nl(a,qs),this.doDisable),this[t](nl(a,Ys),this.doEnable)},setWhileOpenListeners:function(e){this.setModalListener(e),this.setDropdownListener(e),this.visibleCheck(e),this.setOnTouchStartListener(e)},visibleCheck:function(e){var t=this;this.clearVisibilityInterval();var a=this.getTarget();e&&(this.$_visibleInterval=setInterval((function(){var e=t.getTemplateElement();!e||!t.localShow||a.parentNode&&oc(a)||t.forceHide()}),100))},setModalListener:function(e){this.isInModal()&&this[e?"listenOnRoot":"listenOffRoot"](JX,this.forceHide)},setOnTouchStartListener:function(e){var t=this;"ontouchstart"in document.documentElement&&zr(document.body.children).forEach((function(a){al(e,a,"mouseover",t.$_noop)}))},setDropdownListener:function(e){var t=this.getTarget();if(t&&this.bvEventRoot&&this.isDropdown){var a=NH(t);a&&a[e?"$on":"$off"](ki,this.forceHide)}},handleEvent:function(e){var t=this.getTarget();if(t&&!sc(t)&&this.$_enabled&&!this.dropdownOpen()){var a=e.type,o=this.computedTriggers;if("click"===a&&Cr(o,"click"))this.click(e);else if("mouseenter"===a&&Cr(o,"hover"))this.enter(e);else if("focusin"===a&&Cr(o,"focus"))this.enter(e);else if("focusout"===a&&(Cr(o,"focus")||Cr(o,"blur"))||"mouseleave"===a&&Cr(o,"hover")){var s=this.getTemplateElement(),i=e.target,n=e.relatedTarget;if(s&&hc(s,i)&&hc(t,n)||s&&hc(t,i)&&hc(s,n)||s&&hc(s,i)&&hc(s,n)||hc(t,i)&&hc(t,n))return;this.leave(e)}}},doHide:function(e){e&&this.getTargetId()!==e&&this.computedId!==e||this.forceHide()},doShow:function(e){e&&this.getTargetId()!==e&&this.computedId!==e||this.show()},doDisable:function(e){e&&this.getTargetId()!==e&&this.computedId!==e||this.disable()},doEnable:function(e){e&&this.getTargetId()!==e&&this.computedId!==e||this.enable()},click:function(e){this.$_enabled&&!this.dropdownOpen()&&(Sc(e.currentTarget),this.activeTrigger.click=!this.activeTrigger.click,this.isWithActiveTrigger?this.enter(null):this.leave(null))},toggle:function(){this.$_enabled&&!this.dropdownOpen()&&(this.localShow?this.leave(null):this.enter(null))},enter:function(){var e=this,t=arguments.length>0&&void 0!==arguments[0]?arguments[0]:null;t&&(this.activeTrigger["focusin"===t.type?"focus":"hover"]=!0),this.localShow||"in"===this.$_hoverState?this.$_hoverState="in":(this.clearHoverTimeout(),this.$_hoverState="in",this.computedDelay.show?(this.fixTitle(),this.$_hoverTimeout=setTimeout((function(){"in"===e.$_hoverState?e.show():e.localShow||e.restoreTitle()}),this.computedDelay.show)):this.show())},leave:function(){var e=this,t=arguments.length>0&&void 0!==arguments[0]?arguments[0]:null;t&&(this.activeTrigger["focusout"===t.type?"focus":"hover"]=!1,"focusout"===t.type&&Cr(this.computedTriggers,"blur")&&(this.activeTrigger.click=!1,this.activeTrigger.hover=!1)),this.isWithActiveTrigger||(this.clearHoverTimeout(),this.$_hoverState="out",this.computedDelay.hide?this.$_hoverTimeout=setTimeout((function(){"out"===e.$_hoverState&&e.hide()}),this.computedDelay.hide):this.hide())}}});function aZ(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function oZ(e){for(var t=1;t0&&e[yZ].updateData(t)}))}var i={title:o.title,content:o.content,triggers:o.trigger,placement:o.placement,fallbackPlacement:o.fallbackPlacement,variant:o.variant,customClass:o.customClass,container:o.container,boundary:o.boundary,delay:o.delay,offset:o.offset,noFade:!o.animation,id:o.id,disabled:o.disabled,html:o.html},n=e[yZ].__bv_prev_data__;if(e[yZ].__bv_prev_data__=i,!iL(i,n)){var r={target:e};at(i).forEach((function(t){i[t]!==n[t]&&(r[t]="title"!==t&&"content"!==t||!Be(i[t])?i[t]:i[t](e))})),e[yZ].updateData(r)}}},LZ=function(e){e[yZ]&&(e[yZ].$destroy(),e[yZ]=null),delete e[yZ]},OZ={bind:function(e,t,a){BZ(e,t,a)},componentUpdated:function(e,t,a){Ls((function(){BZ(e,t,a)}))},unbind:function(e){LZ(e)}},EZ=Ft({directives:{VBPopover:OZ}}),UZ=Ft({components:{BPopover:vZ},plugins:{VBPopoverPlugin:EZ}}),FZ=Jc({animated:Wc(qi,null),label:Wc(Zi),labelHtml:Wc(Zi),max:Wc(hn,null),precision:Wc(hn,null),showProgress:Wc(qi,null),showValue:Wc(qi,null),striped:Wc(qi,null),value:Wc(hn,0),variant:Wc(Zi)},Vo),HZ=Ms({name:Vo,mixins:[Tr],inject:{getBvProgress:{default:function(){return function(){return{}}}}},props:FZ,computed:{bvProgress:function(){return this.getBvProgress()},progressBarClasses:function(){var e=this.computedAnimated,t=this.computedVariant;return[t?"bg-".concat(t):"",this.computedStriped||e?"progress-bar-striped":"",e?"progress-bar-animated":""]},progressBarStyles:function(){return{width:this.computedValue/this.computedMax*100+"%"}},computedValue:function(){return xr(this.value,0)},computedMax:function(){var e=xr(this.max)||xr(this.bvProgress.max,0);return e>0?e:100},computedPrecision:function(){return Tl(Vr(this.precision,Vr(this.bvProgress.precision,0)),0)},computedProgress:function(){var e=this.computedPrecision,t=Ll(10,e);return Br(100*t*this.computedValue/this.computedMax/t,e)},computedVariant:function(){return this.variant||this.bvProgress.variant},computedStriped:function(){return Le(this.striped)?this.striped:this.bvProgress.striped||!1},computedAnimated:function(){return Le(this.animated)?this.animated:this.bvProgress.animated||!1},computedShowProgress:function(){return Le(this.showProgress)?this.showProgress:this.bvProgress.showProgress||!1},computedShowValue:function(){return Le(this.showValue)?this.showValue:this.bvProgress.showValue||!1}},render:function(e){var t,a=this.label,o=this.labelHtml,s=this.computedValue,i=this.computedPrecision,n={};return this.hasNormalizedSlot()?t=this.normalizeSlot():a||o?n=yO(o,a):this.computedShowProgress?t=this.computedProgress:this.computedShowValue&&(t=Br(s,i)),e("div",{staticClass:"progress-bar",class:this.progressBarClasses,style:this.progressBarStyles,attrs:{role:"progressbar","aria-valuemin":"0","aria-valuemax":jr(this.computedMax),"aria-valuenow":Br(s,i)},domProps:n},t)}});function jZ(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function GZ(e){for(var t=1;t0&&void 0!==arguments[0]?arguments[0]:{},t=arguments.length>1&&void 0!==arguments[1]?arguments[1]:{};this.noCloseOnRouteChange||e.fullPath===t.fullPath||this.hide()})),NZ),created:function(){this.$_returnFocusEl=null},mounted:function(){var e=this;this.listenOnRoot(t0,this.handleToggle),this.listenOnRoot(e0,this.handleSync),this.$nextTick((function(){e.emitState(e.localShow)}))},activated:function(){this.emitSync()},beforeDestroy:function(){this.localShow=!1,this.$_returnFocusEl=null},methods:{hide:function(){this.localShow=!1},emitState:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:this.localShow;this.emitOnRoot(a0,this.safeId(),e)},emitSync:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:this.localShow;this.emitOnRoot(o0,this.safeId(),e)},handleToggle:function(e){e&&e===this.safeId()&&(this.localShow=!this.localShow)},handleSync:function(e){var t=this;e&&e===this.safeId()&&this.$nextTick((function(){t.emitSync(t.localShow)}))},onKeydown:function(e){var t=e.keyCode;!this.noCloseOnEsc&&t===QB&&this.localShow&&this.hide()},onBackdropClick:function(){this.localShow&&!this.noCloseOnBackdrop&&this.hide()},onTopTrapFocus:function(){var e=Rc(this.$refs.content);this.enforceFocus(e.reverse()[0])},onBottomTrapFocus:function(){var e=Rc(this.$refs.content);this.enforceFocus(e[0])},onBeforeEnter:function(){this.$_returnFocusEl=ec(I?[document.body]:[]),this.isOpen=!0},onAfterEnter:function(e){hc(e,ec())||this.enforceFocus(e),this.$emit(ki)},onAfterLeave:function(){this.enforceFocus(this.$_returnFocusEl),this.$_returnFocusEl=null,this.isOpen=!1,this.$emit(ii)},enforceFocus:function(e){this.noEnforceFocus||Sc(e)}},render:function(e){var t,a=this.bgVariant,o=this.width,s=this.textVariant,i=this.localShow,n=""===this.shadow||this.shadow,r=e(this.tag,{staticClass:ZZ,class:[(t={shadow:!0===n},XZ(t,"shadow-".concat(n),n&&!0!==n),XZ(t,"".concat(ZZ,"-right"),this.right),XZ(t,"bg-".concat(a),a),XZ(t,"text-".concat(s),s),t),this.sidebarClass],style:{width:o},attrs:this.computedAttrs,directives:[{name:"show",value:i}],ref:"content"},[f0(e,this)]);r=e("transition",{props:this.transitionProps,on:{beforeEnter:this.onBeforeEnter,afterEnter:this.onAfterEnter,afterLeave:this.onAfterLeave}},[r]);var c=e(vl,{props:{noFade:this.noSlide}},[g0(e,this)]),l=e(),h=e();return this.backdrop&&i&&(l=e("div",{attrs:{tabindex:"0"},on:{focus:this.onTopTrapFocus}}),h=e("div",{attrs:{tabindex:"0"},on:{focus:this.onBottomTrapFocus}})),e("div",{staticClass:"b-sidebar-outer",style:{zIndex:this.zIndex},attrs:{tabindex:"-1"},on:{keydown:this.onKeydown}},[l,r,h,c])}}),A0=Ft({components:{BSidebar:v0},plugins:{VBTogglePlugin:RH}});function P0(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var b0=Jc({animation:Wc(Zi,"wave"),height:Wc(Zi),size:Wc(Zi),type:Wc(Zi,"text"),variant:Wc(Zi),width:Wc(Zi)},Lo),y0=Ms({name:Lo,functional:!0,props:b0,render:function(e,t){var a,o=t.data,s=t.props,i=s.size,n=s.animation,r=s.variant;return e("div",bs(o,{staticClass:"b-skeleton",style:{width:i||s.width,height:i||s.height},class:(a={},P0(a,"b-skeleton-".concat(s.type),!0),P0(a,"b-skeleton-animate-".concat(n),n),P0(a,"bg-".concat(r),r),a)}))}});function w0(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function I0(e){for(var t=1;t0}}});function M0(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var T0={stacked:Wc(rn,!1)},V0=Ms({props:T0,computed:{isStacked:function(){var e=this.stacked;return""===e||e},isStackedAlways:function(){return!0===this.isStacked},stackedTableClasses:function(){var e=this.isStackedAlways;return M0({"b-table-stacked":e},"b-table-stacked-".concat(this.stacked),!e&&this.isStacked)}}});function x0(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function B0(e){for(var t=1;t0&&!n,[i,{"table-striped":this.striped,"table-hover":t,"table-dark":this.dark,"table-bordered":this.bordered,"table-borderless":this.borderless,"table-sm":this.small,border:this.outlined,"b-table-fixed":this.fixed,"b-table-caption-top":this.captionTop,"b-table-no-border-collapse":this.noBorderCollapse},a?"".concat(this.dark?"bg":"table","-").concat(a):"",s,o]},tableAttrs:function(){var e=Jl(this),t=e.computedItems,a=e.filteredItems,o=e.computedFields,s=e.selectableTableAttrs,i=e.computedBusy,n=this.isTableSimple?{}:{"aria-busy":jr(i),"aria-colcount":jr(o.length),"aria-describedby":this.bvAttrs["aria-describedby"]||this.$refs.caption?this.captionId:null},r=t&&a&&a.length>t.length?jr(a.length):null;return B0(B0(B0({"aria-rowcount":r},this.bvAttrs),{},{id:this.safeId(),role:this.bvAttrs.role||"table"},n),s)}},render:function(e){var t=Jl(this),a=t.wrapperClasses,o=t.renderCaption,s=t.renderColgroup,i=t.renderThead,n=t.renderTbody,r=t.renderTfoot,c=[];this.isTableSimple?c.push(this.normalizeSlot()):(c.push(o?o():null),c.push(s?s():null),c.push(i?i():null),c.push(n?n():null),c.push(r?r():null));var l=e("table",{staticClass:"table b-table",class:this.tableClasses,attrs:this.tableAttrs,key:"b-table"},c.filter(yt));return a.length>0?e("div",{class:a,style:this.wrapperStyles,key:"wrap"},[l]):l}});function U0(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function F0(e){for(var t=1;t0},J0=Jc({animation:Wc(Zi),columns:Wc(Qi,5,q0),hideHeader:Wc(qi,!1),rows:Wc(Qi,3,q0),showFooter:Wc(qi,!1),tableProps:Wc(Yi,{})},Uo),K0=Ms({name:Uo,functional:!0,props:J0,render:function(e,t){var a=t.data,o=t.props,s=o.animation,i=o.columns,n=e("th",[e(y0,{props:{animation:s}})]),r=e("tr",Rr(i,n)),c=e("td",[e(y0,{props:{width:"75%",animation:s}})]),l=e("tr",Rr(i,c)),h=e("tbody",Rr(o.rows,l)),d=o.hideHeader?e():e("thead",[r]),m=o.showFooter?e("tfoot",[r]):e();return e(G0,bs(a,{props:N0({},o.tableProps)}),[d,h,m])}}),Q0=Jc({loading:Wc(qi,!1)},Fo),Y0=Ms({name:Fo,functional:!0,props:Q0,render:function(e,t){var a=t.data,o=t.props,s=t.slots,i=t.scopedSlots,n=s(),r=i||{},c={};return o.loading?e("div",bs(a,{attrs:{role:"alert","aria-live":"polite","aria-busy":!0},staticClass:"b-skeleton-wrapper",key:"loading"}),Mr(Nn,c,r,n)):Mr(wn,c,r,n)}}),X0=Ft({components:{BSkeleton:y0,BSkeletonIcon:D0,BSkeletonImg:_0,BSkeletonTable:K0,BSkeletonWrapper:Y0}}),Z0=Ft({components:{BSpinner:WY}});function e1(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function t1(e){for(var t=1;t0?e:null},p1=function(e){return xe(e)||m1(e)>0},u1=Jc({colspan:Wc(hn,null,p1),rowspan:Wc(hn,null,p1),stackedHeading:Wc(Zi),stickyColumn:Wc(qi,!1),variant:Wc(Zi)},Wo),f1=Ms({name:Wo,mixins:[fL,zL,Tr],inject:{getBvTableTr:{default:function(){return function(){return{}}}}},inheritAttrs:!1,props:u1,computed:{bvTableTr:function(){return this.getBvTableTr()},tag:function(){return"td"},inTbody:function(){return this.bvTableTr.inTbody},inThead:function(){return this.bvTableTr.inThead},inTfoot:function(){return this.bvTableTr.inTfoot},isDark:function(){return this.bvTableTr.isDark},isStacked:function(){return this.bvTableTr.isStacked},isStackedCell:function(){return this.inTbody&&this.isStacked},isResponsive:function(){return this.bvTableTr.isResponsive},isStickyHeader:function(){return this.bvTableTr.isStickyHeader},hasStickyHeader:function(){return this.bvTableTr.hasStickyHeader},isStickyColumn:function(){return!this.isStacked&&(this.isResponsive||this.hasStickyHeader)&&this.stickyColumn},rowVariant:function(){return this.bvTableTr.variant},headVariant:function(){return this.bvTableTr.headVariant},footVariant:function(){return this.bvTableTr.footVariant},tableVariant:function(){return this.bvTableTr.tableVariant},computedColspan:function(){return m1(this.colspan)},computedRowspan:function(){return m1(this.rowspan)},cellClasses:function(){var e=this.variant,t=this.headVariant,a=this.isStickyColumn;return(!e&&this.isStickyHeader&&!t||!e&&a&&this.inTfoot&&!this.footVariant||!e&&a&&this.inThead&&!t||!e&&a&&this.inTbody)&&(e=this.rowVariant||this.tableVariant||"b-table-default"),[e?"".concat(this.isDark?"bg":"table","-").concat(e):null,a?"b-table-sticky-column":null]},cellAttrs:function(){var e=this.stackedHeading,t=this.inThead||this.inTfoot,a=this.computedColspan,o=this.computedRowspan,s="cell",i=null;return t?(s="columnheader",i=a>0?"colspan":"col"):tc(this.tag,"th")&&(s="rowheader",i=o>0?"rowgroup":"row"),h1(h1({colspan:a,rowspan:o,role:s,scope:i},this.bvAttrs),{},{"data-label":this.isStackedCell&&!xe(e)?jr(e):null})}},render:function(e){var t=[this.normalizeSlot()];return e(this.tag,{class:this.cellClasses,attrs:this.cellAttrs,on:this.bvListeners},[this.isStackedCell?e("div",[t]):t])}});function g1(e,t,a){return t in e?Object.defineProperty(e,t,{value:a,enumerable:!0,configurable:!0,writable:!0}):e[t]=a,e}var v1="busy",A1=Fi+v1,P1=g1({},v1,Wc(qi,!1)),b1=Ms({props:P1,data:function(){return{localBusy:!1}},computed:{computedBusy:function(){return this[v1]||this.localBusy}},watch:{localBusy:function(e,t){e!==t&&this.$emit(A1,e)}},methods:{stopIfBusy:function(e){return!!this.computedBusy&&(ol(e),!0)},renderBusy:function(){var e=this.tbodyTrClass,t=this.tbodyTrAttr,a=this.$createElement;return this.computedBusy&&this.hasNormalizedSlot(pr)?a(n1,{staticClass:"b-table-busy-slot",class:[Be(e)?e(null,pr):e],attrs:Be(t)?t(null,pr):t,key:"table-busy-slot"},[a(f1,{props:{colspan:this.computedFields.length||null}},[this.normalizeSlot(pr)])]):null}}}),y1={caption:Wc(Zi),captionHtml:Wc(Zi)},w1=Ms({props:y1,computed:{captionId:function(){return this.isStacked?this.safeId("_caption_"):null}},methods:{renderCaption:function(){var e=this.caption,t=this.captionHtml,a=this.$createElement,o=a(),s=this.hasNormalizedSlot(ur);return(s||e||t)&&(o=a("caption",{attrs:{id:this.captionId},domProps:s?{}:yO(t,e),key:"caption",ref:"caption"},this.normalizeSlot(ur))),o}}}),I1={},z1=Ms({methods:{renderColgroup:function(){var e=this.computedFields,t=this.$createElement,a=t();return this.hasNormalizedSlot(fr)&&(a=t("colgroup",{key:"colgroup"},[this.normalizeSlot(fr,{columns:e.length,fields:e})])),a}}}),C1={emptyFilteredHtml:Wc(Zi),emptyFilteredText:Wc(Zi,"There are no records matching your request"),emptyHtml:Wc(Zi),emptyText:Wc(Zi,"There are no records to show"),showEmpty:Wc(qi,!1)},D1=Ms({props:C1,methods:{renderEmpty:function(){var e=Jl(this),t=e.computedItems,a=e.computedBusy,o=this.$createElement,s=o();if(this.showEmpty&&(!t||0===t.length)&&(!a||!this.hasNormalizedSlot(pr))){var i=this.computedFields,n=this.isFiltered,r=this.emptyText,c=this.emptyHtml,l=this.emptyFilteredText,h=this.emptyFilteredHtml,d=this.tbodyTrClass,m=this.tbodyTrAttr;s=this.normalizeSlot(n?Sn:Rn,{emptyFilteredHtml:h,emptyFilteredText:l,emptyHtml:c,emptyText:r,fields:i,items:t}),s||(s=o("div",{class:["text-center","my-2"],domProps:n?yO(h,l):yO(c,r)})),s=o(f1,{props:{colspan:i.length||null}},[o("div",{attrs:{role:"alert","aria-live":"polite"}},[s])]),s=o(n1,{staticClass:"b-table-empty-row",class:[Be(d)?d(null,"row-empty"):d],attrs:Be(m)?m(null,"row-empty"):m,key:n?"b-empty-filtered-row":"b-empty-row"},[s])}return s}}}),R1=function e(t){return xe(t)?"":He(t)&&!Ge(t)?at(t).sort().map((function(a){return e(t[a])})).filter((function(e){return!!e})).join(" "):jr(t)};function S1(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function _1(e){for(var t=1;t3&&void 0!==arguments[3]?arguments[3]:{},s=at(o).reduce((function(t,a){var s=o[a],i=s.filterByFormatted,n=Be(i)?i:i?s.formatter:null;return Be(n)&&(t[a]=n(e[a],a,e)),t}),it(e)),i=at(s).filter((function(e){return!x1[e]&&!(Fe(t)&&t.length>0&&Cr(t,e))&&!(Fe(a)&&a.length>0&&!Cr(a,e))}));return nt(s,i)},O1=function(e,t,a,o){return He(e)?R1(L1(e,t,a,o)):""};function E1(e){return j1(e)||H1(e)||F1(e)||U1()}function U1(){throw new TypeError("Invalid attempt to spread non-iterable instance.\nIn order to be iterable, non-array objects must have a [Symbol.iterator]() method.")}function F1(e,t){if(e){if("string"===typeof e)return G1(e,t);var a=Object.prototype.toString.call(e).slice(8,-1);return"Object"===a&&e.constructor&&(a=e.constructor.name),"Map"===a||"Set"===a?Array.from(e):"Arguments"===a||/^(?:Ui|I)nt(?:8|16|32)(?:Clamped)?Array$/.test(a)?G1(e,t):void 0}}function H1(e){if("undefined"!==typeof Symbol&&null!=e[Symbol.iterator]||null!=e["@@iterator"])return Array.from(e)}function j1(e){if(Array.isArray(e))return G1(e)}function G1(e,t){(null==t||t>e.length)&&(t=e.length);for(var a=0,o=new Array(t);a0&&Ct(W1,Go),e},localFiltering:function(){return!this.hasProvider||!!this.noProviderFiltering},filteredCheck:function(){var e=this.filteredItems,t=this.localItems,a=this.localFilter;return{filteredItems:e,localItems:t,localFilter:a}},localFilterFn:function(){var e=this.filterFunction;return Qc(e)?e:null},filteredItems:function(){var e=this.localItems,t=this.localFilter,a=this.localFiltering?this.filterFnFactory(this.localFilterFn,t)||this.defaultFilterFnFactory(t):null;return a&&e.length>0?e.filter(a):e}},watch:{computedFilterDebounce:function(e){!e&&this.$_filterTimer&&(this.clearFilterTimer(),this.localFilter=this.filterSanitize(this.filter))},filter:{deep:!0,handler:function(e){var t=this,a=this.computedFilterDebounce;this.clearFilterTimer(),a&&a>0?this.$_filterTimer=setTimeout((function(){t.localFilter=t.filterSanitize(e)}),a):this.localFilter=this.filterSanitize(e)}},filteredCheck:function(e){var t=e.filteredItems,a=e.localFilter,o=!1;a?iL(a,[])||iL(a,{})?o=!1:a&&(o=!0):o=!1,o&&this.$emit(Zs,t,t.length),this.isFiltered=o},isFiltered:function(e,t){if(!1===e&&!0===t){var a=this.localItems;this.$emit(Zs,a,a.length)}}},created:function(){var e=this;this.$_filterTimer=null,this.$nextTick((function(){e.isFiltered=Boolean(e.localFilter)}))},beforeDestroy:function(){this.clearFilterTimer()},methods:{clearFilterTimer:function(){clearTimeout(this.$_filterTimer),this.$_filterTimer=null},filterSanitize:function(e){return!this.localFiltering||this.localFilterFn||Oe(e)||$e(e)?bt(e):""},filterFnFactory:function(e,t){if(!e||!Be(e)||!t||iL(t,[])||iL(t,{}))return null;var a=function(a){return e(a,t)};return a},defaultFilterFnFactory:function(e){var t=this;if(!e||!Oe(e)&&!$e(e))return null;var a=e;if(Oe(a)){var o=Hr(e).replace(J,"\\s+");a=new RegExp(".*".concat(o,".*"),"i")}var s=function(e){return a.lastIndex=0,a.test(O1(e,t.computedFilterIgnored,t.computedFilterIncluded,t.computedFieldsObj))};return s}}}),q1=function(e,t){var a=null;return Oe(t)?a={key:e,label:t}:Be(t)?a={key:e,formatter:t}:He(t)?(a=it(t),a.key=a.key||e):!1!==t&&(a={key:e}),a},J1=function(e,t){var a=[];if(Fe(e)&&e.filter(yt).forEach((function(e){if(Oe(e))a.push({key:e,label:Er(e)});else if(He(e)&&e.key&&Oe(e.key))a.push(it(e));else if(He(e)&&1===at(e).length){var t=at(e)[0],o=q1(t,e[t]);o&&a.push(o)}})),0===a.length&&Fe(t)&&t.length>0){var o=t[0];at(o).forEach((function(e){x1[e]||a.push({key:e,label:Er(e)})}))}var s={};return a.filter((function(e){return!s[e.key]&&(s[e.key]=!0,e.label=Oe(e.label)?e.label:Er(e.key),!0)}))};function K1(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function Q1(e){for(var t=1;t0&&e.some(yt)},selectableIsMultiSelect:function(){return this.isSelectable&&Cr(["range","multi"],this.selectMode)},selectableTableClasses:function(){var e,t=this.isSelectable;return e={"b-table-selectable":t},d5(e,"b-table-select-".concat(this.selectMode),t),d5(e,"b-table-selecting",this.selectableHasSelection),d5(e,"b-table-selectable-no-click",t&&!this.hasSelectableRowClick),e},selectableTableAttrs:function(){if(!this.isSelectable)return{};var e=this.bvAttrs.role||f5;return{role:e,"aria-multiselectable":e===f5?jr(this.selectableIsMultiSelect):null}}},watch:{computedItems:function(e,t){var a=!1;if(this.isSelectable&&this.selectedRows.length>0){a=Fe(e)&&Fe(t)&&e.length===t.length;for(var o=0;a&&o=0&&e0&&(this.selectedLastClicked=-1,this.selectedRows=this.selectableIsMultiSelect?Rr(e,!0):[!0])},isRowSelected:function(e){return!(!Ee(e)||!this.selectedRows[e])},clearSelected:function(){this.selectedLastClicked=-1,this.selectedRows=[]},selectableRowClasses:function(e){if(this.isSelectable&&this.isRowSelected(e)){var t=this.selectedVariant;return d5({"b-table-row-selected":!0},"".concat(this.dark?"bg":"table","-").concat(t),t)}return{}},selectableRowAttrs:function(e){return{"aria-selected":this.isSelectable?this.isRowSelected(e)?"true":"false":null}},setSelectionHandlers:function(e){var t=e&&!this.noSelectOnClick?"$on":"$off";this[t](yi,this.selectionHandler),this[t](Zs,this.clearSelected),this[t](Ns,this.clearSelected)},selectionHandler:function(e,t,a){if(this.isSelectable&&!this.noSelectOnClick){var o=this.selectMode,s=this.selectedLastRow,i=this.selectedRows.slice(),n=!i[t];if("single"===o)i=[];else if("range"===o)if(s>-1&&a.shiftKey){for(var r=Ml(s,t);r<=Tl(s,t);r++)i[r]=!0;n=!0}else a.ctrlKey||a.metaKey||(i=[],n=!0),n&&(this.selectedLastRow=t);i[t]=n,this.selectedRows=i}else this.clearSelected()}}}),A5=function(e,t){return e.map((function(e,t){return[t,e]})).sort(function(e,t){return this(e[1],t[1])||e[0]-t[0]}.bind(t)).map((function(e){return e[1]}))},P5=function(e){return xe(e)?"":Ue(e)?xr(e,e):e},b5=function(e,t){var a=arguments.length>2&&void 0!==arguments[2]?arguments[2]:{},o=a.sortBy,s=void 0===o?null:o,i=a.formatter,n=void 0===i?null:i,r=a.locale,c=void 0===r?void 0:r,l=a.localeOptions,h=void 0===l?{}:l,d=a.nullLast,m=void 0!==d&&d,p=It(e,s,null),u=It(t,s,null);return Be(n)&&(p=n(p,s,e),u=n(u,s,t)),p=P5(p),u=P5(u),Ge(p)&&Ge(u)||Ee(p)&&Ee(u)?pu?1:0:m&&""===p&&""!==u?1:m&&""!==p&&""===u?-1:R1(p).localeCompare(R1(u),c,h)};function y5(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function w5(e){for(var t=1;t0&&void 0!==arguments[0]?arguments[0]:document,t=zc();return!!(t&&""!==t.toString().trim()&&t.containsNode&&Zr(e))&&t.containsNode(e,!0)},j5=Jc(u1,Qo),G5=Ms({name:Qo,extends:f1,props:j5,computed:{tag:function(){return"th"}}});function W5(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function N5(e){for(var t=1;te.length)&&(t=e.length);for(var a=0,o=new Array(t);a0&&(P=String((r-1)*c+t+1));var b=jr(It(e,n))||null,y=b||jr(t),w=b?this.safeId("_row_".concat(b)):null,I=Jl(this).selectableRowClasses?this.selectableRowClasses(t):{},z=Jl(this).selectableRowAttrs?this.selectableRowAttrs(t):{},C=Be(l)?l(e,"row"):l,D=Be(h)?h(e,"row"):h;if(g.push(m(n1,$5({class:[C,I,u?"b-table-has-details":""],props:{variant:e[T1]||null},attrs:N5(N5({id:w},D),{},{tabindex:f?"0":null,"data-pk":b||null,"aria-details":v,"aria-owns":v,"aria-rowindex":P},z),on:{mouseenter:this.rowHovered,mouseleave:this.rowUnhovered},key:"__b-table-row-".concat(y,"__"),ref:"item-rows"},_s,!0),A)),u){var R={item:e,index:t,fields:s,toggleDetails:this.toggleDetailsFactory(p,e)};Jl(this).supportsSelectableRows&&(R.rowSelected=this.isRowSelected(t),R.selectRow=function(){return a.selectRow(t)},R.unselectRow=function(){return a.unselectRow(t)});var S=m(f1,{props:{colspan:s.length},class:this.detailsTdClass},[this.normalizeSlot(mr,R)]);i&&g.push(m("tr",{staticClass:"d-none",attrs:{"aria-hidden":"true",role:"presentation"},key:"__b-table-details-stripe__".concat(y)}));var _=Be(this.tbodyTrClass)?this.tbodyTrClass(e,mr):this.tbodyTrClass,k=Be(this.tbodyTrAttr)?this.tbodyTrAttr(e,mr):this.tbodyTrAttr;g.push(m(n1,{staticClass:"b-table-details",class:[_],props:{variant:e[T1]||null},attrs:N5(N5({},k),{},{id:v,tabindex:"-1"}),key:"__b-table-details__".concat(y)},[S]))}else p&&(g.push(m()),i&&g.push(m()));return g}}});function t2(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function a2(e){for(var t=1;t0&&a&&a.length>0?zr(t.children).filter((function(e){return Cr(a,e)})):[]},getTbodyTrIndex:function(e){if(!Zr(e))return-1;var t="TR"===e.tagName?e:lc("tr",e,!0);return t?this.getTbodyTrs().indexOf(t):-1},emitTbodyRowEvent:function(e,t){if(e&&this.hasListener(e)&&t&&t.target){var a=this.getTbodyTrIndex(t.target);if(a>-1){var o=this.computedItems[a];this.$emit(e,o,a,t)}}},tbodyRowEventStopped:function(e){return this.stopIfBusy&&this.stopIfBusy(e)},onTbodyRowKeydown:function(e){var t=e.target,a=e.keyCode;if(!this.tbodyRowEventStopped(e)&&"TR"===t.tagName&&ac(t)&&0===t.tabIndex)if(Cr([KB,aL],a))ol(e),this.onTBodyRowClicked(e);else if(Cr([oL,qB,YB,JB],a)){var o=this.getTbodyTrIndex(t);if(o>-1){ol(e);var s=this.getTbodyTrs(),i=e.shiftKey;a===YB||i&&a===oL?Sc(s[0]):a===JB||i&&a===qB?Sc(s[s.length-1]):a===oL&&o>0?Sc(s[o-1]):a===qB&&oe.length)&&(t=e.length);for(var a=0,o=new Array(t);a0&&void 0!==arguments[0]&&arguments[0],a=Jl(this),o=a.computedFields,s=a.isSortable,i=a.isSelectable,n=a.headVariant,r=a.footVariant,c=a.headRowVariant,l=a.footRowVariant,h=this.$createElement;if(this.isStackedAlways||0===o.length)return h();var d=s||this.hasListener(si),m=i?this.selectAllRows:QU,p=i?this.clearSelected:QU,u=function(a,o){var i=a.label,n=a.labelHtml,r=a.variant,c=a.stickyColumn,l=a.key,u=null;a.label.trim()||a.headerTitle||(u=Er(a.key));var f={};d&&(f.click=function(o){e.headClicked(o,a,t)},f.keydown=function(o){var s=o.keyCode;s!==KB&&s!==aL||e.headClicked(o,a,t)});var g=s?e.sortTheadThAttrs(l,a,t):{},v=s?e.sortTheadThClasses(l,a,t):null,A=s?e.sortTheadThLabel(l,a,t):null,P={class:[{"position-relative":A},e.fieldClasses(a),v],props:{variant:r,stickyColumn:c},style:a.thStyle||{},attrs:D2(D2({tabindex:d&&a.sortable?"0":null,abbr:a.headerAbbr||null,title:a.headerTitle||null,"aria-colindex":o+1,"aria-label":u},e.getThValues(null,l,a.thAttr,t?"foot":"head",{})),g),on:f,key:l},b=[S2(l),S2(l.toLowerCase()),S2()];t&&(b=[_2(l),_2(l.toLowerCase()),_2()].concat(P2(b)));var y={label:i,column:l,field:a,isFoot:t,selectAllRows:m,clearSelected:p},w=e.normalizeSlot(b,y)||h("div",{domProps:yO(n,i)}),I=A?h("span",{staticClass:"sr-only"}," (".concat(A,")")):null;return h(G5,P,[w,I].filter(yt))},f=o.map(u).filter(yt),g=[];if(t)g.push(h(n1,{class:this.tfootTrClass,props:{variant:xe(l)?c:l}},f));else{var v={columns:o.length,fields:o,selectAllRows:m,clearSelected:p};g.push(this.normalizeSlot(Pr,v)||h()),g.push(h(n1,{class:this.theadTrClass,props:{variant:c}},f))}return h(t?d2:A2,{class:(t?this.tfootClass:this.theadClass)||null,props:t?{footVariant:r||n||null}:{headVariant:n||null},key:t?"bv-tfoot":"bv-thead"},g)}}}),T2={},V2=Ms({methods:{renderTopRow:function(){var e=this.computedFields,t=this.stacked,a=this.tbodyTrClass,o=this.tbodyTrAttr,s=this.$createElement;return this.hasNormalizedSlot(wr)&&!0!==t&&""!==t?s(n1,{staticClass:"b-table-top-row",class:[Be(a)?a(null,"row-top"):a],attrs:Be(o)?o(null,"row-top"):o,key:"b-top-row"},[this.normalizeSlot(wr,{columns:e.length,fields:e})]):s()}}});function x2(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function B2(e){for(var t=1;t0&&void 0!==arguments[0])||arguments[0];if(this.$_observer&&this.$_observer.disconnect(),this.$_observer=null,t){var a=function(){e.$nextTick((function(){Qr((function(){e.updateTabs()}))}))};this.$_observer=tF(this.$refs.content,a,{childList:!0,subtree:!1,attributes:!0,attributeFilter:["id"]})}},getTabs:function(){var e=this.registeredTabs,t=[];if(I&&e.length>0){var a=e.map((function(e){return"#".concat(e.safeId())})).join(", ");t=nc(a,this.$el).map((function(e){return e.id})).filter(yt)}return A5(e,(function(e,a){return t.indexOf(e.safeId())-t.indexOf(a.safeId())}))},updateTabs:function(){var e=this.getTabs(),t=e.indexOf(e.slice().reverse().find((function(e){return e.localActive&&!e.disabled})));if(t<0){var a=this.currentTab;a>=e.length?t=e.indexOf(e.slice().reverse().find(s3)):e[a]&&!e[a].disabled&&(t=a)}t<0&&(t=e.indexOf(e.find(s3))),e.forEach((function(e,a){e.localActive=a===t})),this.tabs=e,this.currentTab=t},getButtonForTab:function(e){return(this.$refs.buttons||[]).find((function(t){return t.tab===e}))},updateButton:function(e){var t=this.getButtonForTab(e);t&&t.$forceUpdate&&t.$forceUpdate()},activateTab:function(e){var t=this.currentTab,a=this.tabs,o=!1;if(e){var s=a.indexOf(e);if(s!==t&&s>-1&&!e.disabled){var i=new UH(Os,{cancelable:!0,vueTarget:this,componentId:this.safeId()});this.$emit(i.type,s,t,i),i.defaultPrevented||(this.currentTab=s,o=!0)}}return o||this[a3]===t||this.$emit(o3,t),o},deactivateTab:function(e){return!!e&&this.activateTab(this.tabs.filter((function(t){return t!==e})).find(s3))},focusButton:function(e){var t=this;this.$nextTick((function(){Sc(t.getButtonForTab(e))}))},emitTabClick:function(e,t){We(t)&&e&&e.$emit&&!e.disabled&&e.$emit(js,t)},clickTab:function(e,t){this.activateTab(e),this.emitTabClick(e,t)},firstTab:function(e){var t=this.tabs.find(s3);this.activateTab(t)&&e&&(this.focusButton(t),this.emitTabClick(t,e))},previousTab:function(e){var t=Tl(this.currentTab,0),a=this.tabs.slice(0,t).reverse().find(s3);this.activateTab(a)&&e&&(this.focusButton(a),this.emitTabClick(a,e))},nextTab:function(e){var t=Tl(this.currentTab,-1),a=this.tabs.slice(t+1).find(s3);this.activateTab(a)&&e&&(this.focusButton(a),this.emitTabClick(a,e))},lastTab:function(e){var t=this.tabs.slice().reverse().find(s3);this.activateTab(t)&&e&&(this.focusButton(t),this.emitTabClick(t,e))}},render:function(e){var t=this,a=this.align,o=this.card,s=this.end,i=this.fill,n=this.firstTab,r=this.justified,c=this.lastTab,l=this.nextTab,h=this.noKeyNav,d=this.noNavStyle,m=this.pills,p=this.previousTab,u=this.small,f=this.tabs,g=this.vertical,v=f.find((function(e){return e.localActive&&!e.disabled})),A=f.find((function(e){return!e.disabled})),P=f.map((function(a,o){var s,i=a.safeId,r=null;return h||(r=-1,(a===v||!v&&a===A)&&(r=null)),e(i3,Q2({props:{controls:i?i():null,id:a.controlledBy||(i?i("_BV_tab_button_"):null),noKeyNav:h,posInSet:o+1,setSize:f.length,tab:a,tabIndex:r},on:(s={},Q2(s,js,(function(e){t.clickTab(a,e)})),Q2(s,ei,n),Q2(s,vi,p),Q2(s,mi,l),Q2(s,li,c),s),key:a[Rs]||o,ref:"buttons"},_s,!0))})),b=e(QQ,{class:this.localNavClass,attrs:{role:"tablist",id:this.safeId("_BV_tab_controls_")},props:{fill:i,justified:r,align:a,tabs:!d&&!m,pills:!d&&m,vertical:g,small:u,cardHeader:o&&!g},ref:"nav"},[this.normalizeSlot(vr)||e(),P,this.normalizeSlot(gr)||e()]);b=e("div",{class:[{"card-header":o&&!g&&!s,"card-footer":o&&!g&&s,"col-auto":g},this.navWrapperClass],key:"bv-tabs-nav"},[b]);var y=this.normalizeSlot()||[],w=e();0===y.length&&(w=e("div",{class:["tab-pane","active",{"card-body":o}],key:"bv-empty-tab"},this.normalizeSlot(Rn)));var I=e("div",{staticClass:"tab-content",class:[{col:g},this.contentClass],attrs:{id:this.safeId("_BV_tab_container_")},key:"bv-content",ref:"content"},[y,w]);return e(this.tag,{staticClass:"tabs",class:{row:g,"no-gutters":g&&o},attrs:{id:this.safeId()}},[s?I:e(),b,s?e():I])}});function l3(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function h3(e){for(var t=1;t" with name "'.concat(e,'" already exists in the document.'),es),this.dead=!0):this.doRender=!0},beforeDestroy:function(){this.doRender&&this.emitOnRoot(il(es,$s),this.name)},destroyed:function(){var e=this.$el;e&&e.parentNode&&e.parentNode.removeChild(e)},render:function(e){var t=e("div",{class:["d-none",{"b-dead-toaster":this.dead}]});if(this.doRender){var a=e(P3["PortalTarget"],{staticClass:"b-toaster-slot",props:{name:this.staticName,multiple:!0,tag:"div",slim:!1,transition:b3}});t=e("div",{staticClass:"b-toaster",class:[this.staticName],attrs:{id:this.staticName,role:this.role||null,"aria-live":this.ariaLive,"aria-atomic":this.ariaAtomic}},[a])}return t}});function I3(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function z3(e){for(var t=1;t1&&void 0!==arguments[1]?arguments[1]:{};return new UH(e,z3(z3({cancelable:!1,target:this.$el||null,relatedTarget:null},t),{},{vueTarget:this,componentId:this.safeId()}))},emitEvent:function(e){var t=e.type;this.emitOnRoot(il(Zo,t),e),this.$emit(t,e)},ensureToaster:function(){if(!this.static){var e=this.computedToaster;if(!P3["Wormhole"].hasTarget(e)){var t=document.createElement("div");document.body.appendChild(t);var a=wK(this.bvEventRoot,w3,{propsData:{name:e}});a.$mount(t)}}},startDismissTimer:function(){this.clearDismissTimer(),this.noAutoHide||(this.$_dismissTimer=setTimeout(this.hide,this.resumeDismiss||this.computedDuration),this.dismissStarted=Date.now(),this.resumeDismiss=0)},clearDismissTimer:function(){clearTimeout(this.$_dismissTimer),this.$_dismissTimer=null},setHoverHandler:function(e){var t=this.$refs["b-toast"];al(e,t,"mouseenter",this.onPause,Wi),al(e,t,"mouseleave",this.onUnPause,Wi)},onPause:function(){if(!this.noAutoHide&&!this.noHoverPause&&this.$_dismissTimer&&!this.resumeDismiss){var e=Date.now()-this.dismissStarted;e>0&&(this.clearDismissTimer(),this.resumeDismiss=Tl(this.computedDuration-e,M3))}},onUnPause:function(){this.noAutoHide||this.noHoverPause||!this.resumeDismiss?this.resumeDismiss=this.dismissStarted=0:this.startDismissTimer()},onLinkClick:function(){var e=this;this.$nextTick((function(){Qr((function(){e.hide()}))}))},onBeforeEnter:function(){this.isTransitioning=!0},onAfterEnter:function(){this.isTransitioning=!1;var e=this.buildEvent(ki);this.emitEvent(e),this.startDismissTimer(),this.setHoverHandler(!0)},onBeforeLeave:function(){this.isTransitioning=!0},onAfterLeave:function(){this.isTransitioning=!1,this.order=0,this.resumeDismiss=this.dismissStarted=0;var e=this.buildEvent(ii);this.emitEvent(e),this.doRender=!1},makeToast:function(e){var t=this,a=this.title,o=this.slotScope,s=th(this),i=[],n=this.normalizeSlot(yr,o);n?i.push(n):a&&i.push(e("strong",{staticClass:"mr-2"},a)),this.noCloseButton||i.push(e(ll,{staticClass:"ml-auto mb-1",on:{click:function(){t.hide()}}}));var r=e();i.length>0&&(r=e(this.headerTag,{staticClass:"toast-header",class:this.headerClass},i));var c=e(s?EL:"div",{staticClass:"toast-body",class:this.bodyClass,props:s?$c(T3,this):{},on:s?{click:this.onLinkClick}:{}},this.normalizeSlot(wn,o));return e("div",{staticClass:"toast",class:this.toastClass,attrs:this.computedAttrs,key:"toast-".concat(this[Rs]),ref:"toast"},[r,c])}},render:function(e){if(!this.doRender||!this.isMounted)return e();var t=this.order,a=this.static,o=this.isHiding,s=this.isStatus,i="b-toast-".concat(this[Rs]),n=e("div",{staticClass:"b-toast",class:this.toastClasses,attrs:z3(z3({},a?{}:this.scopedStyleAttrs),{},{id:this.safeId("_toast_outer"),role:o?null:s?"status":"alert","aria-live":o?null:s?"polite":"assertive","aria-atomic":o?null:"true"}),key:i,ref:"b-toast"},[e(vl,{props:{noFade:this.noFade},on:this.transitionHandlers},[this.localShow?this.makeToast(e):e()])]);return e(P3["Portal"],{props:{name:i,to:this.computedToaster,order:t,slim:!0,disabled:a}},[n])}});function B3(e,t){if(!(e instanceof t))throw new TypeError("Cannot call a class as a function")}function L3(e,t){for(var a=0;ae.length)&&(t=e.length);for(var a=0,o=new Array(t);a1&&void 0!==arguments[1]?arguments[1]:{};e&&!Dt(q3)&&a(U3(U3({},Y3(t)),{},{toastContent:e}),this._vm)}},{key:"show",value:function(e){e&&this._root.$emit(nl(Zo,_i),e)}},{key:"hide",value:function(){var e=arguments.length>0&&void 0!==arguments[0]?arguments[0]:null;this._root.$emit(nl(Zo,ni),e)}}]),e}();e.mixin({beforeCreate:function(){this[J3]=new o(this)}}),ot(e.prototype,q3)||et(e.prototype,q3,{get:function(){return this&&this[J3]||Ct('"'.concat(q3,'" must be accessed from a Vue instance "this" context.'),Zo),this[J3]}})},Z3=Ft({plugins:{plugin:X3}}),e4=Ft({components:{BToast:x3,BToaster:w3},plugins:{BVToastPlugin:Z3}});function t4(e,t){var a=Object.keys(e);if(Object.getOwnPropertySymbols){var o=Object.getOwnPropertySymbols(e);t&&(o=o.filter((function(t){return Object.getOwnPropertyDescriptor(e,t).enumerable}))),a.push.apply(a,o)}return a}function a4(e){for(var t=1;t=a){var o=this.$targets[this.$targets.length-1];this.$activeTarget!==o&&this.activate(o)}else{if(this.$activeTarget&&e0)return this.$activeTarget=null,void this.clear();for(var s=this.$offsets.length;s--;){var i=this.$activeTarget!==this.$targets[s]&&e>=this.$offsets[s]&&(Te(this.$offsets[s+1])||e0&&this.$root&&this.$root.$emit(G4,e,a)}},{key:"clear",value:function(){var e=this;nc("".concat(this.$selector,", ").concat(E4),this.$el).filter((function(e){return uc(e,B4)})).forEach((function(t){return e.setActiveState(t,!1)}))}},{key:"setActiveState",value:function(e,t){e&&(t?mc(e,B4):pc(e,B4))}}],[{key:"Name",get:function(){return V4}},{key:"Default",get:function(){return $4}},{key:"DefaultType",get:function(){return q4}}]),e}(),X4="__BV_Scrollspy__",Z4=/^\d+$/,e8=/^(auto|position|offset)$/,t8=function(e){var t={};return e.arg&&(t.element="#".concat(e.arg)),at(e.modifiers).forEach((function(e){Z4.test(e)?t.offset=Vr(e,0):e8.test(e)&&(t.method=e)})),Oe(e.value)?t.element=e.value:Ee(e.value)?t.offset=Ol(e.value):He(e.value)&&at(e.value).filter((function(e){return!!Y4.DefaultType[e]})).forEach((function(a){t[a]=e.value[a]})),t},a8=function(e,t,a){if(I){var o=t8(t);e[X4]?e[X4].updateConfig(o,gL(YF(a,t))):e[X4]=new Y4(e,o,gL(YF(a,t)))}},o8=function(e){e[X4]&&(e[X4].dispose(),e[X4]=null,delete e[X4])},s8={bind:function(e,t,a){a8(e,t,a)},inserted:function(e,t,a){a8(e,t,a)},update:function(e,t,a){t.value!==t.oldValue&&a8(e,t,a)},componentUpdated:function(e,t,a){t.value!==t.oldValue&&a8(e,t,a)},unbind:function(e){o8(e)}},i8=Ft({directives:{VBScrollspy:s8}}),n8=Ft({directives:{VBVisible:MU}}),r8=Ft({plugins:{VBHoverPlugin:C4,VBModalPlugin:D4,VBPopoverPlugin:EZ,VBScrollspyPlugin:i8,VBTogglePlugin:RH,VBTooltipPlugin:w4,VBVisiblePlugin:n8}}),c8="BootstrapVue",l8=Et({plugins:{componentsPlugin:z4,directivesPlugin:r8}}),h8={install:l8,NAME:c8},d8=Jc(rt(lh,["content","stacked"]),eo),m8=Ms({name:eo,functional:!0,props:d8,render:function(e,t){var a=t.data,o=t.props,s=t.children;return e(hh,bs(a,{staticClass:"b-iconstack",props:o}),s)}}),p8=Ht({components:{BIcon:WB,BIconstack:m8,BIconBlank:gh,BIconAlarm:vh,BIconAlarmFill:Ah,BIconAlignBottom:Ph,BIconAlignCenter:bh,BIconAlignEnd:yh,BIconAlignMiddle:wh,BIconAlignStart:Ih,BIconAlignTop:zh,BIconAlt:Ch,BIconApp:Dh,BIconAppIndicator:Rh,BIconArchive:Sh,BIconArchiveFill:_h,BIconArrow90degDown:kh,BIconArrow90degLeft:Mh,BIconArrow90degRight:Th,BIconArrow90degUp:Vh,BIconArrowBarDown:xh,BIconArrowBarLeft:Bh,BIconArrowBarRight:Lh,BIconArrowBarUp:Oh,BIconArrowClockwise:Eh,BIconArrowCounterclockwise:Uh,BIconArrowDown:Fh,BIconArrowDownCircle:Hh,BIconArrowDownCircleFill:jh,BIconArrowDownLeft:Gh,BIconArrowDownLeftCircle:Wh,BIconArrowDownLeftCircleFill:Nh,BIconArrowDownLeftSquare:$h,BIconArrowDownLeftSquareFill:qh,BIconArrowDownRight:Jh,BIconArrowDownRightCircle:Kh,BIconArrowDownRightCircleFill:Qh,BIconArrowDownRightSquare:Yh,BIconArrowDownRightSquareFill:Xh,BIconArrowDownShort:Zh,BIconArrowDownSquare:ed,BIconArrowDownSquareFill:td,BIconArrowDownUp:ad,BIconArrowLeft:od,BIconArrowLeftCircle:sd,BIconArrowLeftCircleFill:id,BIconArrowLeftRight:nd,BIconArrowLeftShort:rd,BIconArrowLeftSquare:cd,BIconArrowLeftSquareFill:ld,BIconArrowRepeat:hd,BIconArrowReturnLeft:dd,BIconArrowReturnRight:md,BIconArrowRight:pd,BIconArrowRightCircle:ud,BIconArrowRightCircleFill:fd,BIconArrowRightShort:gd,BIconArrowRightSquare:vd,BIconArrowRightSquareFill:Ad,BIconArrowUp:Pd,BIconArrowUpCircle:bd,BIconArrowUpCircleFill:yd,BIconArrowUpLeft:wd,BIconArrowUpLeftCircle:Id,BIconArrowUpLeftCircleFill:zd,BIconArrowUpLeftSquare:Cd,BIconArrowUpLeftSquareFill:Dd,BIconArrowUpRight:Rd,BIconArrowUpRightCircle:Sd,BIconArrowUpRightCircleFill:_d,BIconArrowUpRightSquare:kd,BIconArrowUpRightSquareFill:Md,BIconArrowUpShort:Td,BIconArrowUpSquare:Vd,BIconArrowUpSquareFill:xd,BIconArrowsAngleContract:Bd,BIconArrowsAngleExpand:Ld,BIconArrowsCollapse:Od,BIconArrowsExpand:Ed,BIconArrowsFullscreen:Ud,BIconArrowsMove:Fd,BIconAspectRatio:Hd,BIconAspectRatioFill:jd,BIconAsterisk:Gd,BIconAt:Wd,BIconAward:Nd,BIconAwardFill:$d,BIconBack:qd,BIconBackspace:Jd,BIconBackspaceFill:Kd,BIconBackspaceReverse:Qd,BIconBackspaceReverseFill:Yd,BIconBadge3d:Xd,BIconBadge3dFill:Zd,BIconBadge4k:em,BIconBadge4kFill:tm,BIconBadge8k:am,BIconBadge8kFill:om,BIconBadgeAd:sm,BIconBadgeAdFill:im,BIconBadgeAr:nm,BIconBadgeArFill:rm,BIconBadgeCc:cm,BIconBadgeCcFill:lm,BIconBadgeHd:hm,BIconBadgeHdFill:dm,BIconBadgeTm:mm,BIconBadgeTmFill:pm,BIconBadgeVo:um,BIconBadgeVoFill:fm,BIconBadgeVr:gm,BIconBadgeVrFill:vm,BIconBadgeWc:Am,BIconBadgeWcFill:Pm,BIconBag:bm,BIconBagCheck:ym,BIconBagCheckFill:wm,BIconBagDash:Im,BIconBagDashFill:zm,BIconBagFill:Cm,BIconBagPlus:Dm,BIconBagPlusFill:Rm,BIconBagX:Sm,BIconBagXFill:_m,BIconBank:km,BIconBank2:Mm,BIconBarChart:Tm,BIconBarChartFill:Vm,BIconBarChartLine:xm,BIconBarChartLineFill:Bm,BIconBarChartSteps:Lm,BIconBasket:Om,BIconBasket2:Em,BIconBasket2Fill:Um,BIconBasket3:Fm,BIconBasket3Fill:Hm,BIconBasketFill:jm,BIconBattery:Gm,BIconBatteryCharging:Wm,BIconBatteryFull:Nm,BIconBatteryHalf:$m,BIconBell:qm,BIconBellFill:Jm,BIconBellSlash:Km,BIconBellSlashFill:Qm,BIconBezier:Ym,BIconBezier2:Xm,BIconBicycle:Zm,BIconBinoculars:ep,BIconBinocularsFill:tp,BIconBlockquoteLeft:ap,BIconBlockquoteRight:op,BIconBook:sp,BIconBookFill:ip,BIconBookHalf:np,BIconBookmark:rp,BIconBookmarkCheck:cp,BIconBookmarkCheckFill:lp,BIconBookmarkDash:hp,BIconBookmarkDashFill:dp,BIconBookmarkFill:mp,BIconBookmarkHeart:pp,BIconBookmarkHeartFill:up,BIconBookmarkPlus:fp,BIconBookmarkPlusFill:gp,BIconBookmarkStar:vp,BIconBookmarkStarFill:Ap,BIconBookmarkX:Pp,BIconBookmarkXFill:bp,BIconBookmarks:yp,BIconBookmarksFill:wp,BIconBookshelf:Ip,BIconBootstrap:zp,BIconBootstrapFill:Cp,BIconBootstrapReboot:Dp,BIconBorder:Rp,BIconBorderAll:Sp,BIconBorderBottom:_p,BIconBorderCenter:kp,BIconBorderInner:Mp,BIconBorderLeft:Tp,BIconBorderMiddle:Vp,BIconBorderOuter:xp,BIconBorderRight:Bp,BIconBorderStyle:Lp,BIconBorderTop:Op,BIconBorderWidth:Ep,BIconBoundingBox:Up,BIconBoundingBoxCircles:Fp,BIconBox:Hp,BIconBoxArrowDown:jp,BIconBoxArrowDownLeft:Gp,BIconBoxArrowDownRight:Wp,BIconBoxArrowInDown:Np,BIconBoxArrowInDownLeft:$p,BIconBoxArrowInDownRight:qp,BIconBoxArrowInLeft:Jp,BIconBoxArrowInRight:Kp,BIconBoxArrowInUp:Qp,BIconBoxArrowInUpLeft:Yp,BIconBoxArrowInUpRight:Xp,BIconBoxArrowLeft:Zp,BIconBoxArrowRight:eu,BIconBoxArrowUp:tu,BIconBoxArrowUpLeft:au,BIconBoxArrowUpRight:ou,BIconBoxSeam:su,BIconBraces:iu,BIconBricks:nu,BIconBriefcase:ru,BIconBriefcaseFill:cu,BIconBrightnessAltHigh:lu,BIconBrightnessAltHighFill:hu,BIconBrightnessAltLow:du,BIconBrightnessAltLowFill:mu,BIconBrightnessHigh:pu,BIconBrightnessHighFill:uu,BIconBrightnessLow:fu,BIconBrightnessLowFill:gu,BIconBroadcast:vu,BIconBroadcastPin:Au,BIconBrush:Pu,BIconBrushFill:bu,BIconBucket:yu,BIconBucketFill:wu,BIconBug:Iu,BIconBugFill:zu,BIconBuilding:Cu,BIconBullseye:Du,BIconCalculator:Ru,BIconCalculatorFill:Su,BIconCalendar:_u,BIconCalendar2:ku,BIconCalendar2Check:Mu,BIconCalendar2CheckFill:Tu,BIconCalendar2Date:Vu,BIconCalendar2DateFill:xu,BIconCalendar2Day:Bu,BIconCalendar2DayFill:Lu,BIconCalendar2Event:Ou,BIconCalendar2EventFill:Eu,BIconCalendar2Fill:Uu,BIconCalendar2Minus:Fu,BIconCalendar2MinusFill:Hu,BIconCalendar2Month:ju,BIconCalendar2MonthFill:Gu,BIconCalendar2Plus:Wu,BIconCalendar2PlusFill:Nu,BIconCalendar2Range:$u,BIconCalendar2RangeFill:qu,BIconCalendar2Week:Ju,BIconCalendar2WeekFill:Ku,BIconCalendar2X:Qu,BIconCalendar2XFill:Yu,BIconCalendar3:Xu,BIconCalendar3Event:Zu,BIconCalendar3EventFill:ef,BIconCalendar3Fill:tf,BIconCalendar3Range:af,BIconCalendar3RangeFill:of,BIconCalendar3Week:sf,BIconCalendar3WeekFill:nf,BIconCalendar4:rf,BIconCalendar4Event:cf,BIconCalendar4Range:lf,BIconCalendar4Week:hf,BIconCalendarCheck:df,BIconCalendarCheckFill:mf,BIconCalendarDate:pf,BIconCalendarDateFill:uf,BIconCalendarDay:ff,BIconCalendarDayFill:gf,BIconCalendarEvent:vf,BIconCalendarEventFill:Af,BIconCalendarFill:Pf,BIconCalendarMinus:bf,BIconCalendarMinusFill:yf,BIconCalendarMonth:wf,BIconCalendarMonthFill:If,BIconCalendarPlus:zf,BIconCalendarPlusFill:Cf,BIconCalendarRange:Df,BIconCalendarRangeFill:Rf,BIconCalendarWeek:Sf,BIconCalendarWeekFill:_f,BIconCalendarX:kf,BIconCalendarXFill:Mf,BIconCamera:Tf,BIconCamera2:Vf,BIconCameraFill:xf,BIconCameraReels:Bf,BIconCameraReelsFill:Lf,BIconCameraVideo:Of,BIconCameraVideoFill:Ef,BIconCameraVideoOff:Uf,BIconCameraVideoOffFill:Ff,BIconCapslock:Hf,BIconCapslockFill:jf,BIconCardChecklist:Gf,BIconCardHeading:Wf,BIconCardImage:Nf,BIconCardList:$f,BIconCardText:qf,BIconCaretDown:Jf,BIconCaretDownFill:Kf,BIconCaretDownSquare:Qf,BIconCaretDownSquareFill:Yf,BIconCaretLeft:Xf,BIconCaretLeftFill:Zf,BIconCaretLeftSquare:eg,BIconCaretLeftSquareFill:tg,BIconCaretRight:ag,BIconCaretRightFill:og,BIconCaretRightSquare:sg,BIconCaretRightSquareFill:ig,BIconCaretUp:ng,BIconCaretUpFill:rg,BIconCaretUpSquare:cg,BIconCaretUpSquareFill:lg,BIconCart:hg,BIconCart2:dg,BIconCart3:mg,BIconCart4:pg,BIconCartCheck:ug,BIconCartCheckFill:fg,BIconCartDash:gg,BIconCartDashFill:vg,BIconCartFill:Ag,BIconCartPlus:Pg,BIconCartPlusFill:bg,BIconCartX:yg,BIconCartXFill:wg,BIconCash:Ig,BIconCashCoin:zg,BIconCashStack:Cg,BIconCast:Dg,BIconChat:Rg,BIconChatDots:Sg,BIconChatDotsFill:_g,BIconChatFill:kg,BIconChatLeft:Mg,BIconChatLeftDots:Tg,BIconChatLeftDotsFill:Vg,BIconChatLeftFill:xg,BIconChatLeftQuote:Bg,BIconChatLeftQuoteFill:Lg,BIconChatLeftText:Og,BIconChatLeftTextFill:Eg,BIconChatQuote:Ug,BIconChatQuoteFill:Fg,BIconChatRight:Hg,BIconChatRightDots:jg,BIconChatRightDotsFill:Gg,BIconChatRightFill:Wg,BIconChatRightQuote:Ng,BIconChatRightQuoteFill:$g,BIconChatRightText:qg,BIconChatRightTextFill:Jg,BIconChatSquare:Kg,BIconChatSquareDots:Qg,BIconChatSquareDotsFill:Yg,BIconChatSquareFill:Xg,BIconChatSquareQuote:Zg,BIconChatSquareQuoteFill:ev,BIconChatSquareText:tv,BIconChatSquareTextFill:av,BIconChatText:ov,BIconChatTextFill:sv,BIconCheck:iv,BIconCheck2:nv,BIconCheck2All:rv,BIconCheck2Circle:cv,BIconCheck2Square:lv,BIconCheckAll:hv,BIconCheckCircle:dv,BIconCheckCircleFill:mv,BIconCheckLg:pv,BIconCheckSquare:uv,BIconCheckSquareFill:fv,BIconChevronBarContract:gv,BIconChevronBarDown:vv,BIconChevronBarExpand:Av,BIconChevronBarLeft:Pv,BIconChevronBarRight:bv,BIconChevronBarUp:yv,BIconChevronCompactDown:wv,BIconChevronCompactLeft:Iv,BIconChevronCompactRight:zv,BIconChevronCompactUp:Cv,BIconChevronContract:Dv,BIconChevronDoubleDown:Rv,BIconChevronDoubleLeft:Sv,BIconChevronDoubleRight:_v,BIconChevronDoubleUp:kv,BIconChevronDown:Mv,BIconChevronExpand:Tv,BIconChevronLeft:Vv,BIconChevronRight:xv,BIconChevronUp:Bv,BIconCircle:Lv,BIconCircleFill:Ov,BIconCircleHalf:Ev,BIconCircleSquare:Uv,BIconClipboard:Fv,BIconClipboardCheck:Hv,BIconClipboardData:jv,BIconClipboardMinus:Gv,BIconClipboardPlus:Wv,BIconClipboardX:Nv,BIconClock:$v,BIconClockFill:qv,BIconClockHistory:Jv,BIconCloud:Kv,BIconCloudArrowDown:Qv,BIconCloudArrowDownFill:Yv,BIconCloudArrowUp:Xv,BIconCloudArrowUpFill:Zv,BIconCloudCheck:eA,BIconCloudCheckFill:tA,BIconCloudDownload:aA,BIconCloudDownloadFill:oA,BIconCloudDrizzle:sA,BIconCloudDrizzleFill:iA,BIconCloudFill:nA,BIconCloudFog:rA,BIconCloudFog2:cA,BIconCloudFog2Fill:lA,BIconCloudFogFill:hA,BIconCloudHail:dA,BIconCloudHailFill:mA,BIconCloudHaze:pA,BIconCloudHaze1:uA,BIconCloudHaze2Fill:fA,BIconCloudHazeFill:gA,BIconCloudLightning:vA,BIconCloudLightningFill:AA,BIconCloudLightningRain:PA,BIconCloudLightningRainFill:bA,BIconCloudMinus:yA,BIconCloudMinusFill:wA,BIconCloudMoon:IA,BIconCloudMoonFill:zA,BIconCloudPlus:CA,BIconCloudPlusFill:DA,BIconCloudRain:RA,BIconCloudRainFill:SA,BIconCloudRainHeavy:_A,BIconCloudRainHeavyFill:kA,BIconCloudSlash:MA,BIconCloudSlashFill:TA,BIconCloudSleet:VA,BIconCloudSleetFill:xA,BIconCloudSnow:BA,BIconCloudSnowFill:LA,BIconCloudSun:OA,BIconCloudSunFill:EA,BIconCloudUpload:UA,BIconCloudUploadFill:FA,BIconClouds:HA,BIconCloudsFill:jA,BIconCloudy:GA,BIconCloudyFill:WA,BIconCode:NA,BIconCodeSlash:$A,BIconCodeSquare:qA,BIconCoin:JA,BIconCollection:KA,BIconCollectionFill:QA,BIconCollectionPlay:YA,BIconCollectionPlayFill:XA,BIconColumns:ZA,BIconColumnsGap:eP,BIconCommand:tP,BIconCompass:aP,BIconCompassFill:oP,BIconCone:sP,BIconConeStriped:iP,BIconController:nP,BIconCpu:rP,BIconCpuFill:cP,BIconCreditCard:lP,BIconCreditCard2Back:hP,BIconCreditCard2BackFill:dP,BIconCreditCard2Front:mP,BIconCreditCard2FrontFill:pP,BIconCreditCardFill:uP,BIconCrop:fP,BIconCup:gP,BIconCupFill:vP,BIconCupStraw:AP,BIconCurrencyBitcoin:PP,BIconCurrencyDollar:bP,BIconCurrencyEuro:yP,BIconCurrencyExchange:wP,BIconCurrencyPound:IP,BIconCurrencyYen:zP,BIconCursor:CP,BIconCursorFill:DP,BIconCursorText:RP,BIconDash:SP,BIconDashCircle:_P,BIconDashCircleDotted:kP,BIconDashCircleFill:MP,BIconDashLg:TP,BIconDashSquare:VP,BIconDashSquareDotted:xP,BIconDashSquareFill:BP,BIconDiagram2:LP,BIconDiagram2Fill:OP,BIconDiagram3:EP,BIconDiagram3Fill:UP,BIconDiamond:FP,BIconDiamondFill:HP,BIconDiamondHalf:jP,BIconDice1:GP,BIconDice1Fill:WP,BIconDice2:NP,BIconDice2Fill:$P,BIconDice3:qP,BIconDice3Fill:JP,BIconDice4:KP,BIconDice4Fill:QP,BIconDice5:YP,BIconDice5Fill:XP,BIconDice6:ZP,BIconDice6Fill:eb,BIconDisc:tb,BIconDiscFill:ab,BIconDiscord:ob,BIconDisplay:sb,BIconDisplayFill:ib,BIconDistributeHorizontal:nb,BIconDistributeVertical:rb,BIconDoorClosed:cb,BIconDoorClosedFill:lb,BIconDoorOpen:hb,BIconDoorOpenFill:db,BIconDot:mb,BIconDownload:pb,BIconDroplet:ub,BIconDropletFill:fb,BIconDropletHalf:gb,BIconEarbuds:vb,BIconEasel:Ab,BIconEaselFill:Pb,BIconEgg:bb,BIconEggFill:yb,BIconEggFried:wb,BIconEject:Ib,BIconEjectFill:zb,BIconEmojiAngry:Cb,BIconEmojiAngryFill:Db,BIconEmojiDizzy:Rb,BIconEmojiDizzyFill:Sb,BIconEmojiExpressionless:_b,BIconEmojiExpressionlessFill:kb,BIconEmojiFrown:Mb,BIconEmojiFrownFill:Tb,BIconEmojiHeartEyes:Vb,BIconEmojiHeartEyesFill:xb,BIconEmojiLaughing:Bb,BIconEmojiLaughingFill:Lb,BIconEmojiNeutral:Ob,BIconEmojiNeutralFill:Eb,BIconEmojiSmile:Ub,BIconEmojiSmileFill:Fb,BIconEmojiSmileUpsideDown:Hb,BIconEmojiSmileUpsideDownFill:jb,BIconEmojiSunglasses:Gb,BIconEmojiSunglassesFill:Wb,BIconEmojiWink:Nb,BIconEmojiWinkFill:$b,BIconEnvelope:qb,BIconEnvelopeFill:Jb,BIconEnvelopeOpen:Kb,BIconEnvelopeOpenFill:Qb,BIconEraser:Yb,BIconEraserFill:Xb,BIconExclamation:Zb,BIconExclamationCircle:ey,BIconExclamationCircleFill:ty,BIconExclamationDiamond:ay,BIconExclamationDiamondFill:oy,BIconExclamationLg:sy,BIconExclamationOctagon:iy,BIconExclamationOctagonFill:ny,BIconExclamationSquare:ry,BIconExclamationSquareFill:cy,BIconExclamationTriangle:ly,BIconExclamationTriangleFill:hy,BIconExclude:dy,BIconEye:my,BIconEyeFill:py,BIconEyeSlash:uy,BIconEyeSlashFill:fy,BIconEyedropper:gy,BIconEyeglasses:vy,BIconFacebook:Ay,BIconFile:Py,BIconFileArrowDown:by,BIconFileArrowDownFill:yy,BIconFileArrowUp:wy,BIconFileArrowUpFill:Iy,BIconFileBarGraph:zy,BIconFileBarGraphFill:Cy,BIconFileBinary:Dy,BIconFileBinaryFill:Ry,BIconFileBreak:Sy,BIconFileBreakFill:_y,BIconFileCheck:ky,BIconFileCheckFill:My,BIconFileCode:Ty,BIconFileCodeFill:Vy,BIconFileDiff:xy,BIconFileDiffFill:By,BIconFileEarmark:Ly,BIconFileEarmarkArrowDown:Oy,BIconFileEarmarkArrowDownFill:Ey,BIconFileEarmarkArrowUp:Uy,BIconFileEarmarkArrowUpFill:Fy,BIconFileEarmarkBarGraph:Hy,BIconFileEarmarkBarGraphFill:jy,BIconFileEarmarkBinary:Gy,BIconFileEarmarkBinaryFill:Wy,BIconFileEarmarkBreak:Ny,BIconFileEarmarkBreakFill:$y,BIconFileEarmarkCheck:qy,BIconFileEarmarkCheckFill:Jy,BIconFileEarmarkCode:Ky,BIconFileEarmarkCodeFill:Qy,BIconFileEarmarkDiff:Yy,BIconFileEarmarkDiffFill:Xy,BIconFileEarmarkEasel:Zy,BIconFileEarmarkEaselFill:ew,BIconFileEarmarkExcel:tw,BIconFileEarmarkExcelFill:aw,BIconFileEarmarkFill:ow,BIconFileEarmarkFont:sw,BIconFileEarmarkFontFill:iw,BIconFileEarmarkImage:nw,BIconFileEarmarkImageFill:rw,BIconFileEarmarkLock:cw,BIconFileEarmarkLock2:lw,BIconFileEarmarkLock2Fill:hw,BIconFileEarmarkLockFill:dw,BIconFileEarmarkMedical:mw,BIconFileEarmarkMedicalFill:pw,BIconFileEarmarkMinus:uw,BIconFileEarmarkMinusFill:fw,BIconFileEarmarkMusic:gw,BIconFileEarmarkMusicFill:vw,BIconFileEarmarkPdf:Aw,BIconFileEarmarkPdfFill:Pw,BIconFileEarmarkPerson:bw,BIconFileEarmarkPersonFill:yw,BIconFileEarmarkPlay:ww,BIconFileEarmarkPlayFill:Iw,BIconFileEarmarkPlus:zw,BIconFileEarmarkPlusFill:Cw,BIconFileEarmarkPost:Dw,BIconFileEarmarkPostFill:Rw,BIconFileEarmarkPpt:Sw,BIconFileEarmarkPptFill:_w,BIconFileEarmarkRichtext:kw,BIconFileEarmarkRichtextFill:Mw,BIconFileEarmarkRuled:Tw,BIconFileEarmarkRuledFill:Vw,BIconFileEarmarkSlides:xw,BIconFileEarmarkSlidesFill:Bw,BIconFileEarmarkSpreadsheet:Lw,BIconFileEarmarkSpreadsheetFill:Ow,BIconFileEarmarkText:Ew,BIconFileEarmarkTextFill:Uw,BIconFileEarmarkWord:Fw,BIconFileEarmarkWordFill:Hw,BIconFileEarmarkX:jw,BIconFileEarmarkXFill:Gw,BIconFileEarmarkZip:Ww,BIconFileEarmarkZipFill:Nw,BIconFileEasel:$w,BIconFileEaselFill:qw,BIconFileExcel:Jw,BIconFileExcelFill:Kw,BIconFileFill:Qw,BIconFileFont:Yw,BIconFileFontFill:Xw,BIconFileImage:Zw,BIconFileImageFill:eI,BIconFileLock:tI,BIconFileLock2:aI,BIconFileLock2Fill:oI,BIconFileLockFill:sI,BIconFileMedical:iI,BIconFileMedicalFill:nI,BIconFileMinus:rI,BIconFileMinusFill:cI,BIconFileMusic:lI,BIconFileMusicFill:hI,BIconFilePdf:dI,BIconFilePdfFill:mI,BIconFilePerson:pI,BIconFilePersonFill:uI,BIconFilePlay:fI,BIconFilePlayFill:gI,BIconFilePlus:vI,BIconFilePlusFill:AI,BIconFilePost:PI,BIconFilePostFill:bI,BIconFilePpt:yI,BIconFilePptFill:wI,BIconFileRichtext:II,BIconFileRichtextFill:zI,BIconFileRuled:CI,BIconFileRuledFill:DI,BIconFileSlides:RI,BIconFileSlidesFill:SI,BIconFileSpreadsheet:_I,BIconFileSpreadsheetFill:kI,BIconFileText:MI,BIconFileTextFill:TI,BIconFileWord:VI,BIconFileWordFill:xI,BIconFileX:BI,BIconFileXFill:LI,BIconFileZip:OI,BIconFileZipFill:EI,BIconFiles:UI,BIconFilesAlt:FI,BIconFilm:HI,BIconFilter:jI,BIconFilterCircle:GI,BIconFilterCircleFill:WI,BIconFilterLeft:NI,BIconFilterRight:$I,BIconFilterSquare:qI,BIconFilterSquareFill:JI,BIconFlag:KI,BIconFlagFill:QI,BIconFlower1:YI,BIconFlower2:XI,BIconFlower3:ZI,BIconFolder:ez,BIconFolder2:tz,BIconFolder2Open:az,BIconFolderCheck:oz,BIconFolderFill:sz,BIconFolderMinus:iz,BIconFolderPlus:nz,BIconFolderSymlink:rz,BIconFolderSymlinkFill:cz,BIconFolderX:lz,BIconFonts:hz,BIconForward:dz,BIconForwardFill:mz,BIconFront:pz,BIconFullscreen:uz,BIconFullscreenExit:fz,BIconFunnel:gz,BIconFunnelFill:vz,BIconGear:Az,BIconGearFill:Pz,BIconGearWide:bz,BIconGearWideConnected:yz,BIconGem:wz,BIconGenderAmbiguous:Iz,BIconGenderFemale:zz,BIconGenderMale:Cz,BIconGenderTrans:Dz,BIconGeo:Rz,BIconGeoAlt:Sz,BIconGeoAltFill:_z,BIconGeoFill:kz,BIconGift:Mz,BIconGiftFill:Tz,BIconGithub:Vz,BIconGlobe:xz,BIconGlobe2:Bz,BIconGoogle:Lz,BIconGraphDown:Oz,BIconGraphUp:Ez,BIconGrid:Uz,BIconGrid1x2:Fz,BIconGrid1x2Fill:Hz,BIconGrid3x2:jz,BIconGrid3x2Gap:Gz,BIconGrid3x2GapFill:Wz,BIconGrid3x3:Nz,BIconGrid3x3Gap:$z,BIconGrid3x3GapFill:qz,BIconGridFill:Jz,BIconGripHorizontal:Kz,BIconGripVertical:Qz,BIconHammer:Yz,BIconHandIndex:Xz,BIconHandIndexFill:Zz,BIconHandIndexThumb:eC,BIconHandIndexThumbFill:tC,BIconHandThumbsDown:aC,BIconHandThumbsDownFill:oC,BIconHandThumbsUp:sC,BIconHandThumbsUpFill:iC,BIconHandbag:nC,BIconHandbagFill:rC,BIconHash:cC,BIconHdd:lC,BIconHddFill:hC,BIconHddNetwork:dC,BIconHddNetworkFill:mC,BIconHddRack:pC,BIconHddRackFill:uC,BIconHddStack:fC,BIconHddStackFill:gC,BIconHeadphones:vC,BIconHeadset:AC,BIconHeadsetVr:PC,BIconHeart:bC,BIconHeartFill:yC,BIconHeartHalf:wC,BIconHeptagon:IC,BIconHeptagonFill:zC,BIconHeptagonHalf:CC,BIconHexagon:DC,BIconHexagonFill:RC,BIconHexagonHalf:SC,BIconHourglass:_C,BIconHourglassBottom:kC,BIconHourglassSplit:MC,BIconHourglassTop:TC,BIconHouse:VC,BIconHouseDoor:xC,BIconHouseDoorFill:BC,BIconHouseFill:LC,BIconHr:OC,BIconHurricane:EC,BIconImage:UC,BIconImageAlt:FC,BIconImageFill:HC,BIconImages:jC,BIconInbox:GC,BIconInboxFill:WC,BIconInboxes:NC,BIconInboxesFill:$C,BIconInfo:qC,BIconInfoCircle:JC,BIconInfoCircleFill:KC,BIconInfoLg:QC,BIconInfoSquare:YC,BIconInfoSquareFill:XC,BIconInputCursor:ZC,BIconInputCursorText:eD,BIconInstagram:tD,BIconIntersect:aD,BIconJournal:oD,BIconJournalAlbum:sD,BIconJournalArrowDown:iD,BIconJournalArrowUp:nD,BIconJournalBookmark:rD,BIconJournalBookmarkFill:cD,BIconJournalCheck:lD,BIconJournalCode:hD,BIconJournalMedical:dD,BIconJournalMinus:mD,BIconJournalPlus:pD,BIconJournalRichtext:uD,BIconJournalText:fD,BIconJournalX:gD,BIconJournals:vD,BIconJoystick:AD,BIconJustify:PD,BIconJustifyLeft:bD,BIconJustifyRight:yD,BIconKanban:wD,BIconKanbanFill:ID,BIconKey:zD,BIconKeyFill:CD,BIconKeyboard:DD,BIconKeyboardFill:RD,BIconLadder:SD,BIconLamp:_D,BIconLampFill:kD,BIconLaptop:MD,BIconLaptopFill:TD,BIconLayerBackward:VD,BIconLayerForward:xD,BIconLayers:BD,BIconLayersFill:LD,BIconLayersHalf:OD,BIconLayoutSidebar:ED,BIconLayoutSidebarInset:UD,BIconLayoutSidebarInsetReverse:FD,BIconLayoutSidebarReverse:HD,BIconLayoutSplit:jD,BIconLayoutTextSidebar:GD,BIconLayoutTextSidebarReverse:WD,BIconLayoutTextWindow:ND,BIconLayoutTextWindowReverse:$D,BIconLayoutThreeColumns:qD,BIconLayoutWtf:JD,BIconLifePreserver:KD,BIconLightbulb:QD,BIconLightbulbFill:YD,BIconLightbulbOff:XD,BIconLightbulbOffFill:ZD,BIconLightning:eR,BIconLightningCharge:tR,BIconLightningChargeFill:aR,BIconLightningFill:oR,BIconLink:sR,BIconLink45deg:iR,BIconLinkedin:nR,BIconList:rR,BIconListCheck:cR,BIconListNested:lR,BIconListOl:hR,BIconListStars:dR,BIconListTask:mR,BIconListUl:pR,BIconLock:uR,BIconLockFill:fR,BIconMailbox:gR,BIconMailbox2:vR,BIconMap:AR,BIconMapFill:PR,BIconMarkdown:bR,BIconMarkdownFill:yR,BIconMask:wR,BIconMastodon:IR,BIconMegaphone:zR,BIconMegaphoneFill:CR,BIconMenuApp:DR,BIconMenuAppFill:RR,BIconMenuButton:SR,BIconMenuButtonFill:_R,BIconMenuButtonWide:kR,BIconMenuButtonWideFill:MR,BIconMenuDown:TR,BIconMenuUp:VR,BIconMessenger:xR,BIconMic:BR,BIconMicFill:LR,BIconMicMute:OR,BIconMicMuteFill:ER,BIconMinecart:UR,BIconMinecartLoaded:FR,BIconMoisture:HR,BIconMoon:jR,BIconMoonFill:GR,BIconMoonStars:WR,BIconMoonStarsFill:NR,BIconMouse:$R,BIconMouse2:qR,BIconMouse2Fill:JR,BIconMouse3:KR,BIconMouse3Fill:QR,BIconMouseFill:YR,BIconMusicNote:XR,BIconMusicNoteBeamed:ZR,BIconMusicNoteList:eS,BIconMusicPlayer:tS,BIconMusicPlayerFill:aS,BIconNewspaper:oS,BIconNodeMinus:sS,BIconNodeMinusFill:iS,BIconNodePlus:nS,BIconNodePlusFill:rS,BIconNut:cS,BIconNutFill:lS,BIconOctagon:hS,BIconOctagonFill:dS,BIconOctagonHalf:mS,BIconOption:pS,BIconOutlet:uS,BIconPaintBucket:fS,BIconPalette:gS,BIconPalette2:vS,BIconPaletteFill:AS,BIconPaperclip:PS,BIconParagraph:bS,BIconPatchCheck:yS,BIconPatchCheckFill:wS,BIconPatchExclamation:IS,BIconPatchExclamationFill:zS,BIconPatchMinus:CS,BIconPatchMinusFill:DS,BIconPatchPlus:RS,BIconPatchPlusFill:SS,BIconPatchQuestion:_S,BIconPatchQuestionFill:kS,BIconPause:MS,BIconPauseBtn:TS,BIconPauseBtnFill:VS,BIconPauseCircle:xS,BIconPauseCircleFill:BS,BIconPauseFill:LS,BIconPeace:OS,BIconPeaceFill:ES,BIconPen:US,BIconPenFill:FS,BIconPencil:HS,BIconPencilFill:jS,BIconPencilSquare:GS,BIconPentagon:WS,BIconPentagonFill:NS,BIconPentagonHalf:$S,BIconPeople:qS,BIconPeopleFill:JS,BIconPercent:KS,BIconPerson:QS,BIconPersonBadge:YS,BIconPersonBadgeFill:XS,BIconPersonBoundingBox:ZS,BIconPersonCheck:e_,BIconPersonCheckFill:t_,BIconPersonCircle:a_,BIconPersonDash:o_,BIconPersonDashFill:s_,BIconPersonFill:i_,BIconPersonLinesFill:n_,BIconPersonPlus:r_,BIconPersonPlusFill:c_,BIconPersonSquare:l_,BIconPersonX:h_,BIconPersonXFill:d_,BIconPhone:m_,BIconPhoneFill:p_,BIconPhoneLandscape:u_,BIconPhoneLandscapeFill:f_,BIconPhoneVibrate:g_,BIconPhoneVibrateFill:v_,BIconPieChart:A_,BIconPieChartFill:P_,BIconPiggyBank:b_,BIconPiggyBankFill:y_,BIconPin:w_,BIconPinAngle:I_,BIconPinAngleFill:z_,BIconPinFill:C_,BIconPinMap:D_,BIconPinMapFill:R_,BIconPip:S_,BIconPipFill:__,BIconPlay:k_,BIconPlayBtn:M_,BIconPlayBtnFill:T_,BIconPlayCircle:V_,BIconPlayCircleFill:x_,BIconPlayFill:B_,BIconPlug:L_,BIconPlugFill:O_,BIconPlus:E_,BIconPlusCircle:U_,BIconPlusCircleDotted:F_,BIconPlusCircleFill:H_,BIconPlusLg:j_,BIconPlusSquare:G_,BIconPlusSquareDotted:W_,BIconPlusSquareFill:N_,BIconPower:$_,BIconPrinter:q_,BIconPrinterFill:J_,BIconPuzzle:K_,BIconPuzzleFill:Q_,BIconQuestion:Y_,BIconQuestionCircle:X_,BIconQuestionCircleFill:Z_,BIconQuestionDiamond:ek,BIconQuestionDiamondFill:tk,BIconQuestionLg:ak,BIconQuestionOctagon:ok,BIconQuestionOctagonFill:sk,BIconQuestionSquare:ik,BIconQuestionSquareFill:nk,BIconRainbow:rk,BIconReceipt:ck,BIconReceiptCutoff:lk,BIconReception0:hk,BIconReception1:dk,BIconReception2:mk,BIconReception3:pk,BIconReception4:uk,BIconRecord:fk,BIconRecord2:gk,BIconRecord2Fill:vk,BIconRecordBtn:Ak,BIconRecordBtnFill:Pk,BIconRecordCircle:bk,BIconRecordCircleFill:yk,BIconRecordFill:wk,BIconRecycle:Ik,BIconReddit:zk,BIconReply:Ck,BIconReplyAll:Dk,BIconReplyAllFill:Rk,BIconReplyFill:Sk,BIconRss:_k,BIconRssFill:kk,BIconRulers:Mk,BIconSafe:Tk,BIconSafe2:Vk,BIconSafe2Fill:xk,BIconSafeFill:Bk,BIconSave:Lk,BIconSave2:Ok,BIconSave2Fill:Ek,BIconSaveFill:Uk,BIconScissors:Fk,BIconScrewdriver:Hk,BIconSdCard:jk,BIconSdCardFill:Gk,BIconSearch:Wk,BIconSegmentedNav:Nk,BIconServer:$k,BIconShare:qk,BIconShareFill:Jk,BIconShield:Kk,BIconShieldCheck:Qk,BIconShieldExclamation:Yk,BIconShieldFill:Xk,BIconShieldFillCheck:Zk,BIconShieldFillExclamation:eM,BIconShieldFillMinus:tM,BIconShieldFillPlus:aM,BIconShieldFillX:oM,BIconShieldLock:sM,BIconShieldLockFill:iM,BIconShieldMinus:nM,BIconShieldPlus:rM,BIconShieldShaded:cM,BIconShieldSlash:lM,BIconShieldSlashFill:hM,BIconShieldX:dM,BIconShift:mM,BIconShiftFill:pM,BIconShop:uM,BIconShopWindow:fM,BIconShuffle:gM,BIconSignpost:vM,BIconSignpost2:AM,BIconSignpost2Fill:PM,BIconSignpostFill:bM,BIconSignpostSplit:yM,BIconSignpostSplitFill:wM,BIconSim:IM,BIconSimFill:zM,BIconSkipBackward:CM,BIconSkipBackwardBtn:DM,BIconSkipBackwardBtnFill:RM,BIconSkipBackwardCircle:SM,BIconSkipBackwardCircleFill:_M,BIconSkipBackwardFill:kM,BIconSkipEnd:MM,BIconSkipEndBtn:TM,BIconSkipEndBtnFill:VM,BIconSkipEndCircle:xM,BIconSkipEndCircleFill:BM,BIconSkipEndFill:LM,BIconSkipForward:OM,BIconSkipForwardBtn:EM,BIconSkipForwardBtnFill:UM,BIconSkipForwardCircle:FM,BIconSkipForwardCircleFill:HM,BIconSkipForwardFill:jM,BIconSkipStart:GM,BIconSkipStartBtn:WM,BIconSkipStartBtnFill:NM,BIconSkipStartCircle:$M,BIconSkipStartCircleFill:qM,BIconSkipStartFill:JM,BIconSkype:KM,BIconSlack:QM,BIconSlash:YM,BIconSlashCircle:XM,BIconSlashCircleFill:ZM,BIconSlashLg:eT,BIconSlashSquare:tT,BIconSlashSquareFill:aT,BIconSliders:oT,BIconSmartwatch:sT,BIconSnow:iT,BIconSnow2:nT,BIconSnow3:rT,BIconSortAlphaDown:cT,BIconSortAlphaDownAlt:lT,BIconSortAlphaUp:hT,BIconSortAlphaUpAlt:dT,BIconSortDown:mT,BIconSortDownAlt:pT,BIconSortNumericDown:uT,BIconSortNumericDownAlt:fT,BIconSortNumericUp:gT,BIconSortNumericUpAlt:vT,BIconSortUp:AT,BIconSortUpAlt:PT,BIconSoundwave:bT,BIconSpeaker:yT,BIconSpeakerFill:wT,BIconSpeedometer:IT,BIconSpeedometer2:zT,BIconSpellcheck:CT,BIconSquare:DT,BIconSquareFill:RT,BIconSquareHalf:ST,BIconStack:_T,BIconStar:kT,BIconStarFill:MT,BIconStarHalf:TT,BIconStars:VT,BIconStickies:xT,BIconStickiesFill:BT,BIconSticky:LT,BIconStickyFill:OT,BIconStop:ET,BIconStopBtn:UT,BIconStopBtnFill:FT,BIconStopCircle:HT,BIconStopCircleFill:jT,BIconStopFill:GT,BIconStoplights:WT,BIconStoplightsFill:NT,BIconStopwatch:$T,BIconStopwatchFill:qT,BIconSubtract:JT,BIconSuitClub:KT,BIconSuitClubFill:QT,BIconSuitDiamond:YT,BIconSuitDiamondFill:XT,BIconSuitHeart:ZT,BIconSuitHeartFill:eV,BIconSuitSpade:tV,BIconSuitSpadeFill:aV,BIconSun:oV,BIconSunFill:sV,BIconSunglasses:iV,BIconSunrise:nV,BIconSunriseFill:rV,BIconSunset:cV,BIconSunsetFill:lV,BIconSymmetryHorizontal:hV,BIconSymmetryVertical:dV,BIconTable:mV,BIconTablet:pV,BIconTabletFill:uV,BIconTabletLandscape:fV,BIconTabletLandscapeFill:gV,BIconTag:vV,BIconTagFill:AV,BIconTags:PV,BIconTagsFill:bV,BIconTelegram:yV,BIconTelephone:wV,BIconTelephoneFill:IV,BIconTelephoneForward:zV,BIconTelephoneForwardFill:CV,BIconTelephoneInbound:DV,BIconTelephoneInboundFill:RV,BIconTelephoneMinus:SV,BIconTelephoneMinusFill:_V,BIconTelephoneOutbound:kV,BIconTelephoneOutboundFill:MV,BIconTelephonePlus:TV,BIconTelephonePlusFill:VV,BIconTelephoneX:xV,BIconTelephoneXFill:BV,BIconTerminal:LV,BIconTerminalFill:OV,BIconTextCenter:EV,BIconTextIndentLeft:UV,BIconTextIndentRight:FV,BIconTextLeft:HV,BIconTextParagraph:jV,BIconTextRight:GV,BIconTextarea:WV,BIconTextareaResize:NV,BIconTextareaT:$V,BIconThermometer:qV,BIconThermometerHalf:JV,BIconThermometerHigh:KV,BIconThermometerLow:QV,BIconThermometerSnow:YV,BIconThermometerSun:XV,BIconThreeDots:ZV,BIconThreeDotsVertical:ex,BIconToggle2Off:tx,BIconToggle2On:ax,BIconToggleOff:ox,BIconToggleOn:sx,BIconToggles:ix,BIconToggles2:nx,BIconTools:rx,BIconTornado:cx,BIconTranslate:lx,BIconTrash:hx,BIconTrash2:dx,BIconTrash2Fill:mx,BIconTrashFill:px,BIconTree:ux,BIconTreeFill:fx,BIconTriangle:gx,BIconTriangleFill:vx,BIconTriangleHalf:Ax,BIconTrophy:Px,BIconTrophyFill:bx,BIconTropicalStorm:yx,BIconTruck:wx,BIconTruckFlatbed:Ix,BIconTsunami:zx,BIconTv:Cx,BIconTvFill:Dx,BIconTwitch:Rx,BIconTwitter:Sx,BIconType:_x,BIconTypeBold:kx,BIconTypeH1:Mx,BIconTypeH2:Tx,BIconTypeH3:Vx,BIconTypeItalic:xx,BIconTypeStrikethrough:Bx,BIconTypeUnderline:Lx,BIconUiChecks:Ox,BIconUiChecksGrid:Ex,BIconUiRadios:Ux,BIconUiRadiosGrid:Fx,BIconUmbrella:Hx,BIconUmbrellaFill:jx,BIconUnion:Gx,BIconUnlock:Wx,BIconUnlockFill:Nx,BIconUpc:$x,BIconUpcScan:qx,BIconUpload:Jx,BIconVectorPen:Kx,BIconViewList:Qx,BIconViewStacked:Yx,BIconVinyl:Xx,BIconVinylFill:Zx,BIconVoicemail:eB,BIconVolumeDown:tB,BIconVolumeDownFill:aB,BIconVolumeMute:oB,BIconVolumeMuteFill:sB,BIconVolumeOff:iB,BIconVolumeOffFill:nB,BIconVolumeUp:rB,BIconVolumeUpFill:cB,BIconVr:lB,BIconWallet:hB,BIconWallet2:dB,BIconWalletFill:mB,BIconWatch:pB,BIconWater:uB,BIconWhatsapp:fB,BIconWifi:gB,BIconWifi1:vB,BIconWifi2:AB,BIconWifiOff:PB,BIconWind:bB,BIconWindow:yB,BIconWindowDock:wB,BIconWindowSidebar:IB,BIconWrench:zB,BIconX:CB,BIconXCircle:DB,BIconXCircleFill:RB,BIconXDiamond:SB,BIconXDiamondFill:_B,BIconXLg:kB,BIconXOctagon:MB,BIconXOctagonFill:TB,BIconXSquare:VB,BIconXSquareFill:xB,BIconYoutube:BB,BIconZoomIn:LB,BIconZoomOut:OB}});a("14d9");function u8(e,t){for(var a in t)e[a]=t[a];return e}var f8=/[!'()*]/g,g8=function(e){return"%"+e.charCodeAt(0).toString(16)},v8=/%2C/g,A8=function(e){return encodeURIComponent(e).replace(f8,g8).replace(v8,",")};function P8(e){try{return decodeURIComponent(e)}catch(t){0}return e}function b8(e,t,a){void 0===t&&(t={});var o,s=a||w8;try{o=s(e||"")}catch(r){o={}}for(var i in t){var n=t[i];o[i]=Array.isArray(n)?n.map(y8):y8(n)}return o}var y8=function(e){return null==e||"object"===typeof e?e:String(e)};function w8(e){var t={};return e=e.trim().replace(/^(\?|#|&)/,""),e?(e.split("&").forEach((function(e){var a=e.replace(/\+/g," ").split("="),o=P8(a.shift()),s=a.length>0?P8(a.join("=")):null;void 0===t[o]?t[o]=s:Array.isArray(t[o])?t[o].push(s):t[o]=[t[o],s]})),t):t}function I8(e){var t=e?Object.keys(e).map((function(t){var a=e[t];if(void 0===a)return"";if(null===a)return A8(t);if(Array.isArray(a)){var o=[];return a.forEach((function(e){void 0!==e&&(null===e?o.push(A8(t)):o.push(A8(t)+"="+A8(e)))})),o.join("&")}return A8(t)+"="+A8(a)})).filter((function(e){return e.length>0})).join("&"):null;return t?"?"+t:""}var z8=/\/?$/;function C8(e,t,a,o){var s=o&&o.options.stringifyQuery,i=t.query||{};try{i=D8(i)}catch(r){}var n={name:t.name||e&&e.name,meta:e&&e.meta||{},path:t.path||"/",hash:t.hash||"",query:i,params:t.params||{},fullPath:_8(t,s),matched:e?S8(e):[]};return a&&(n.redirectedFrom=_8(a,s)),Object.freeze(n)}function D8(e){if(Array.isArray(e))return e.map(D8);if(e&&"object"===typeof e){var t={};for(var a in e)t[a]=D8(e[a]);return t}return e}var R8=C8(null,{path:"/"});function S8(e){var t=[];while(e)t.unshift(e),e=e.parent;return t}function _8(e,t){var a=e.path,o=e.query;void 0===o&&(o={});var s=e.hash;void 0===s&&(s="");var i=t||I8;return(a||"/")+i(o)+s}function k8(e,t,a){return t===R8?e===t:!!t&&(e.path&&t.path?e.path.replace(z8,"")===t.path.replace(z8,"")&&(a||e.hash===t.hash&&M8(e.query,t.query)):!(!e.name||!t.name)&&(e.name===t.name&&(a||e.hash===t.hash&&M8(e.query,t.query)&&M8(e.params,t.params))))}function M8(e,t){if(void 0===e&&(e={}),void 0===t&&(t={}),!e||!t)return e===t;var a=Object.keys(e).sort(),o=Object.keys(t).sort();return a.length===o.length&&a.every((function(a,s){var i=e[a],n=o[s];if(n!==a)return!1;var r=t[a];return null==i||null==r?i===r:"object"===typeof i&&"object"===typeof r?M8(i,r):String(i)===String(r)}))}function T8(e,t){return 0===e.path.replace(z8,"/").indexOf(t.path.replace(z8,"/"))&&(!t.hash||e.hash===t.hash)&&V8(e.query,t.query)}function V8(e,t){for(var a in t)if(!(a in e))return!1;return!0}function x8(e){for(var t=0;t=0&&(t=e.slice(o),e=e.slice(0,o));var s=e.indexOf("?");return s>=0&&(a=e.slice(s+1),e=e.slice(0,s)),{path:e,query:a,hash:t}}function F8(e){return e.replace(/\/(?:\s*\/)+/g,"/")}var H8=Array.isArray||function(e){return"[object Array]"==Object.prototype.toString.call(e)},j8=r7,G8=J8,W8=K8,N8=X8,$8=n7,q8=new RegExp(["(\\\\.)","([\\/.])?(?:(?:\\:(\\w+)(?:\\(((?:\\\\.|[^\\\\()])+)\\))?|\\(((?:\\\\.|[^\\\\()])+)\\))([+*?])?|(\\*))"].join("|"),"g");function J8(e,t){var a,o=[],s=0,i=0,n="",r=t&&t.delimiter||"/";while(null!=(a=q8.exec(e))){var c=a[0],l=a[1],h=a.index;if(n+=e.slice(i,h),i=h+c.length,l)n+=l[1];else{var d=e[i],m=a[2],p=a[3],u=a[4],f=a[5],g=a[6],v=a[7];n&&(o.push(n),n="");var A=null!=m&&null!=d&&d!==m,P="+"===g||"*"===g,b="?"===g||"*"===g,y=a[2]||r,w=u||f;o.push({name:p||s++,prefix:m||"",delimiter:y,optional:b,repeat:P,partial:A,asterisk:!!v,pattern:w?e7(w):v?".*":"[^"+Z8(y)+"]+?"})}}return i1||!b.length)return 0===b.length?e():e("span",{},b)}if("a"===this.tag)P.on=A,P.attrs={href:r,"aria-current":g};else{var y=v7(this.$slots.default);if(y){y.isStatic=!1;var w=y.data=u8({},y.data);for(var I in w.on=w.on||{},w.on){var z=w.on[I];I in A&&(w.on[I]=Array.isArray(z)?z:[z])}for(var C in A)C in w.on?w.on[C].push(A[C]):w.on[C]=v;var D=y.data.attrs=u8({},y.data.attrs);D.href=r,D["aria-current"]=g}else P.on=A}return e(this.tag,P,this.$slots.default)}};function g7(e){if(!(e.metaKey||e.altKey||e.ctrlKey||e.shiftKey)&&!e.defaultPrevented&&(void 0===e.button||0===e.button)){if(e.currentTarget&&e.currentTarget.getAttribute){var t=e.currentTarget.getAttribute("target");if(/\b_blank\b/i.test(t))return}return e.preventDefault&&e.preventDefault(),!0}}function v7(e){if(e)for(var t,a=0;a-1&&(r.params[d]=a.params[d]);return r.path=l7(l.path,r.params,'named route "'+c+'"'),m(l,r,n)}if(r.path){r.params={};for(var p=0;p-1}function o6(e,t){return a6(e)&&e._isRouter&&(null==t||e.type===t)}function s6(e,t,a){var o=function(s){s>=e.length?a():e[s]?t(e[s],(function(){o(s+1)})):o(s+1)};o(0)}function i6(e){return function(t,a,o){var s=!1,i=0,n=null;n6(e,(function(e,t,a,r){if("function"===typeof e&&void 0===e.cid){s=!0,i++;var c,l=h6((function(t){l6(t)&&(t=t.default),e.resolved="function"===typeof t?t:d7.extend(t),a.components[r]=t,i--,i<=0&&o()})),h=h6((function(e){var t="Failed to resolve async component "+r+": "+e;n||(n=a6(e)?e:new Error(t),o(n))}));try{c=e(l,h)}catch(m){h(m)}if(c)if("function"===typeof c.then)c.then(l,h);else{var d=c.component;d&&"function"===typeof d.then&&d.then(l,h)}}})),s||o()}}function n6(e,t){return r6(e.map((function(e){return Object.keys(e.components).map((function(a){return t(e.components[a],e.instances[a],e,a)}))})))}function r6(e){return Array.prototype.concat.apply([],e)}var c6="function"===typeof Symbol&&"symbol"===typeof Symbol.toStringTag;function l6(e){return e.__esModule||c6&&"Module"===e[Symbol.toStringTag]}function h6(e){var t=!1;return function(){var a=[],o=arguments.length;while(o--)a[o]=arguments[o];if(!t)return t=!0,e.apply(this,a)}}var d6=function(e,t){this.router=e,this.base=m6(t),this.current=R8,this.pending=null,this.ready=!1,this.readyCbs=[],this.readyErrorCbs=[],this.errorCbs=[],this.listeners=[]};function m6(e){if(!e)if(P7){var t=document.querySelector("base");e=t&&t.getAttribute("href")||"/",e=e.replace(/^https?:\/\/[^\/]+/,"")}else e="/";return"/"!==e.charAt(0)&&(e="/"+e),e.replace(/\/$/,"")}function p6(e,t){var a,o=Math.max(e.length,t.length);for(a=0;a0)){var t=this.router,a=t.options.scrollBehavior,o=N7&&a;o&&this.listeners.push(V7());var s=function(){var a=e.current,s=w6(e.base);e.current===R8&&s===e._startLocation||e.transitionTo(s,(function(e){o&&x7(t,e,a,!0)}))};window.addEventListener("popstate",s),this.listeners.push((function(){window.removeEventListener("popstate",s)}))}},t.prototype.go=function(e){window.history.go(e)},t.prototype.push=function(e,t,a){var o=this,s=this,i=s.current;this.transitionTo(e,(function(e){$7(F8(o.base+e.fullPath)),x7(o.router,e,i,!1),t&&t(e)}),a)},t.prototype.replace=function(e,t,a){var o=this,s=this,i=s.current;this.transitionTo(e,(function(e){q7(F8(o.base+e.fullPath)),x7(o.router,e,i,!1),t&&t(e)}),a)},t.prototype.ensureURL=function(e){if(w6(this.base)!==this.current.fullPath){var t=F8(this.base+this.current.fullPath);e?$7(t):q7(t)}},t.prototype.getCurrentLocation=function(){return w6(this.base)},t}(d6);function w6(e){var t=window.location.pathname,a=t.toLowerCase(),o=e.toLowerCase();return!e||a!==o&&0!==a.indexOf(F8(o+"/"))||(t=t.slice(e.length)),(t||"/")+window.location.search+window.location.hash}var I6=function(e){function t(t,a,o){e.call(this,t,a),o&&z6(this.base)||C6()}return e&&(t.__proto__=e),t.prototype=Object.create(e&&e.prototype),t.prototype.constructor=t,t.prototype.setupListeners=function(){var e=this;if(!(this.listeners.length>0)){var t=this.router,a=t.options.scrollBehavior,o=N7&&a;o&&this.listeners.push(V7());var s=function(){var t=e.current;C6()&&e.transitionTo(D6(),(function(a){o&&x7(e.router,a,t,!0),N7||_6(a.fullPath)}))},i=N7?"popstate":"hashchange";window.addEventListener(i,s),this.listeners.push((function(){window.removeEventListener(i,s)}))}},t.prototype.push=function(e,t,a){var o=this,s=this,i=s.current;this.transitionTo(e,(function(e){S6(e.fullPath),x7(o.router,e,i,!1),t&&t(e)}),a)},t.prototype.replace=function(e,t,a){var o=this,s=this,i=s.current;this.transitionTo(e,(function(e){_6(e.fullPath),x7(o.router,e,i,!1),t&&t(e)}),a)},t.prototype.go=function(e){window.history.go(e)},t.prototype.ensureURL=function(e){var t=this.current.fullPath;D6()!==t&&(e?S6(t):_6(t))},t.prototype.getCurrentLocation=function(){return D6()},t}(d6);function z6(e){var t=w6(e);if(!/^\/#/.test(t))return window.location.replace(F8(e+"/#"+t)),!0}function C6(){var e=D6();return"/"===e.charAt(0)||(_6("/"+e),!1)}function D6(){var e=window.location.href,t=e.indexOf("#");return t<0?"":(e=e.slice(t+1),e)}function R6(e){var t=window.location.href,a=t.indexOf("#"),o=a>=0?t.slice(0,a):t;return o+"#"+e}function S6(e){N7?$7(R6(e)):window.location.hash=e}function _6(e){N7?q7(R6(e)):window.location.replace(R6(e))}var k6=function(e){function t(t,a){e.call(this,t,a),this.stack=[],this.index=-1}return e&&(t.__proto__=e),t.prototype=Object.create(e&&e.prototype),t.prototype.constructor=t,t.prototype.push=function(e,t,a){var o=this;this.transitionTo(e,(function(e){o.stack=o.stack.slice(0,o.index+1).concat(e),o.index++,t&&t(e)}),a)},t.prototype.replace=function(e,t,a){var o=this;this.transitionTo(e,(function(e){o.stack=o.stack.slice(0,o.index).concat(e),t&&t(e)}),a)},t.prototype.go=function(e){var t=this,a=this.index+e;if(!(a<0||a>=this.stack.length)){var o=this.stack[a];this.confirmTransition(o,(function(){var e=t.current;t.index=a,t.updateRoute(o),t.router.afterHooks.forEach((function(t){t&&t(o,e)}))}),(function(e){o6(e,J7.duplicated)&&(t.index=a)}))}},t.prototype.getCurrentLocation=function(){var e=this.stack[this.stack.length-1];return e?e.fullPath:"/"},t.prototype.ensureURL=function(){},t}(d6),M6=function(e){void 0===e&&(e={}),this.app=null,this.apps=[],this.options=e,this.beforeHooks=[],this.resolveHooks=[],this.afterHooks=[],this.matcher=z7(e.routes||[],this);var t=e.mode||"hash";switch(this.fallback="history"===t&&!N7&&!1!==e.fallback,this.fallback&&(t="hash"),P7||(t="abstract"),this.mode=t,t){case"history":this.history=new y6(this,e.base);break;case"hash":this.history=new I6(this,e.base,this.fallback);break;case"abstract":this.history=new k6(this,e.base);break;default:0}},T6={currentRoute:{configurable:!0}};M6.prototype.match=function(e,t,a){return this.matcher.match(e,t,a)},T6.currentRoute.get=function(){return this.history&&this.history.current},M6.prototype.init=function(e){var t=this;if(this.apps.push(e),e.$once("hook:destroyed",(function(){var a=t.apps.indexOf(e);a>-1&&t.apps.splice(a,1),t.app===e&&(t.app=t.apps[0]||null),t.app||t.history.teardown()})),!this.app){this.app=e;var a=this.history;if(a instanceof y6||a instanceof I6){var o=function(e){var o=a.current,s=t.options.scrollBehavior,i=N7&&s;i&&"fullPath"in e&&x7(t,e,o,!1)},s=function(e){a.setupListeners(),o(e)};a.transitionTo(a.getCurrentLocation(),s,s)}a.listen((function(e){t.apps.forEach((function(t){t._route=e}))}))}},M6.prototype.beforeEach=function(e){return x6(this.beforeHooks,e)},M6.prototype.beforeResolve=function(e){return x6(this.resolveHooks,e)},M6.prototype.afterEach=function(e){return x6(this.afterHooks,e)},M6.prototype.onReady=function(e,t){this.history.onReady(e,t)},M6.prototype.onError=function(e){this.history.onError(e)},M6.prototype.push=function(e,t,a){var o=this;if(!t&&!a&&"undefined"!==typeof Promise)return new Promise((function(t,a){o.history.push(e,t,a)}));this.history.push(e,t,a)},M6.prototype.replace=function(e,t,a){var o=this;if(!t&&!a&&"undefined"!==typeof Promise)return new Promise((function(t,a){o.history.replace(e,t,a)}));this.history.replace(e,t,a)},M6.prototype.go=function(e){this.history.go(e)},M6.prototype.back=function(){this.go(-1)},M6.prototype.forward=function(){this.go(1)},M6.prototype.getMatchedComponents=function(e){var t=e?e.matched?e:this.resolve(e).route:this.currentRoute;return t?[].concat.apply([],t.matched.map((function(e){return Object.keys(e.components).map((function(t){return e.components[t]}))}))):[]},M6.prototype.resolve=function(e,t,a){t=t||this.history.current;var o=h7(e,t,a,this),s=this.match(o,t),i=s.redirectedFrom||s.fullPath,n=this.history.base,r=B6(n,i,this.mode);return{location:o,route:s,href:r,normalizedTo:o,resolved:s}},M6.prototype.getRoutes=function(){return this.matcher.getRoutes()},M6.prototype.addRoute=function(e,t){this.matcher.addRoute(e,t),this.history.current!==R8&&this.history.transitionTo(this.history.getCurrentLocation())},M6.prototype.addRoutes=function(e){this.matcher.addRoutes(e),this.history.current!==R8&&this.history.transitionTo(this.history.getCurrentLocation())},Object.defineProperties(M6.prototype,T6);var V6=M6;function x6(e,t){return e.push(t),function(){var a=e.indexOf(t);a>-1&&e.splice(a,1)}}function B6(e,t,a){var o="hash"===a?"#"+t:t;return e?F8(e+"/"+o):o}M6.install=A7,M6.version="3.6.5",M6.isNavigationFailure=o6,M6.NavigationFailureType=J7,M6.START_LOCATION=R8,P7&&window.Vue&&window.Vue.use(M6);var L6=function(){var e=this,t=e.$createElement,a=e._self._c||t;return a("b-tab",[a("Summary",{attrs:{iam_data:e.iam_data,"policy-filter":e.policyFilter}})],1)},O6=[],E6=function(){var e=this,t=e.$createElement,a=e._self._c||t;return a("div",{staticClass:"report"},[a("b-row",{staticClass:"mb-3"},[a("b-col",[a("h3",[e._v("Executive Summary")]),a("p",[e._v(" This report contains the security assessment results from "),a("a",{attrs:{href:"https://github.com/salesforce/cloudsplaining",rel:"noreferrer"}},[e._v("Cloudsplaining")]),e._v(", which maps out the IAM risk landscape in a report.")]),a("p",[e._v(" The assessment identifies where resource ARN constraints are not used and identifies other risks in IAM policies: ")]),a("ul",[a("li",[e._v("Privilege Escalation")]),a("li",[e._v("Resource Exposure")]),a("li",[e._v("Infrastructure Modification")]),a("li",[e._v("Data Exfiltration")])]),a("p",[e._v(" Remediating these issues, where necessary, will help to limit the blast radius in the case of compromised AWS credentials. ")])])],1),a("b-row",{staticClass:"mb-3"},[a("b-col",{attrs:{lg:"8"}},[a("div",{staticClass:"d-none d-sm-block"},[a("SummaryFindings",{attrs:{"inline-policy-risks":e.inlinePolicyRisks,"customer-managed-policy-risks":e.customerManagedPolicyRisks,"aws-managed-policy-risks":e.awsManagedPolicyRisks}})],1)]),a("b-col",[a("b-table-simple",{attrs:{small:"",responsive:""}},[a("b-thead",{attrs:{"head-variant":"dark"}},[a("b-tr",[a("b-th",[e._v("Risk")]),a("b-th",[e._v("Instances")]),a("b-th",[e._v("Severity")])],1)],1),a("b-tbody",[a("b-tr",[a("b-th",[e._v("Privilege Escalation")]),a("b-td",[e._v(e._s(e.policyRisks.PrivilegeEscalation))]),a("b-td",[e._v(e._s(e.severity.PrivilegeEscalation))])],1),a("b-tr",[a("b-th",[e._v("Data Exfiltration")]),a("b-td",[e._v(e._s(e.policyRisks.DataExfiltration))]),a("b-td",[e._v(e._s(e.severity.DataExfiltration))])],1),a("b-tr",[a("b-th",[e._v("Resource Exposure")]),a("b-td",[e._v(e._s(e.policyRisks.ResourceExposure))]),a("b-td",[e._v(e._s(e.severity.ResourceExposure))])],1),a("b-tr",[a("b-th",[e._v("Credentials Exposure")]),a("b-td",[e._v(e._s(e.policyRisks.CredentialsExposure))]),a("b-td",[e._v(e._s(e.severity.CredentialsExposure))])],1),a("b-tr",[a("b-th",[e._v("Infrastructure Modification")]),a("b-td",[e._v(e._s(e.policyRisks.InfrastructureModification))]),a("b-td",[e._v(e._s(e.severity.InfrastructureModification))])],1)],1)],1)],1)],1)],1)},U6=[],F6=function(){var e=this,t=e.$createElement,a=e._self._c||t;return a("Bar",{attrs:{"chart-options":e.chartOptions,"chart-data":e.chartData,height:e.height,"inline-policy-risks":e.inlinePolicyRisks,"aws-managed-policy-risks":e.awsManagedPolicyRisks,"customer-managed-policy-risks":e.customerManagedPolicyRisks}})},H6=[];
/*!
* Chart.js v3.9.1
* https://www.chartjs.org
@@ -34,7 +34,7 @@ function lee(e){return e+.5|0}const hee=(e,t,a)=>Math.max(Math.min(e,a),t);funct
* https://www.chartjs.org
* (c) 2022 Chart.js Contributors
* Released under the MIT License
- */class Zae{constructor(){this._request=null,this._charts=new Map,this._running=!1,this._lastDate=void 0}_notify(e,t,a,o){const s=t.listeners[o],i=t.duration;s.forEach(o=>o({chart:e,initial:t.initial,numSteps:i,currentStep:Math.min(a-t.start,i)}))}_refresh(){this._request||(this._running=!0,this._request=Y9.call(window,()=>{this._update(),this._request=null,this._running&&this._refresh()}))}_update(e=Date.now()){let t=0;this._charts.forEach((a,o)=>{if(!a.running||!a.items.length)return;const s=a.items;let i,n=s.length-1,r=!1;for(;n>=0;--n)i=s[n],i._active?(i._total>a.duration&&(a.duration=i._total),i.tick(e),r=!0):(s[n]=s[s.length-1],s.pop());r&&(o.draw(),this._notify(o,a,e,"progress")),s.length||(a.running=!1,this._notify(o,a,e,"complete"),a.initial=!1),t+=s.length}),this._lastDate=e,0===t&&(this._running=!1)}_getAnims(e){const t=this._charts;let a=t.get(e);return a||(a={running:!1,initial:!0,items:[],listeners:{complete:[],progress:[]}},t.set(e,a)),a}listen(e,t,a){this._getAnims(e).listeners[t].push(a)}add(e,t){t&&t.length&&this._getAnims(e).items.push(...t)}has(e){return this._getAnims(e).items.length>0}start(e){const t=this._charts.get(e);t&&(t.running=!0,t.start=Date.now(),t.duration=t.items.reduce((e,t)=>Math.max(e,t._duration),0),this._refresh())}running(e){if(!this._running)return!1;const t=this._charts.get(e);return!!(t&&t.running&&t.items.length)}stop(e){const t=this._charts.get(e);if(!t||!t.items.length)return;const a=t.items;let o=a.length-1;for(;o>=0;--o)a[o].cancel();t.items=[],this._notify(e,t,Date.now(),"complete")}remove(e){return this._charts.delete(e)}}var eoe=new Zae;const toe="transparent",aoe={boolean(e,t,a){return a>.5?t:e},color(e,t,a){const o=ate(e||toe),s=o.valid&&ate(t||toe);return s&&s.valid?s.mix(o,a).hexString():t},number(e,t,a){return e+(t-e)*a}};class ooe{constructor(e,t,a,o){const s=t[a];o=Bte([e.to,o,s,e.from]);const i=Bte([e.from,s,o]);this._active=!0,this._fn=e.fn||aoe[e.type||typeof i],this._easing=cee[e.easing]||cee.linear,this._start=Math.floor(Date.now()+(e.delay||0)),this._duration=this._total=Math.floor(e.duration),this._loop=!!e.loop,this._target=t,this._prop=a,this._from=i,this._to=o,this._promises=void 0}active(){return this._active}update(e,t,a){if(this._active){this._notify(!1);const o=this._target[this._prop],s=a-this._start,i=this._duration-s;this._start=a,this._duration=Math.floor(Math.max(i,e.duration)),this._total+=s,this._loop=!!e.loop,this._to=Bte([e.to,t,o,e.from]),this._from=Bte([e.from,o,t])}}cancel(){this._active&&(this.tick(Date.now()),this._active=!1,this._notify(!1))}tick(e){const t=e-this._start,a=this._duration,o=this._prop,s=this._from,i=this._loop,n=this._to;let r;if(this._active=s!==n&&(i||t1?2-r:r,r=this._easing(Math.min(1,Math.max(0,r))),this._target[o]=this._fn(s,n,r))}wait(){const e=this._promises||(this._promises=[]);return new Promise((t,a)=>{e.push({res:t,rej:a})})}_notify(e){const t=e?"res":"rej",a=this._promises||[];for(let o=0;o"onProgress"!==e&&"onComplete"!==e&&"fn"!==e}),lte.set("animations",{colors:{type:"color",properties:ioe},numbers:{type:"number",properties:soe}}),lte.describe("animations",{_fallback:"animation"}),lte.set("transitions",{active:{animation:{duration:400}},resize:{animation:{duration:0}},show:{animations:{colors:{from:"transparent"},visible:{type:"boolean",duration:0}}},hide:{animations:{colors:{to:"transparent"},visible:{type:"boolean",easing:"linear",fn:e=>0|e}}}});class roe{constructor(e,t){this._chart=e,this._properties=new Map,this.configure(t)}configure(e){if(!$6(e))return;const t=this._properties;Object.getOwnPropertyNames(e).forEach(a=>{const o=e[a];if(!$6(o))return;const s={};for(const e of noe)s[e]=o[e];(N6(o.properties)&&o.properties||[a]).forEach(e=>{e!==a&&t.has(e)||t.set(e,s)})})}_animateOptions(e,t){const a=t.options,o=loe(e,a);if(!o)return[];const s=this._createAnimations(o,a);return a.$shared&&coe(e.options.$animations,a).then(()=>{e.options=a},()=>{}),s}_createAnimations(e,t){const a=this._properties,o=[],s=e.$animations||(e.$animations={}),i=Object.keys(t),n=Date.now();let r;for(r=i.length-1;r>=0;--r){const c=i[r];if("$"===c.charAt(0))continue;if("options"===c){o.push(...this._animateOptions(e,t));continue}const l=t[c];let h=s[c];const d=a.get(c);if(h){if(d&&h.active()){h.update(d,l,n);continue}h.cancel()}d&&d.duration?(s[c]=h=new ooe(d,e,c,l),o.push(h)):e[c]=l}return o}update(e,t){if(0===this._properties.size)return void Object.assign(e,t);const a=this._createAnimations(e,t);return a.length?(eoe.add(this._chart,a),!0):void 0}}function coe(e,t){const a=[],o=Object.keys(t);for(let s=0;s0||!a&&t<0)return s.index}return null}function yoe(e,t){const{chart:a,_cachedMeta:o}=e,s=a._stacks||(a._stacks={}),{iScale:i,vScale:n,index:r}=o,c=i.axis,l=n.axis,h=voe(i,n,o),d=t.length;let m;for(let p=0;pa[e].axis===t).shift()}function Ioe(e,t){return Ote(e,{active:!1,dataset:void 0,datasetIndex:t,index:t,mode:"default",type:"dataset"})}function zoe(e,t,a){return Ote(e,{active:!1,dataIndex:t,parsed:void 0,raw:void 0,element:a,index:t,mode:"default",type:"data"})}function Coe(e,t){const a=e.controller.index,o=e.vScale&&e.vScale.axis;if(o){t=t||e._parsed;for(const e of t){const t=e._stacks;if(!t||void 0===t[o]||void 0===t[o][a])return;delete t[o][a]}}}const Doe=e=>"reset"===e||"none"===e,Roe=(e,t)=>t?e:Object.assign({},e),Soe=(e,t,a)=>e&&!t.hidden&&t._stacked&&{keys:poe(a,!0),values:null};class _oe{constructor(e,t){this.chart=e,this._ctx=e.ctx,this.index=t,this._cachedDataOpts={},this._cachedMeta=this.getMeta(),this._type=this._cachedMeta.type,this.options=void 0,this._parsing=!1,this._data=void 0,this._objectData=void 0,this._sharedOptions=void 0,this._drawStart=void 0,this._drawCount=void 0,this.enableOptionSharing=!1,this.supportsDecimation=!1,this.$context=void 0,this._syncList=[],this.initialize()}initialize(){const e=this._cachedMeta;this.configure(),this.linkScales(),e._stacked=goe(e.vScale,e),this.addElements()}updateIndex(e){this.index!==e&&Coe(this._cachedMeta),this.index=e}linkScales(){const e=this.chart,t=this._cachedMeta,a=this.getDataset(),o=(e,t,a,o)=>"x"===e?t:"r"===e?o:a,s=t.xAxisID=K6(a.xAxisID,woe(e,"x")),i=t.yAxisID=K6(a.yAxisID,woe(e,"y")),n=t.rAxisID=K6(a.rAxisID,woe(e,"r")),r=t.indexAxis,c=t.iAxisID=o(r,s,i,n),l=t.vAxisID=o(r,i,s,n);t.xScale=this.getScaleForId(s),t.yScale=this.getScaleForId(i),t.rScale=this.getScaleForId(n),t.iScale=this.getScaleForId(c),t.vScale=this.getScaleForId(l)}getDataset(){return this.chart.data.datasets[this.index]}getMeta(){return this.chart.getDatasetMeta(this.index)}getScaleForId(e){return this.chart.scales[e]}_getOtherScale(e){const t=this._cachedMeta;return e===t.iScale?t.vScale:t.iScale}reset(){this._update("reset")}_destroy(){const e=this._cachedMeta;this._data&&K9(this._data,this),e._stacked&&Coe(e)}_dataCheck(){const e=this.getDataset(),t=e.data||(e.data=[]),a=this._data;if($6(t))this._data=foe(t);else if(a!==t){if(a){K9(a,this);const e=this._cachedMeta;Coe(e),e._parsed=[]}t&&Object.isExtensible(t)&&J9(t,this),this._syncList=[],this._data=t}}addElements(){const e=this._cachedMeta;this._dataCheck(),this.datasetElementType&&(e.dataset=new this.datasetElementType)}buildOrUpdateElements(e){const t=this._cachedMeta,a=this.getDataset();let o=!1;this._dataCheck();const s=t._stacked;t._stacked=goe(t.vScale,t),t.stack!==a.stack&&(o=!0,Coe(t),t.stack=a.stack),this._resyncElements(e),(o||s!==t._stacked)&&yoe(this,t._parsed)}configure(){const e=this.chart.config,t=e.datasetScopeKeys(this._type),a=e.getOptionScopes(this.getDataset(),t,!0);this.options=e.createResolver(a,this.getContext()),this._parsing=this.options.parsing,this._cachedDataOpts={}}parse(e,t){const{_cachedMeta:a,_data:o}=this,{iScale:s,_stacked:i}=a,n=s.axis;let r,c,l,h=0===e&&t===o.length||a._sorted,d=e>0&&a._parsed[e-1];if(!1===this._parsing)a._parsed=o,a._sorted=!0,l=o;else{l=N6(o[e])?this.parseArrayData(a,o,e,t):$6(o[e])?this.parseObjectData(a,o,e,t):this.parsePrimitiveData(a,o,e,t);const s=()=>null===c[n]||d&&c[n]t||h=0;--d)if(!p()){this.updateRangeFromParsed(c,e,m,r);break}return c}getAllParsedValues(e){const t=this._cachedMeta._parsed,a=[];let o,s,i;for(o=0,s=t.length;o=0&ðis.getContext(a,o),u=c.resolveNamedOptions(d,m,p,h);return u.$shared&&(u.$shared=r,s[i]=Object.freeze(Roe(u,r))),u}_resolveAnimations(e,t,a){const o=this.chart,s=this._cachedDataOpts,i="animation-"+t,n=s[i];if(n)return n;let r;if(!1!==o.options.animation){const o=this.chart.config,s=o.datasetAnimationScopeKeys(this._type,t),i=o.getOptionScopes(this.getDataset(),s);r=o.createResolver(i,this.getContext(e,a,t))}const c=new roe(o,r&&r.animations);return r&&r._cacheable&&(s[i]=Object.freeze(c)),c}getSharedOptions(e){if(e.$shared)return this._sharedOptions||(this._sharedOptions=Object.assign({},e))}includeOptions(e,t){return!t||Doe(e)||this.chart._animationsDisabled}_getSharedOptions(e,t){const a=this.resolveDataElementOptions(e,t),o=this._sharedOptions,s=this.getSharedOptions(a),i=this.includeOptions(t,s)||s!==o;return this.updateSharedOptions(s,t,a),{sharedOptions:s,includeOptions:i}}updateElement(e,t,a,o){Doe(o)?Object.assign(e,a):this._resolveAnimations(t,o).update(e,a)}updateSharedOptions(e,t,a){e&&!Doe(t)&&this._resolveAnimations(void 0,t).update(e,a)}_setStyle(e,t,a,o){e.active=o;const s=this.getStyle(t,o);this._resolveAnimations(t,a,o).update(e,{options:!o&&this.getSharedOptions(s)||s})}removeHoverStyle(e,t,a){this._setStyle(e,a,"active",!1)}setHoverStyle(e,t,a){this._setStyle(e,a,"active",!0)}_removeDatasetHoverStyle(){const e=this._cachedMeta.dataset;e&&this._setStyle(e,void 0,"active",!1)}_setDatasetHoverStyle(){const e=this._cachedMeta.dataset;e&&this._setStyle(e,void 0,"active",!0)}_resyncElements(e){const t=this._data,a=this._cachedMeta.data;for(const[n,r,c]of this._syncList)this[n](r,c);this._syncList=[];const o=a.length,s=t.length,i=Math.min(s,o);i&&this.parse(0,i),s>o?this._insertElements(o,s-o,e):s{for(e.length+=t,n=e.length-1;n>=i;n--)e[n]=e[n-t]};for(r(s),n=e;ne-t))}return e._cache.$bar}function Moe(e){const t=e.iScale,a=koe(t,e.type);let o,s,i,n,r=t._length;const c=()=>{32767!==i&&-32768!==i&&(m9(n)&&(r=Math.min(r,Math.abs(i-n)||r)),n=i)};for(o=0,s=a.length;o0?s[e-1]:null,r=eMath.abs(r)&&(c=r,l=n),t[a.axis]=l,t._custom={barStart:c,barEnd:l,start:s,end:i,min:n,max:r}}function Boe(e,t,a,o){return N6(e)?xoe(e,t,a,o):t[a.axis]=a.parse(e,o),t}function Loe(e,t,a,o){const s=e.iScale,i=e.vScale,n=s.getLabels(),r=s===i,c=[];let l,h,d,m;for(l=a,h=a+o;l=a?1:-1)}function Uoe(e){let t,a,o,s,i;return e.horizontal?(t=e.base>e.x,a="left",o="right"):(t=e.basee.controller.options.grouped),s=a.options.stacked,i=[],n=e=>{const a=e.controller.getParsed(t),o=a&&a[e.vScale.axis];if(W6(o)||isNaN(o))return!0};for(const r of o)if((void 0===t||!n(r))&&((!1===s||-1===i.indexOf(r.stack)||void 0===s&&void 0===r.stack)&&i.push(r.stack),r.index===e))break;return i.length||i.push(void 0),i}_getStackCount(e){return this._getStacks(void 0,e).length}_getStackIndex(e,t,a){const o=this._getStacks(e,a),s=void 0!==t?o.indexOf(t):-1;return-1===s?o.length-1:s}_getRuler(){const e=this.options,t=this._cachedMeta,a=t.iScale,o=[];let s,i;for(s=0,i=t.data.length;s=0;--a)t=Math.max(t,e[a].size(this.resolveDataElementOptions(a))/2);return t>0&&t}getLabelAndValue(e){const t=this._cachedMeta,{xScale:a,yScale:o}=t,s=this.getParsed(e),i=a.getLabelForValue(s.x),n=o.getLabelForValue(s.y),r=s._custom;return{label:t.label,value:"("+i+", "+n+(r?", "+r:"")+")"}}update(e){const t=this._cachedMeta.data;this.updateElements(t,0,t.length,e)}updateElements(e,t,a,o){const s="reset"===o,{iScale:i,vScale:n}=this._cachedMeta,{sharedOptions:r,includeOptions:c}=this._getSharedOptions(t,o),l=i.axis,h=n.axis;for(let d=t;dU9(e,r,c,!0)?1:Math.max(t,t*a,o,o*a),u=(e,t,o)=>U9(e,r,c,!0)?-1:Math.min(t,t*a,o,o*a),f=p(0,l,d),g=p(y9,h,m),v=u(g9,l,d),A=u(g9+y9,h,m);o=(f-v)/2,s=(g-A)/2,i=-(f+v)/2,n=-(g+A)/2}return{ratioX:o,ratioY:s,offsetX:i,offsetY:n}}$oe.id="bubble",$oe.defaults={datasetElementType:!1,dataElementType:"point",animations:{numbers:{type:"number",properties:["x","y","borderWidth","radius"]}}},$oe.overrides={scales:{x:{type:"linear"},y:{type:"linear"}},plugins:{tooltip:{callbacks:{title(){return""}}}}};class Joe extends _oe{constructor(e,t){super(e,t),this.enableOptionSharing=!0,this.innerRadius=void 0,this.outerRadius=void 0,this.offsetX=void 0,this.offsetY=void 0}linkScales(){}parse(e,t){const a=this.getDataset().data,o=this._cachedMeta;if(!1===this._parsing)o._parsed=a;else{let s,i,n=e=>+a[e];if($6(a[e])){const{key:e="value"}=this._parsing;n=t=>+c9(a[t],e)}for(s=e,i=e+t;s0&&!isNaN(e)?v9*(Math.abs(e)/t):0}getLabelAndValue(e){const t=this._cachedMeta,a=this.chart,o=a.data.labels||[],s=Bae(t._parsed[e],a.options.locale);return{label:o[e]||"",value:s}}getMaxBorderWidth(e){let t=0;const a=this.chart;let o,s,i,n,r;if(!e)for(o=0,s=a.data.datasets.length;o"spacing"!==e,_indexable:e=>"spacing"!==e},Joe.overrides={aspectRatio:1,plugins:{legend:{labels:{generateLabels(e){const t=e.data;if(t.labels.length&&t.datasets.length){const{labels:{pointStyle:a}}=e.legend.options;return t.labels.map((t,o)=>{const s=e.getDatasetMeta(0),i=s.controller.getStyle(o);return{text:t,fillStyle:i.backgroundColor,strokeStyle:i.borderColor,lineWidth:i.borderWidth,pointStyle:a,hidden:!e.getDataVisibility(o),index:o}})}return[]}},onClick(e,t,a){a.chart.toggleDataVisibility(t.index),a.chart.update()}},tooltip:{callbacks:{title(){return""},label(e){let t=e.label;const a=": "+e.formattedValue;return N6(t)?(t=t.slice(),t[0]+=a):t+=a,t}}}}};class Koe extends _oe{initialize(){this.enableOptionSharing=!0,this.supportsDecimation=!0,super.initialize()}update(e){const t=this._cachedMeta,{dataset:a,data:o=[],_dataset:s}=t,i=this.chart._animationsDisabled;let{start:n,count:r}=oee(t,o,i);this._drawStart=n,this._drawCount=r,see(t)&&(n=0,r=o.length),a._chart=this.chart,a._datasetIndex=this.index,a._decimated=!!s._decimated,a.points=o;const c=this.resolveDatasetElementOptions(e);this.options.showLine||(c.borderWidth=0),c.segment=this.options.segment,this.updateElement(a,void 0,{animated:!i,options:c},e),this.updateElements(o,n,r,e)}updateElements(e,t,a,o){const s="reset"===o,{iScale:i,vScale:n,_stacked:r,_dataset:c}=this._cachedMeta,{sharedOptions:l,includeOptions:h}=this._getSharedOptions(t,o),d=i.axis,m=n.axis,{spanGaps:p,segment:u}=this.options,f=S9(p)?p:Number.POSITIVE_INFINITY,g=this.chart._animationsDisabled||s||"none"===o;let v=t>0&&this.getParsed(t-1);for(let A=t;A0&&Math.abs(a[d]-v[d])>f,u&&(p.parsed=a,p.raw=c.data[A]),h&&(p.options=l||this.resolveDataElementOptions(A,t.active?"active":o)),g||this.updateElement(t,A,p,o),v=a}}getMaxOverflow(){const e=this._cachedMeta,t=e.dataset,a=t.options&&t.options.borderWidth||0,o=e.data||[];if(!o.length)return a;const s=o[0].size(this.resolveDataElementOptions(0)),i=o[o.length-1].size(this.resolveDataElementOptions(o.length-1));return Math.max(a,s,i)/2}draw(){const e=this._cachedMeta;e.dataset.updateControlPoints(this.chart.chartArea,e.iScale.axis),super.draw()}}Koe.id="line",Koe.defaults={datasetElementType:"line",dataElementType:"point",showLine:!0,spanGaps:!1},Koe.overrides={scales:{_index_:{type:"category"},_value_:{type:"linear"}}};class Qoe extends _oe{constructor(e,t){super(e,t),this.innerRadius=void 0,this.outerRadius=void 0}getLabelAndValue(e){const t=this._cachedMeta,a=this.chart,o=a.data.labels||[],s=Bae(t._parsed[e].r,a.options.locale);return{label:o[e]||"",value:s}}parseObjectData(e,t,a,o){return oae.bind(this)(e,t,a,o)}update(e){const t=this._cachedMeta.data;this._updateRadius(),this.updateElements(t,0,t.length,e)}getMinMax(){const e=this._cachedMeta,t={min:Number.POSITIVE_INFINITY,max:Number.NEGATIVE_INFINITY};return e.data.forEach((e,a)=>{const o=this.getParsed(a).r;!isNaN(o)&&this.chart.getDataVisibility(a)&&(ot.max&&(t.max=o))}),t}_updateRadius(){const e=this.chart,t=e.chartArea,a=e.options,o=Math.min(t.right-t.left,t.bottom-t.top),s=Math.max(o/2,0),i=Math.max(a.cutoutPercentage?s/100*a.cutoutPercentage:1,0),n=(s-i)/e.getVisibleDatasetCount();this.outerRadius=s-n*this.index,this.innerRadius=this.outerRadius-n}updateElements(e,t,a,o){const s="reset"===o,i=this.chart,n=i.options,r=n.animation,c=this._cachedMeta.rScale,l=c.xCenter,h=c.yCenter,d=c.getIndexAngle(0)-.5*g9;let m,p=d;const u=360/this.countVisibleElements();for(m=0;m 


