Utilities for working with the MITRE™ ATT&CK™ framework, including a relational data model and an adversary emulation planning tool.
- ATT&CK™ Data Model – relational schema for representing MITRE™ ATT&CK data, enriched with Red Canary ATOMIC™ tests
- ATT&CK™ View – adversary emulation planning tooleee.
- Release Notes
- Overview
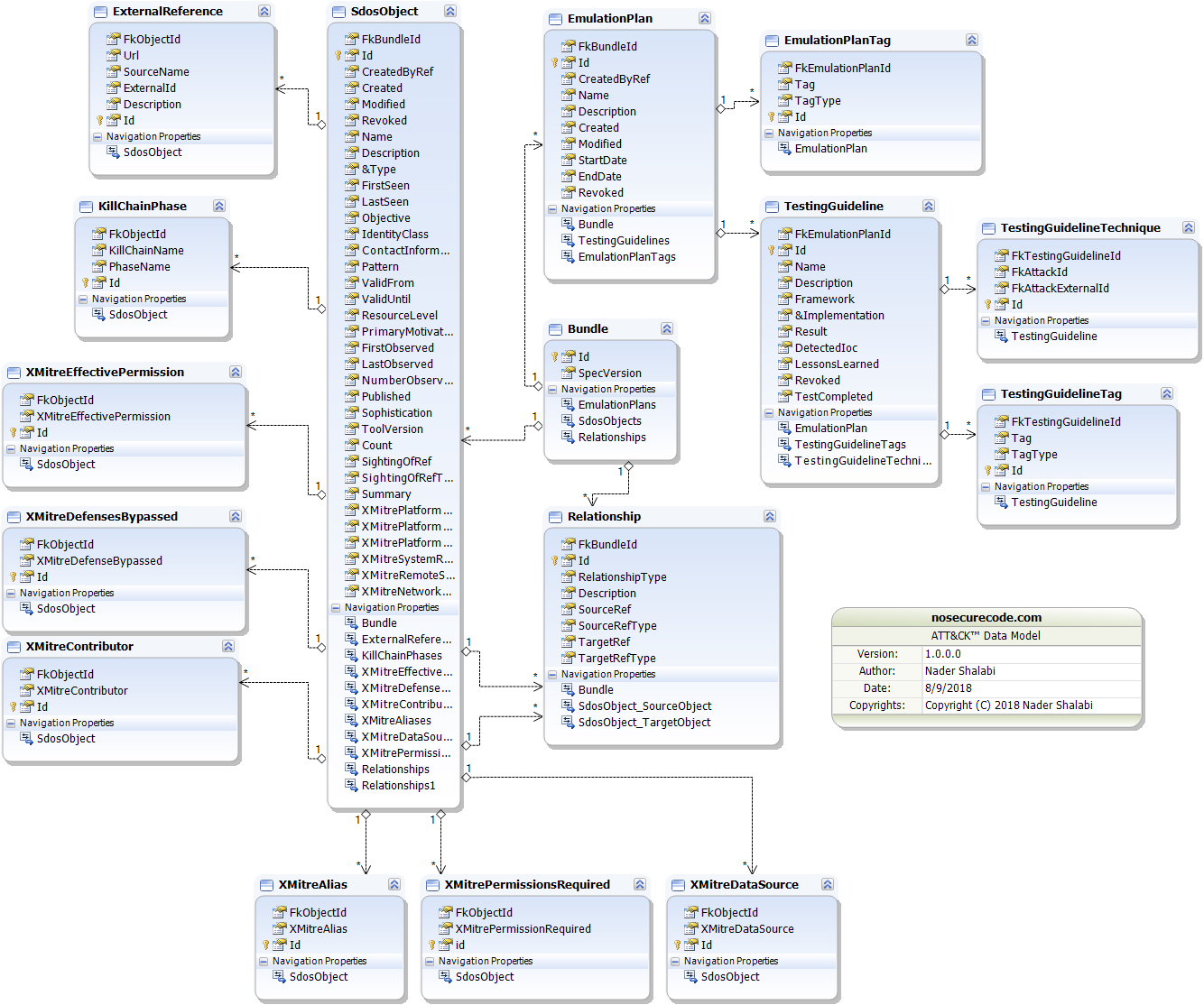
- The ATT&CK™ Data Model
- Accessing ATT&CK™ Data with SQL
- Additional Resources
- Support
- License
- Contact
- attack_view_db_structure.sql and attack_view_db_data.sql – scripts to build SQLite database structure and load data.
- enterprise-attack.xml – XML version of MITRE™ ATT&CK™ JSON.
- ics-attack.xml – XML version of MITRE™ ICS ATT&CK™ JSON.
- mobile-attack.xml – XML version of MITRE™ Mobile ATT&CK™ JSON.
ATT&CK™ View is a planning tool to help defenders design adversary emulation plans using the MITRE™ ATT&CK™ framework.
It provides a structured approach and comes bundled with a full adversary emulation plan for APT3 (developed by MITRE™). It also serves as an example usage of teh relational data model and how to enrich teh model (extend) with additonal data such as Red Canary ATOMIC™ tests.
(Source: MITRE Adversary Emulation Plans)
The ATT&CK™ framework is widely used, but many use cases require ATT&CK-enabled tools.
This repository provides a relational database (SQLite) to simplify integration and enable building custom tools or fusing ATT&CK with other frameworks.
Think in terms of a data model instead of the underlying database technology — the schema can be adapted to any DBMS.
Example conceptual model (can be implemented in any RDBMS):
Below are sample SQL queries for exploring the ATT&CK™ database.
To run them, use any SQLite management tool (see SQLite Management Tools).
SELECT name
FROM sdos_object
WHERE type IS "attack-pattern";OUTPUT
| name |
|---|
| .bash_profile and .bashrc |
| Access Token Manipulation |
| Accessibility Features |
| Account Discovery |
| Account Manipulation |
| ... |
SELECT id, name
FROM sdos_object
WHERE type IS "attack-pattern";OUTPUT
| id | name |
|---|---|
| attack-pattern--01df3350-ce05-4bdf-bdf8-0a919a66d4a8 | .bash_profile and .bashrc |
| attack-pattern--dcaa092b-7de9-4a21-977f-7fcb77e89c48 | Access Token Manipulation |
| attack-pattern--9b99b83a-1aac-4e29-b975-b374950551a3 | Accessibility Features |
| attack-pattern--72b74d71-8169-42aa-92e0-e7b04b9f5a08 | Account Discovery |
| attack-pattern--a10641f4-87b4-45a3-a906-92a149cb2c27 | Account Manipulation |
| ... | |
The id field is a unique key that will be used frequently in many SQL queries
The external references are stored in external_references table, since one ATT&CK™ technique can have one or more references, the link between the two tables is the technique identifier (check previous query), I will list multiple ways to access the external references
SELECT name, external_id
FROM sdos_object INNER JOIN external_references
ON sdos_object.id = external_references.fk_object_id
WHERE sdos_object.type IS "attack-pattern"
AND external_references.source_name IS "mitre-attack";OUTPUT
| name | external_id |
|---|---|
| .bash_profile and .bashrc | T1156 |
| Access Token Manipulation | T1134 |
| Accessibility Features | T1015 |
| Account Discovery | T1087 |
| Account Manipulation | T1098 |
| ... | |
SELECT name, external_id
FROM sdos_object INNER JOIN external_references
ON sdos_object.id = external_references.fk_object_id
WHERE sdos_object.type IS "attack-pattern"
AND x_mitre_platforms_windows IS "true"
AND external_references.source_name IS "mitre-attack";OUTPUT
| name | external_id |
|---|---|
| Access Token Manipulation | T1134 |
| Accessibility Features | T1015 |
| Account Discovery | T1087 |
| Account Manipulation | T1098 |
| AppCert DLLs | T1182 |
| ... | |
SELECT name, description
FROM sdos_object
WHERE type IS "malware";OUTPUT
| name | description |
|---|---|
| 3PARA RAT | 3PARA RAT is a remote access tool (RAT) programmed in C++ that has been used by Putter Panda. (Citation: CrowdStrike Putter Panda) Aliases: 3PARA RAT |
| 4H RAT | 4H RAT is malware that has been used by Putter Panda since at least 2007. (Citation: CrowdStrike Putter Panda) Aliases: 4H RAT |
| ADVSTORESHELL | ADVSTORESHELL is a spying backdoor that has been used by APT28 from at least 2012 to 2016. It is generally used for long-term espionage and is deployed on targets deemed interesting after a reconnaissance phase. (Citation: Kaspersky Sofacy) (Citation: ESET Sednit Part 2) Aliases: ADVSTORESHELL, NETUI, EVILTOSS, AZZY, Sedreco |
| ASPXSpy | ASPXSpy is a Web shell. It has been modified by Threat Group-3390 actors to create the ASPXTool version. (Citation: Dell TG-3390) Aliases: ASPXSpy, ASPXTool |
| Agent.btz | Agent.btz is a worm that primarily spreads itself via removable devices such as USB drives. It reportedly infected U.S. military networks in 2008. (Citation: Securelist Agent.btz) Aliases: Agent.btz |
| ... | |
SELECT name, description
FROM sdos_object
WHERE type IS "intrusion-set";OUTPUT
| name | description |
|---|---|
| APT1 | APT1 is a Chinese threat group that has been attributed to the 2nd Bureau of the People’s Liberation Army (PLA) General Staff Department’s (GSD) 3rd Department, commonly known by its Military Unit Cover Designator (MUCD) as Unit 61398. (Citation: Mandiant APT1) |
| APT12 | APT12 is a threat group that has been attributed to China. (Citation: Meyers Numbered Panda) |
| APT16 | APT16 is a China-based threat group that has launched spearphishing campaigns targeting Japanese and Taiwanese organizations. (Citation: FireEye EPS Awakens Part 2) |
| APT17 | APT17 is a China-based threat group that has conducted network intrusions against U.S. government entities, the defense industry, law firms, information technology companies, mining companies, and non-government organizations. (Citation: FireEye APT17) |
| APT18 | APT18 is a threat group that has operated since at least 2009 and has targeted a range of industries, including technology, manufacturing, human rights groups, government, and medical. (Citation: Dell Lateral Movement) |
| ... | |
All STIX 2.0 Domain Objects (SDO) relations are stored in "relationship" table. The following query is a nested query used to get the tools/malware used by APT3:
SELECT name, description
FROM sdos_object
WHERE (type IS "malware" OR type IS "tool")
AND id IN (SELECT target_ref
FROM relationship
WHERE relationship_type IS "uses"
AND source_ref IS "intrusion-set--0bbdf25b-30ff-4894-a1cd-49260d0dd2d9");OUTPUT
| name | description |
|---|---|
| OSInfo | OSInfo is a custom tool used by APT3 to do internal discovery on a victim's computer and network. (Citation: Symantec Buckeye) Aliases: OSInfo |
| PlugX | PlugX is a remote access tool (RAT) that uses modular plugins. (Citation: Lastline PlugX Analysis) It has been used by multiple threat groups. (Citation: FireEye Clandestine Fox Part 2) (Citation: New DragonOK) (Citation: Dell TG-3390) Aliases: PlugX, Sogu, Kaba, Korplug |
| RemoteCMD | RemoteCMD is a custom tool used by APT3 to execute commands on a remote system similar to SysInternal's PSEXEC functionality. (Citation: Symantec Buckeye) Aliases: RemoteCMD |
| SHOTPUT | SHOTPUT is a custom backdoor used by APT3. (Citation: FireEye Clandestine Wolf) Aliases: SHOTPUT, Backdoor.APT.CookieCutter, Pirpi |
| schtasks | schtasks is used to schedule execution of programs or scripts on a Windows system to run at a specific date and time. (Citation: TechNet Schtasks) Aliases: schtasks, schtasks.exe |
| ... | |
ATOMIC™ Tests are stored in three tables
- atomic_test table, this table simply maps ATOMIC™ tests to ATT&CK™ techniques. Each atomic_test record has one or more atomic_attack_test records that contains the actual test details
- atomic_attack_test, this tables holds the actual ATOMIC™ test details, each test has one or more input arguments represented with an atomic_input_arguments record
- atomic_input_arguments, holds tests input arguments details
The following SQL statement retrieves the ATOMIC™ test(s) associated with ATT&CK™ technique "T1031"
SELECT name, description, executor_name, executor_command
FROM atomic_attack_test
WHERE fk_atomic_attack_id IN
(SELECT id FROM atomic_attack
WHERE fk_attack_external_id IS "T1031");OUTPUT
| name | description | executor_name | executor_command |
|---|---|---|---|
| Modify Fax service to run PowerShell | This test will temporarily modify the service Fax by changing the binPath to PowerShell and will then revert the binPath change, restoring Fax to its original state. | command_prompt | sc config Fax binPath= "C:\windows\system32\WindowsPowerShell\v1.0\powershell.exe -noexit -c \"write-host 'T1031 Test'\"" sc start Fax sc config Fax binPath= "C:\WINDOWS\system32\fxssvc.exe" |
- MITRE ATT&CK™ : de l’importance de la temporalité
- Purple Team Playbook: Threat Modeling for Security Testingn
For any customizations or business collaboration inquiries, please visit applyingcode.com.
For issues or feature requests, please file a GitHub issue.
Alternatively, email: nader_shalabi@hotmail.com
Copyright Nader Shallabi. All rights reserved.
ATT&CK™ TOOLS CAN BE COPIED AND/OR DISTRIBUTED WITHOUT ANY EXPRESS PERMISSION OF NADER SHALLABI.
THIS SOFTWARE IS PROVIDED BY NADER SHALLABI "AS IS" AND ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL NADER SHALLABI
OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS
OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED
AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF
ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
The views and conclusions contained in the software and documentation are those of the authors and
should not be interpreted as representing official policies, either expressed or implied, of Nader Shallabi.